Method for guarantee safety of electronic file
An electronic file and security technology, applied in the field of encryption and decryption of electronic files, can solve the problems of not being able to control the use of files by users, permissions, and inability to view, and achieve the effect of low cost and increased protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The content of the present invention will be further described in detail below in conjunction with the accompanying drawings.
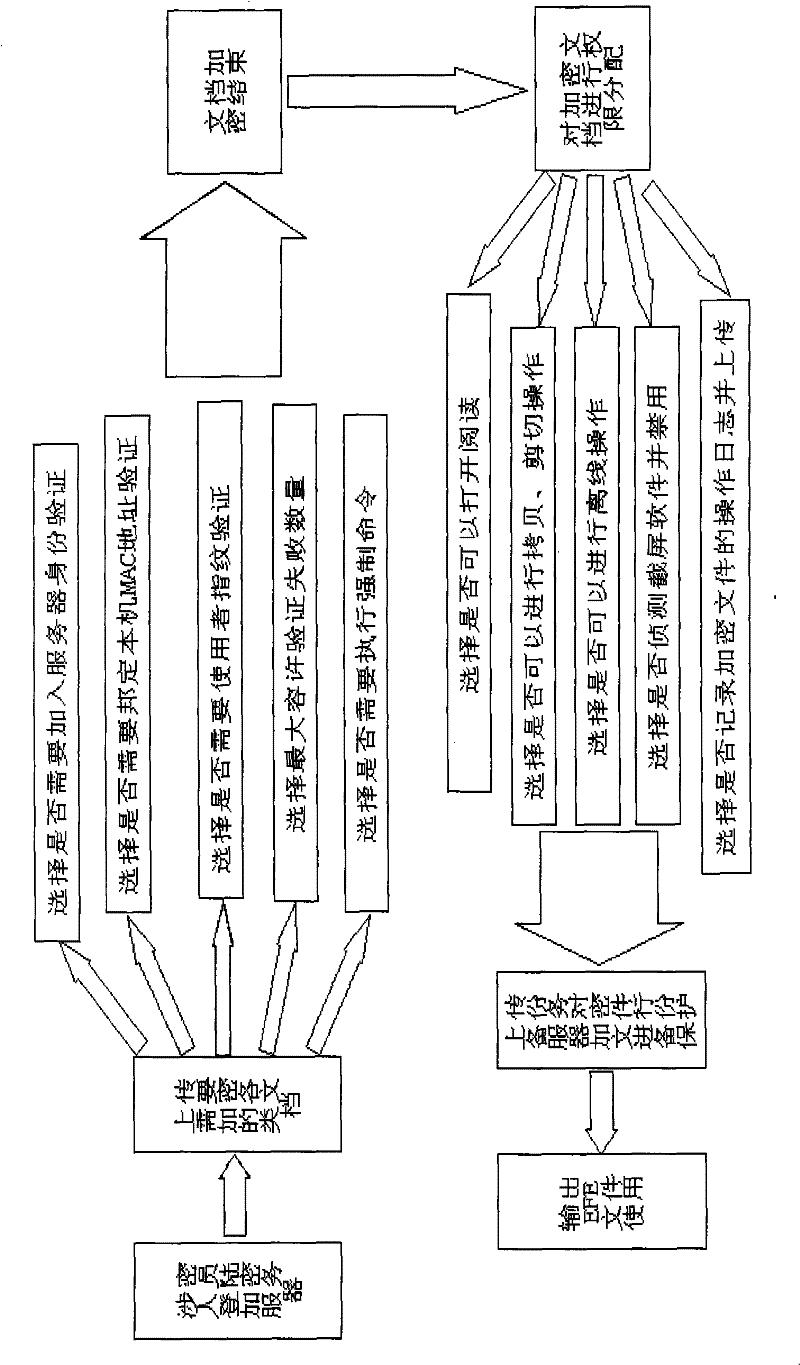
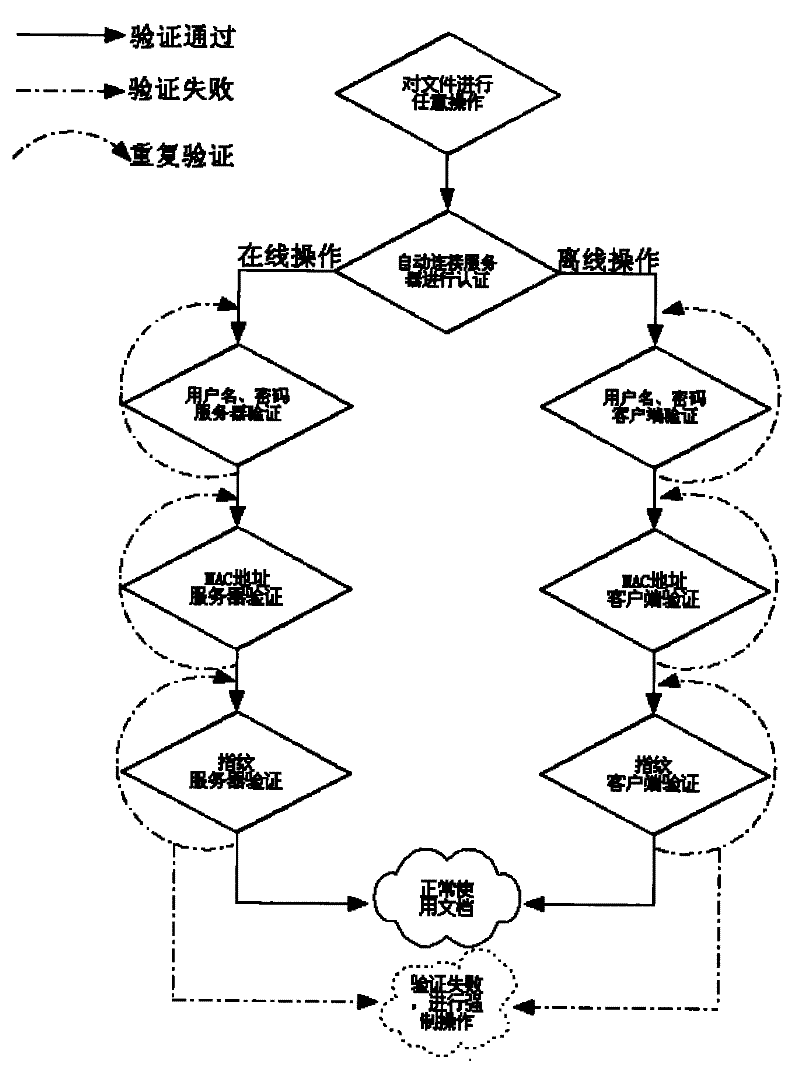
[0040] see figure 1 , the concrete flow process of the encryption process of the present invention is:
[0041] First, the initial confidential personnel of the document log in to the encryption server, upload various documents that need to be encrypted, and after verifying the document format, select the required encryption method. The specific options are:
[0042] 1. Do you need to join server identity verification?
[0043] 2. Do you need to bind the local MAC address for verification?
[0044] 3. Whether user fingerprints are required for authentication
[0045] 4. Select the maximum allowable number of verification failures
[0046] 5. Choose whether to make a mandatory order
[0047] Among the above 5 options, at least one of the first 3 items must be selected, and the last two items are mandatory. After the selection is completed, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com