Method for binding computer hardware and software
A computer hardware, computer technology, applied in the direction of computer security devices, computing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
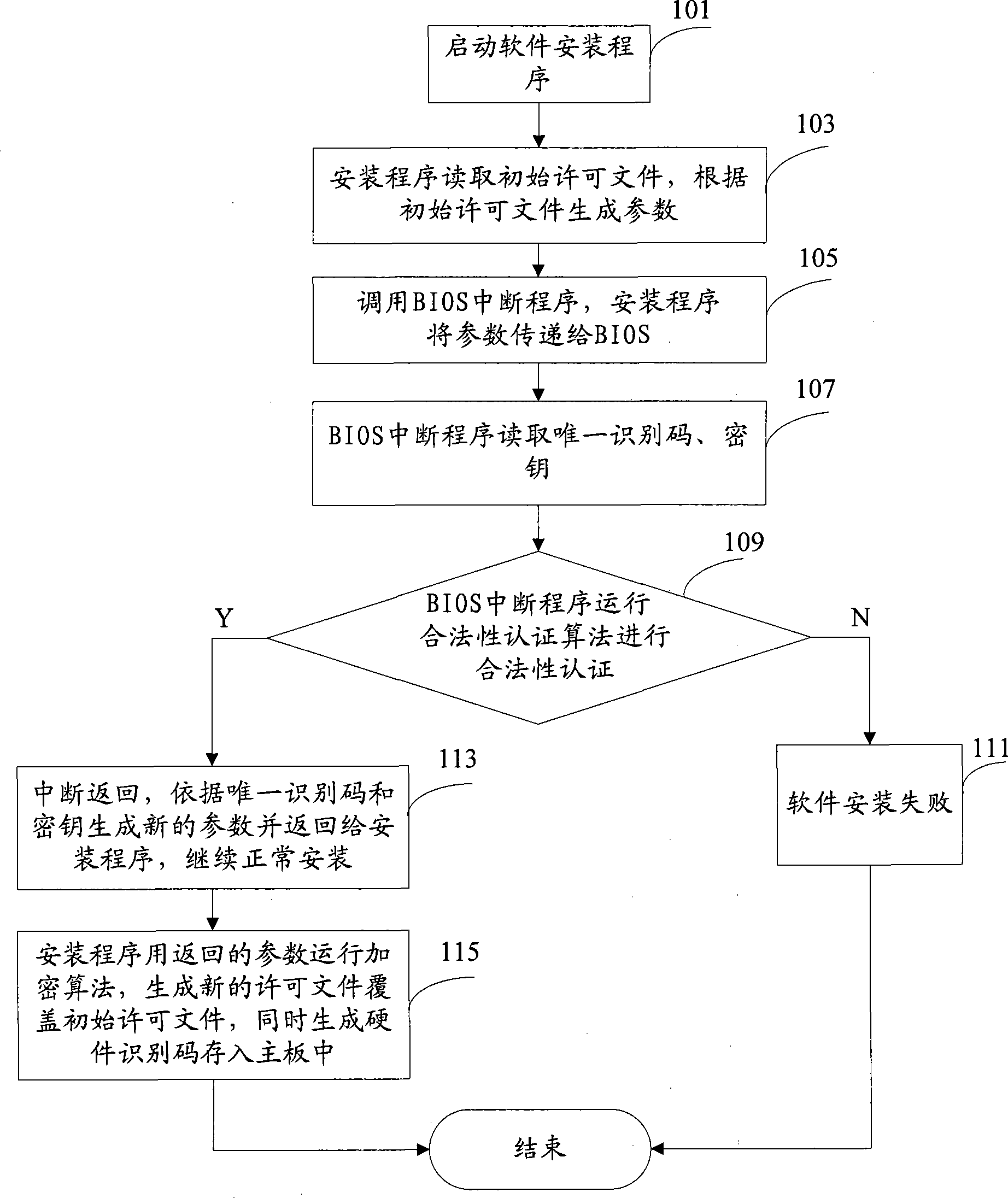
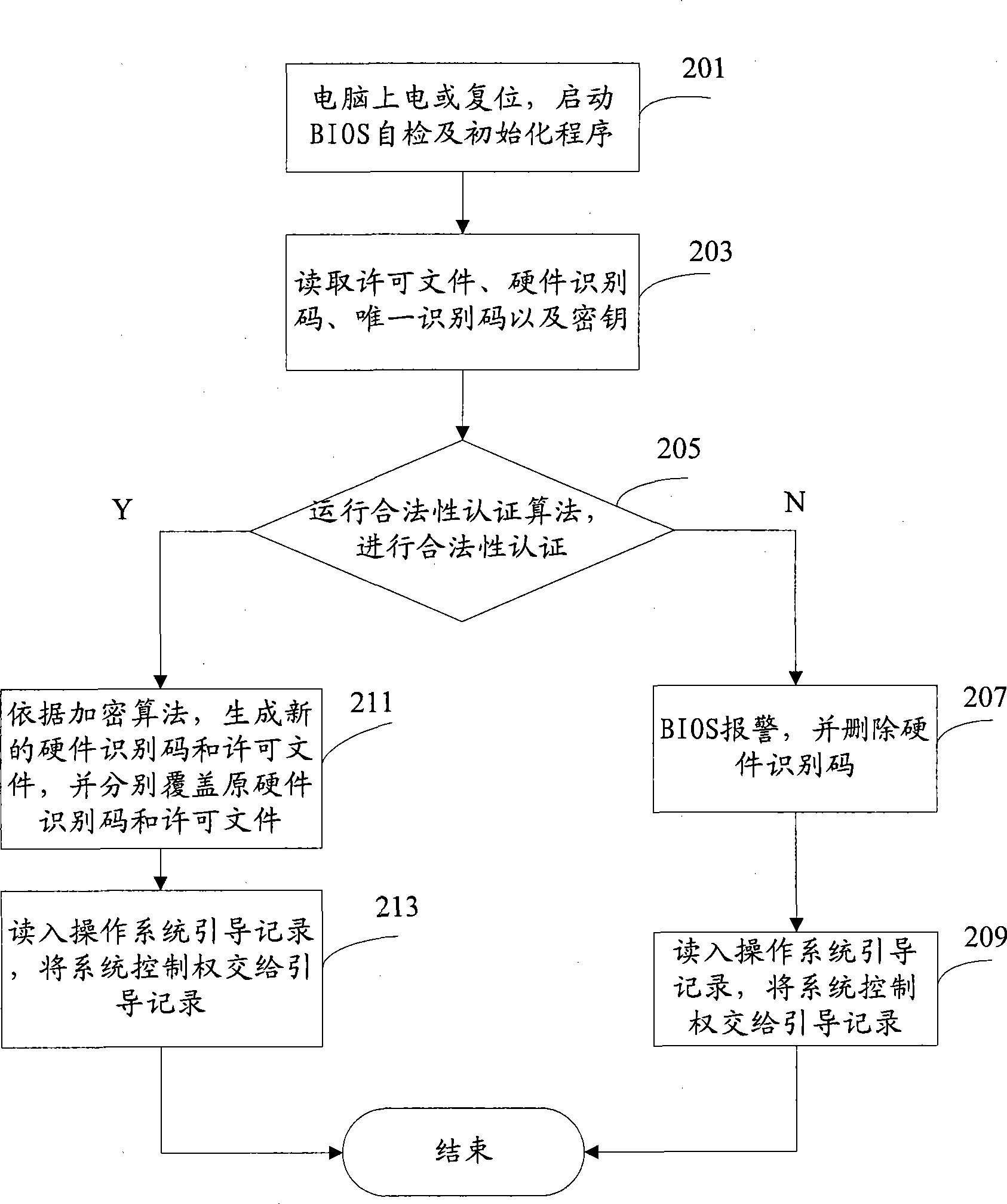
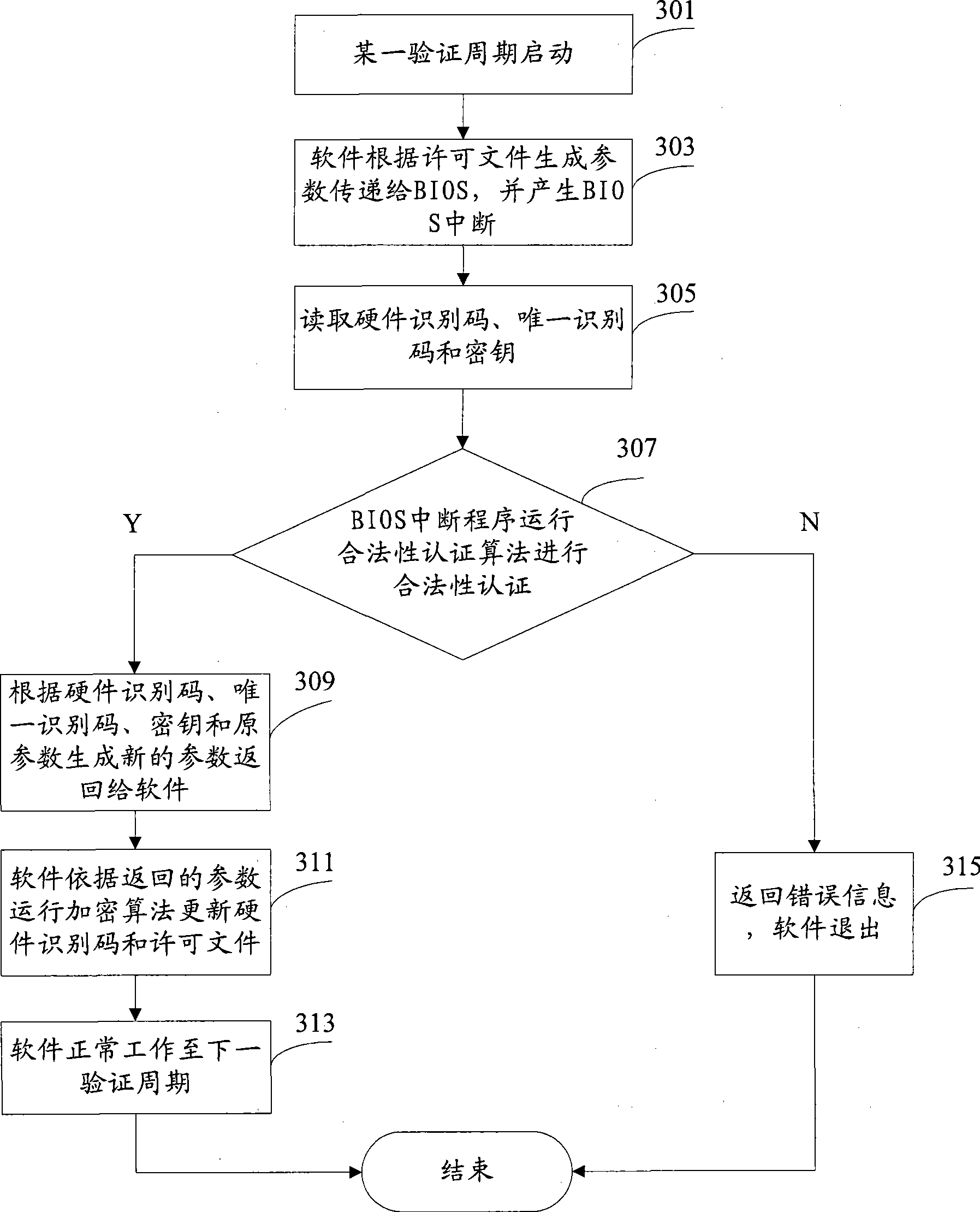
[0035] Because the present invention relates to the calling of BIOS, before introducing the present invention, at first the effect of computer BIOS and its work process are introduced:
[0036] 1. The first is the self-test process: After the computer is powered on, the system will have a process of checking each internal device, which is completed by a program usually called POST (Power On Self Test / power-on self-test) , which is also a function of the BIOS program. The complete self-inspection includes the test of CPU, 640K extended memory above 1M, ROM, motherboard, CMOS memory, serial and parallel ports, display card, soft hard disk subsystem and keyboard.
[0037] 2. If a problem is found during the self-inspection, the system will give a prompt message or whistle a warning. If there is no problem, start the initialization process after completing the self-test, that is, the BIOS will search for valid boot drives such as soft drives, hard drives, CDROMs, and network serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com