General protocol parsing method and system
A general protocol and analysis method technology, applied in the field of general protocol analysis, can solve problems such as insufficient consideration, and achieve the effects of simple structure, enhanced intrusion detection ability, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
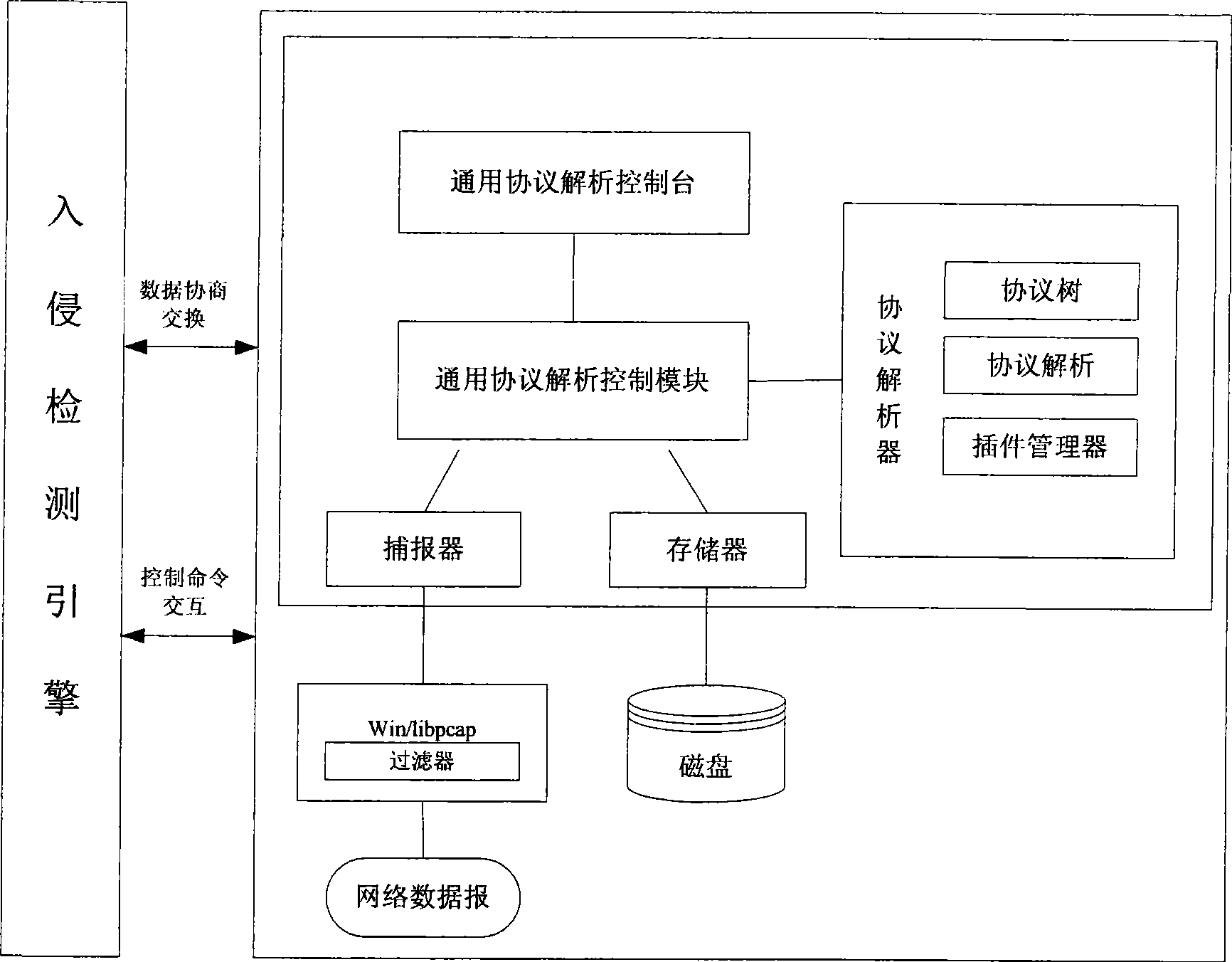
[0040] This embodiment is a basic mode of a general protocol analysis method, and the system used is such as figure 1 shown. It includes an intrusion detection engine, a general protocol analysis console, a general protocol analysis control module, a trap, a memory, and a protocol analysis device. Contains the following steps:
[0041] ① The protocol and field registration steps of the general protocol analysis system;
[0042] Each protocol analysis plug-in supported by the general protocol analysis system must first register with the system. Only through registration can the general protocol analysis system know the name, data type, and representation of the subtree / field (decimal / hexadecimal / string etc.), all of this information comes from static data declared inside the subprotocol. In addition, the protocol parser can also choose to provide a structure for the core to further explain the specific meaning corresponding to the field value. This structure is also static d...
Embodiment 2
[0052] This embodiment is an optimal scheme of the protocol and field registration steps of the general protocol analysis system in the first embodiment.
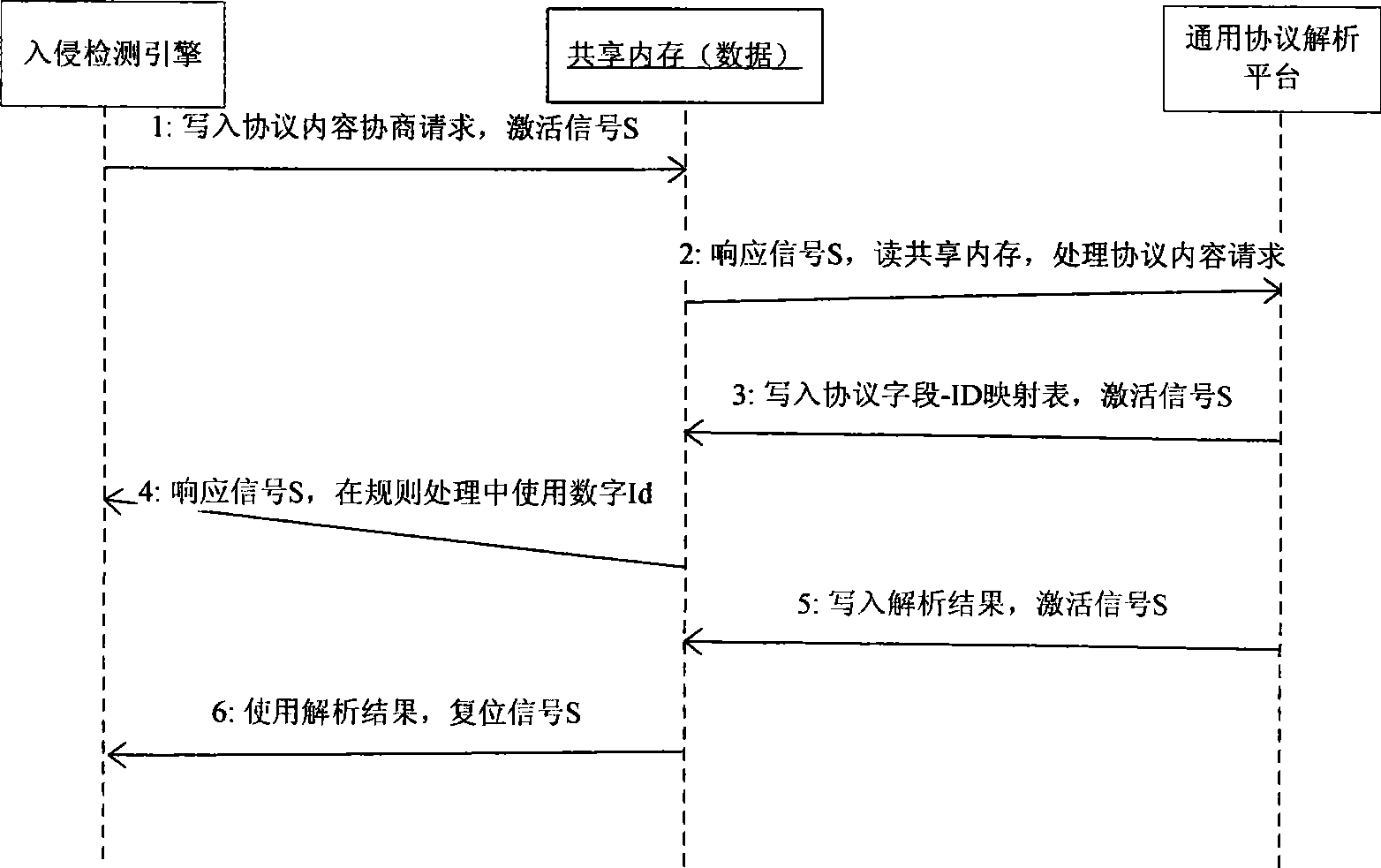
[0053] The basic idea of this embodiment is: its process is as follows Image 6 As shown: Each protocol parser supported by the general protocol parsing system must first register with the system. The registered content includes: the way the system identifies the protocol (port or feature byte callback function), the information of the protocol field (type, name, abbreviation) etc.), the entry point for protocol analysis. After the registration is completed, the general protocol parsing system knows the subtree / field name, data type, and representation (decimal / hexadecimal / string, etc.), all of which come from the static data declared inside the subprotocol. In addition, the protocol parser can also choose to provide a structure for the core to further explain the specific meaning corresponding to the field value. This s...
Embodiment 3
[0056] This embodiment is a preferred solution of the report capturing step in the general protocol analysis system in the first embodiment. The basic idea of this embodiment is: first judge the application environment, if it is under Linux, then call Libpcap (network datagram capture development report under linux) to capture the report, if it is under Windows, then call Winpcap (network datagram under windows) Report Capture Development Report) is a platform-independent network datagram capture device. The trapper in the general protocol analysis system adopts a general datagram filter mechanism, which is a filtering module based on the kernel, which enables the trapper to capture specific datagrams, and can filter out unnecessary datagrams on the network , and only capture datagrams of interest. Datagram filters such as Figure 8 As shown, it consists of two parts, one is the network forwarding part, and the other is the data filtering part. The network forwarding part ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com