Method, apparatus and network device for identifying virus document
A virus file and file technology, applied in computer security devices, electrical components, instruments, etc., can solve problems such as system damage, virus analysis process extension, and anti-virus product upgrade cycle, so as to achieve fast recovery, improve efficiency, and save money. Analyzing the effect of time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
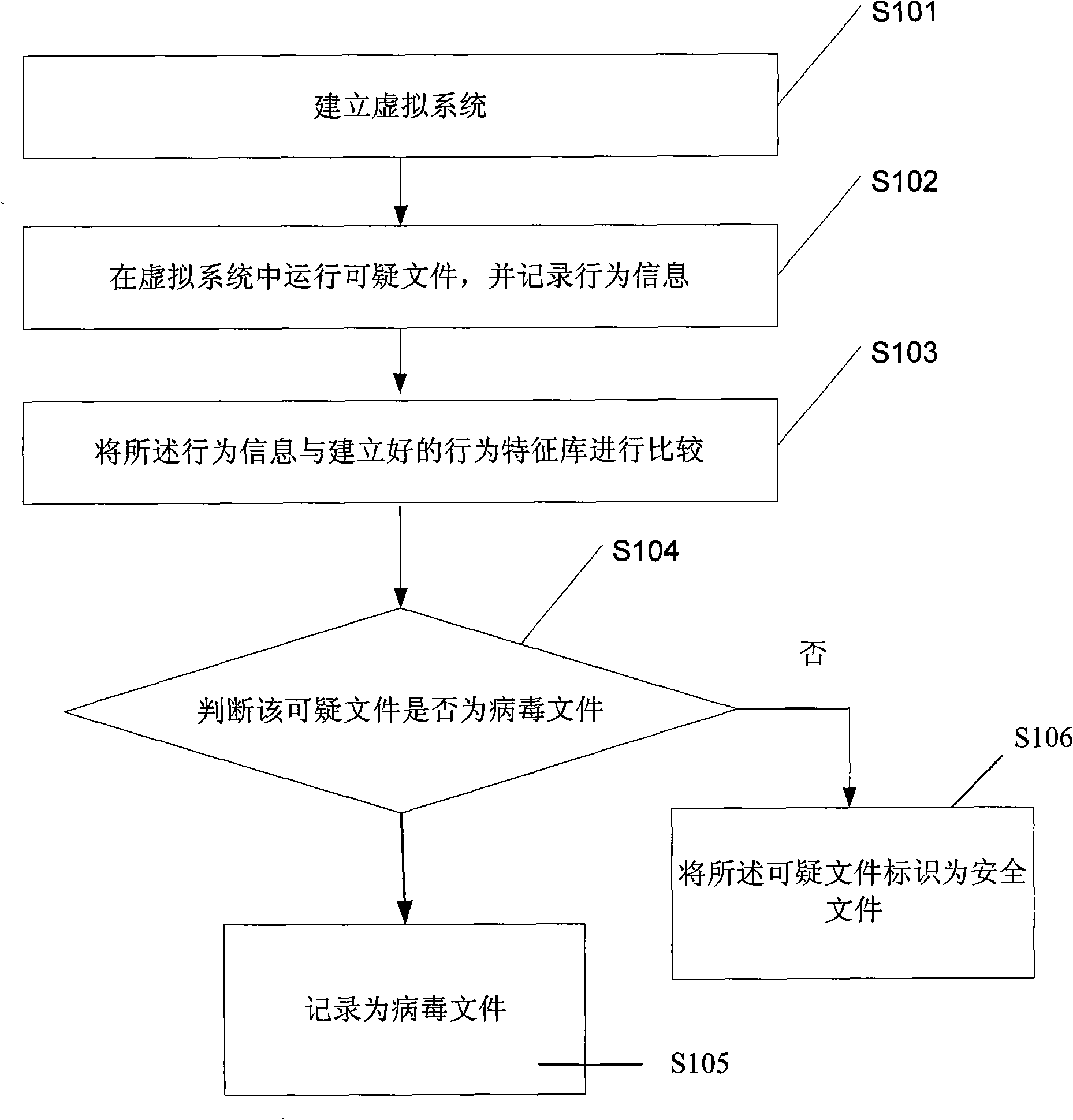
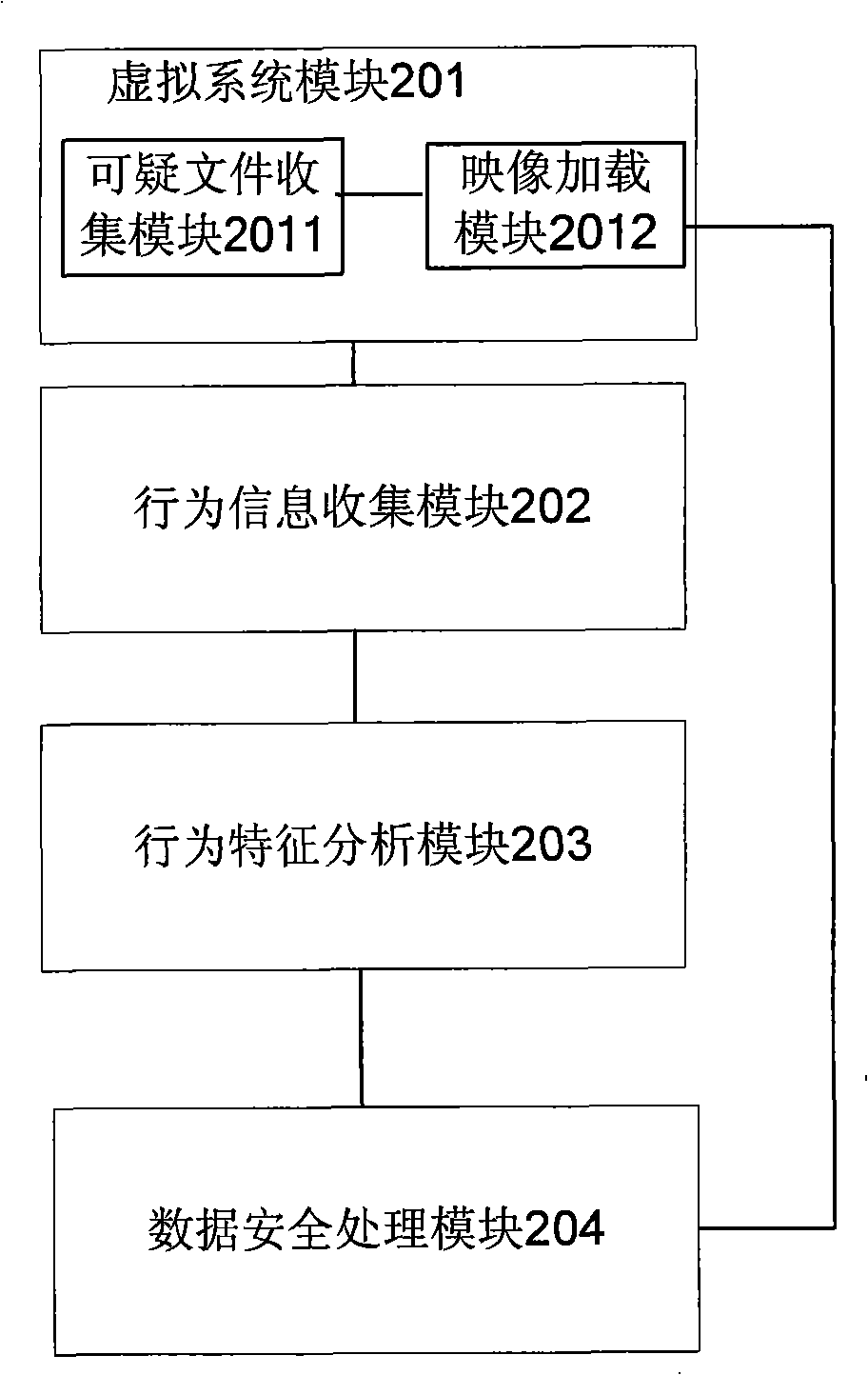
[0021] In the process of virus analysis, to identify whether a suspicious file is a virus file is usually to analyze the running behavior of the file, so as to confirm whether it is a virus file. see figure 1 , the present invention provides a kind of method of identification virus file, at first construct virtual system (S101) in the system, when suspicious file is found, make suspicious file run in this virtual system, and record the behavior information of suspicious file (S102); And compare (S103) the behavior information and virus behavior feature database, judge whether described suspicious file is virus file (S104), if so, then described suspicious file is identified as virus file (S105); Otherwise, all The suspicious file is identified as a safe file (S106).
[0022] For step S101, the virtual system can build a virtual framework by using computer programs to monitor key APIs of the system and simulate some functions of the real system. It can simulate the process of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com