Remote controlling method and system based on transparent proxy equipment
A technology of transparent proxy and remote control software, applied in the field of network communication security, can solve the problem of inability to directly configure remotely, and achieve the effect of improving manageability and interactivity, less investment, and improving humanization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
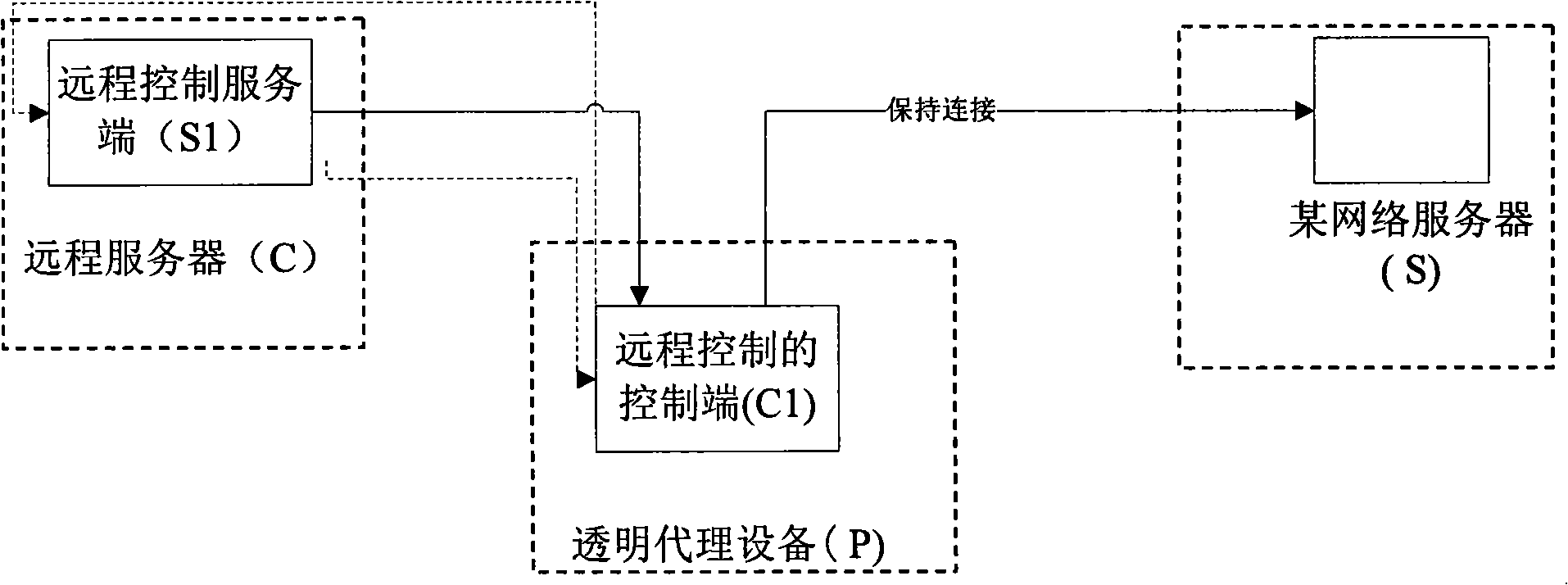
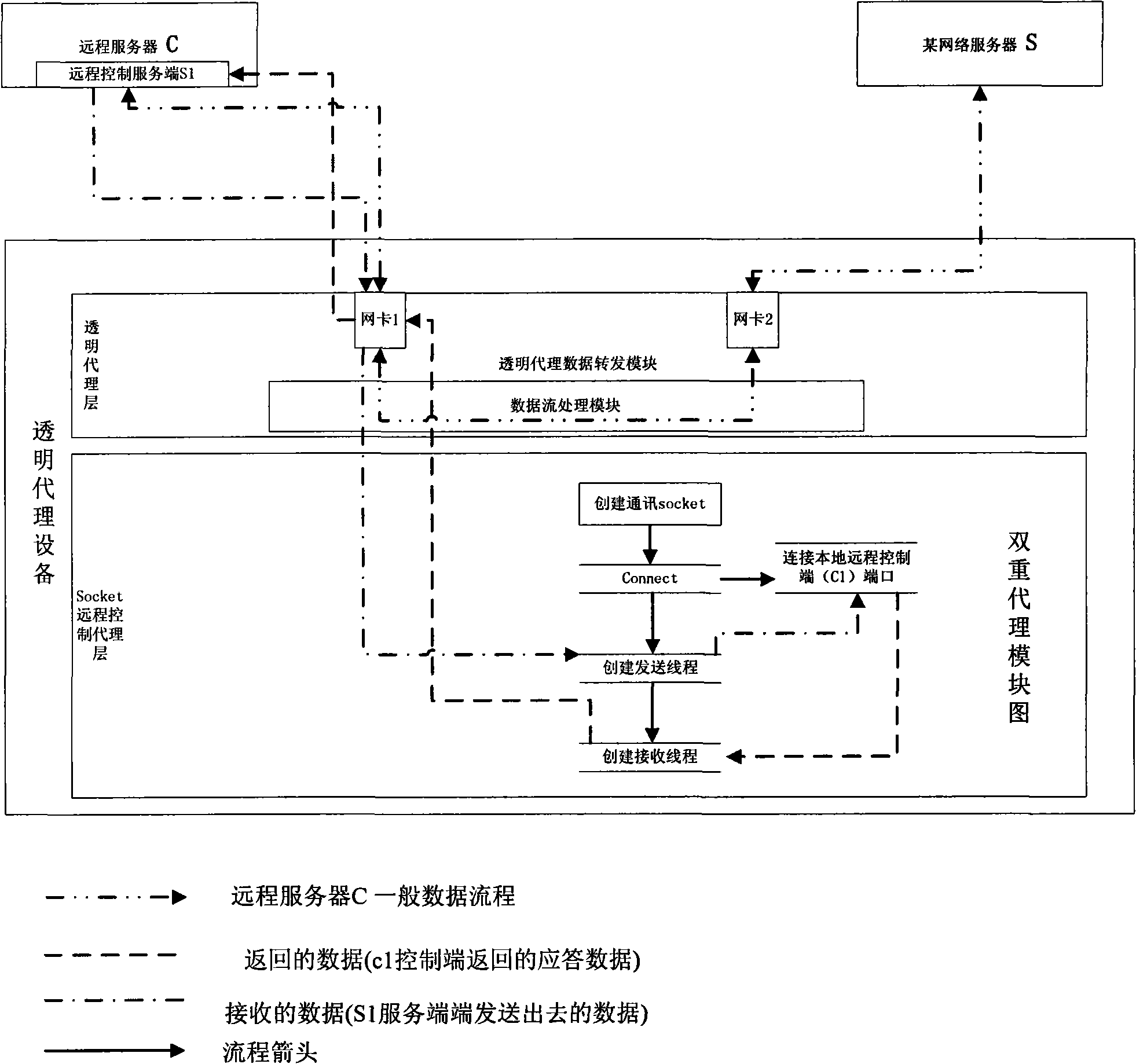
[0040] figure 1 The middle data analysis module is responsible for analyzing the incoming data from (1). Since the communication mode between C1 and S1 is a private protocol, we can use this private protocol to distinguish whether it is the communication data between C1 and S1 or If the communication data of other protocols is found to be common data, it will be directly forwarded by (2). Because this system is mainly used in hardware firewalls, auditing systems, etc., such systems themselves have data analysis modules to decode network flow data and protocols. The clue of 3 yuan can determine whether it is the data sent by the remote server (S1), such as the above-mentioned IP: 202.108.
[0041] If it is found that the data is sent by the remote control software server (S1), see figure 1 In (3), the parsing module will pass the parsed application layer data to the proxy device. At this time, the data will not be forwarded through (2), but will send Ack to the remote server ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com