A two-factor authentication key agreement protocol for multi-gateway wireless sensor networks
A wireless sensor and two-factor authentication technology, applied in the field of user identity authentication and session key agreement agreement, can solve the problems of wireless sensor network and user threats, few authentication and key agreement agreements, wireless sensor network security loopholes, etc., to achieve Effect of untraceability protection, anonymity protection, and high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described below in conjunction with the accompanying drawings.
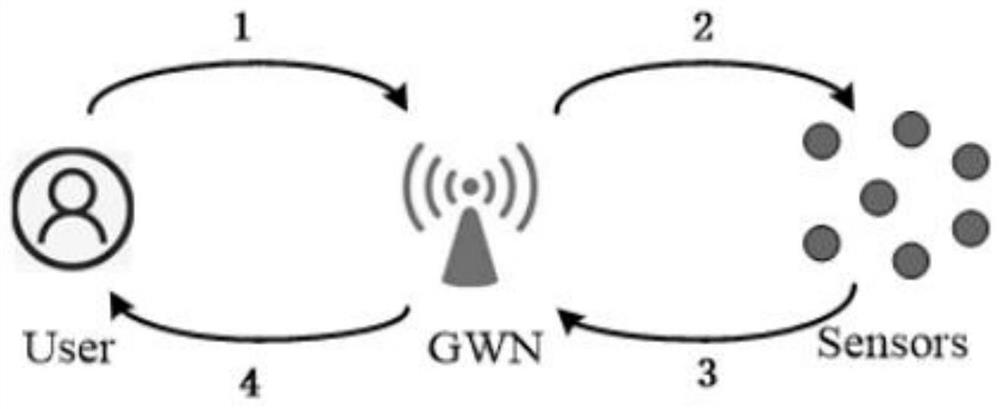
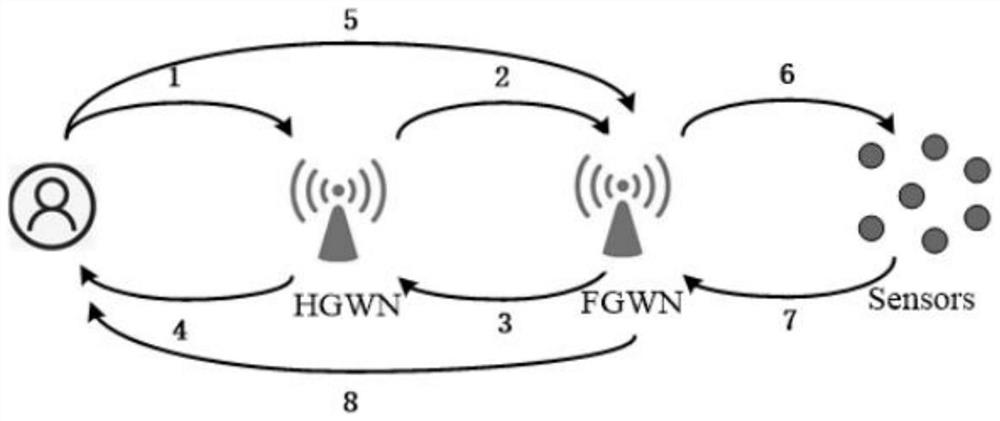
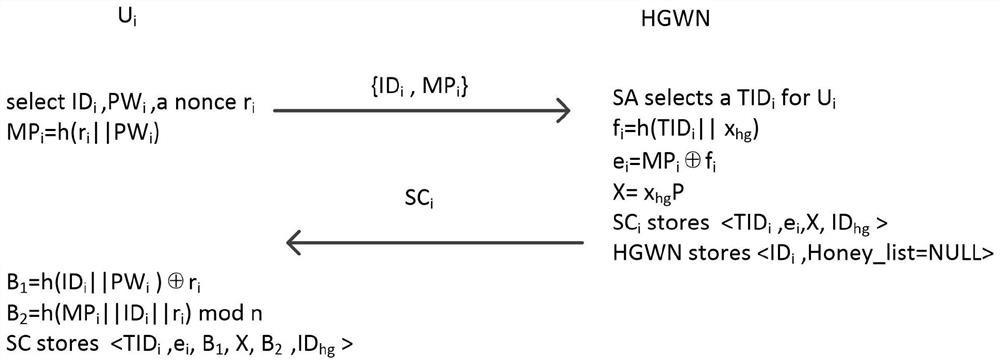
[0064] FIG. 1 is a communication model diagram of a multi-gateway wireless sensor network in the present invention. The multi-gateway communication model includes three types of entities, sensor nodes, gateway nodes and users. Gateway nodes are divided into home gateway nodes and external gateway nodes. For users and sensor nodes, the gateway nodes that are relatively close to them are called home gateway nodes, and the rest of the gateway nodes are called external gateway nodes. After the sensors and gateway nodes are placed, they are stationary. In wsn, the cost of sending and receiving messages increases with distance. Sensor nodes have the characteristics of low memory, low battery power, low bandwidth, and limited computing power. The gateway node has strong computing power. So we should reduce the computational load of sensor nodes. Sensor nodes are used fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com