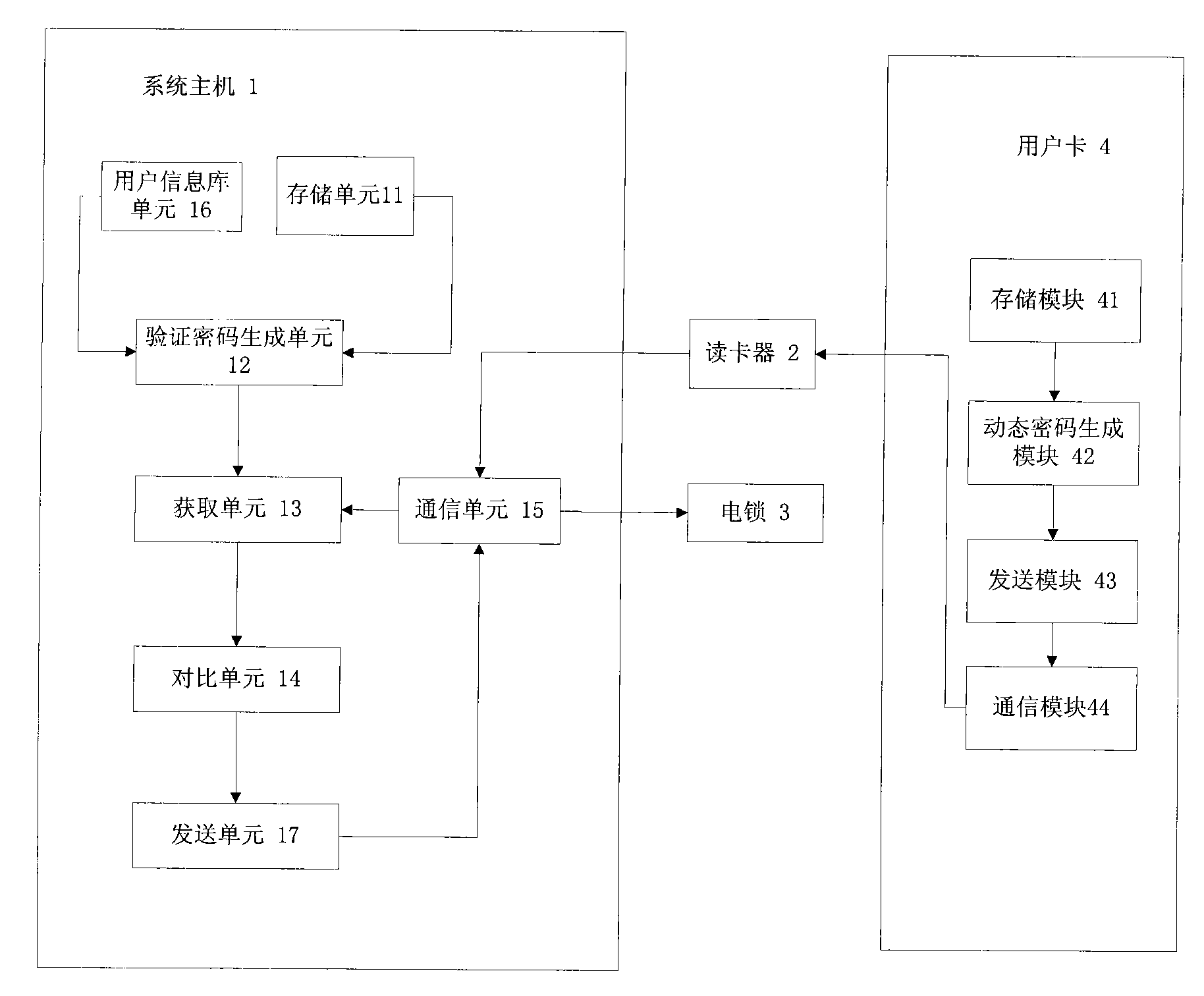Access control system generated and verified on the basis of dynamic password and authentication method thereof
A technology of dynamic password and access control system, applied in the field of identity authentication, which can solve problems such as loss and copying
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Such as figure 1 As shown, the embodiment of the present invention includes a system host 1, a card reader 2, an electric lock 3 and multiple user cards.
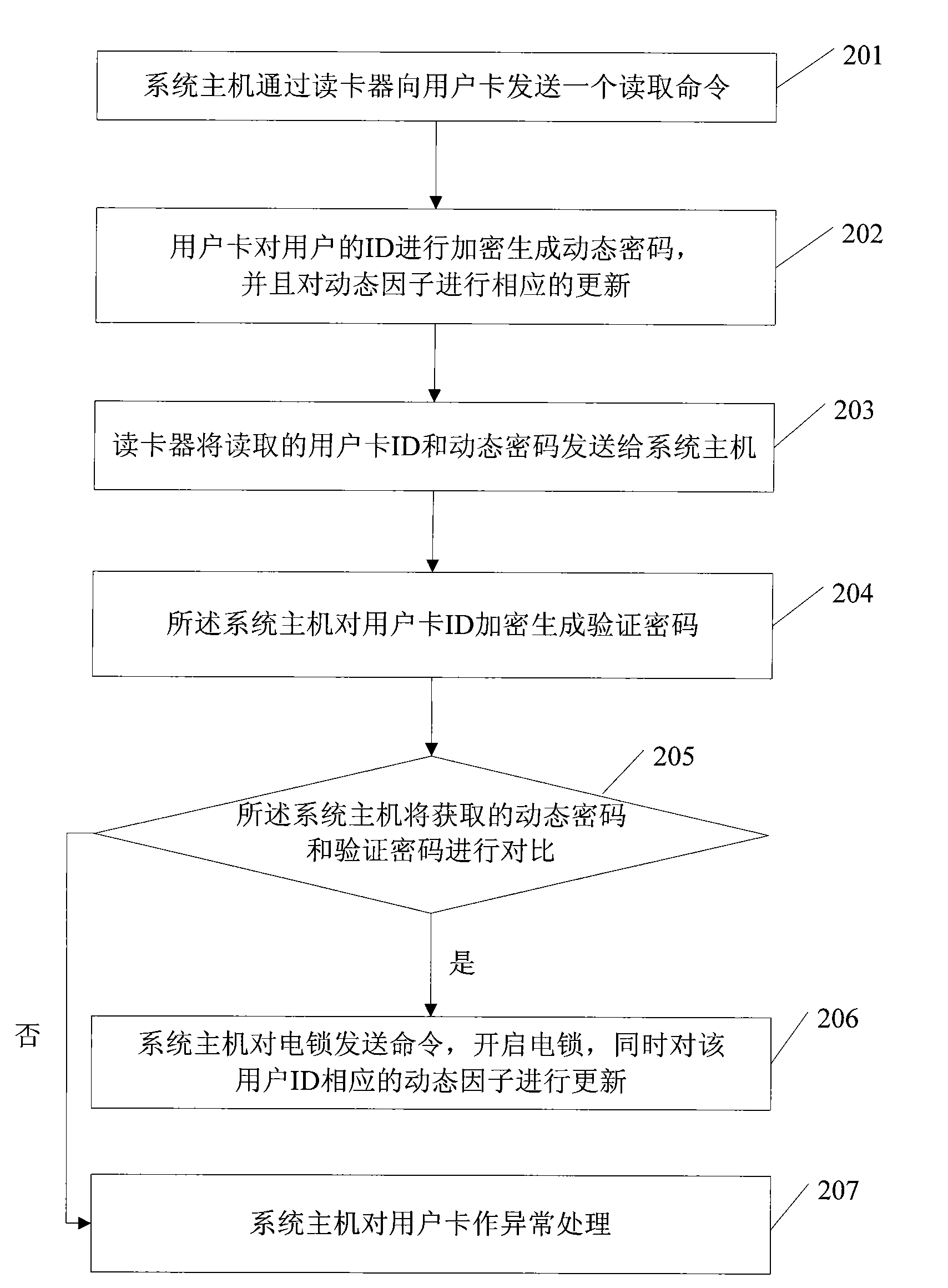
[0050] The system host 1 includes a storage unit 11 , a verification password generation unit 12 , an acquisition unit 13 , a comparison unit 14 , a communication unit 15 , a user information database unit 16 , and a sending unit 17 . The storage unit 11 in the system mainframe 1 stores preset algorithms and keys required to generate the verification password, and the preset algorithms can be HOPT, DES, RSA, SHA algorithms or preset by the manufacturer. The verification password generating unit 12 in the system mainframe 1 is used to use the preset algorithm and key stored in the storage unit 11 to generate a verification password according to the ID of the user card obtained and the dynamic factor of the card stored in the user information library unit 16 . The obtaining unit 13 in the system host 1 is used to obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com