Method, network equipment and network system for defending distributed denial service DDoS attack
A technology of network equipment and network systems, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of the characteristics of attacks and the thresholds for judging attacks that are not easy to determine, false positives and false negatives, etc. The effect of effective defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
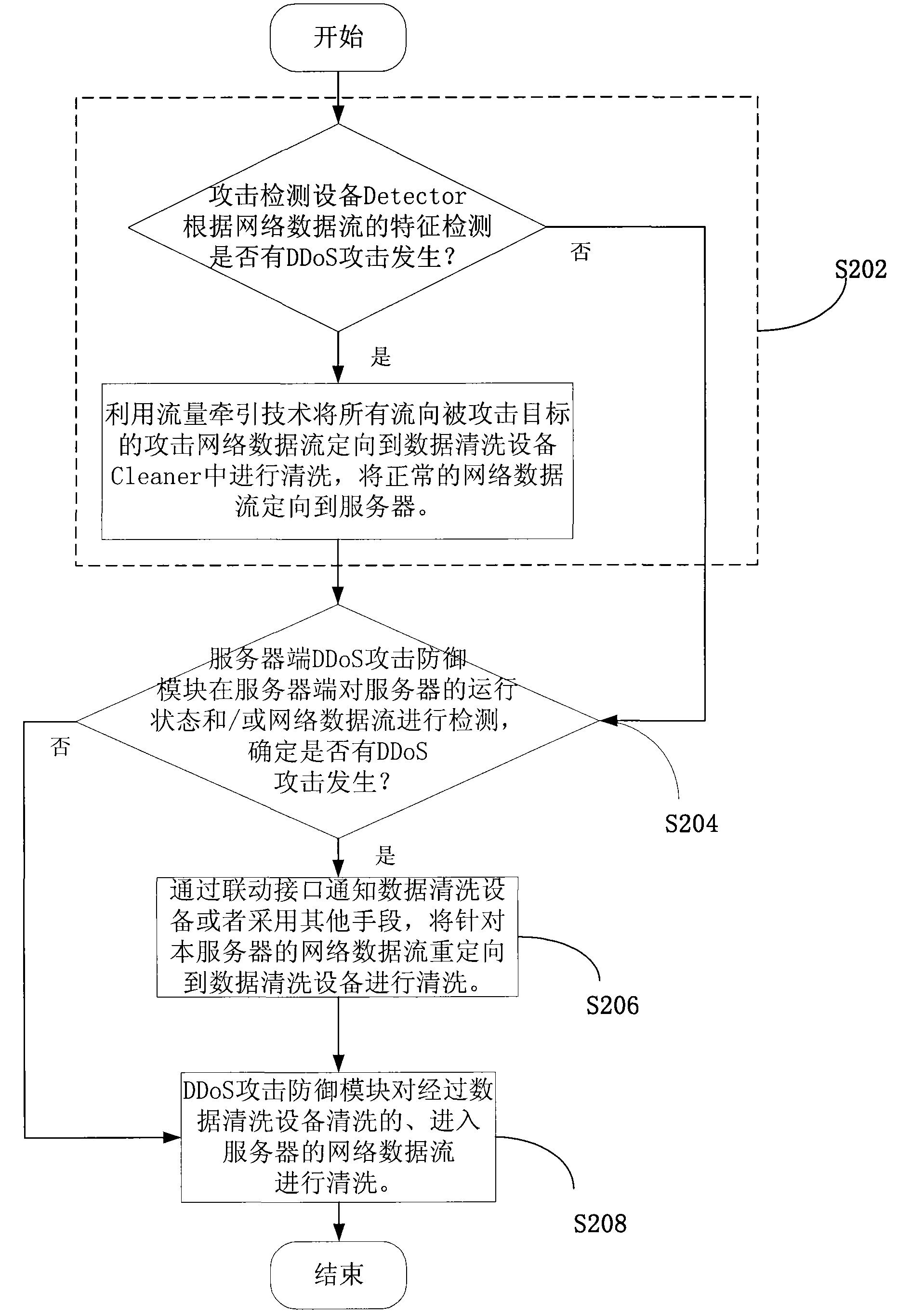
[0031] The embodiment of the present invention proposes to install a DDoS attack defense module on the attacked target server, which can detect the running status of the server and / or the network data flow entering the server, and then feed back the detection results to the data flow cleaning equipment. The server-side DDoS attack defense module can be hardware or software, and it can be not limited to network interface layer, kernel-level or application-level software. This module can be an independent software or a part of a security software. It can be from Hardware or software for defense at all levels.
[0032] The running state of the server may be the running load of the central processing unit, the memory, network traffic, and the like.
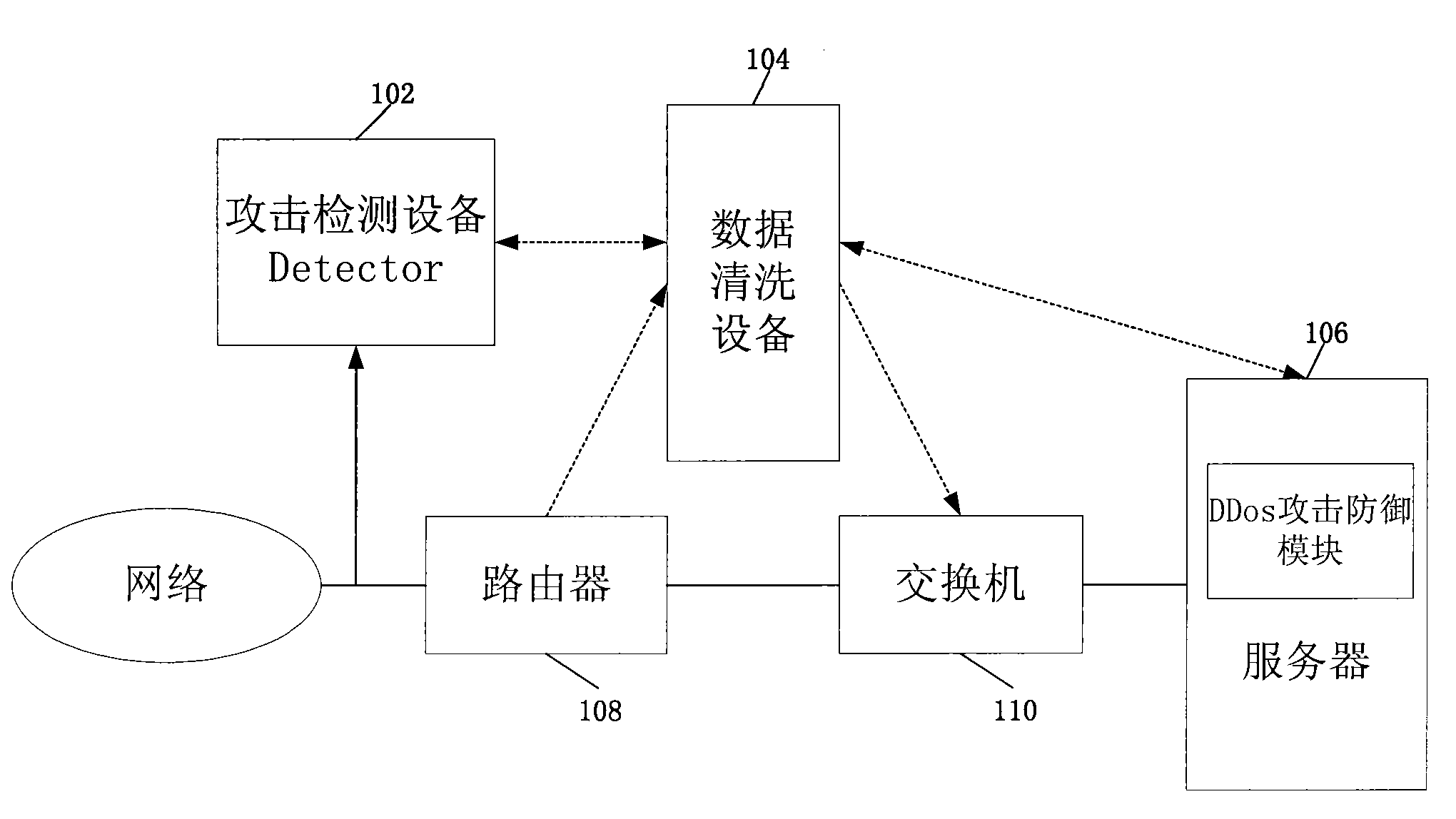
[0033] like figure 1 As shown, the network system of this embodiment includes:
[0034] The attack detection device Detector102 is used to detect the network data flow on the network side; when a DDoS attack against a certain serve...
Embodiment 2
[0052] In this embodiment, there is no need to install an attack detection device Detector on the network side, and only a DDoS attack defense module needs to be installed on the attacked target server.
[0053] like Figure 4 As shown, the network system of this embodiment includes:
[0054] The data flow cleaning device Cleaner402 is used to negotiate with the attack detection device Detector and the server, and clean the network data flow according to the negotiation result;
[0055] At least one server 404 is used to receive and process the network data flow from the network side, which includes: a DDoS attack defense module, which is used to detect the running status of the server and / or network data flow, and feed back the detection result to the data cleaning device; furthermore, the data stream that has been cleaned by the data cleaning device can also be cleaned.
[0056] The data cleaning device Cleaner can be deployed anywhere on the front end of the server. like...
Embodiment 3
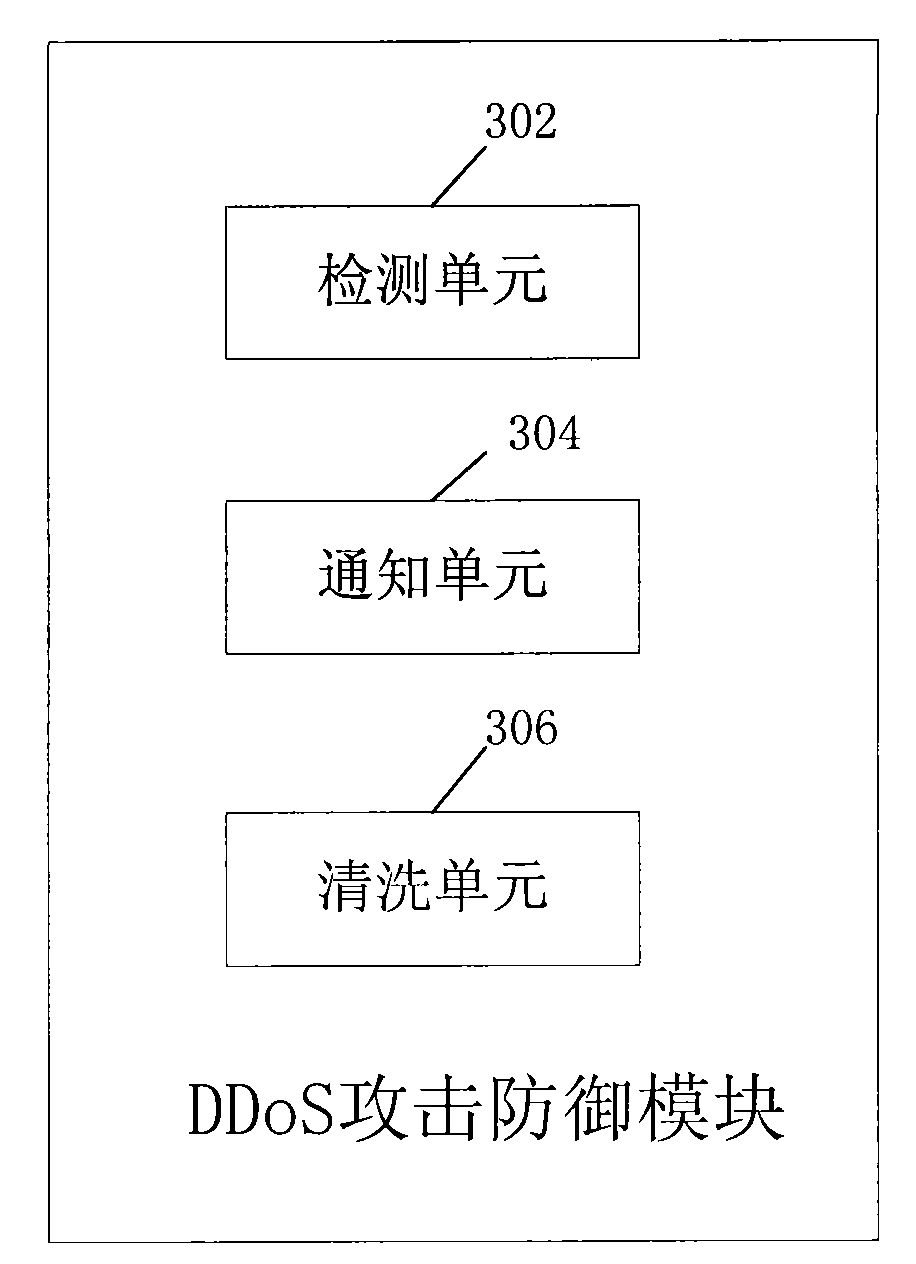
[0066] The solution of this embodiment adds a load alarm mechanism on the server, see Image 6 As shown, the DDoS attack defense module may further include:
[0067] The load alarm unit 602 is used to monitor the traffic of the network data stream entering the server, and send an alarm to the data cleaning device when the data stream traffic reaches a preset value, such as a self-defined dangerous level.
[0068] Detecting the traffic entering the server can be realized by detecting the traffic on the network card, which can be divided into levels according to the capacity, and can be linked with the cleaning and filtering intensity of the data cleaning equipment. When the traffic passing through the network card of the server reaches a dangerous level, an alarm is sent to the data cleaning device.
[0069] Through the embodiment of the present invention, the server end can be made to alarm and defend against DDos attacks according to the traffic, thereby improving the securi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com