Method and system for implementing end-to-end media stream cryptographic key negotiation
A technology of key negotiation and media streaming, applied in transmission systems, usage of multiple keys/algorithms, and key distribution, it can solve the problems of inability to meet legal interception, inability to obtain keys, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
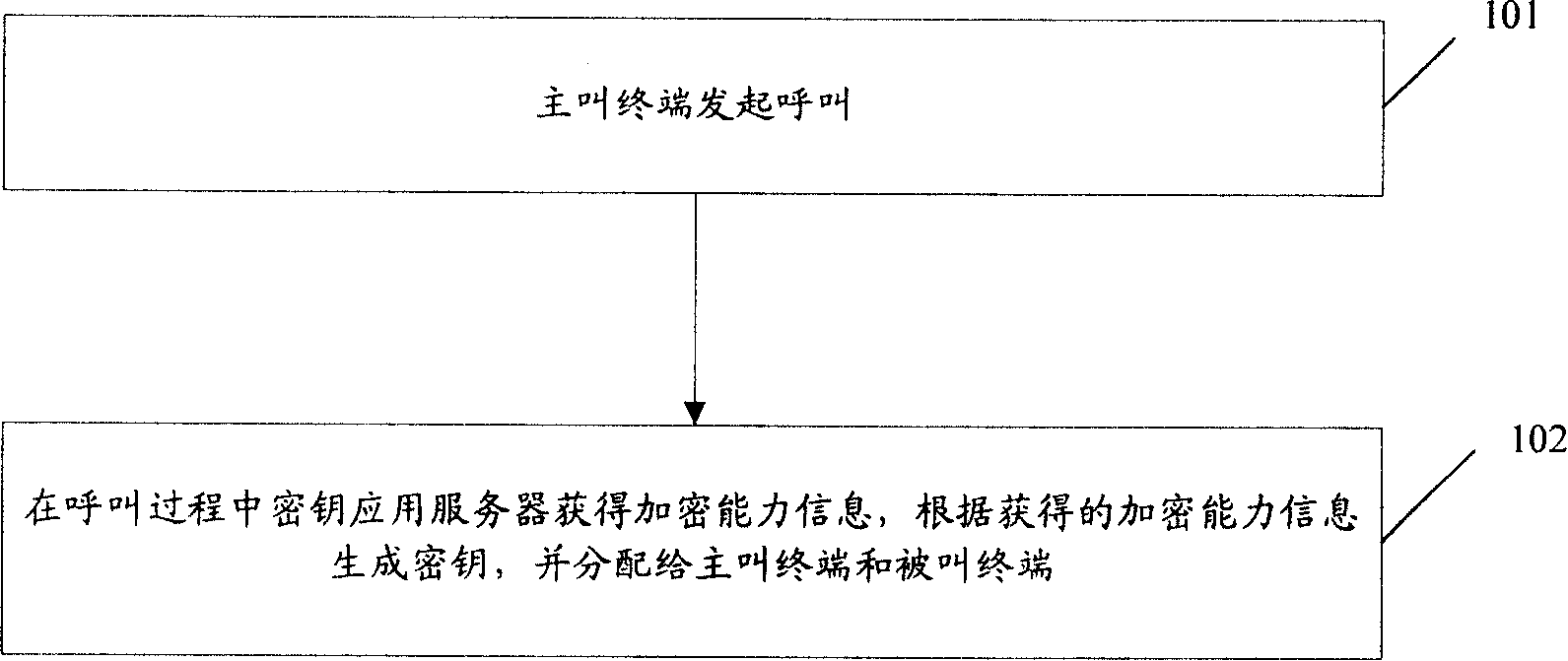
[0105] In this embodiment, the encryption service is a value-added service, and both the calling terminal and the called terminal support the encryption capability, and both have signed a contract in advance; in this embodiment, the call service entity on the calling side is the call session control function Entity (S-CSCF), the call service entity of the called side is the called side S-CSCF; the key application server of the calling side and the key application server of the called side are both SIP application servers; the call response message sent by the calling terminal The SIP message header in contains the precondition negotiation.
[0106] figure 2 is a schematic diagram of message flow in this embodiment. Such as figure 2 As shown, the method for implementing end-to-end media stream key negotiation in this embodiment includes the following steps:
[0107] Step 201: the calling terminal sends a call request message to the calling side S-CSCF.
[0108] The call r...
Embodiment 2
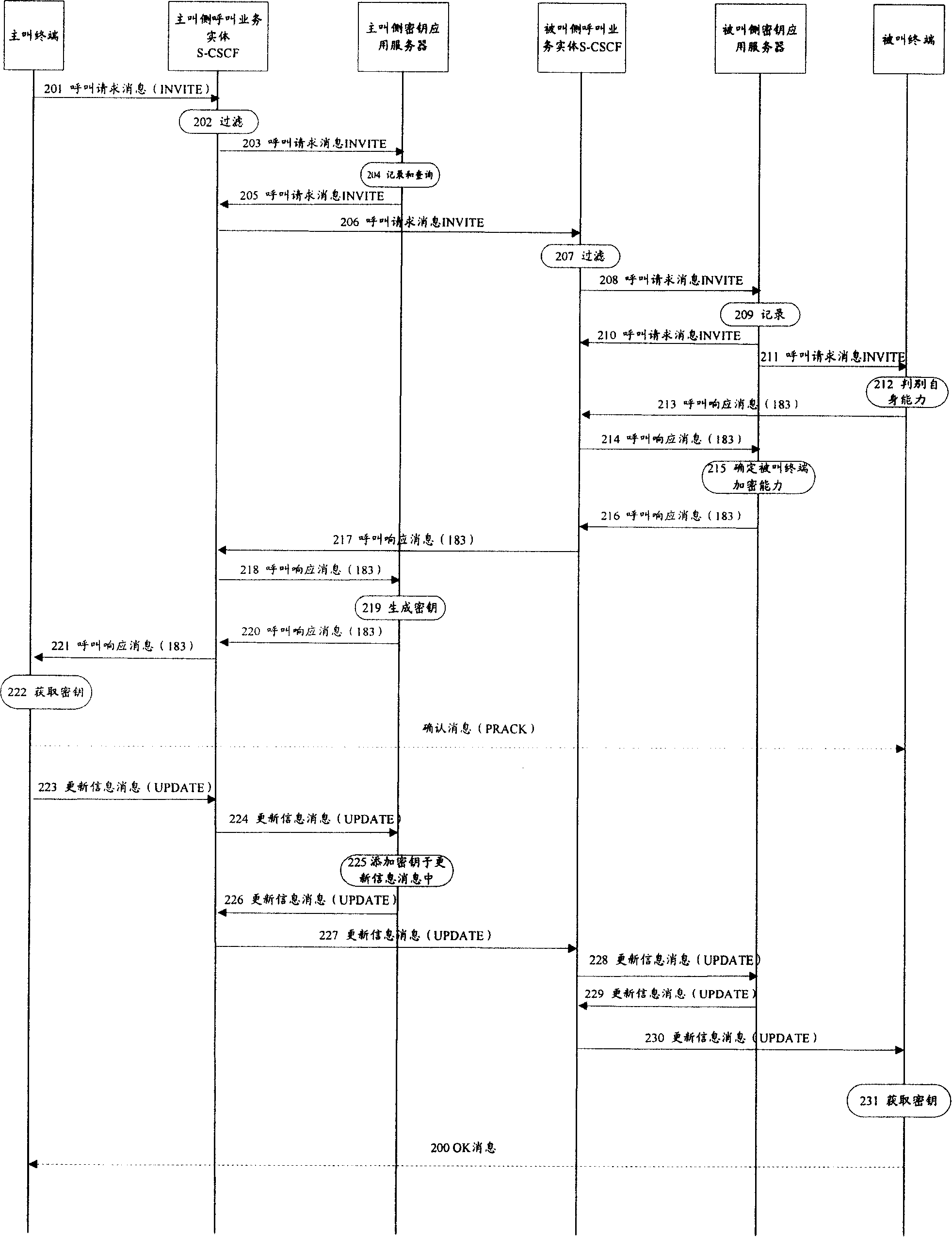
[0176] In this embodiment, the encryption service is a value-added service. Both the calling terminal and the called terminal support the encryption capability, but only the called terminal has signed a contract; CSCF, the call service entity of the called side is the called side S-CSCF; the key application server of the calling side and the key application server of the called side are both SIP application servers; the SIP message header in the call response message sent by the calling terminal does not include precondition negotiation.
[0177] image 3 is a schematic diagram of message flow in this embodiment. Such as image 3 As shown, the method for implementing end-to-end media stream key negotiation in this embodiment includes the following steps:
[0178] Steps 301 to 303 are the same as steps 201 to 203 in Embodiment 1, and will not be repeated here.
[0179] Step 304: The key application server on the calling side records the encryption capability infor...
Embodiment 3
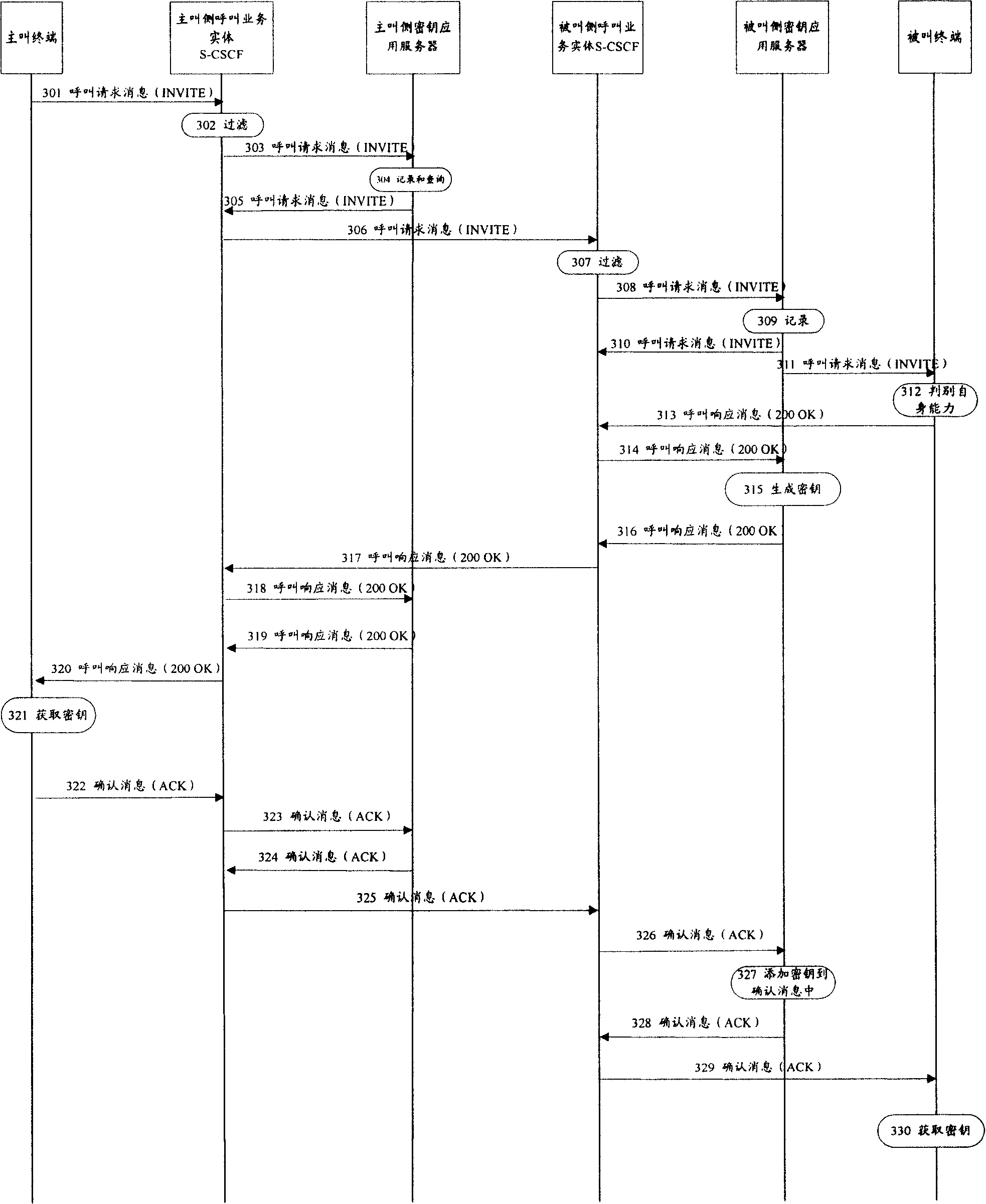
[0195] In this embodiment, the encryption service is regarded as a basic service, and the key application server obtains the encryption capability information from the call response message; The entity is the called side S-CSCF; the calling side key application server and the called side key application server are both SIP proxy mode units in the S-CSCF; the SIP message header in the call response message sent by the calling terminal does not contain Contains precondition negotiation.
[0196] Figure 4 is a schematic diagram of message flow in this embodiment. Such as Figure 4 As shown, this embodiment includes the following steps:
[0197] Steps 401 to 409: The calling terminal sends a call request message to the called terminal. During the sending process, when the calling service entity on the calling side receives the call request message, it filters the call request message according to the filter criteria obtained in advance , and send the call request mess...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com