Method, system and apparatus for protecting proxy mobile internet protocol signalling
A protection proxy and signaling technology, applied in wireless network protocols, secure communication devices, security devices, etc., can solve the problem of not providing a random number transmission method for calculating the shared key, low efficiency in the search process, and PMIP signaling does not support random numbers issues such as transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] In order to make the purpose, technical solutions and beneficial effects of the present invention more clear, the present invention will be further described in detail below in conjunction with the embodiments and accompanying drawings.
[0066] The first method for protecting PMIP signaling provided in the embodiments of the present invention includes:
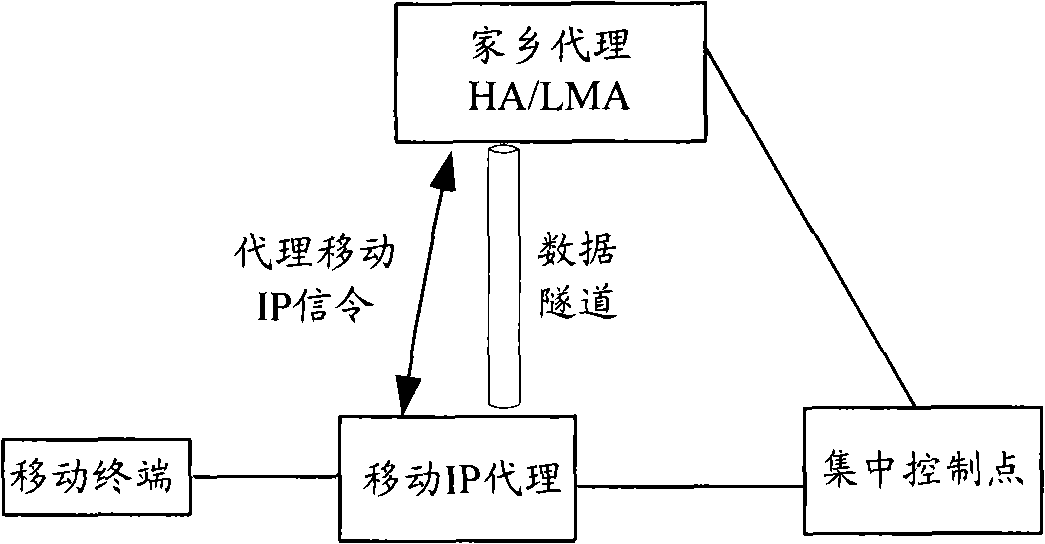
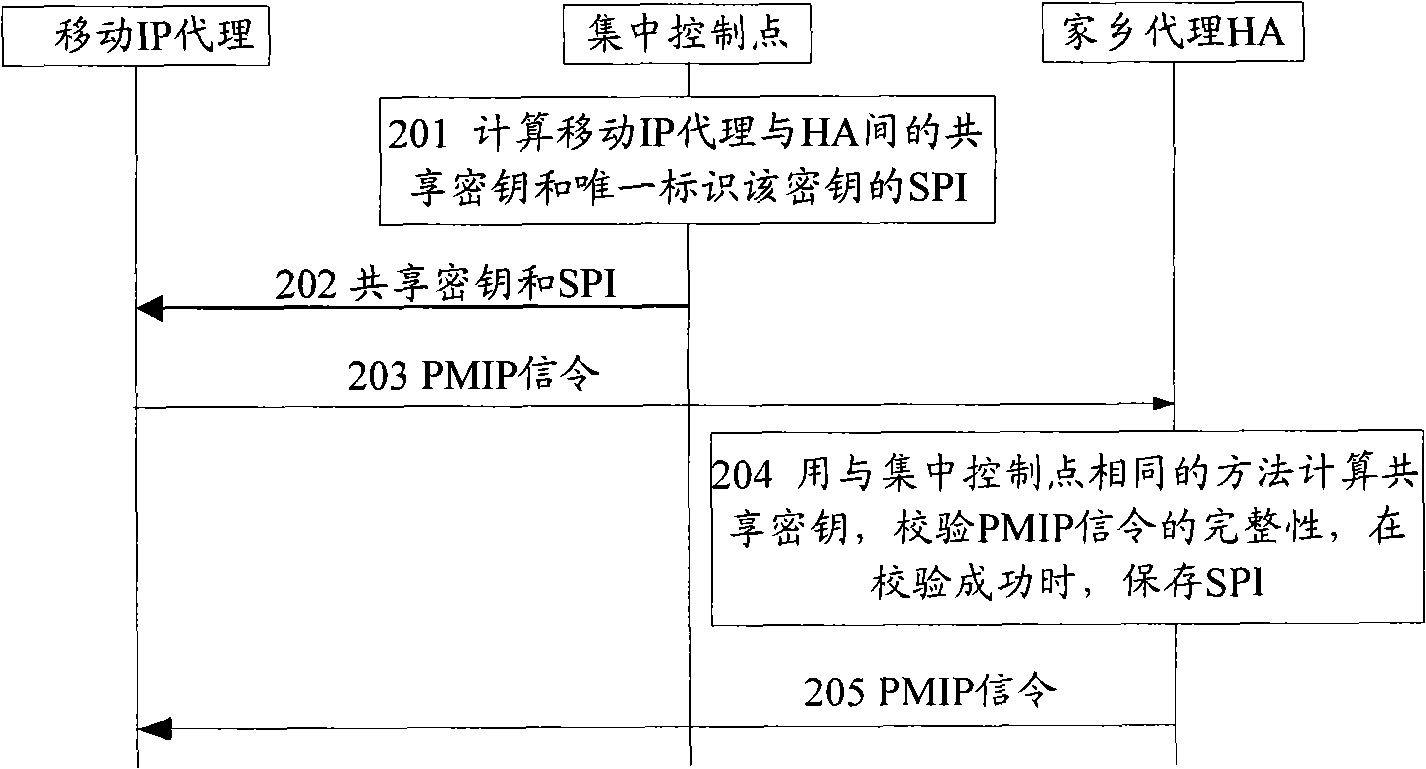
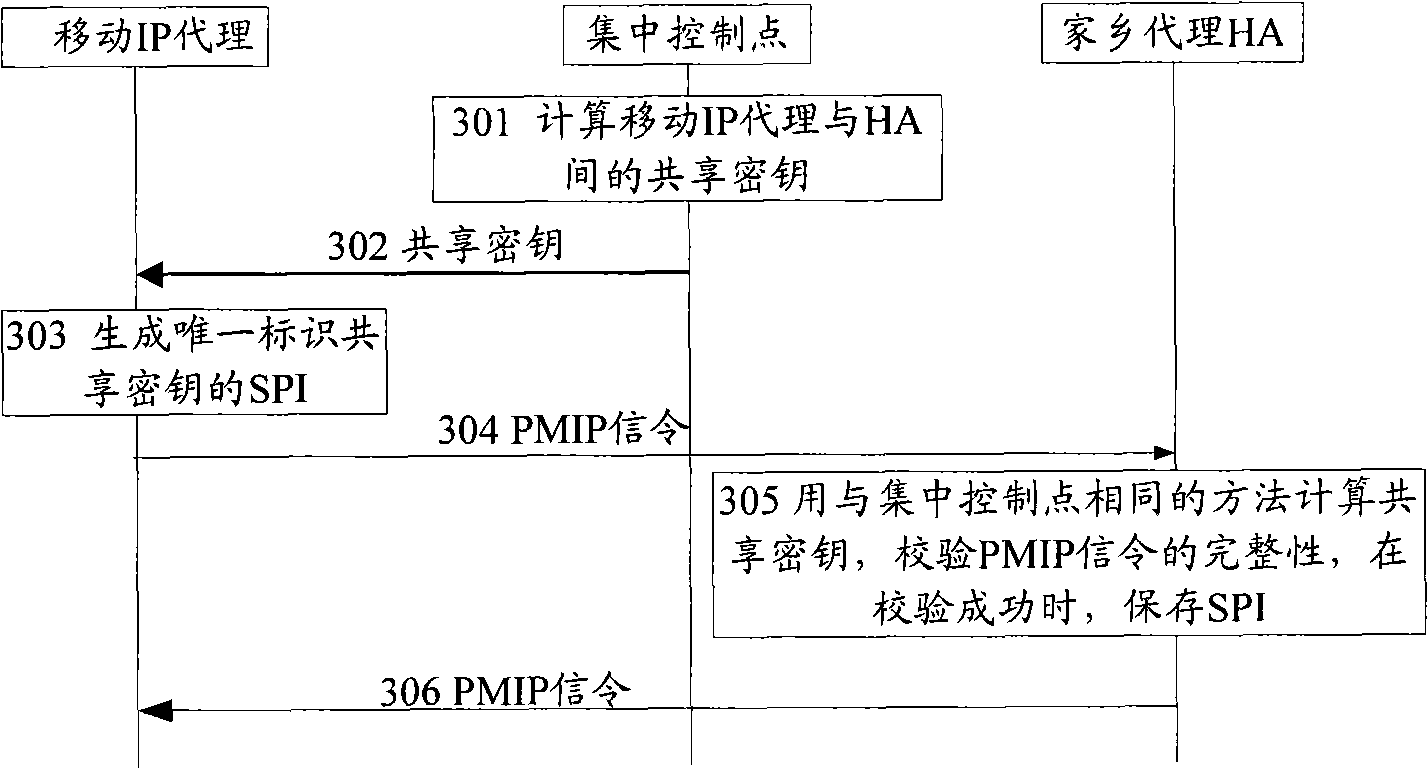
[0067] The centralized control point calculates the shared key of the mobile IP agent and the HA; generates the SPI that uniquely identifies the shared key; the mobile IP agent sends the PMIP signaling to the HA, and uses the shared key to protect the integrity of the PMIP signaling, Carry the SPI in the PMIP signaling and send it to the HA; the HA receives the PMIP signaling from the mobile IP agent, uses the same method as the centralized control point to calculate the shared key, and uses the calculated shared key to verify the received The integrity of the PMIP signaling, when the verification is successful, save t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com