Method for prewarning aggression based on software defect and network aggression relation excavation
A network attack and software defect technology, applied in the direction of electrical components, transmission systems, digital transmission systems, etc., can solve the problems that software developers cannot provide constructive software defect repair opinions, difficult software security quality, and cannot fully respond to network attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
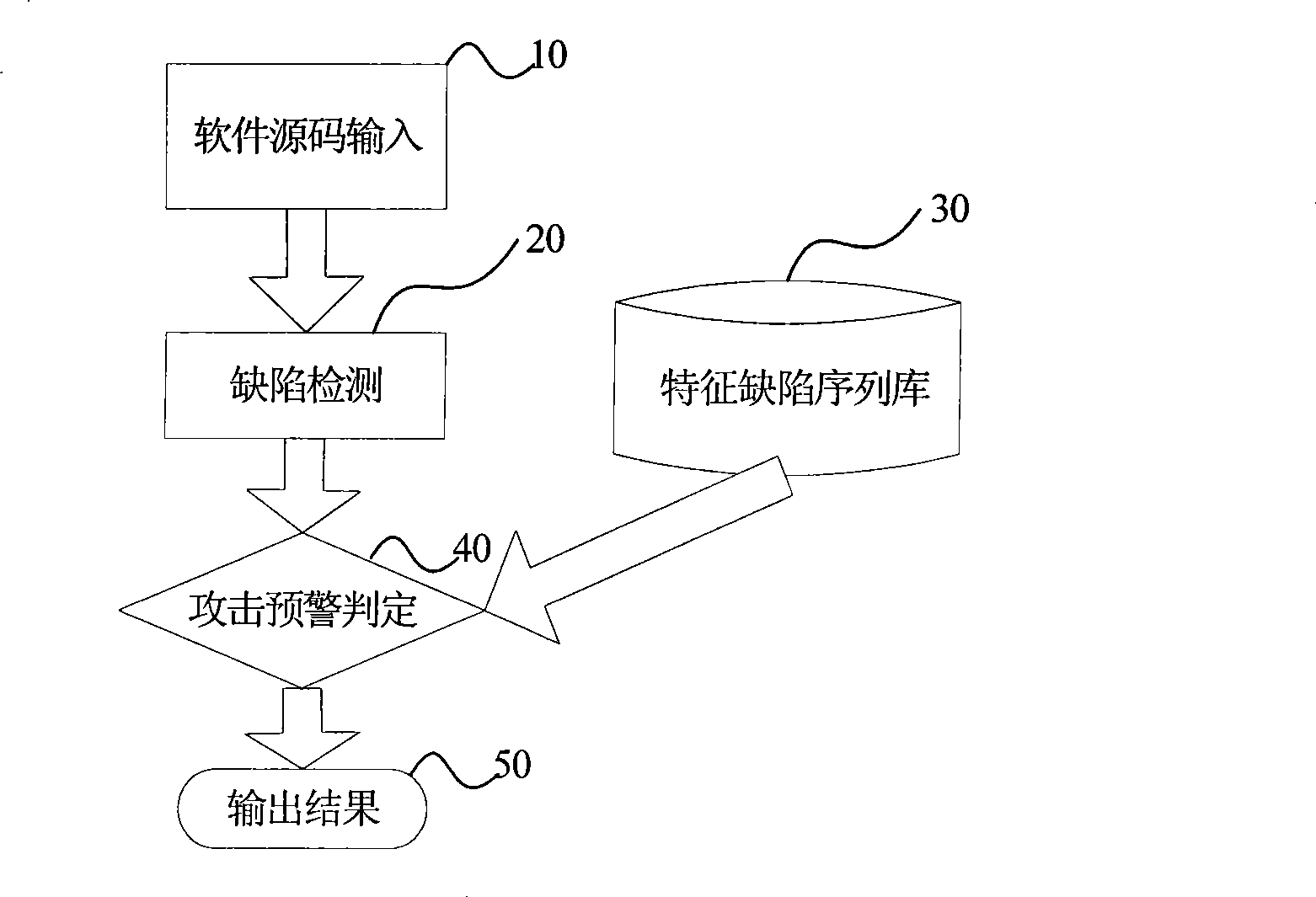
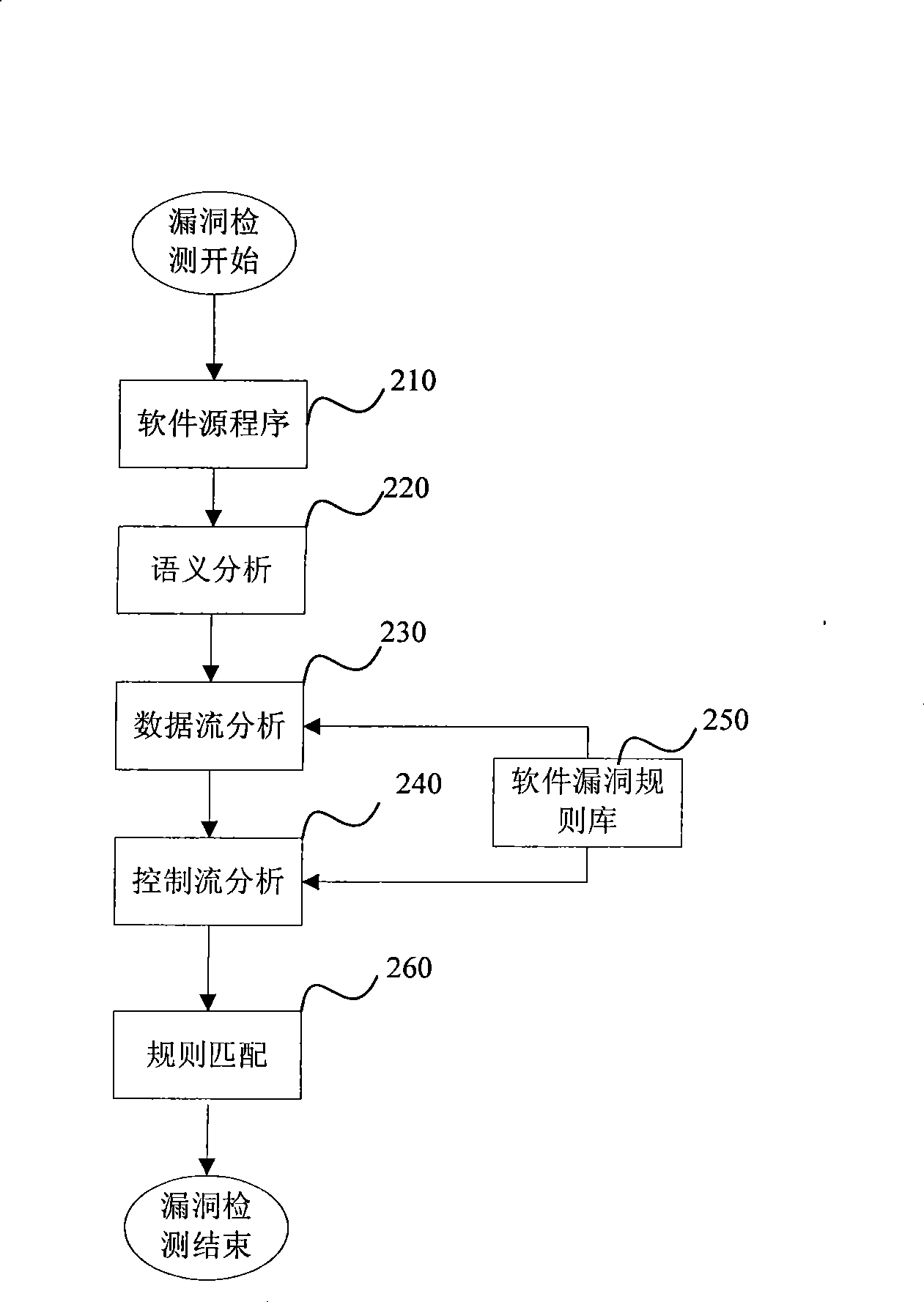
[0026] See figure 1 According to the technical solution of the present invention, the system at least includes: a defect detection subsystem; a characteristic defect sequence library subsystem, which adopts a defect implantation method to mine attack patterns associated with defect types through simulated attack experiments; an attack early warning and determination subsystem, Match the scanned defect types with the records in the characteristic defect sequence database, and output the successfully matched defect types and potential attack modes. Among them, the characteristic defect sequence library subsystem is connected to the attack early warning and judging subsystem, and the defect detection subsystem is connected to the attack early warning and judging subsystem.
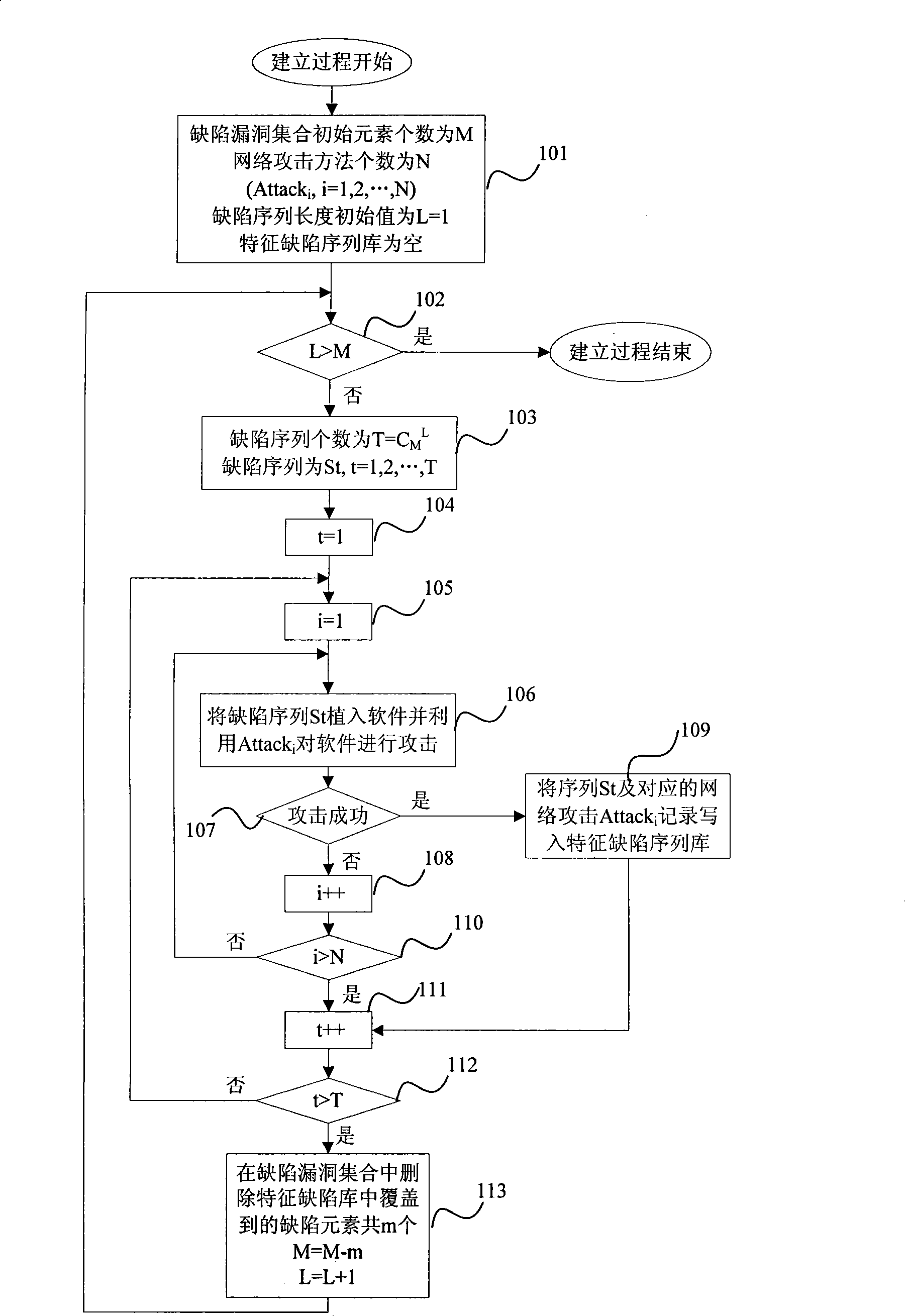
[0027] Refer to figure 2 , First go to step 101, currently the number of known software defect vulnerabilities is M, all vulnerabilities constitute an initial set, the number of commonly used network attack met...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com