Method for generating attack characteristic database, method for preventing network attack and device thereof
An attack feature and network attack technology, applied in the Internet field, can solve problems such as poor effect, occupying too many resources and CPU performance, and achieve the effect of ensuring system performance and good prevention effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with the accompanying drawings.
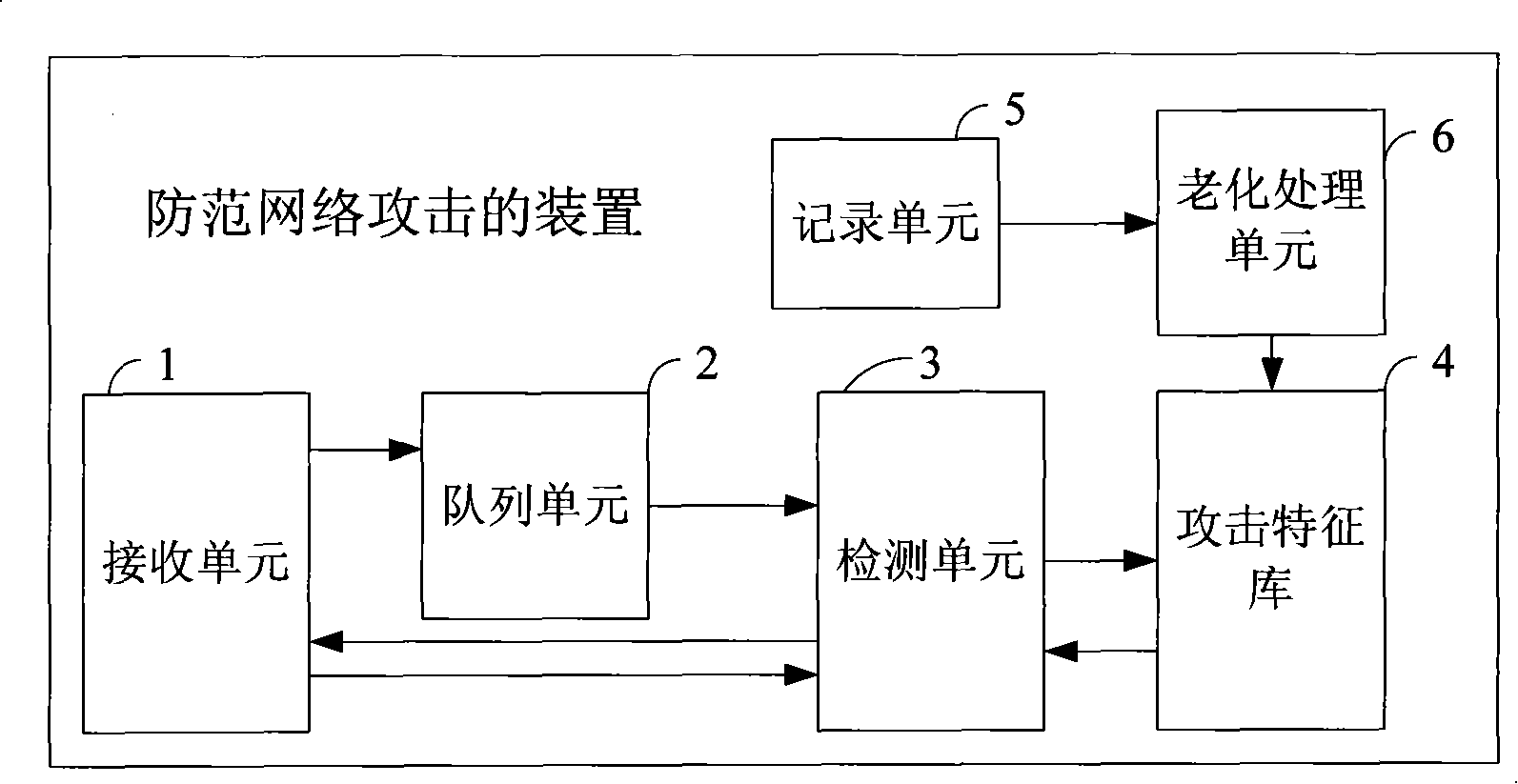
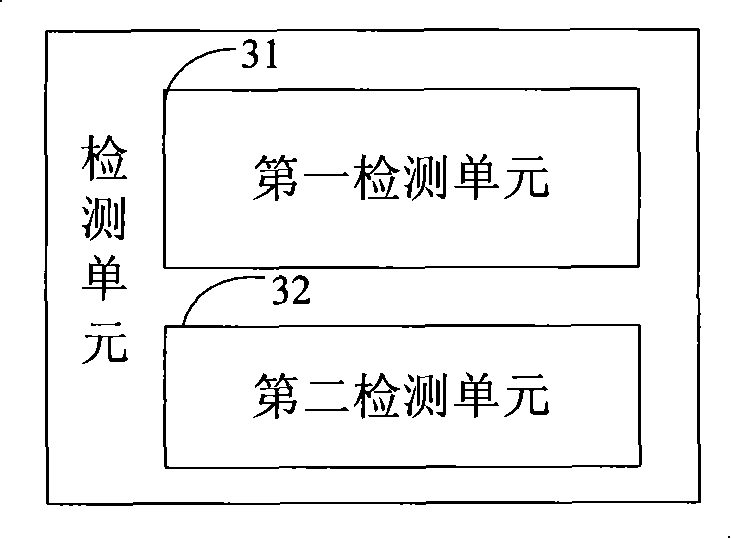
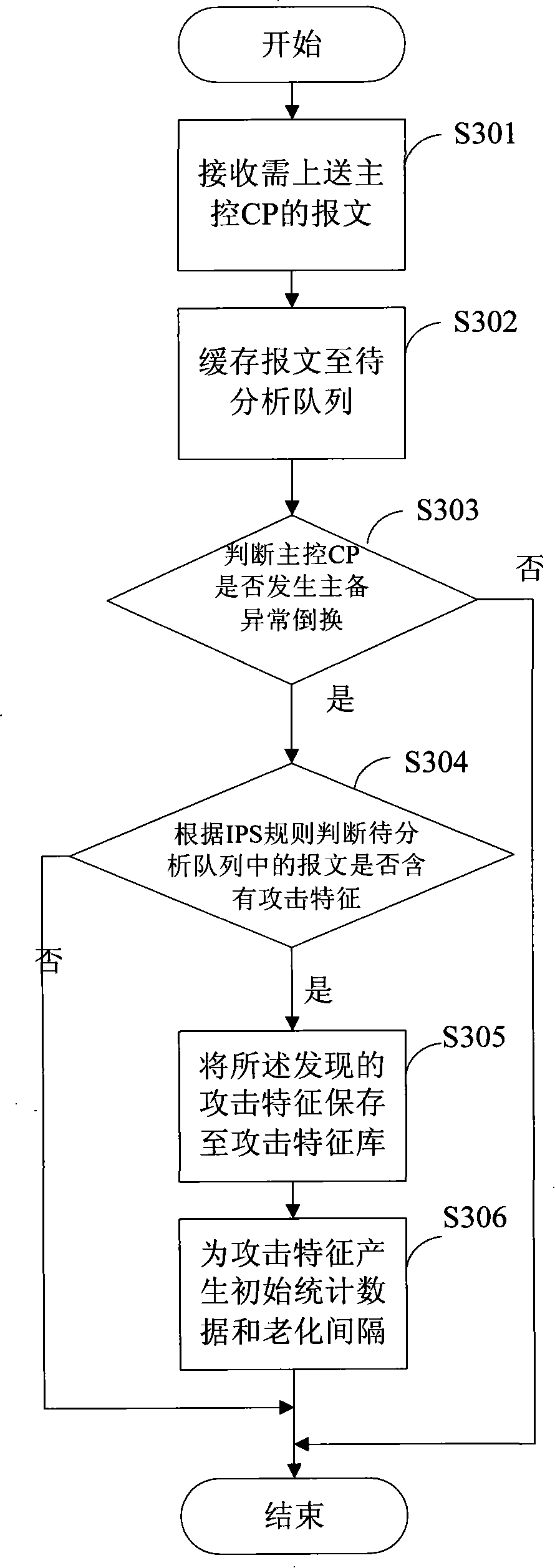
[0025] Reference figure 1 with figure 2 , figure 1 It is a schematic diagram of the overall structure of the device for preventing network attacks according to the embodiment of the present invention. It includes a receiving unit 1, a queue unit 2, a detection unit 3, an attack signature database 4, a recording unit 5 and an aging processing unit 6. Among them: the receiving unit 1 is used for receiving The message that needs to be sent to the master CP. The queue unit 2 is used to store the message that is received by the receiving unit 1 and needs to be sent to the main control CP. The attack signature database 4 is used to store attack characteristics and initial statistical data corresponding to the attack characteristics and the aging interval, where the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com