Method for implementing user and equipment authentication separately employing diameter protocol
A technology for protocol implementation and device authentication, applied in the field of communication systems, it can solve problems such as two rounds of authentication that do not support separate authentication of users and devices, and achieve the effect of strong practicability and simple implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
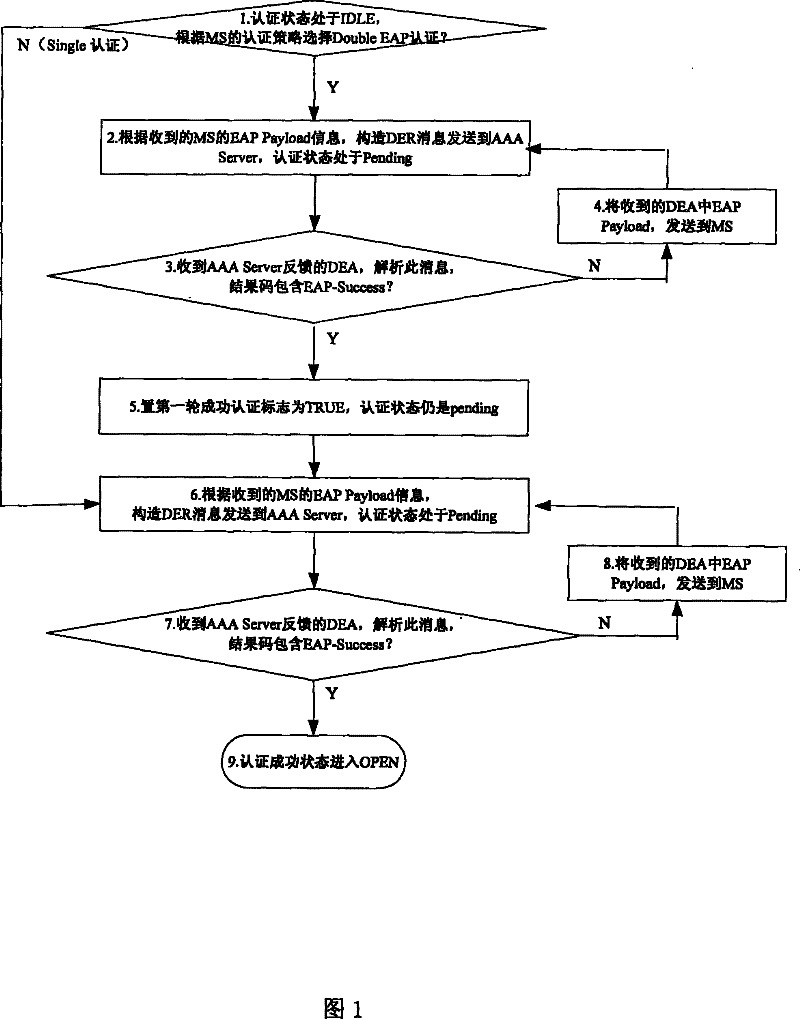
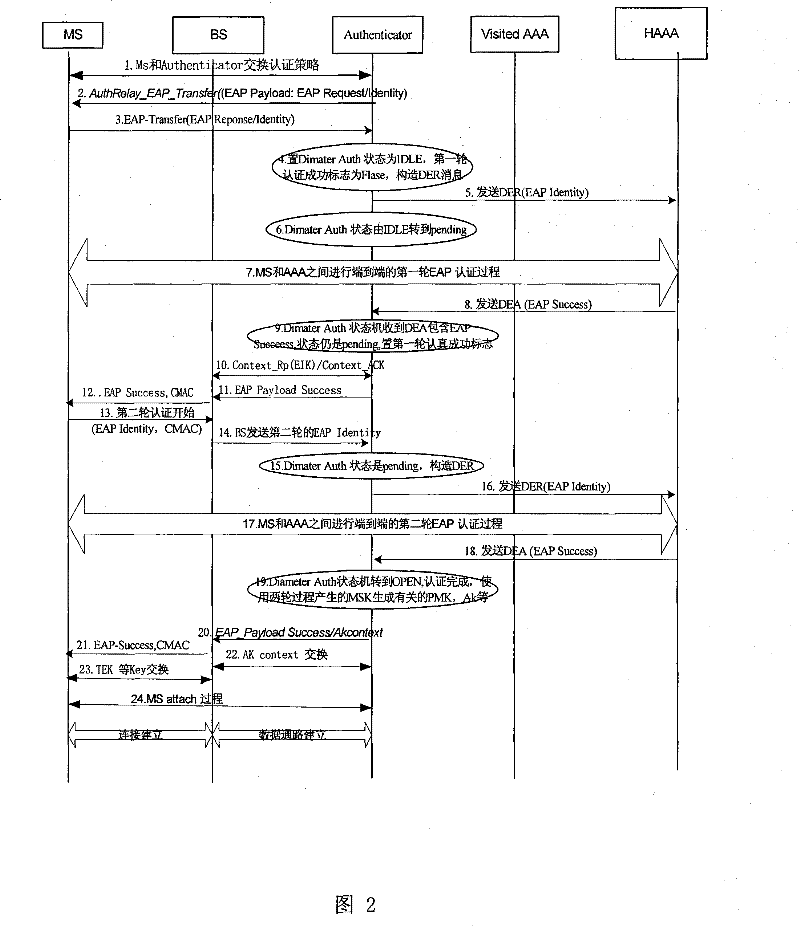
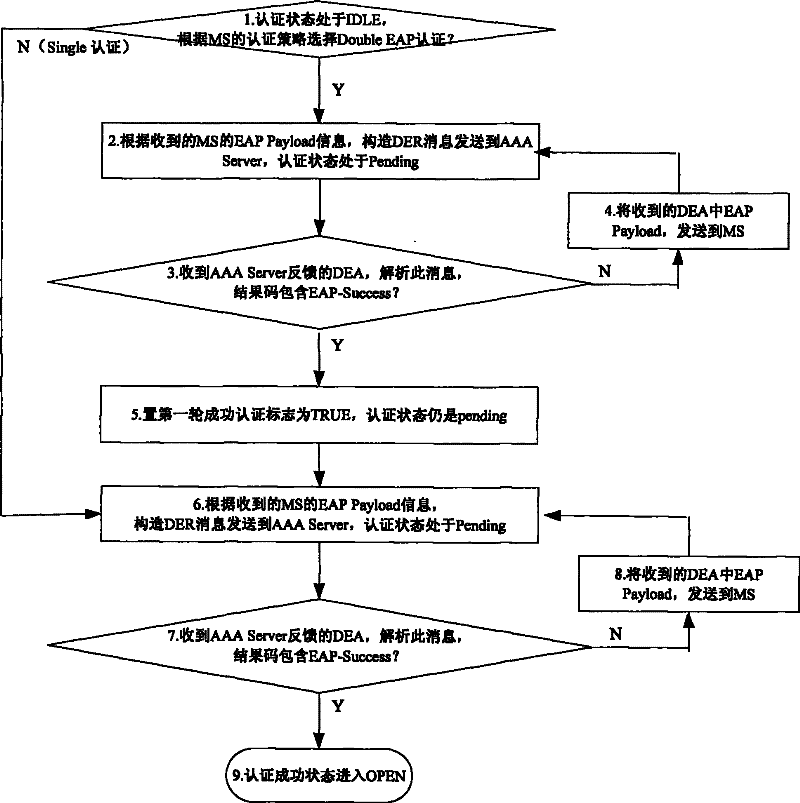
[0036] Using double EAP authentication, an MS uses the embodiment of the initial access process of the method proposed by the present invention, refer to figure 2 , its main steps include:
[0037] 1) MS and Authenticator exchange authentication policies through BS;
[0038] 2) The Authenticator selects the authentication method, and sends an authentication request AuthRelay_EAP_TRANSFER message to the MS through the BS, including information such as EAP-Request / Identity;
[0039] 3) After receiving the EAP_TRANSFER (EAP-Request / Identity) message, the MS replies to the Authenticator through the BS with EAP_TRANSFER (EAP-response / Identity), and reports the identity required for authentication;
[0040] 4) When the Authenticator receives the MS EAP-Identiy, it sets the state of the Diameter authentication state machine to IDLE, and the initial value of the first-round authentication success flag is False; and constructs a DER message according to the received MS EAP-payload. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com