Picture and file virus defense system and method
A defense system and image file technology, applied in the field of virus defense system, can solve the problems of unsaved image files, loss of image file data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
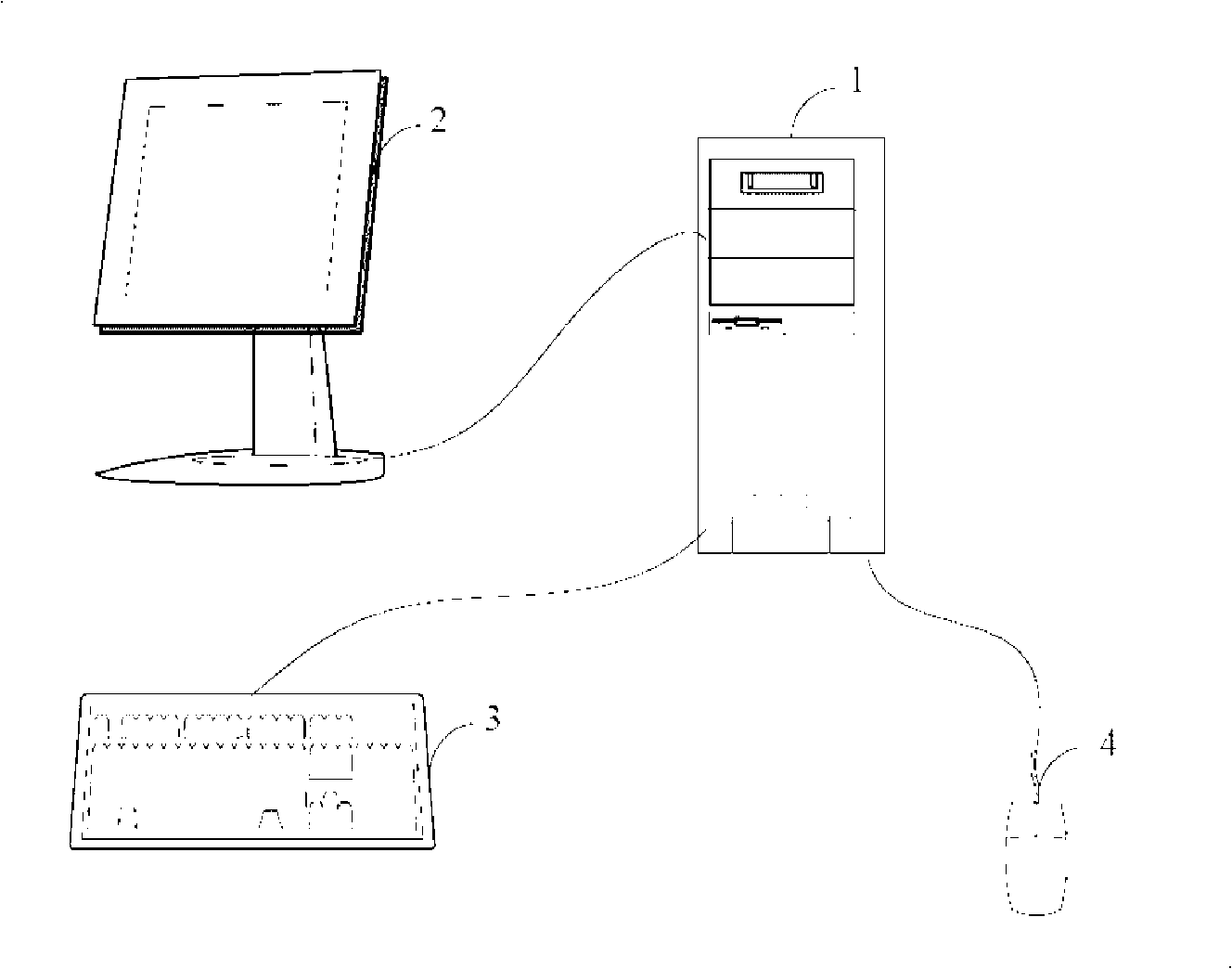
[0012] Such as figure 1 Shown is a hardware architecture diagram of a preferred embodiment of the image file virus defense system of the present invention. The system includes a host computer 1 , a display screen 2 , a keyboard 3 and a mouse 4 . Wherein, the host computer 1 is used for related operations of image file virus defense, and it may be an IBM computer, an Apple Mac PC, a personal computer, a network server, or any other suitable computer. The display screen 2 can be any display device, which provides a graphical user interface for the operator, and the user inputs operation commands to be executed through the keyboard 3 or the mouse 4 .
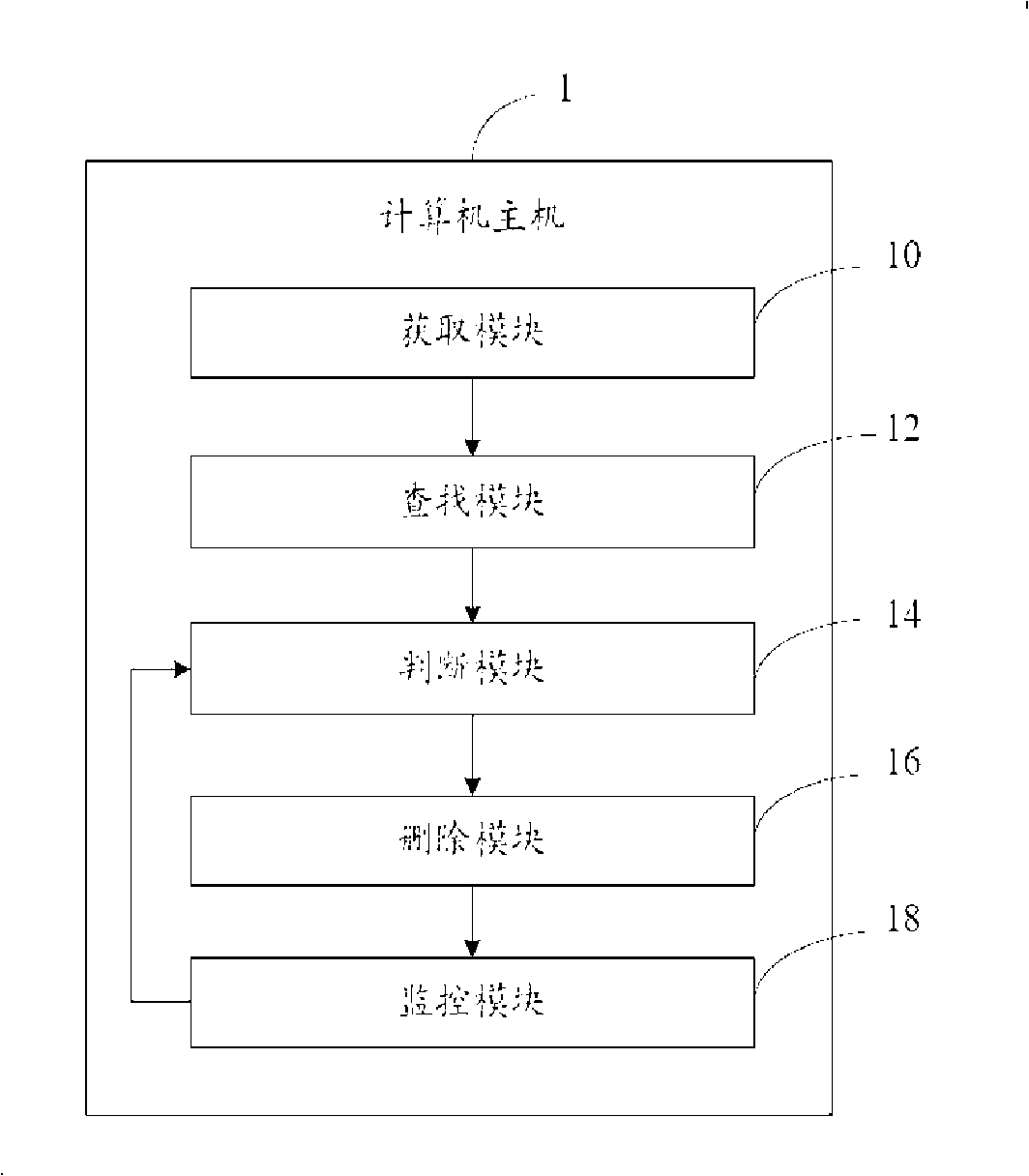
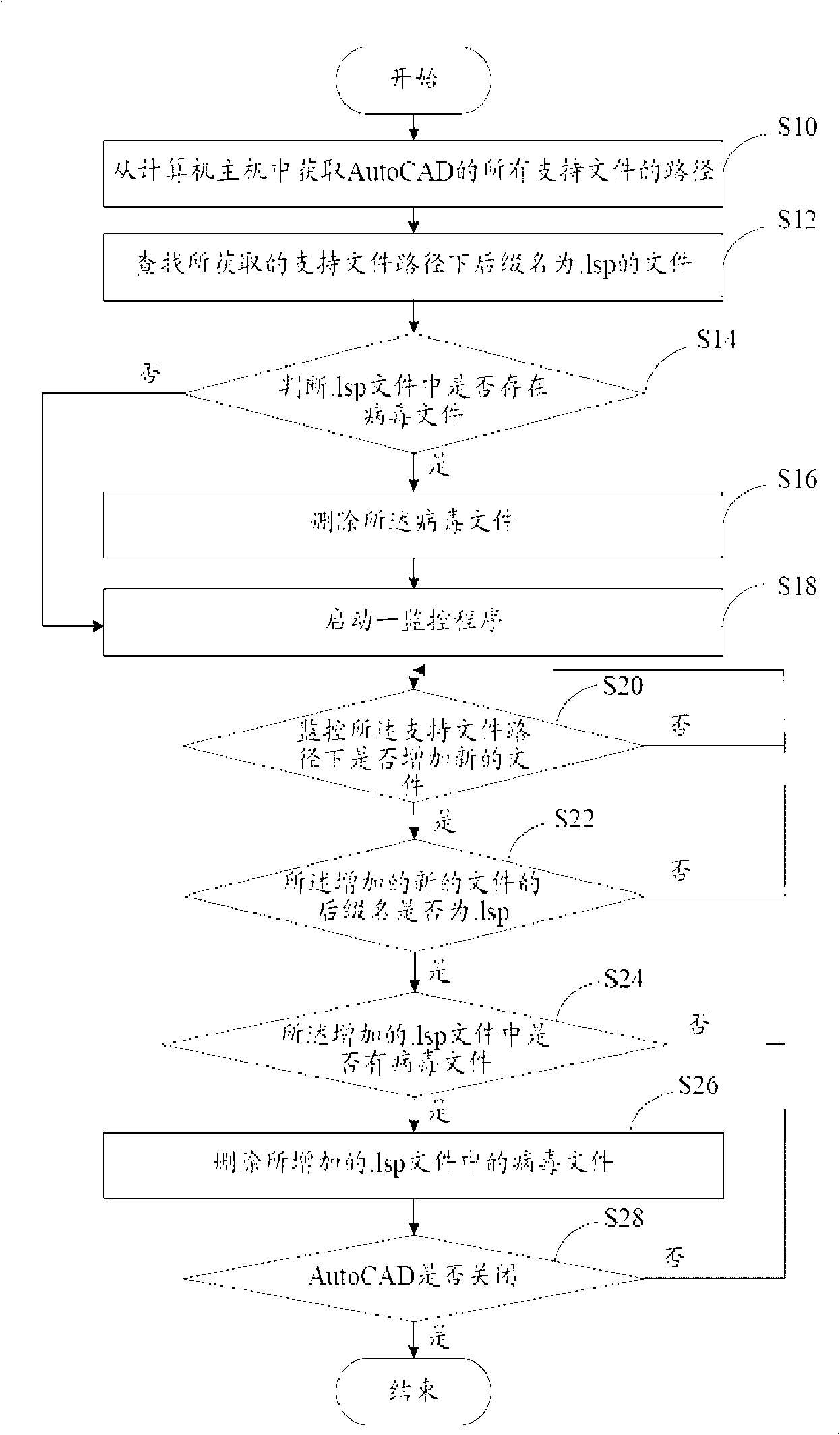
[0013] Such as figure 2 shown, is figure 1 The functional block diagram of the main computer 1 in the computer. The host computer 1 includes an acquisition module 10 , a search module 12 , a judgment module 14 , a deletion module 16 and a monitoring module 18 . In this preferred embodiment, AutoCAD is used as an example for i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com