Singly-key type code inputting method
A password input and password technology, applied in the field of password input, can solve problems such as difficulty in hardware cost control, occupation, and multiple pins.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
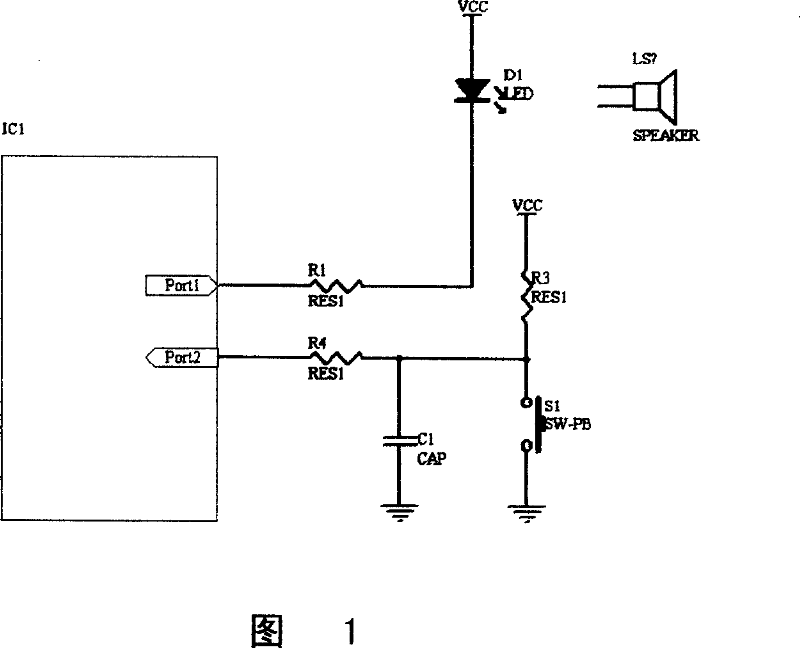
[0016] As shown in Figure 1 and Figure 2, when two I / O ports are used, the controller IC 1 The password output port of Port 1 through the current limiting resistor R1 and the LED D 1 (or the speaker SPEAKER) series circuit is connected to the power supply terminal VCC; the controller IC 1 Enter the password to confirm the port Port 2 Connected to one end of resistor R4, the resistor R 4 There is a pull-up resistor R connected between the other end of the VCC and the power supply terminal VCC 3 , and the power ground is connected by a filter capacitor C 1 and confirm key S 1 constitute a parallel branch. Controller IC 1 It has logic comparator and timer functions, and its working process includes the following steps:
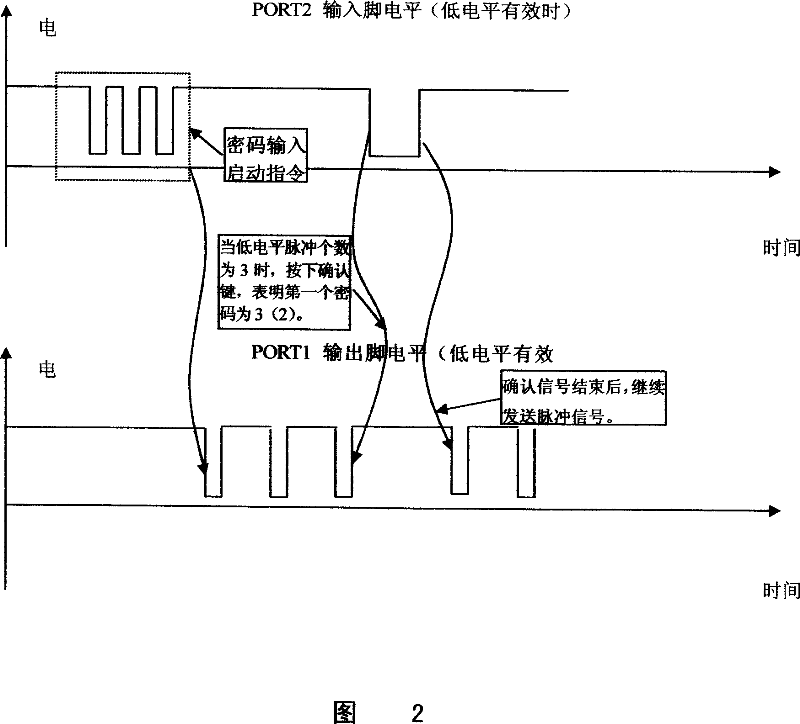
[0017] In the first step, when the controller IC 1 Enter the password to confirm the port Port 2 When it receives a password input start command, it outputs the password to Port Port 1 Output a pulse signal with a specific duty cycle, and monitor the p...
Embodiment 2
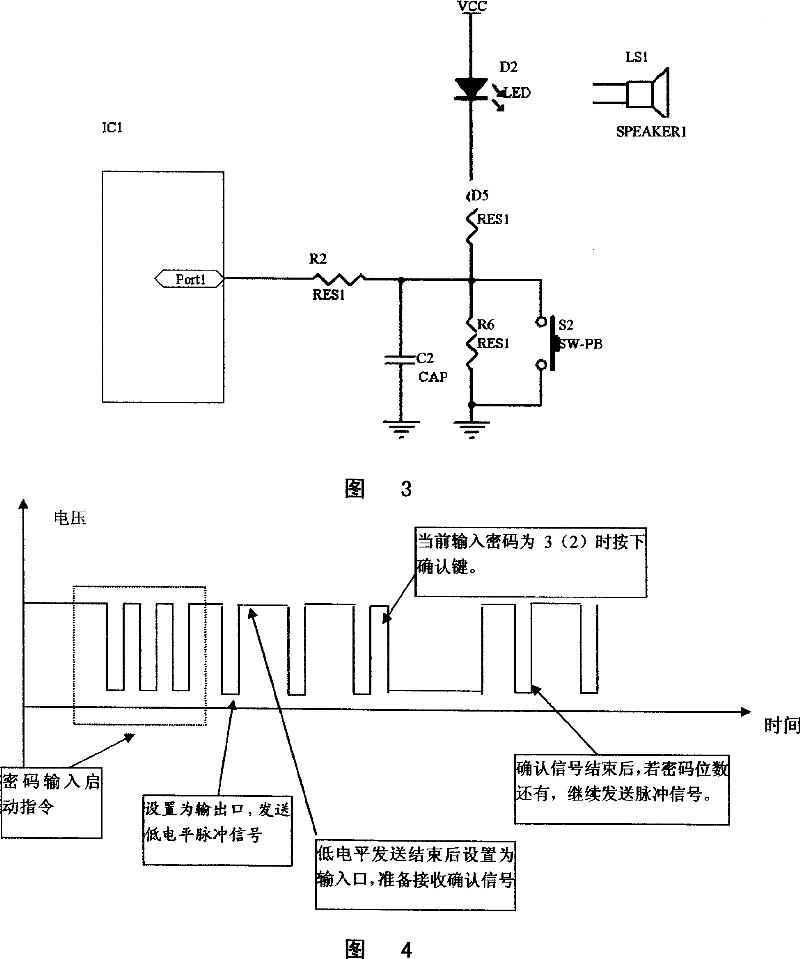
[0023] Embodiment 2: As shown in Fig. 3 and Fig. 4, when an I / O port is used, this pin must be used as an input / output port. Since it is impossible to set a port as input and output at the same time, when sending a low-level pulse signal, this port is used as an output port, and after each low-level transmission is completed, the output port is set as an input port. Ready to receive an acknowledgment signal. At this time, the password output port and the password input confirmation port of the controller are controlled by the controller IC 1 One of the input and output ports serves as a complete, the controller IC 1 The input and output ports with resistor R 2 connected to one end of the resistor R 2 There is a light-emitting diode D connected between the other end and the power supply terminal VCC 2 (or speaker SPEAKER 1 ) and resistor R 5 constitutes a series branch, while the resistor R 2 There is a filter capacitor C connected between the other end and the power gro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com