Lightweight blockchain communication authentication device and method for detecting data tamper-proofing
A technology for detecting data and authentication methods, applied in secure communication devices, digital data protection, data processing applications, etc., can solve the problems that the encryption process is easy to be cracked and consumes a lot of money, so as to speed up transaction processing and dissemination, and prevent tampering , to ensure the effect of credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
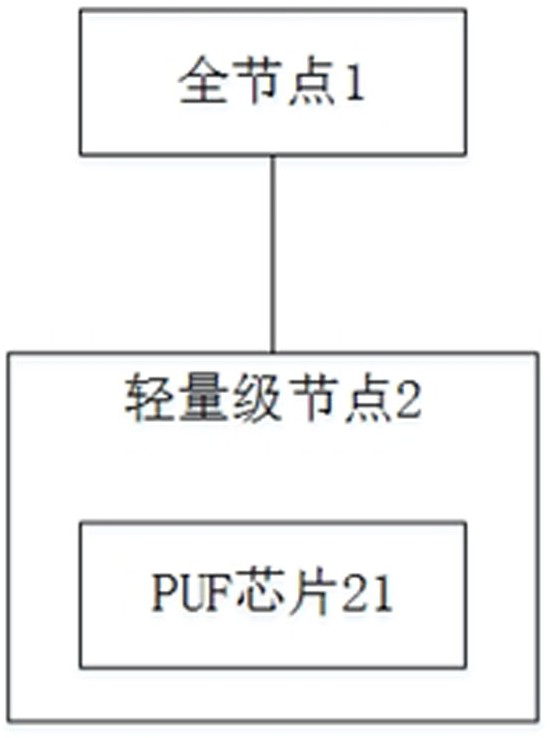
[0037] like figure 1 As shown, a lightweight blockchain communication authentication device for detecting data tampering, including: full node 1 and lightweight node 2, full node 1 is the genesis block and derived from the genesis block Each full node 1 communicates directly with at least one lightweight node 2, and each lightweight node 2 is equipped with a PUF chip 21, and each PUF chip 21 is unique. In this embodiment, a block is a full node 1, and a full node 1 can be connected to one lightweight node 2, or multiple lightweight nodes 2, and the lightweight node 2 can be an IoT device , such as monitoring equipment. The PUF chip 21 is set inside the lightweight node, and each PUF chip has an unpredictable, unique, and unclonable "electronic fingerprint", that is to say, the PUF chip on each lightweight node is unique of.
[0038] In this embodiment, full node 1 is a node with a complete blockchain account book. The full node needs to occupy memory to synchronize all bloc...
Embodiment 2
[0040] like figure 2 As shown, a light-weight blockchain communication authentication method for detecting data tamper-proof, using the device of Embodiment 1, taking the authentication process between a full node and a light-weight node as an example, specifically includes the following step:
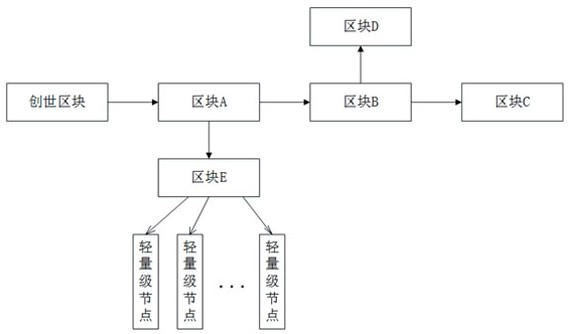
[0041] S1: Starting from the genesis block, generate at least one first new block, use the first new block as the parent block to generate at least one second new block, and use the second new block as the parent block to generate at least one third new block , and so on to form a directed acyclic graph structure, the creation block, the first new block, the second new block and the third new block are all full nodes.
[0042] It should be noted that if a directed graph cannot start from a certain vertex and return to the point through several edges, then this graph is a directed acyclic graph (DAG graph). For example, if figure 2 As shown, starting from the genesis block, a new b...
Embodiment 3
[0064] like Image 6 As shown, an application system of a lightweight block chain communication authentication method for detecting data tampering, including a smart bracelet 101, a microprocessor 102, an FPGA development board 103 and a computer 104, the smart bracelet 101 and a micro The processors 102 are connected by wireless communication, the FPGA development board 103 is connected to the microprocessor 102 through a serial port, the FPGA development board 103 is provided with a PUF chip, and the microprocessor 102 is connected to the computer 104 by communication. The smart bracelet 101, the microprocessor 102, and the FPGA development board 103 together form a lightweight node, and the computer 104 simulates the full node. The smart bracelet 101 is equipped with hardware such as a temperature sensor, a heart rate sensor, and GPS. The health data such as the temperature, heart rate, and location of the user detected by the smart bracelet are transmitted to the microproc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com