Method, system and mobile terminal of preventing playback attack
A mobile terminal, anti-replay technology, applied in the field of authentication, can solve the problems of replay attack, incremental update, no SQN generation and management clear instructions, etc., and achieve the effect of resisting replay attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
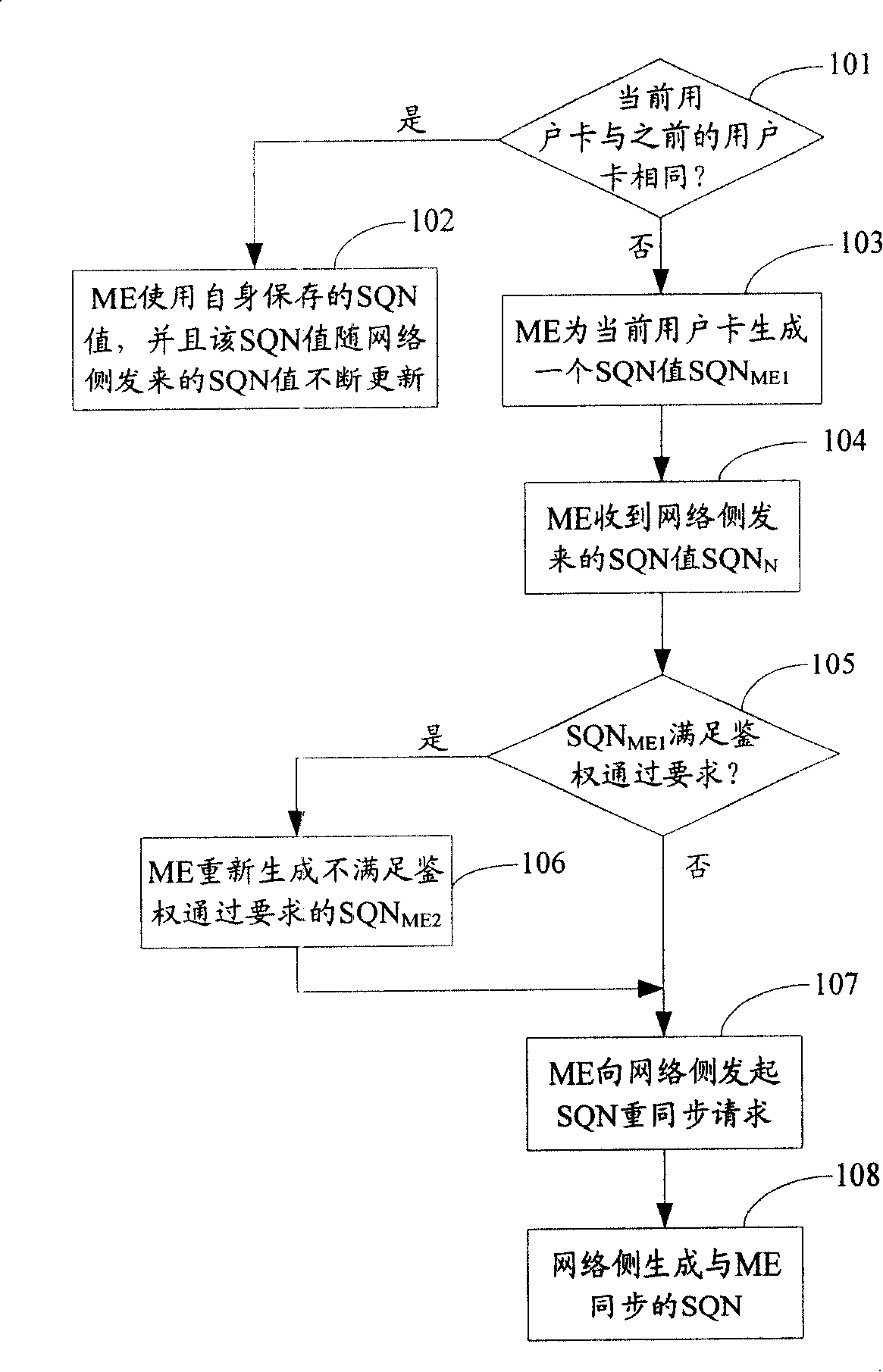
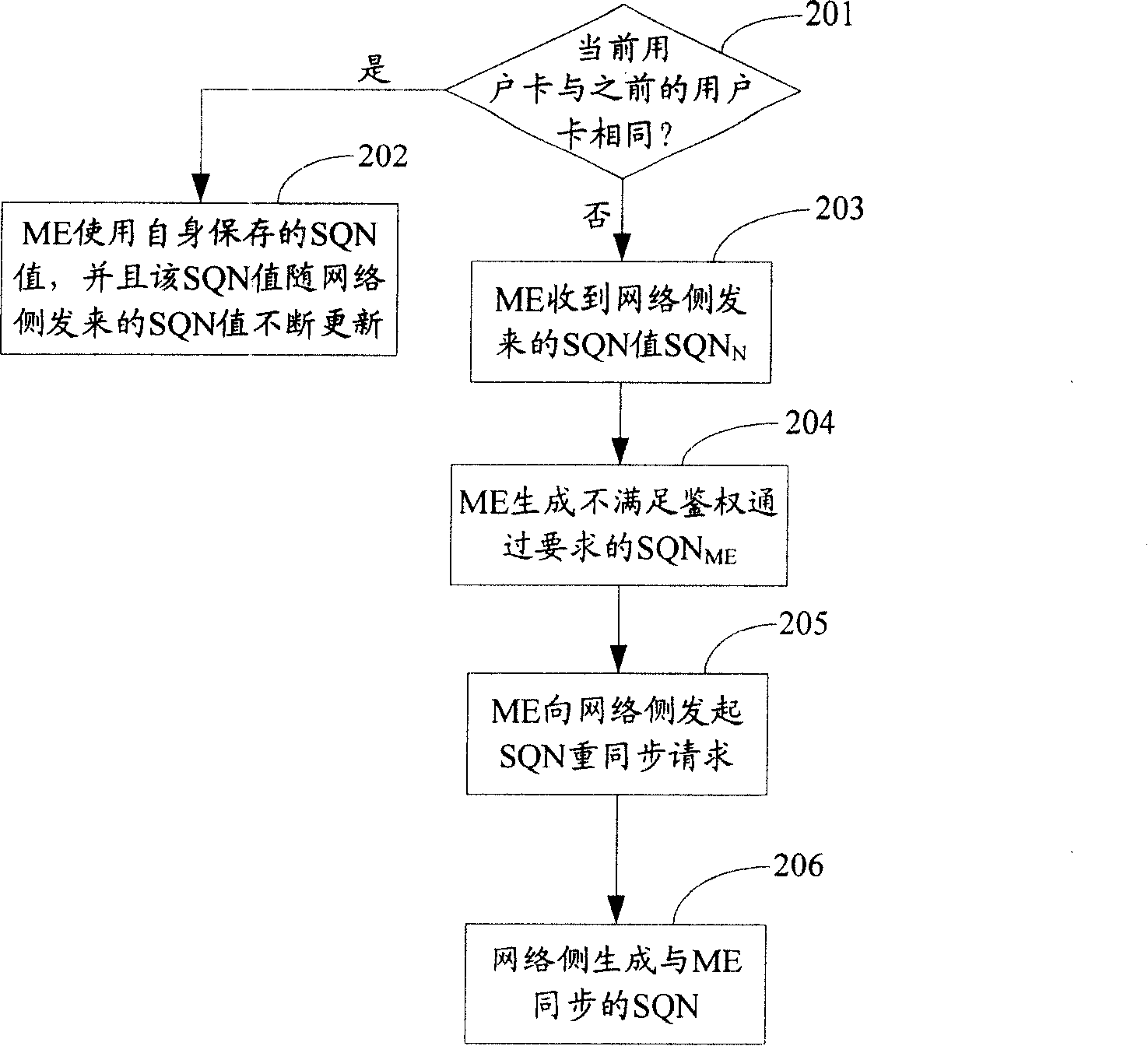
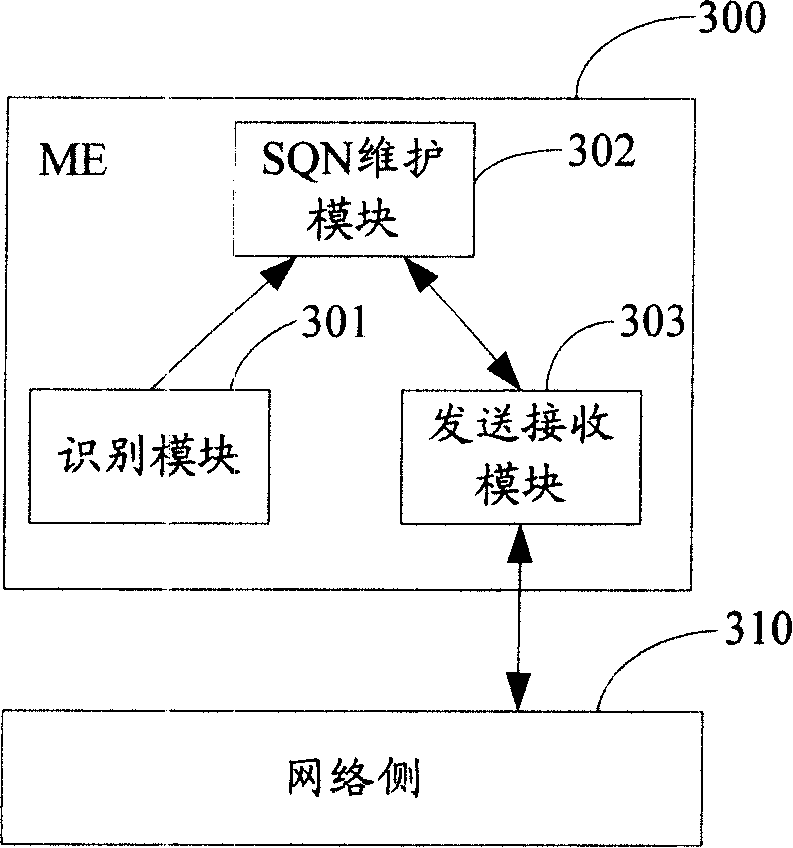
[0020] The basic idea of the embodiment of the present invention is: when the ME determines that the current user card is different from the previous user card, it generates an SQN that does not meet the requirements for passing the authentication, and initiates a SQN resynchronization request to the network side; the network side resynchronizes according to the received SQN Request to generate a SQN synchronized with the ME as the SQN on the network side.
[0021] During specific implementation, there are many methods for the ME to generate the SQN that does not meet the requirements for passing the authentication. Only two implementations are listed below. 1: First generate a random SQN value, and then use the SQN value from the network side to adjust the random SQN value. If the SQN value does not meet the authentication requirements, perform the operation of initiating a SQN resynchronization request to the network side ; Otherwise, regenerate an SQN value until the SQN...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com