Authentication device for providing authentication to users accessing by terminal
A terminal access and authentication technology, applied in the field of communication, can solve the problems of attacking user key security threats, user interference, etc., and achieve the effect of good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
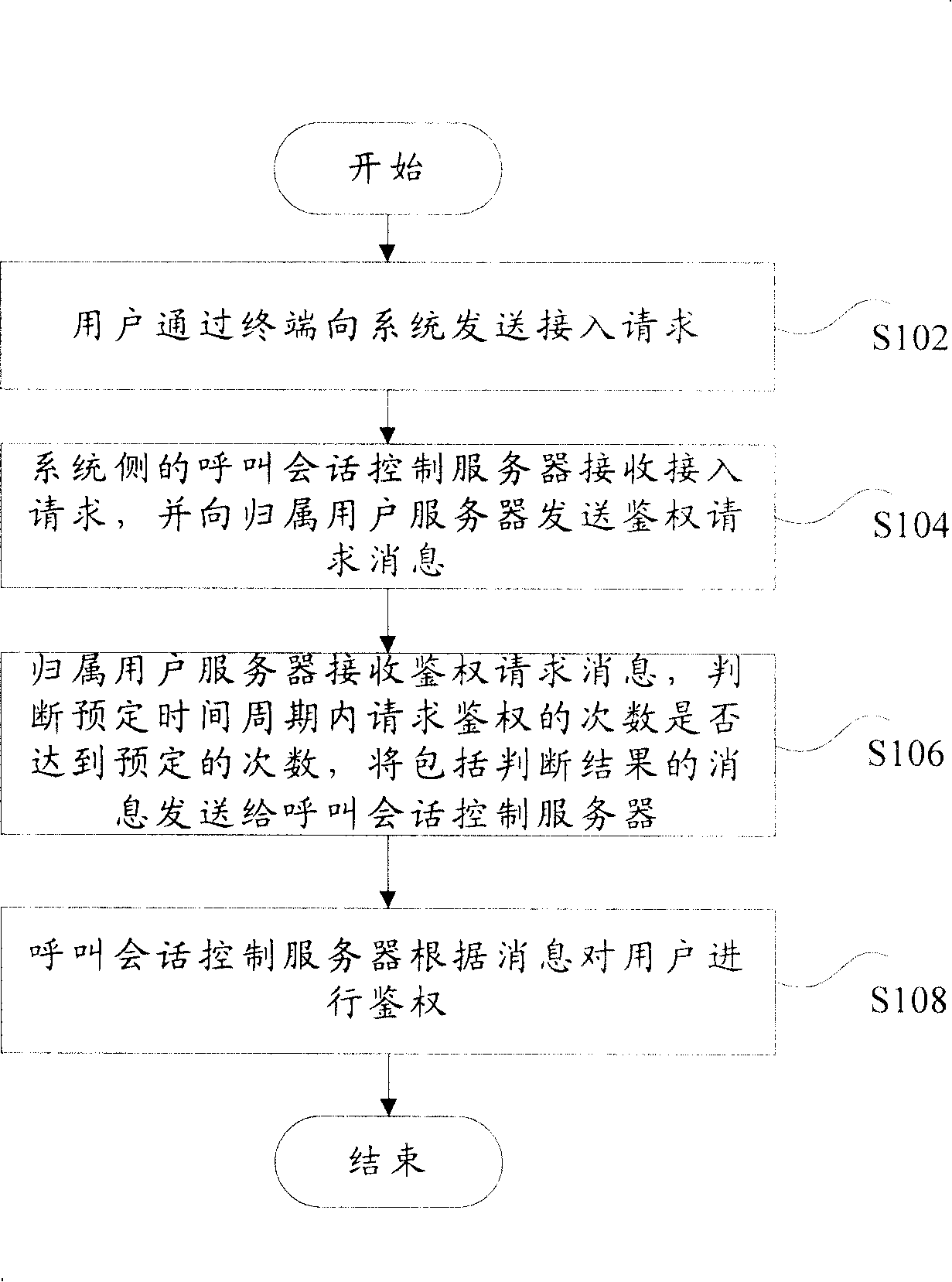
[0025] First, refer to figure 1 with figure 2 The first embodiment of the present invention is described. figure 1 Is a flowchart of a communication system authentication method according to the first embodiment of the present invention, figure 2 It is a detailed flowchart of the authentication method of the communication system according to the first embodiment of the present invention.
[0026] Such as figure 1 As shown, the communication system authentication method according to the first embodiment of the present invention includes the following steps: step S102, the user sends an access request to the system through the terminal; step S104, the call session control server on the system side receives the access request and sends The home subscriber server sends an authentication request message; step S106, the home subscriber server receives the authentication request message, judges whether the number of authentication requests within a predetermined time period reaches ...
no. 2 example
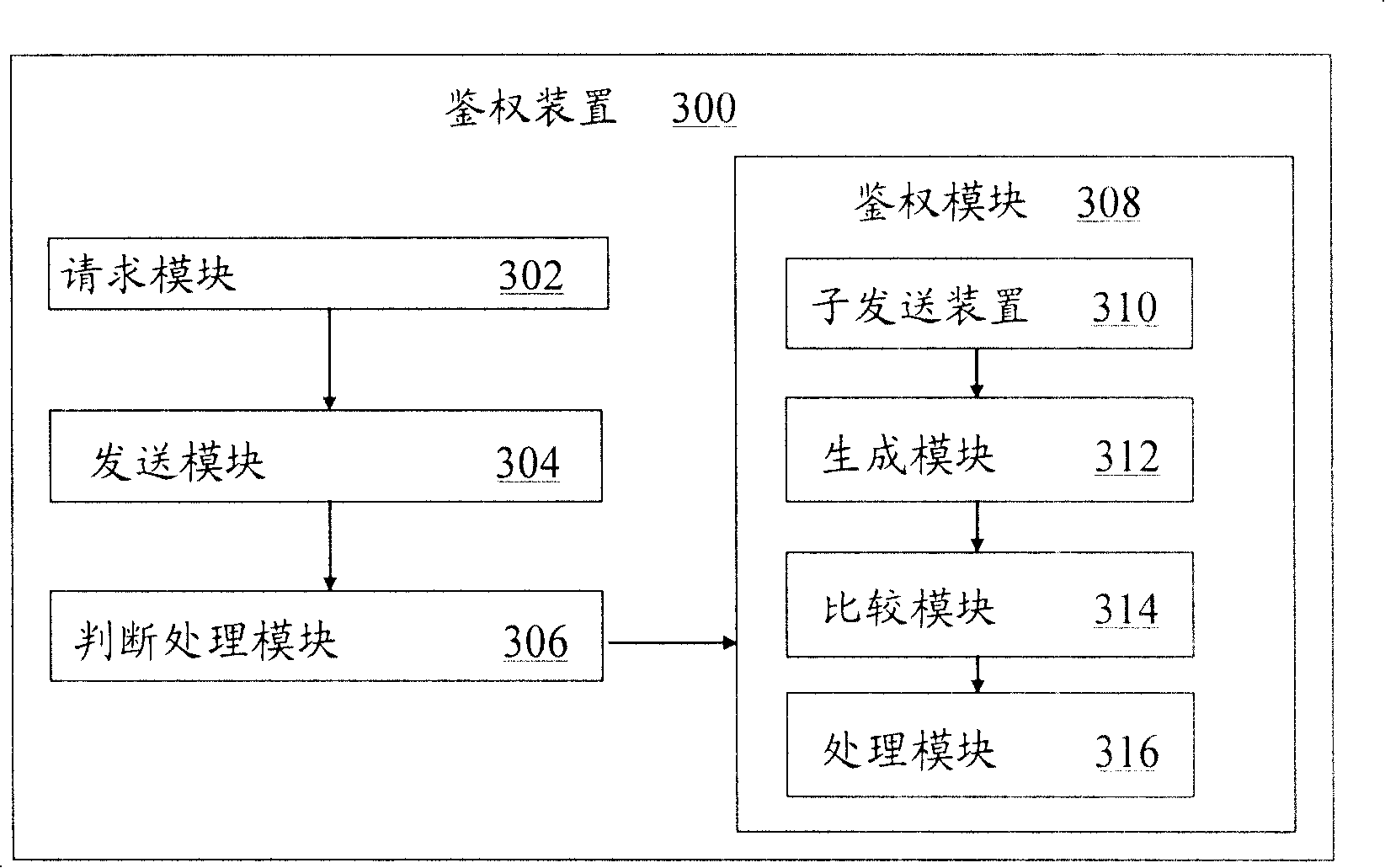
[0035] The following will refer to image 3 The second embodiment of the present invention is described. image 3 It is a block diagram showing the configuration of the authentication device 300 in the communication system according to the second embodiment of the present invention.
[0036] Such asimage 3 As shown, the authentication device 300 in the communication system according to the second embodiment of the present invention includes: a request module 302, which is used to enable a user to send an access request to the system through a terminal; and a sending module 304, which is used to enable a call session on the system side The control server receives the access request and sends an authentication request message to the home user server; the judgment processing module 306 is used to make the home user server receive the authentication request message and judge whether the number of authentication requests within a predetermined time period reaches the predetermined num...
no. 3 example
[0044] The following will refer to Figure 4 , Figure 5 , Figure 6 ,with Figure 7 The third embodiment of the present invention is described. Figure 4 Is a block diagram of a system configuration example to which the present invention is applied, Figure 5 Yes Figure 4 The flow chart of normal user registration in the system shown, Figure 6 Yes Figure 4 The flow chart of malicious registration of illegal users in the system shown, Figure 7 Is in image 3 The flow chart of the present invention is implemented in the system shown.
[0045] In the following, an IMS system is taken as an example to describe the embodiments of the present invention.
[0046] Such as Figure 4 As shown, the mobile or fixed terminal UE 11 accesses the IMS (IP Mutimedia Subsystem) network, and is required to be authenticated during the registration process;
[0047] The access proxy server P-CSCF 12 implements a user agent function, which processes or forwards received requests and services. In the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com