Computer lock and safety case
A computer lock and computer technology, applied in the field of computer locks and security boxes, can solve the problems of insufficient security of computer locks and security boxes, and achieve the effects of enhanced security, convenient use, and enhanced reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
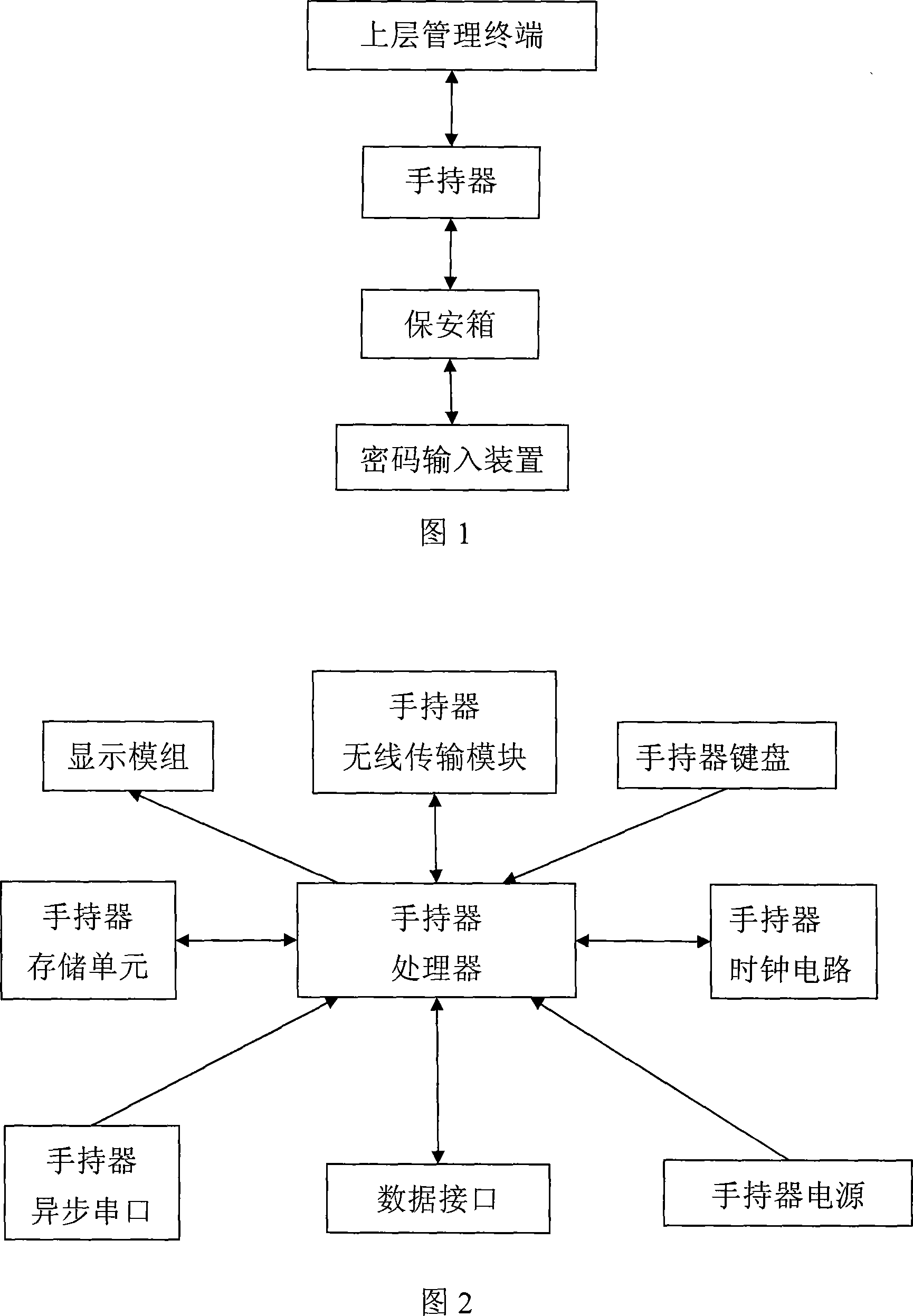
[0042] The security box management and control system of this specific embodiment is shown in Figure 1, including: an upper layer management terminal, a handheld device, a security box and a password input device.
[0043] The upper management terminal mainly includes a computer and upper management software running on the computer, which may also include a data storage server. The data storage server is used to store data, and it conducts two-way communication with the upper management terminal. The upper management terminal can obtain the required data from the data storage server, and can also transmit the data to the data storage server for storage. The data storage server is generally a dedicated server computer; for relatively small financial institutions, the data storage server can also share a computer host with the upper management terminal. It can also be considered that the upper-layer management terminal has a database associated with the upper-layer management s...
Embodiment 2
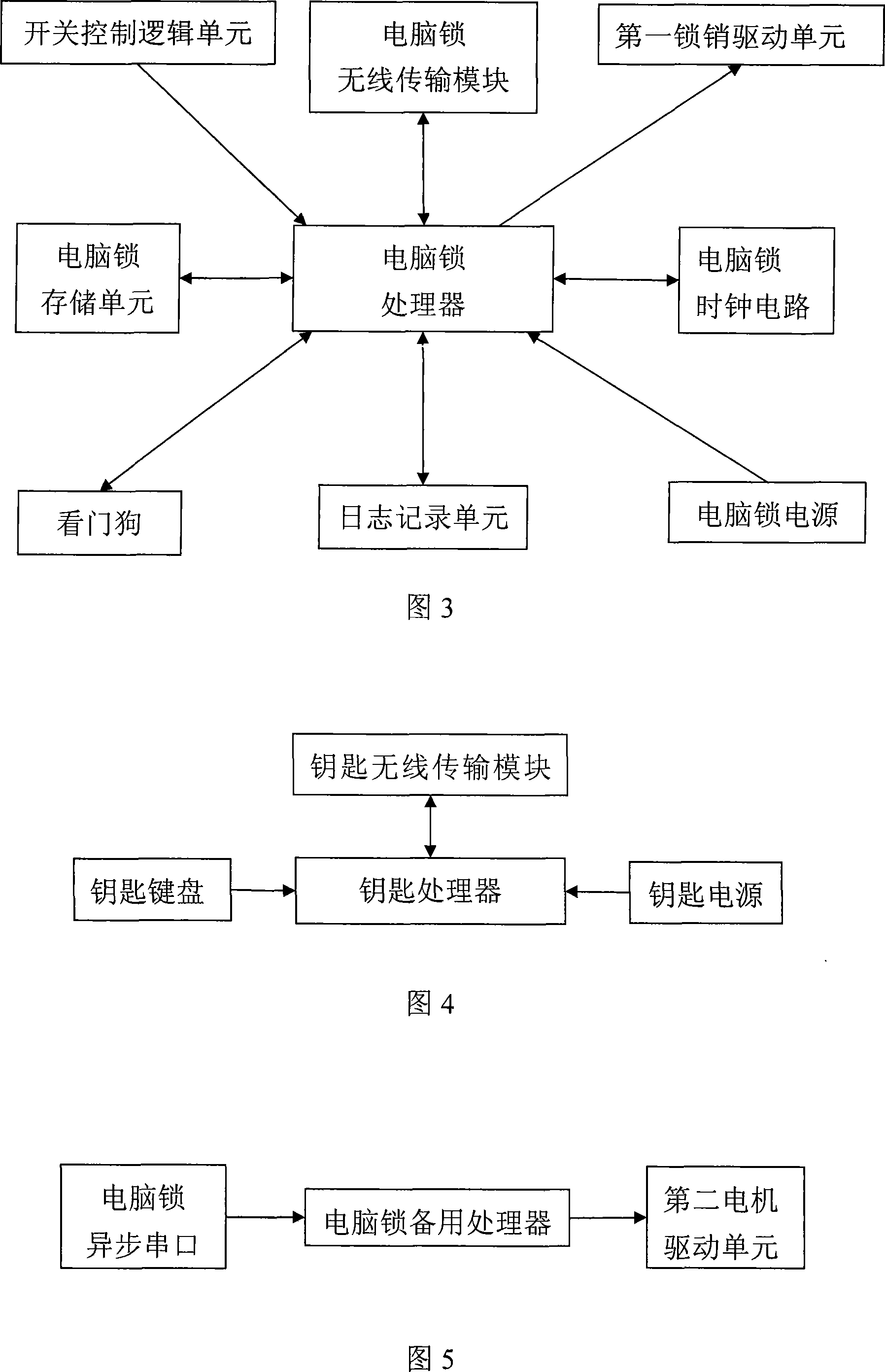
[0078] The difference between this specific embodiment and the first embodiment is that the computer lock of the security box also includes a backup system. Because the security box may often encounter falling and falling situations during on-site operation, the computer lock can also be opened through the backup system in the case of failure to open the box normally, so as to ensure that the use will not be seriously affected, and the reliability of the computer lock and the security box will be improved. .
[0079] The functional block diagram of the backup system is shown in Figure 5, including: a computer lock backup processor, a second lock pin drive unit and a computer lock backup interface. The spare interface of the computer lock is used to connect with the spare interface on the hand-held device, receive forced unlocking data and obtain power supply from the hand-held device.
[0080]Of course, before the upper-level management terminal needs to send the forced unloc...
Embodiment 3
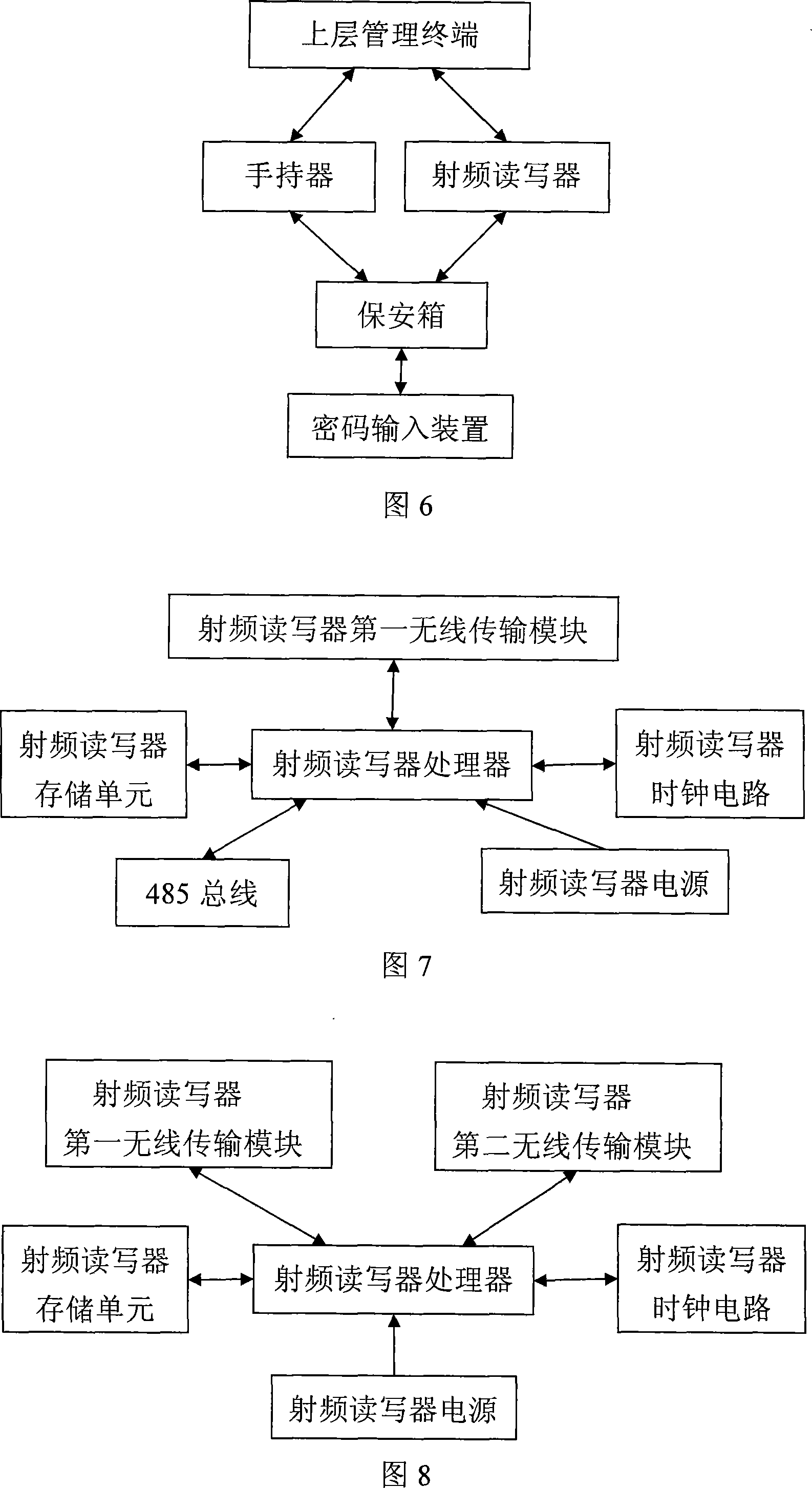
[0082] As shown in FIG. 6 , the difference between this embodiment and Embodiment 1 and Embodiment 2 is that a radio frequency reader is also included. The principle of the radio frequency reader is shown in Figure 7. Its core is a microprocessor. In order to show the difference, it is called the processor of the radio frequency reader. In addition, it also includes the wireless transmission module and storage The unit, the clock circuit and the power supply are referred to here as the first wireless transmission module of the RF reader, the storage unit of the RF reader, the clock circuit of the RF reader, and the power supply of the RF reader. In addition, the radio frequency reader in this specific embodiment also includes a 485 bus, which is used to connect multiple radio frequency readers in series and electrically connect with the upper management terminal. The first wireless transmission module of the radio frequency reader uses 2.4G Hz to communicate wirelessly with th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com