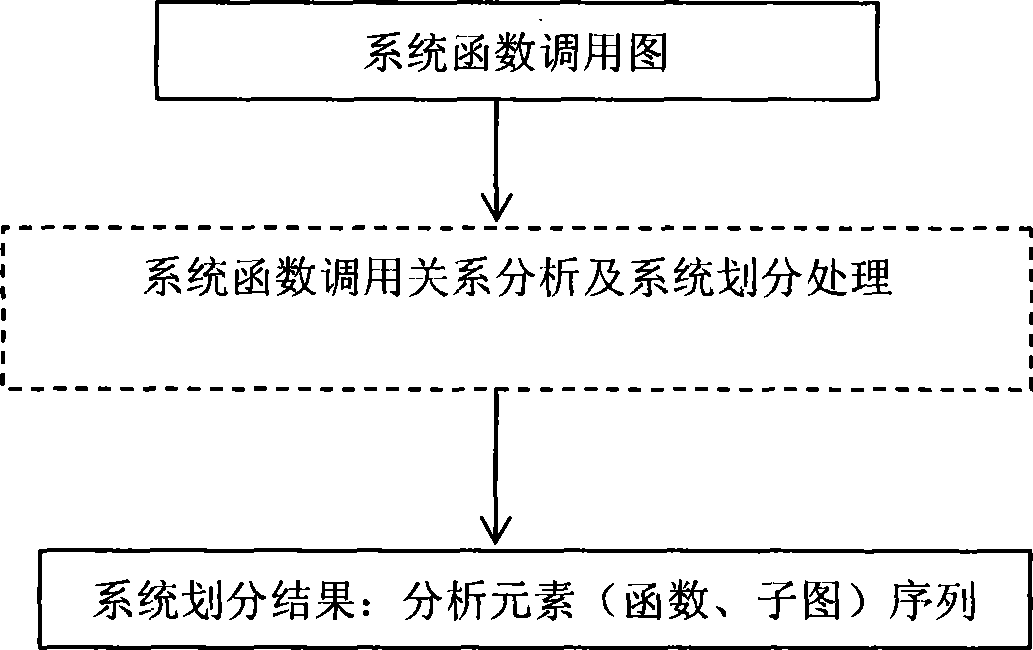
Systems analysis and dividing method orienting covert channel analysis
A system analysis and covert channel technology, applied in the field of system analysis and division oriented to covert channel analysis, can solve problems such as unfavorable analysis and processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
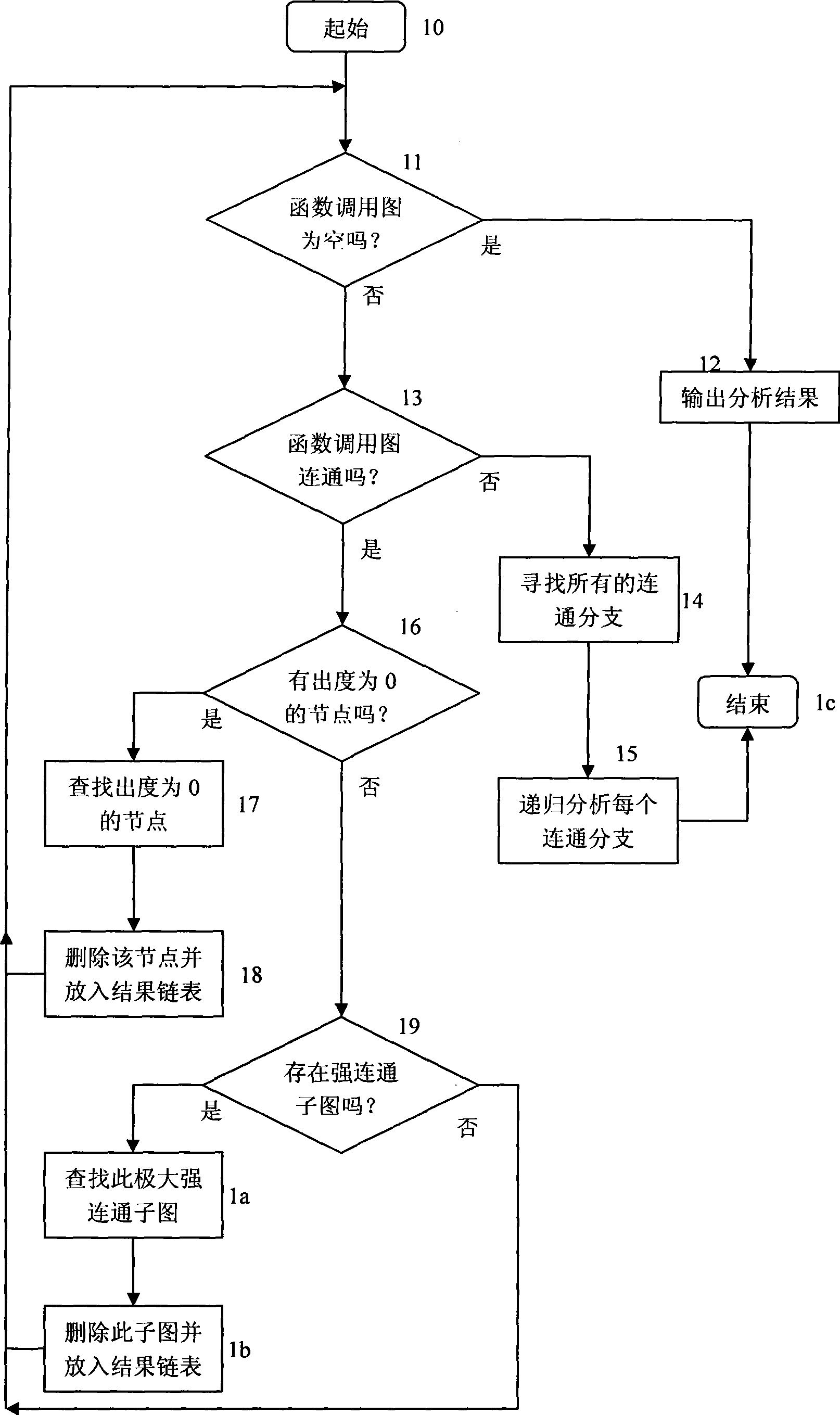
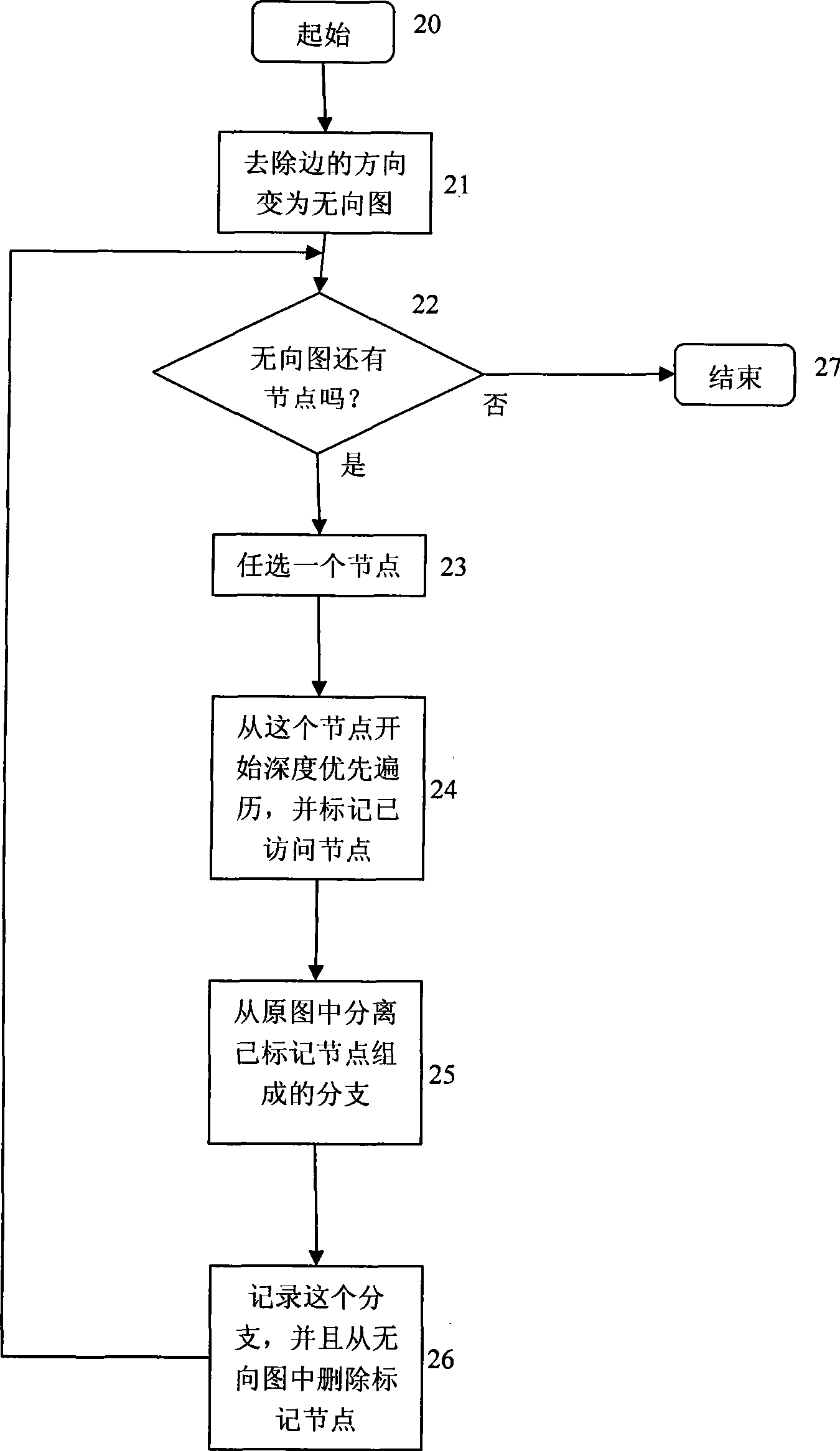
[0030] figure 2Shown is the workflow for performing system analysis and partitioning in this method. Step 10 is an initialization action. Step 11 judges whether the function call graph is empty. If it is idling step 12, it means that the analysis and division algorithm ends. Otherwise, go to step 13. Step 12 outputs the analysis results for use by analysts. Step 13 judges whether the function call graph is connected. If connected, go to step 16, otherwise go to step 14. Step 14 finds out all disconnected branches of the function call graph. Step 15 cyclically analyzes each connected branch of the function call graph. The analysis process is the same as analyzing the entire function call graph. And it prompts the analyst that these disconnected branches can be processed in parallel. Step 16 judges whether there is a node in the function call graph that does not depend on other nodes, that is, a node with an out-degree of 0. In a directed graph, the out-degree of a no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com