Method for processing safety warning and safety policy equipment
A security policy and security device technology, applied in the field of network security, can solve the problems of incompatibility, limit the use range of security device linkage security control module, reduce the use efficiency of security device and security control module, etc., to improve efficiency and simplify processing. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
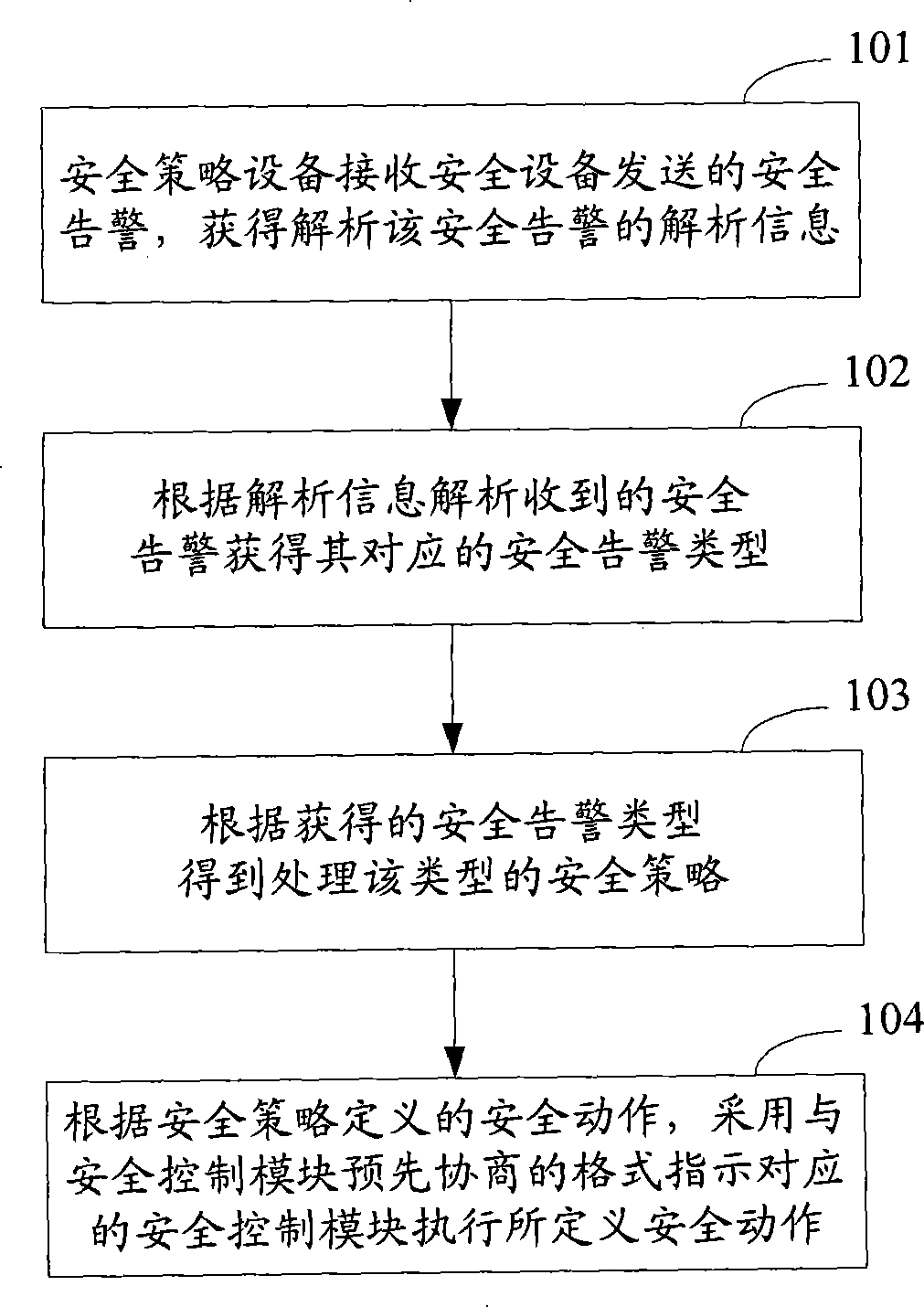
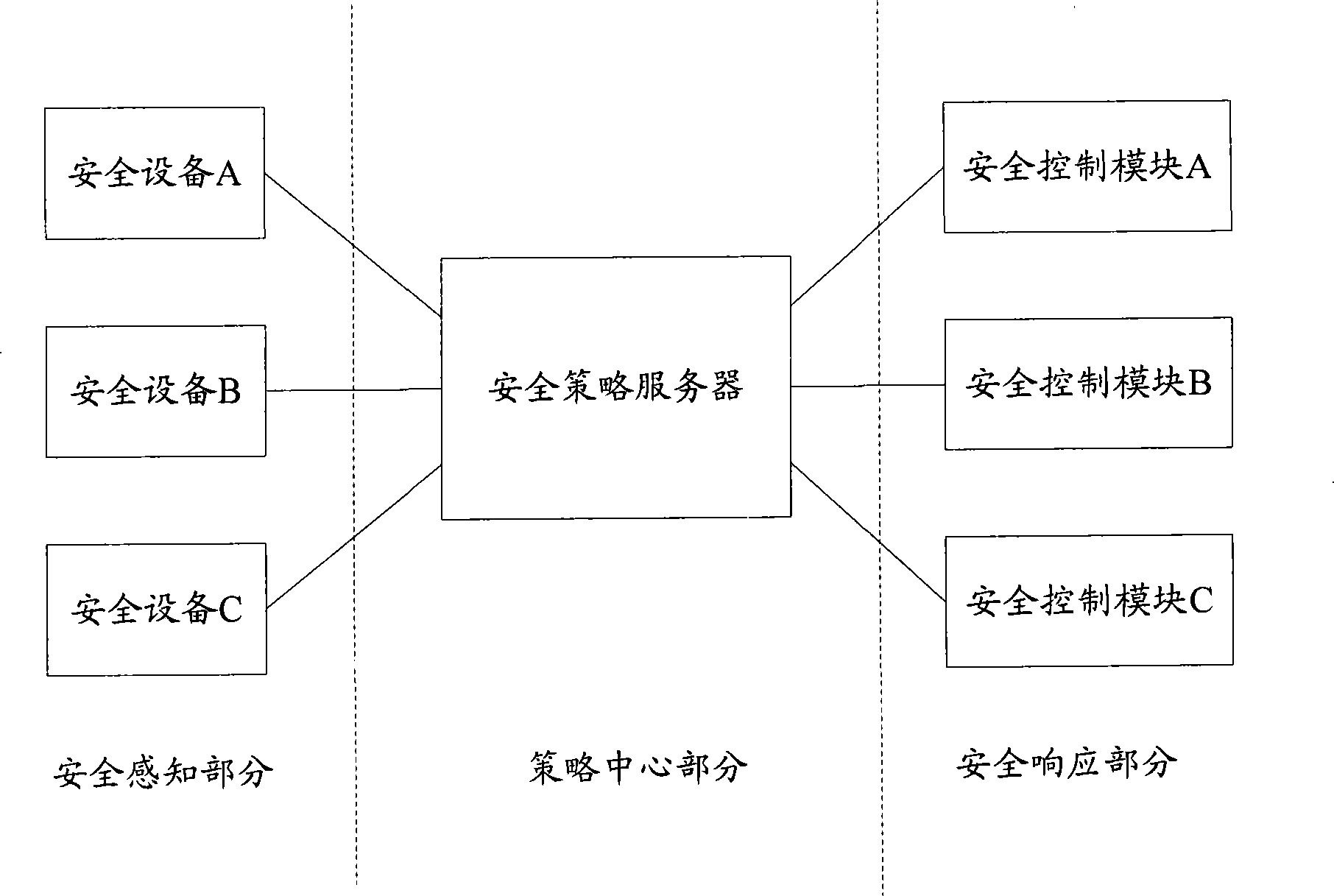
[0026] In order to achieve the purpose of the present invention, as long as the security policy device can analyze the security alarms from the security devices of various manufacturers, and use the format that each security control module can recognize to instruct it to perform security actions, the security device linkage security control module handles security alarms. method, it can be compatible with security devices and security control modules developed by various manufacturers.
[0027] see figure 1 , figure 1 It is an exemplary flowchart of the method of the present invention. Specifically include: in step 101, the security policy device receives the security alarm sent by the security device, and obtains the analysis information for analyzing the security alarm; in step 102, analyzes the received security alarm according to the analysis information to obtain its corresponding security alarm type; In step 103, according to the type of security alarm obtained, obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com