Message processing method and system
A message processing and message technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as IPSec configuration difficulties, data packet misidentification, and data packet discarding, so as to enhance system security and reliability , good processing effect, and the effect of resisting replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
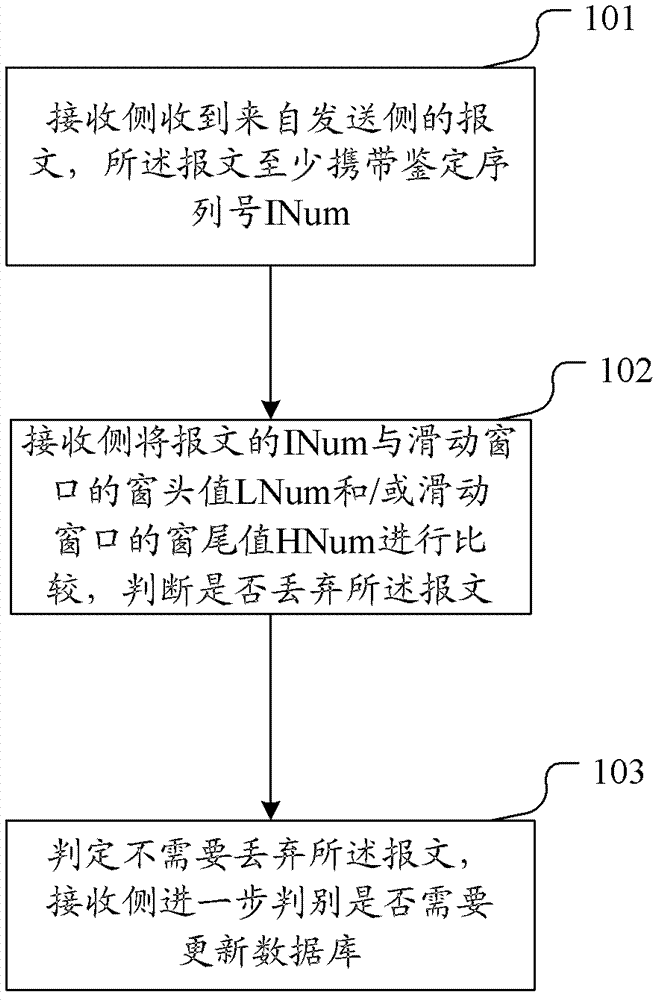
[0106] Taking the implementation of resisting replay attacks in an intermediate system to intermediate system (IS-IS) routing environment as an example, this embodiment can realize the function of resisting replay attacks by extending the TLV segment in the IS-IS message. Specifically, you can Add the identification serial number IdentifyNumber (INum) to the TLV, and set the sliding window window head value LowNumber (LNum) and the sliding window window tail value HighNumber (HNum) to resist replay attacks. The movement of the sliding window is based on the window minimum value moving, and the size of the sliding window is not fixed, the embodiment of the present invention can also implement the anti-replay attack function well in the case of packet delay.
[0107] This embodiment includes the following steps:
[0108] 1. When the specified intermediate system in the broadcast network or the sender in the point-to-point network sends a new message, INum increases by 1. After t...
Embodiment 2
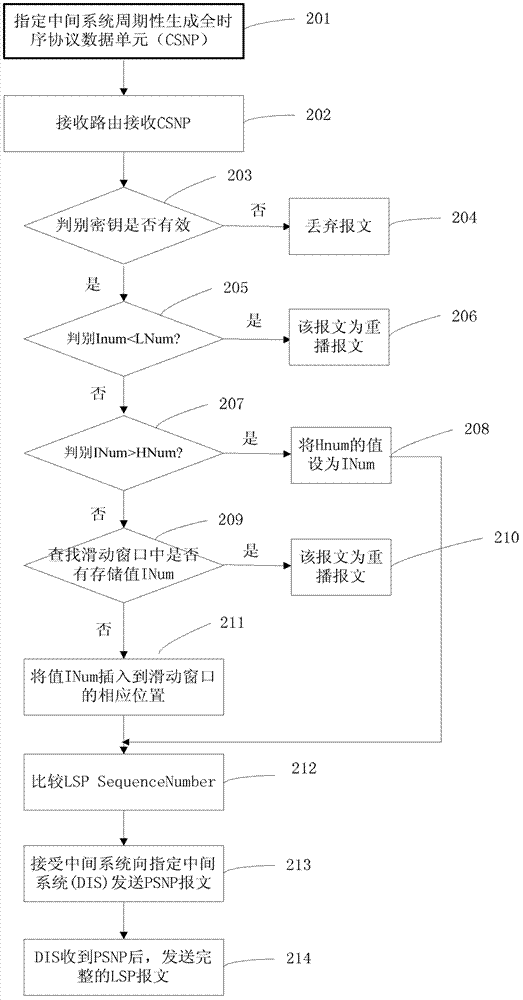
[0131] In this embodiment, in the broadcast network, the router uses CSNP to ensure the integrity of the link state database, and resists the replay attack through the method of the present invention. figure 2 It is a schematic flow diagram of the method of Embodiment 2 of the present invention, such as figure 2 As shown, the process includes the following steps:
[0132] Step 201: In the broadcast network, specify the intermediate system to periodically send the full timing protocol data unit (CSNP), and each time a new message is generated, its IdentifyNumber (INum) is increased by 1; if a new system is established, then generate The INum of the first CSNP message is manually configured, the value of the receiving route LNum is smaller than the value of INum, and a minimum window size is preset, the value of HNum is the sum of LNum and the window size value minus 1, and preset A threshold is T.
[0133] Step 202: In the broadcast network, the CSNP message is flooded to e...
Embodiment 3
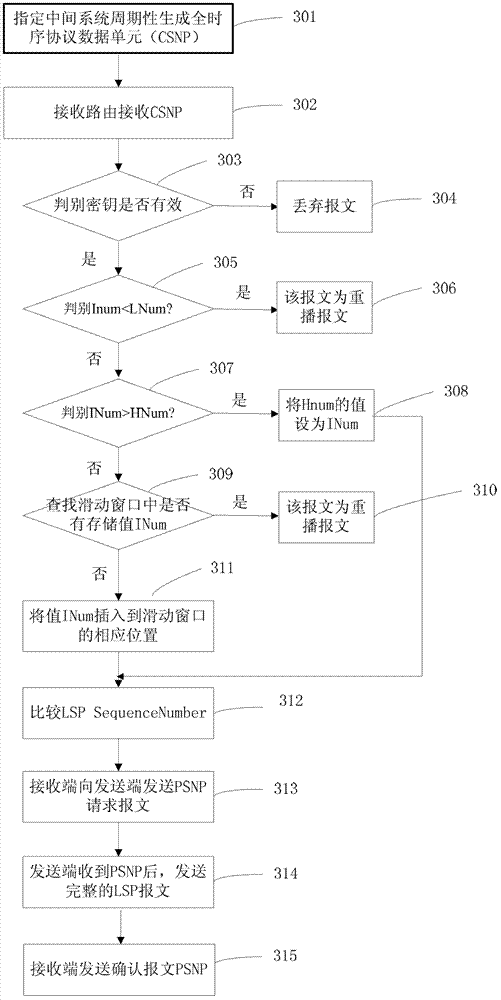
[0155] In this embodiment, in the point-to-point network (P2P), the router will not periodically send the CSNP message, the CSNP message will only be sent once when the link is activated, and the routers at both ends of the link will send the CSNP message to Describes the summary information of all LSPs in the local link state database. During CSNP transmission, the method of the invention resists replay attacks. image 3 It is a schematic flow chart of the method of Embodiment 3 of the present invention, such as image 3 As shown, the process includes the following steps:
[0156] Step 301: In the P2P network, the link sending end sends a full sequence protocol data unit (CSNP), and each time the link end sends a new message, its IdentifyNumber (INum) increases by 1; if a new system is established, Then the INum of the first CSNP message generated is manually configured; and the value of the receiving route LNum is smaller than the value of INum, and a minimum window size i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com