Method and system for policy control in associated response system
A technology for correlating responses and implementing strategies, which is applied in radio/inductive link selection arrangements, synchronization devices, user identity/authority verification, etc. It can solve problems such as account theft, abuse of user paid services, and damage to system performance to achieve security Control and ensure the effect of reliable delivery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
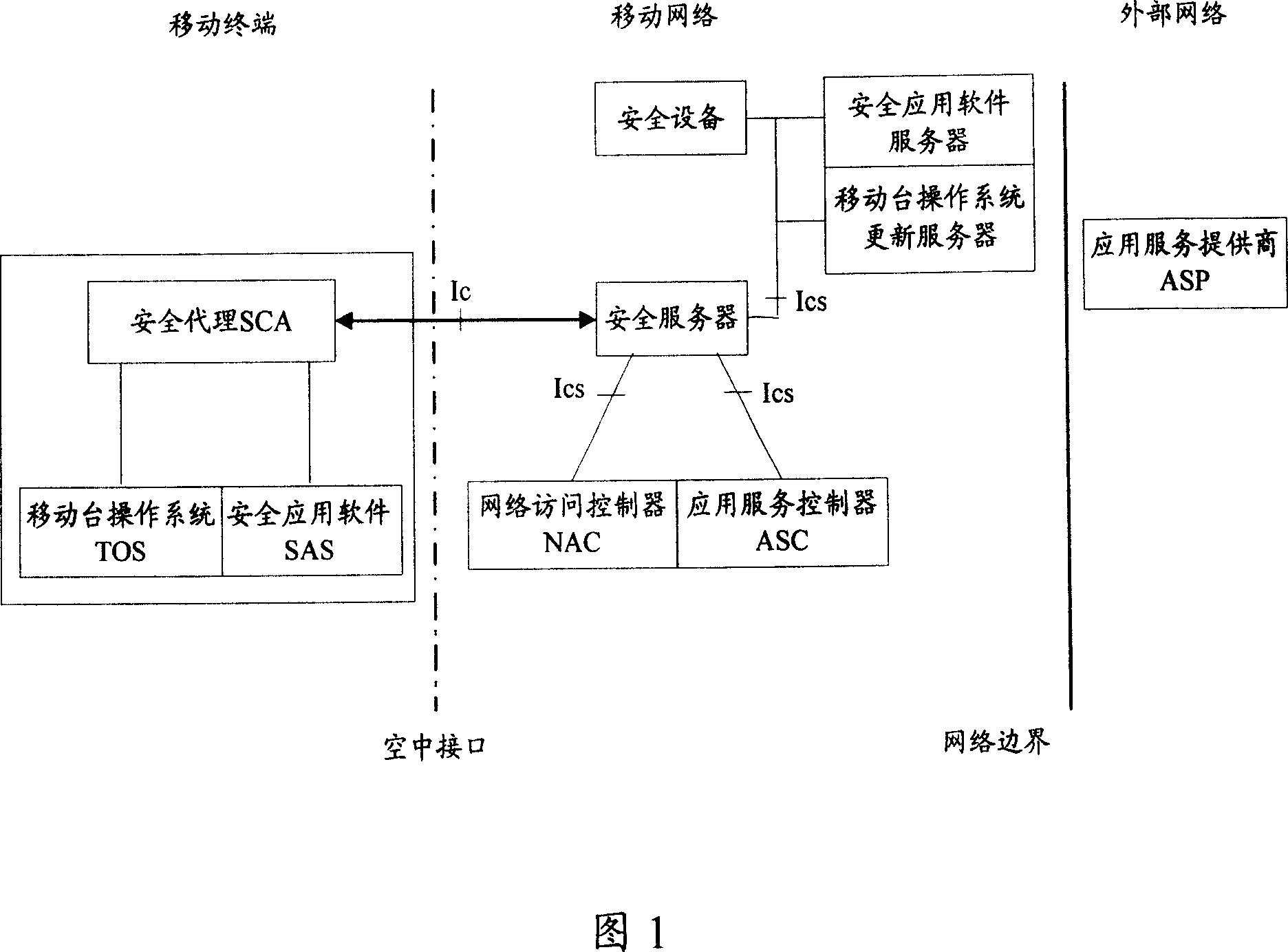
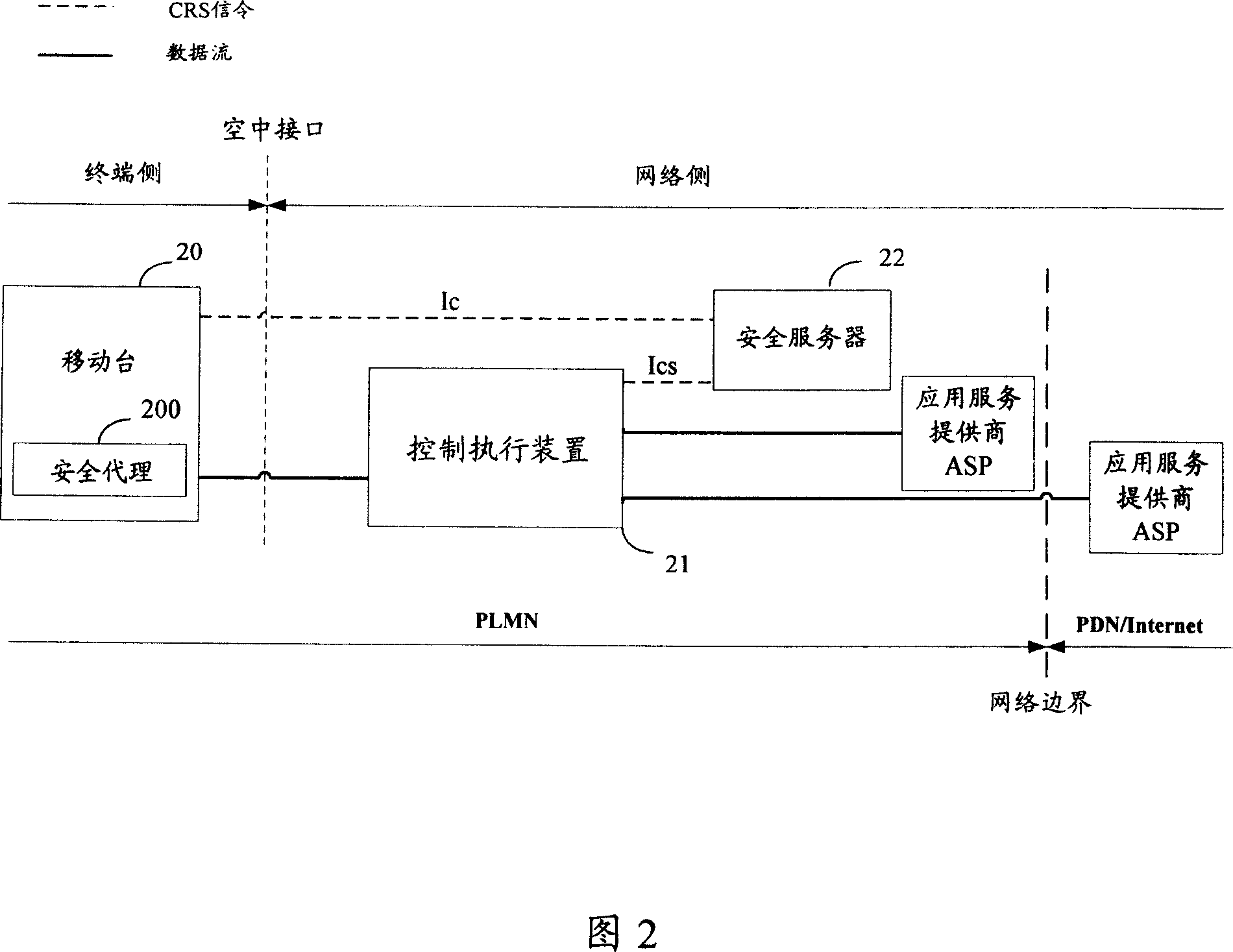
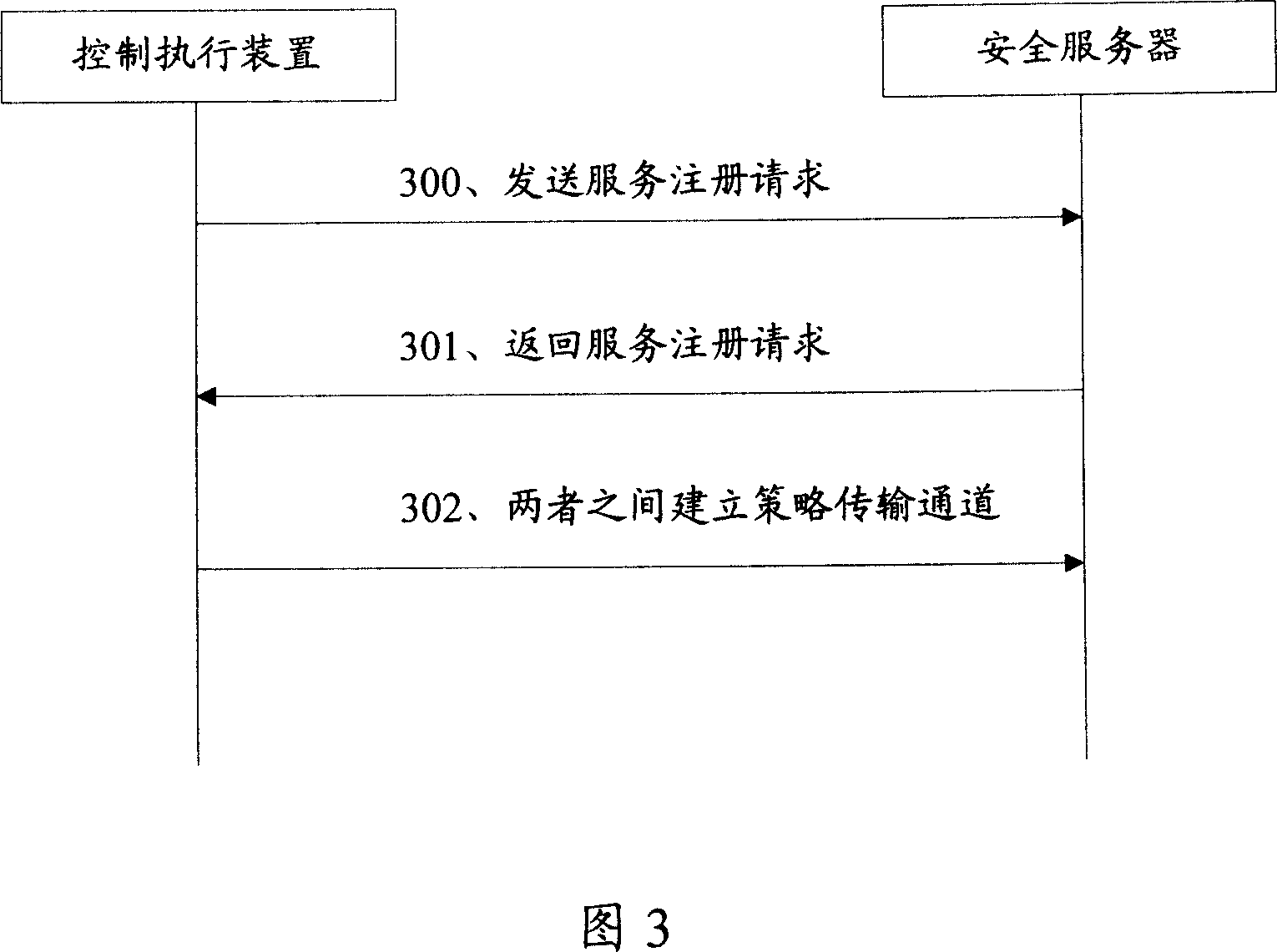
[0051]In order to solve the problem of how to interact between the security server and the control execution device in the existing association response system to reliably issue policies and realize policy control, the present invention establishes a policy transmission channel between the security server and the control execution device , sending the security control policy selected by the security server to the control execution device through the policy transmission channel.
[0052] In the embodiment of the present invention, the mobile station organizes its own security-related information, generates a security-related information report, and sends the security-related information report to the security server on the network side; the security server receives and analyzes the security-related information report, and determines whether the mobile station The security level of the mobile station is selected according to the security level, and the corresponding user control ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com