Grading processing method and grading processing system for security event
A technology for security incidents and hierarchical processing, applied in the field of hierarchical processing of security incidents, which can solve problems such as inability to adapt to the discovery of the most important and urgent incidents, inability to grading the degree of harm of incidents, and delay in processing security incidents.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
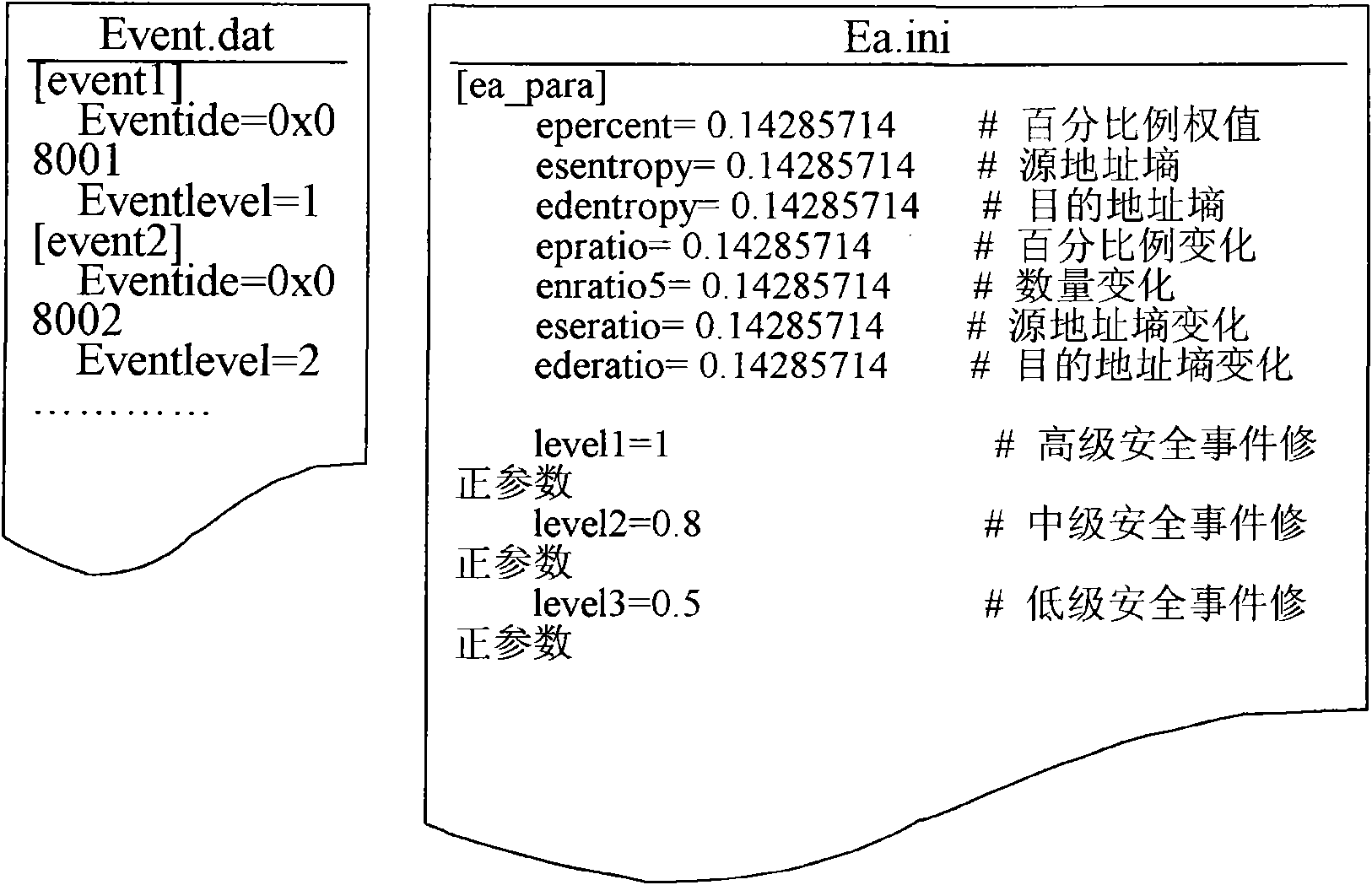
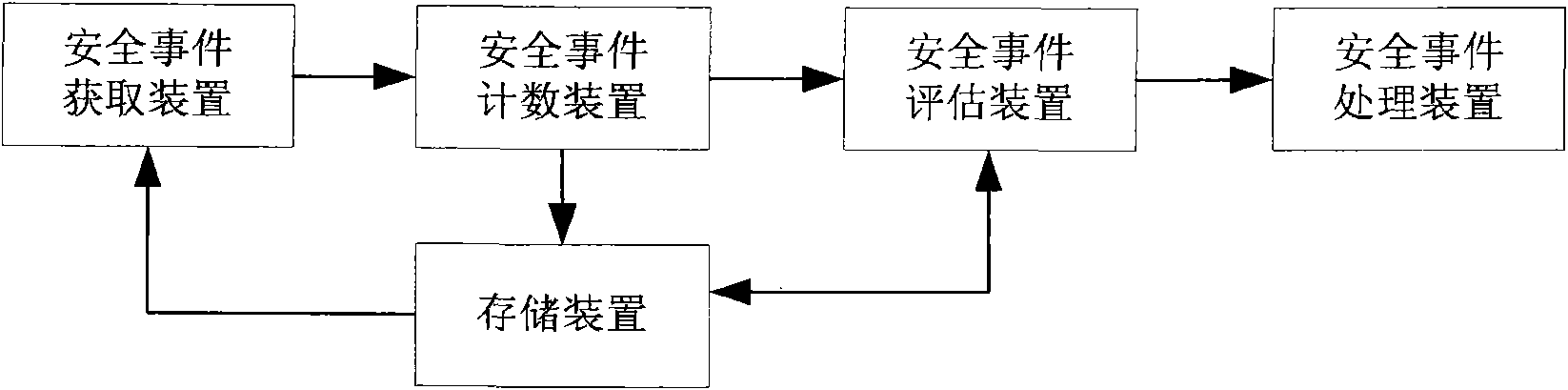
[0070] The invention comprehensively evaluates the parameters related to the hazard degree of the security event, such as the security level, occurrence times, address distribution and parameter changes, so as to complete the determination and processing of the hazard level of the security event more objectively and accurately.
[0071] The following takes the hierarchical processing of IDS system security events as an example, and describes the present invention in detail in conjunction with the accompanying drawings and specific implementations.
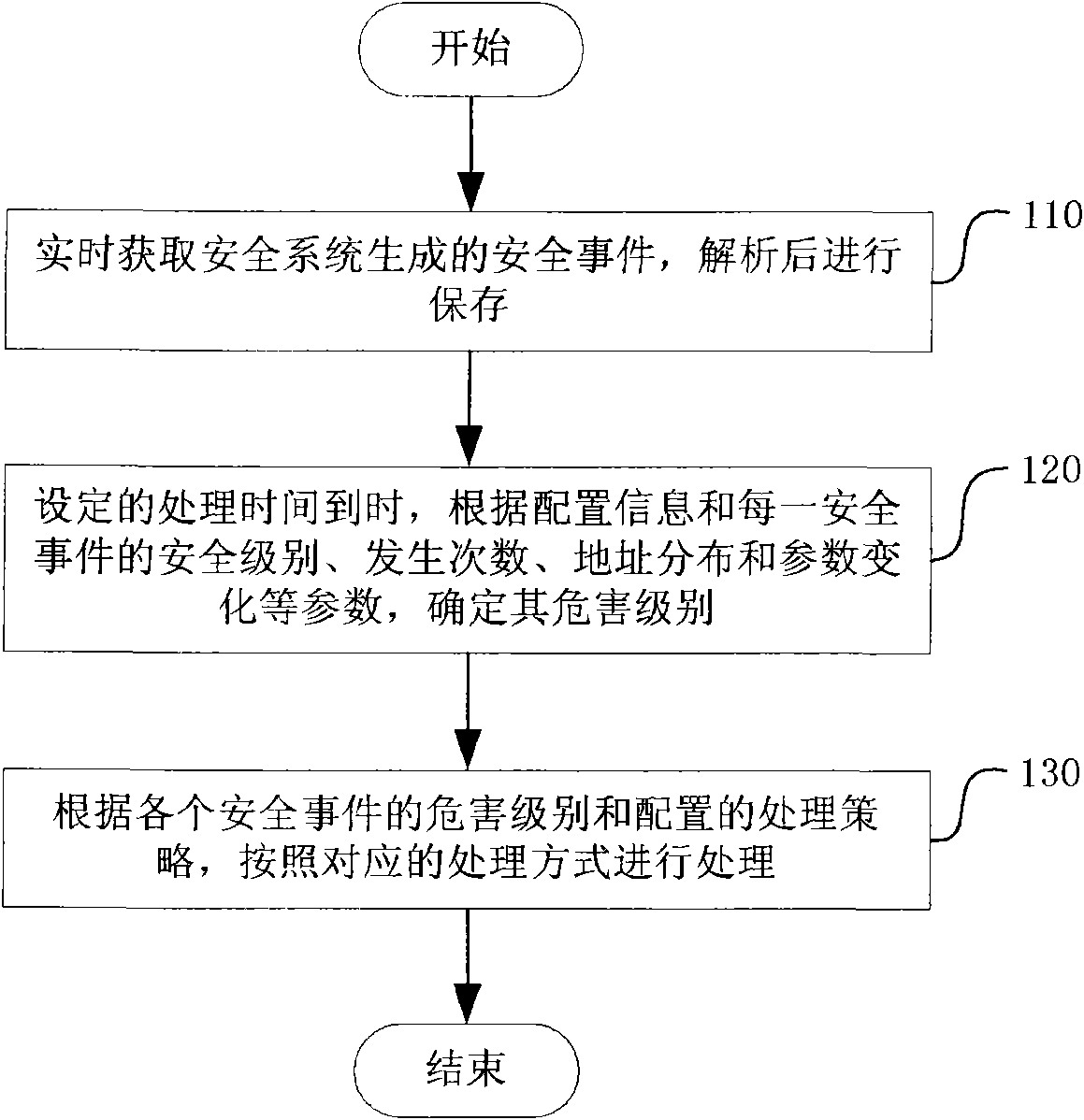
[0072] figure 1 A flow chart showing the hierarchical processing method for security incidents in this embodiment includes the following steps:
[0073] S110, obtain the security event generated by the security system in real time, and store it after parsing, where the security event includes source address and destination address information;
[0074] In this embodiment, the interface function is called to read the security event...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com