STB terminal and its verification method
A verification method and set-top box technology, which are applied in user identity/authority verification, television, analog security/charging systems, etc., can solve the problems of key theft, affecting system security, and inability to realize digital rights management, and improve security. Sexuality, the effect of preventing malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
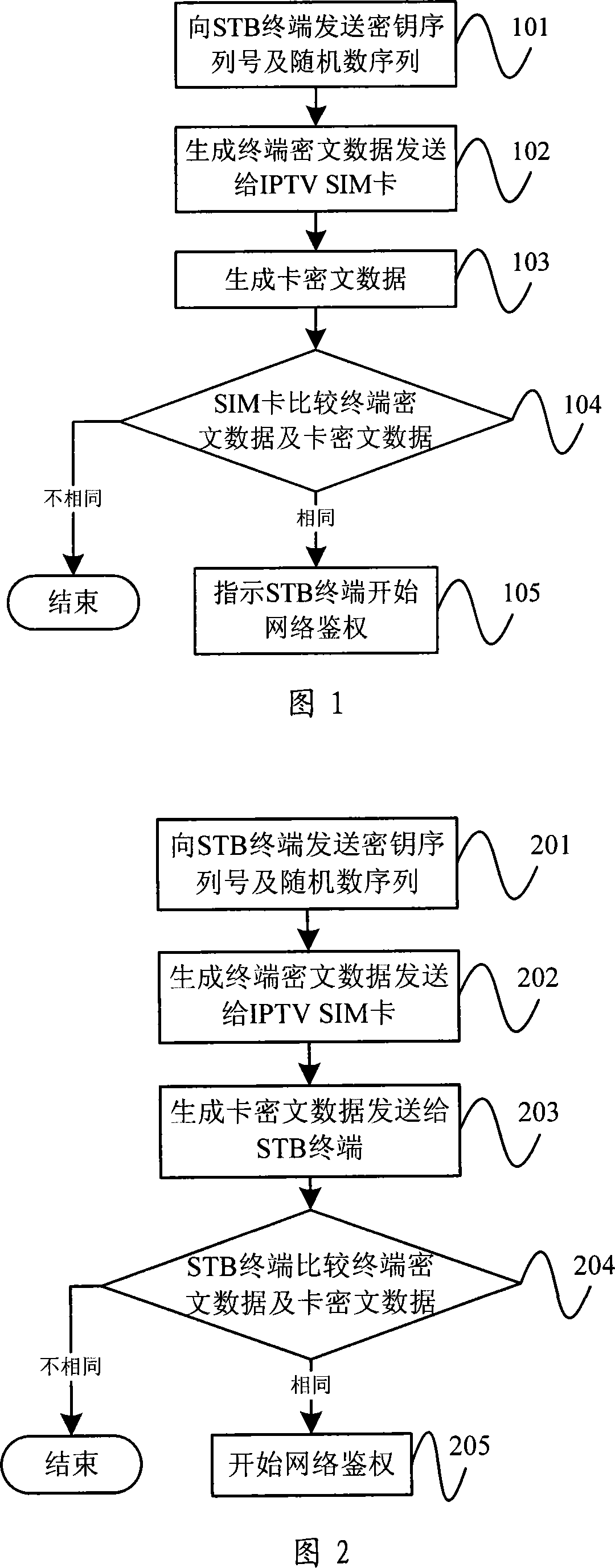
[0027] This embodiment provides a STB terminal verification method, as shown in Figure 1, including:
[0028] In step 101, the IPTV SIM card sends a key sequence number and a random number sequence (abbreviation: RND) to the STB terminal.
[0029] Wherein, the key serial number corresponds to the session key stored in the STB terminal, and is used to select a session key from multiple session keys. The number of digits of the key serial number can be determined according to the number of session keys.
[0030] Step 102, the STB terminal looks up the pre-stored session key in the STB terminal according to the received key serial number, encrypts the received random number sequence, generates terminal ciphertext data, and combines the terminal ciphertext data with the STB terminal The terminal information of the terminal is sent to the IPTV SIM card.
[0031] Wherein, the terminal information of the STB terminal may include a manufacturer code, a key version number, and the li...
Embodiment 2
[0039] This embodiment provides another STB terminal verification method, as shown in Figure 2, including:
[0040] Steps 201 and 202 are the same as steps 101 and 102 in Embodiment 1, and will not be repeated here.
[0041] Step 203, the IPTV SIM card searches for a pre-stored session key in the IPTV SIM card according to the received terminal information of the STB terminal, and encrypts the random number sequence sent to the STB terminal in step 201 according to the session key, Generate card ciphertext data and send it to STB terminal.
[0042] Step 204, the STB terminal compares the card ciphertext data received from the IPTV SIM card with the terminal ciphertext data obtained through encryption in step 202, and when the card ciphertext data is equal to the terminal ciphertext data , pass the verification, and then start running network authentication.
[0043] In addition, this embodiment can also adopt the method of presetting the authentication field described in Emb...
Embodiment 3
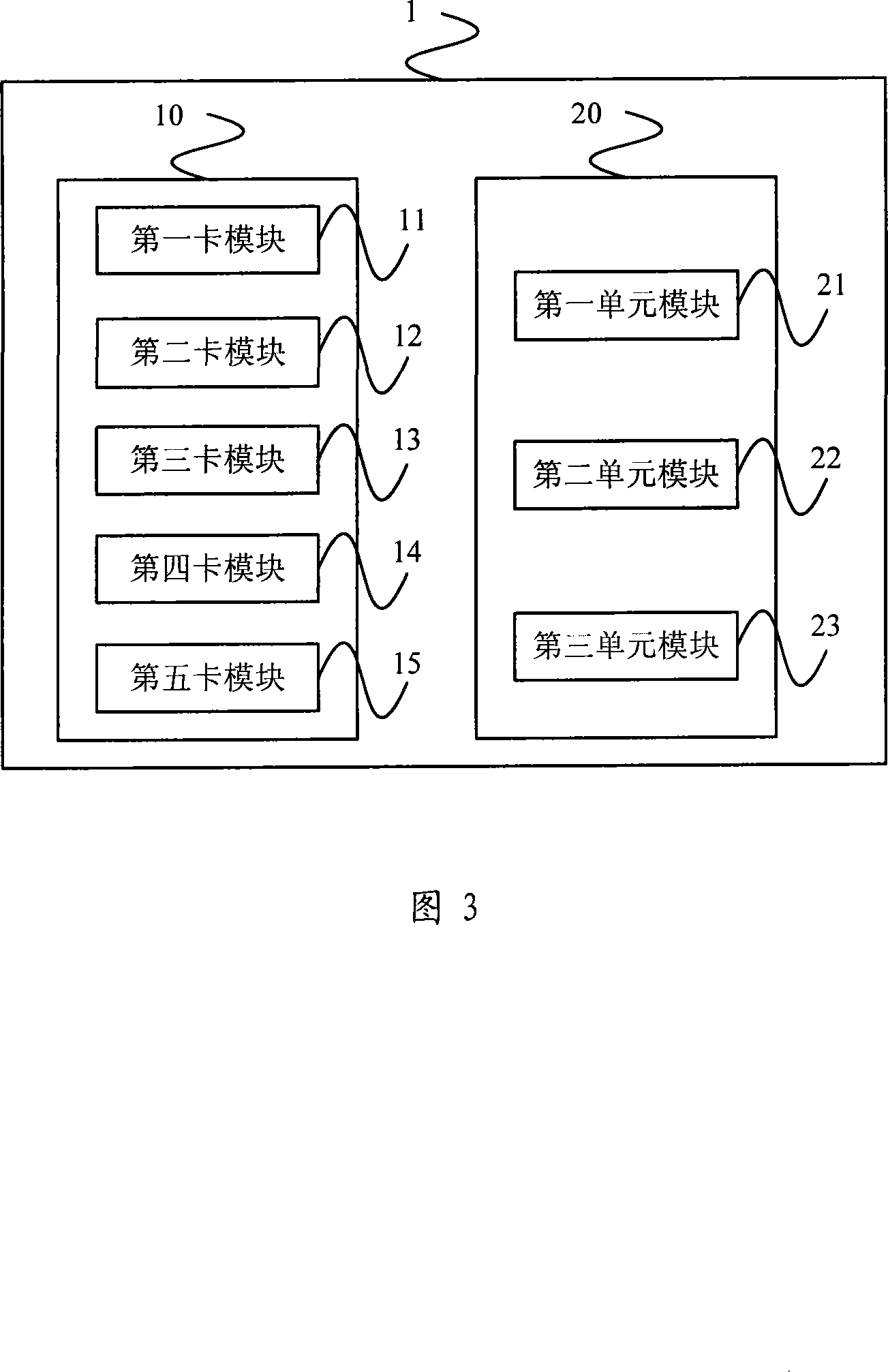
[0047]This embodiment provides a kind of STB terminal, as shown in Figure 3, STB terminal 1 comprises: terminal identification card 10 and verification unit 20, wherein, terminal identification card 10 comprises: first card module 11, second card module 12. The third card module 13 and the fourth card module 14 ; the verification unit 20 includes: a first unit module 21 , a second unit module 22 and a third unit module 23 . Its working principle is:
[0048] The first card module 11 of the terminal identification card 10 sends the key serial number and the random number sequence to the verification unit 20; the first unit module 21 of the verification unit 20 searches the pre-stored session from the key serial number of the first card module 11 Key; the second unit module 22 encrypts the random number sequence from the first card module 11 according to the session key found by the first unit module 21 to generate terminal ciphertext data; the third unit module 23 converts the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com