Trusted measurement and control network authentication method based on double secret values and chaotic encryption
A chaotic encryption, measurement and control network technology, applied in the field of identity authentication, can solve problems such as lengthy certificate verification structure, difficult password operation, and actual verification efficiency limitation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
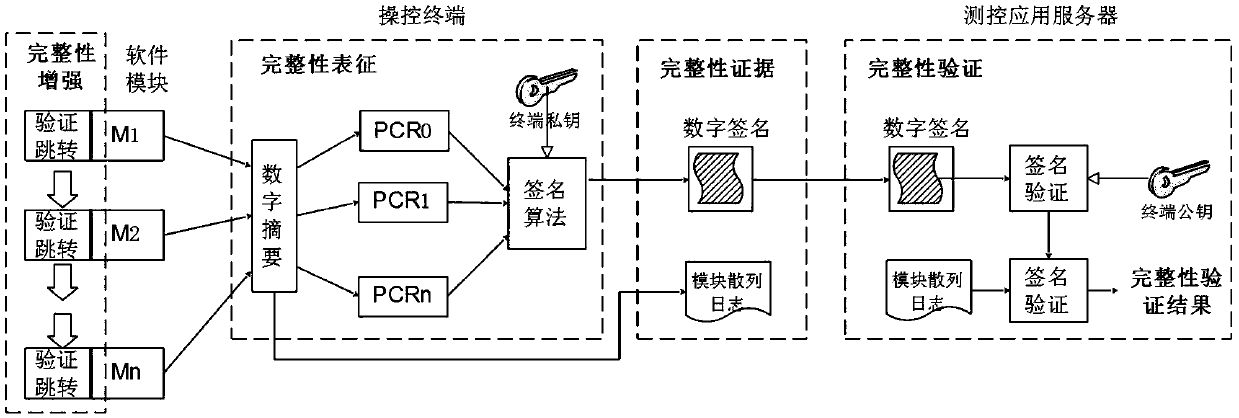
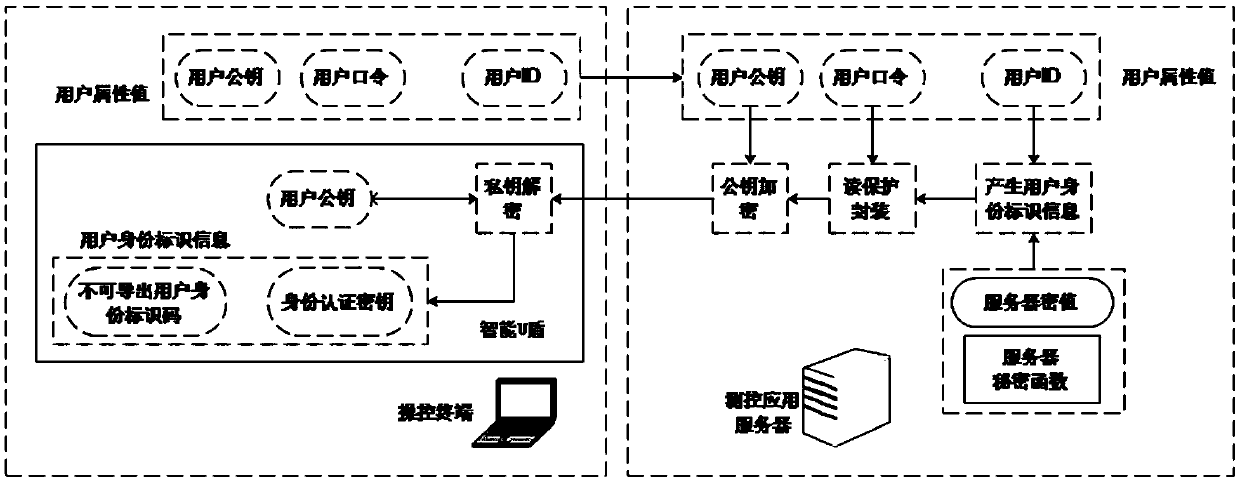
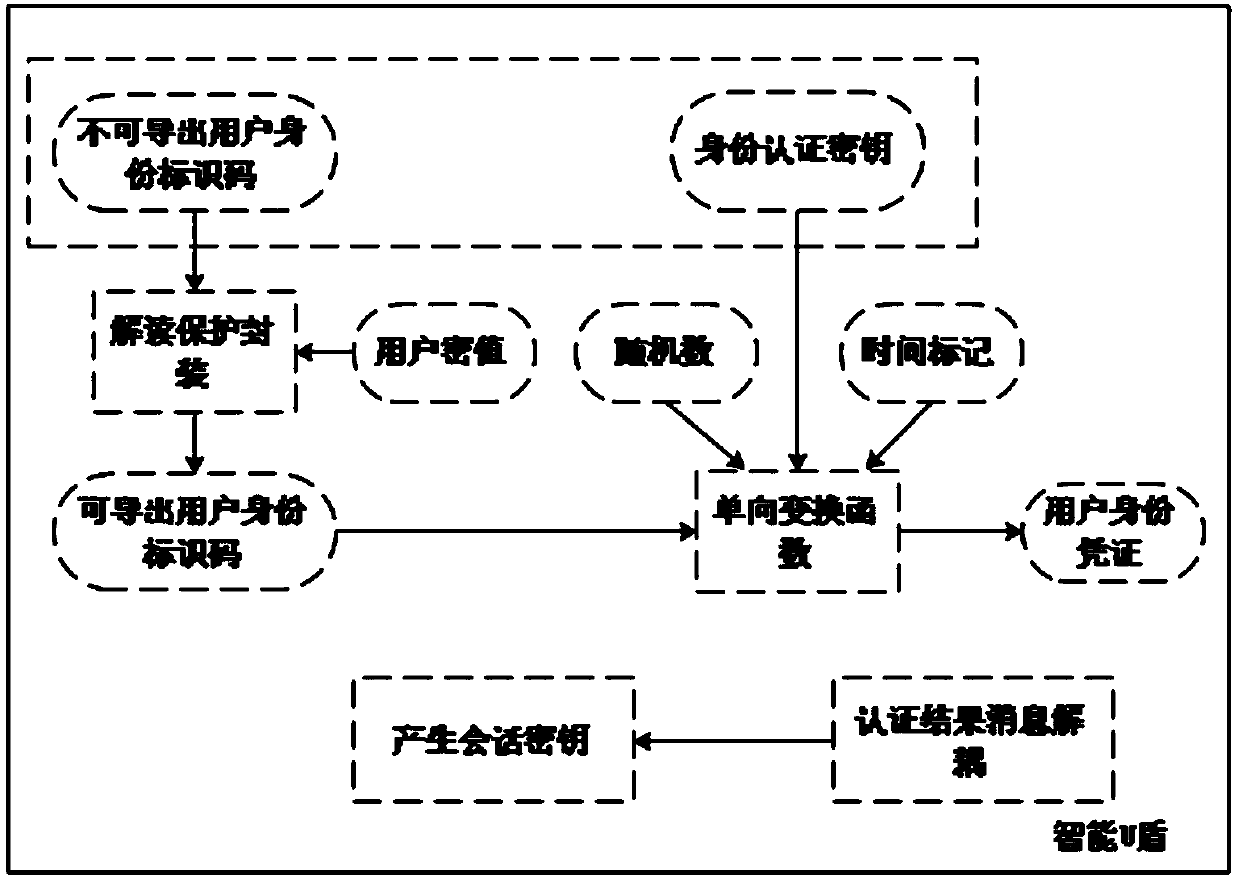
[0054] Such as Figure 6As shown, the present invention relates to a trusted measurement and control network authentication technology method based on double secret values and chaotic encryption algorithms. The specific method is to use double secret Value and chaotic public key cryptography realize identity authentication and key negotiation process, realize secure transmission and verification of user identity certificates, and thus build a safe and reliable data transmission channel. The identity authentication method in the present invention includes multiple links such as secure generation of user identity identification, read protection encapsulation, secure transmission, key negotiation, etc., and a unique and confidential cryptographic function is used in each link to generate data securely , so as to ensure the security of authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com