Method of data access preventing decryption
A data access and data reading technology, applied in the direction of preventing unauthorized use of memory, information storage, static storage, etc., can solve the problem of not being able to guarantee the confidentiality of data in storage devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The invention discloses a data storage device and a data access method thereof. Those skilled in the art will have a better understanding of the above objects and advantages of the present invention after reading the following embodiments and accompanying drawings. The present invention is not limited by the following examples.
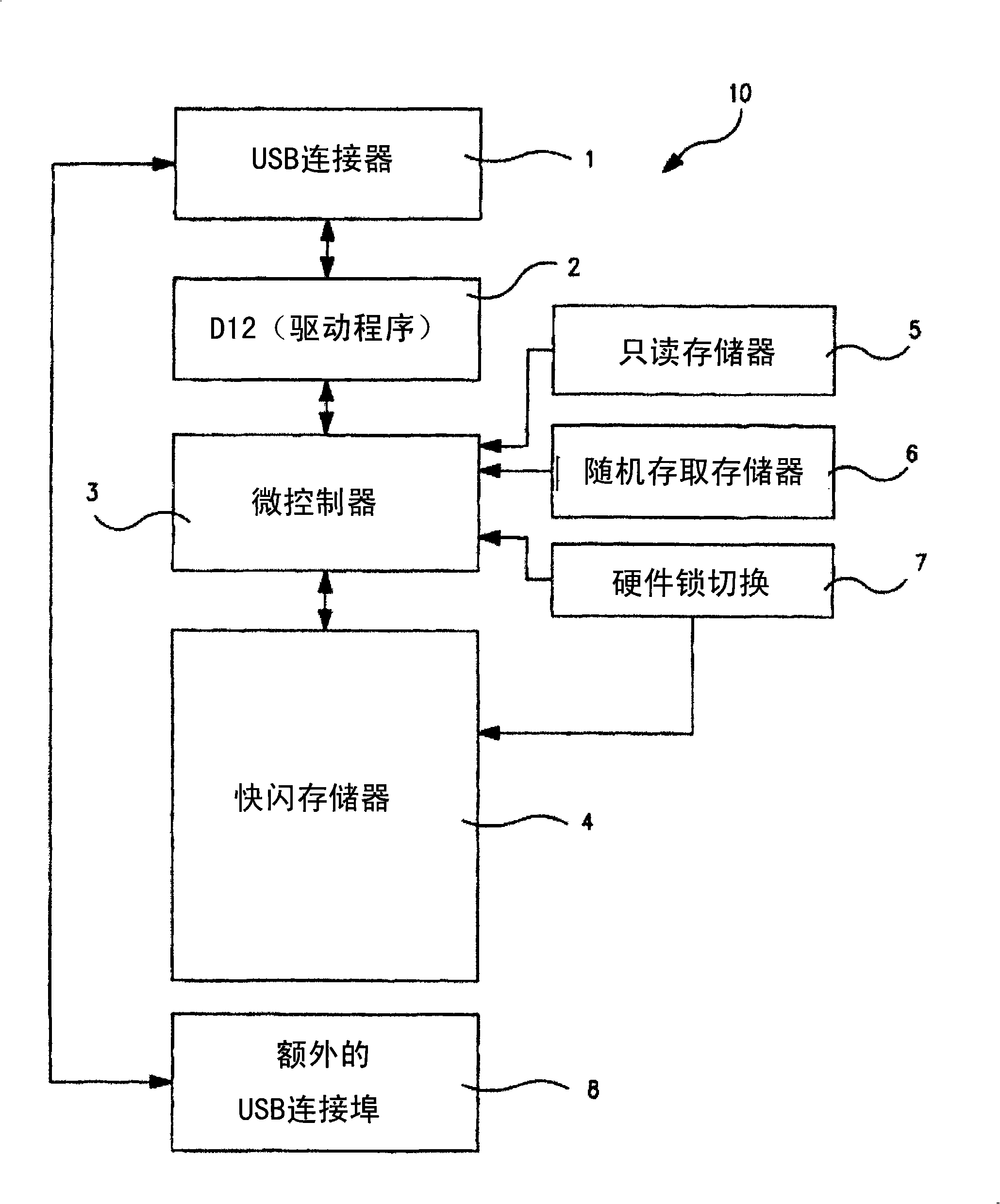
[0034] Please refer to FIG. 4 , illustrating a security mechanism of a data storage device according to the present invention. As shown in Figure 4, the data storage device 1 includes: an interface 20 connected to a data read / write device (not shown), which is used for buffering and transmitting data; a non-volatile memory 21; A flash memory 22 for storing data; an encryption unit 23; and a decryption unit 24, and the above elements will be described in detail below.
[0035]The encryption key and the decryption key are stored in the non-volatile memory 21 at the same time. Each key is a field of bits used to encrypt and decrypt data using t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com