Method and apparatus for negotiating internet cryptographic key exchanging safety coalition existence period
A life cycle and key exchange technology, applied to electrical components, transmission systems, etc., can solve problems such as no response terminal, communication interruption, and IKESA failure, etc., to achieve the effect of easy implementation and simple process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
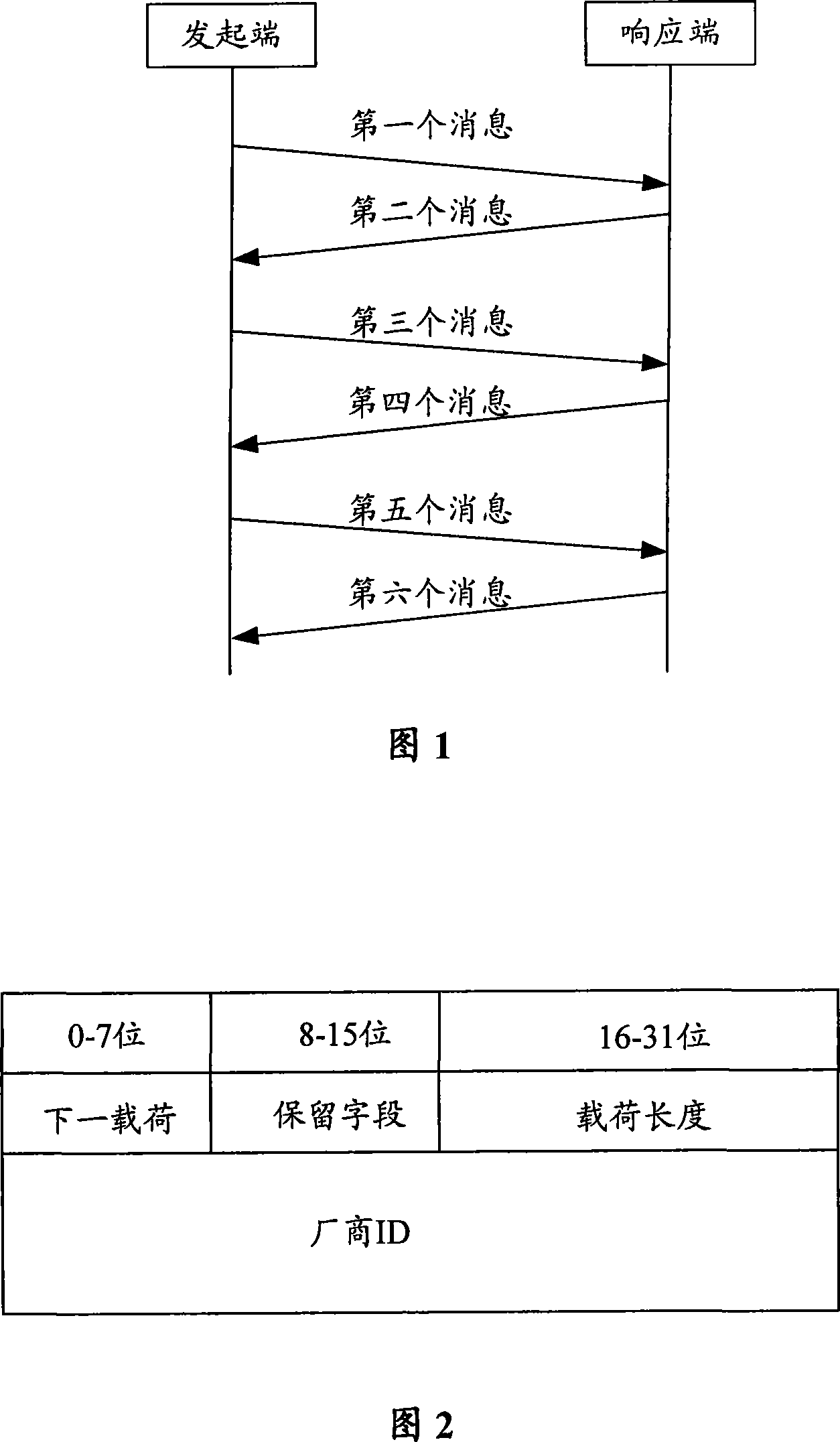
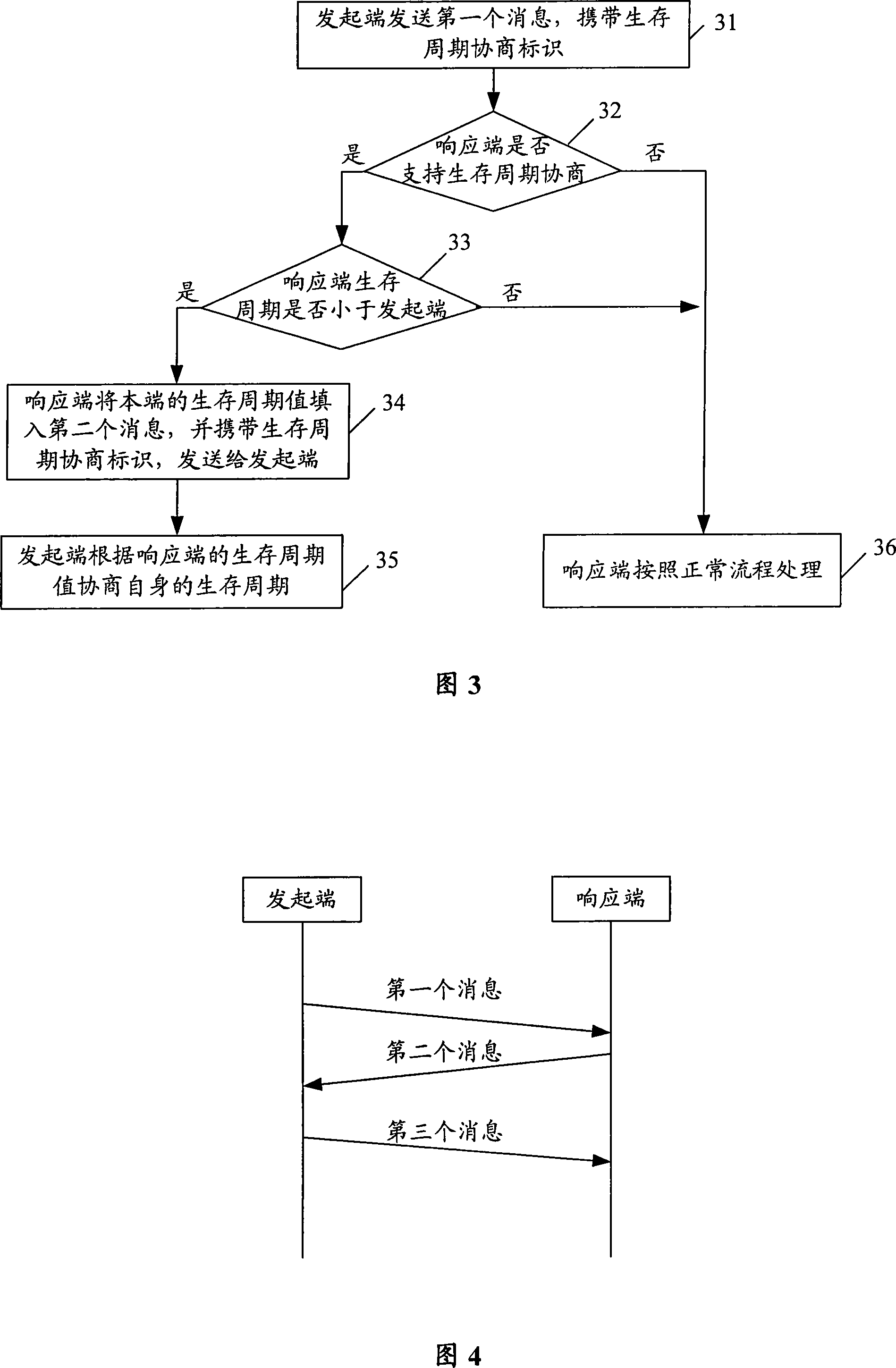
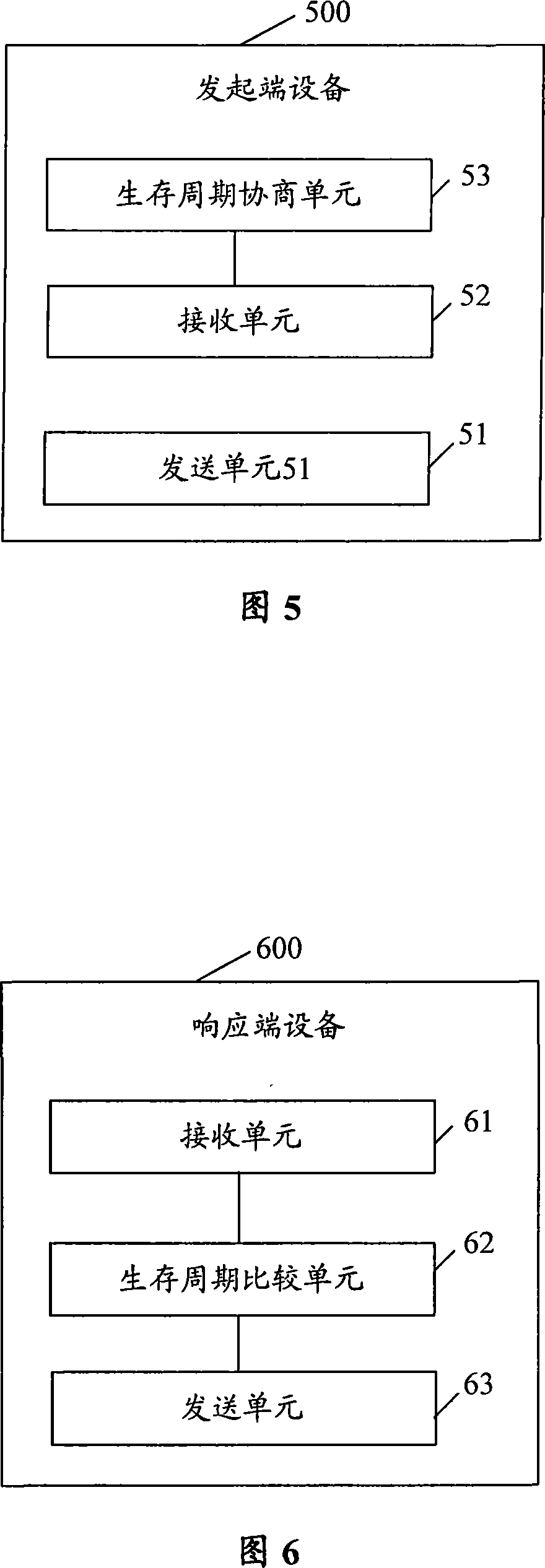
[0059] The main idea of the present invention is: when the IKE SA lifetime of the responder and the initiator are inconsistent, when the IKE SA lifetime of the responder in IKE negotiation is shorter than the IKE SA lifetime of the initiator, the IKE SA lifetime of the responder is transmitted during the IKE negotiation process. The SA lifetime allows the initiator to know the IKE SA lifetime of the responder, so that the IKE SA lifetime of the initiator can be negotiated to a smaller value during IKE SA negotiation. The present invention will be described in detail below through specific embodiments in conjunction with the accompanying drawings.
[0060] In the embodiment of the present invention, the IPSec policy is pre-configured on the corresponding interface between the initiator and the responder, and the traffic flowing through the interface of the initiator triggers IKE negotiation and establishes an IPSec SA. Specifically, the initiating end and the responding end m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com