Method and system based on EAP authentication
A technology for authentication terminal and authentication information, which is applied in the field of information security and can solve the problems of inconvenient unified management and low security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
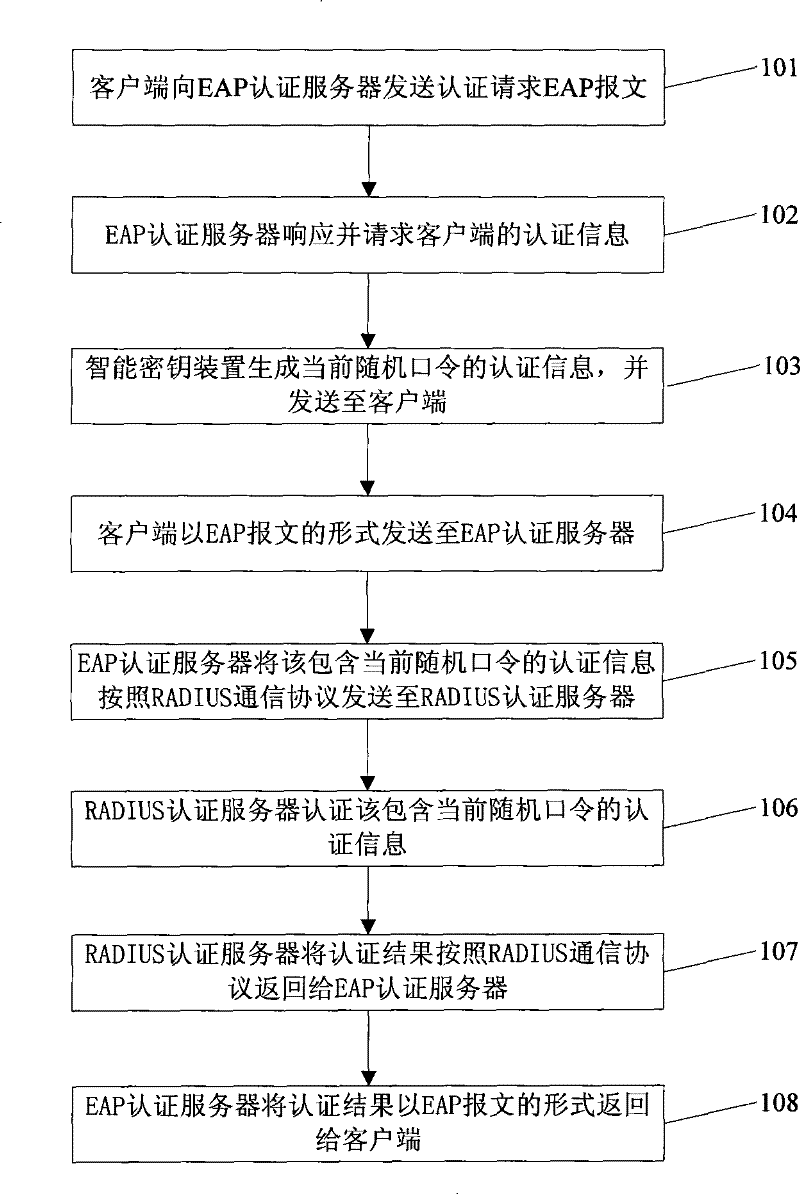
[0093] see figure 1 , the embodiment of the present invention provides a method based on EAP authentication, which specifically includes the following steps:
[0094] Step 101: the client sends an authentication request EAP packet to the EAP authentication server.
[0095] Step 102: The EAP authentication server responds and requests authentication information of the client.
[0096] The EAP authentication server may also be other forms of network access control terminals, such as routers.
[0097] Step 103: The smart key device generates the authentication information of the current random password and sends it to the client.
[0098] The step of generating the current random password by the smart key device is specifically: the smart key device calculates the built-in generating elements according to the preset random password algorithm to generate the current random password. The generation element is a time generation element, an event generation element, or the like. ...
Embodiment 2
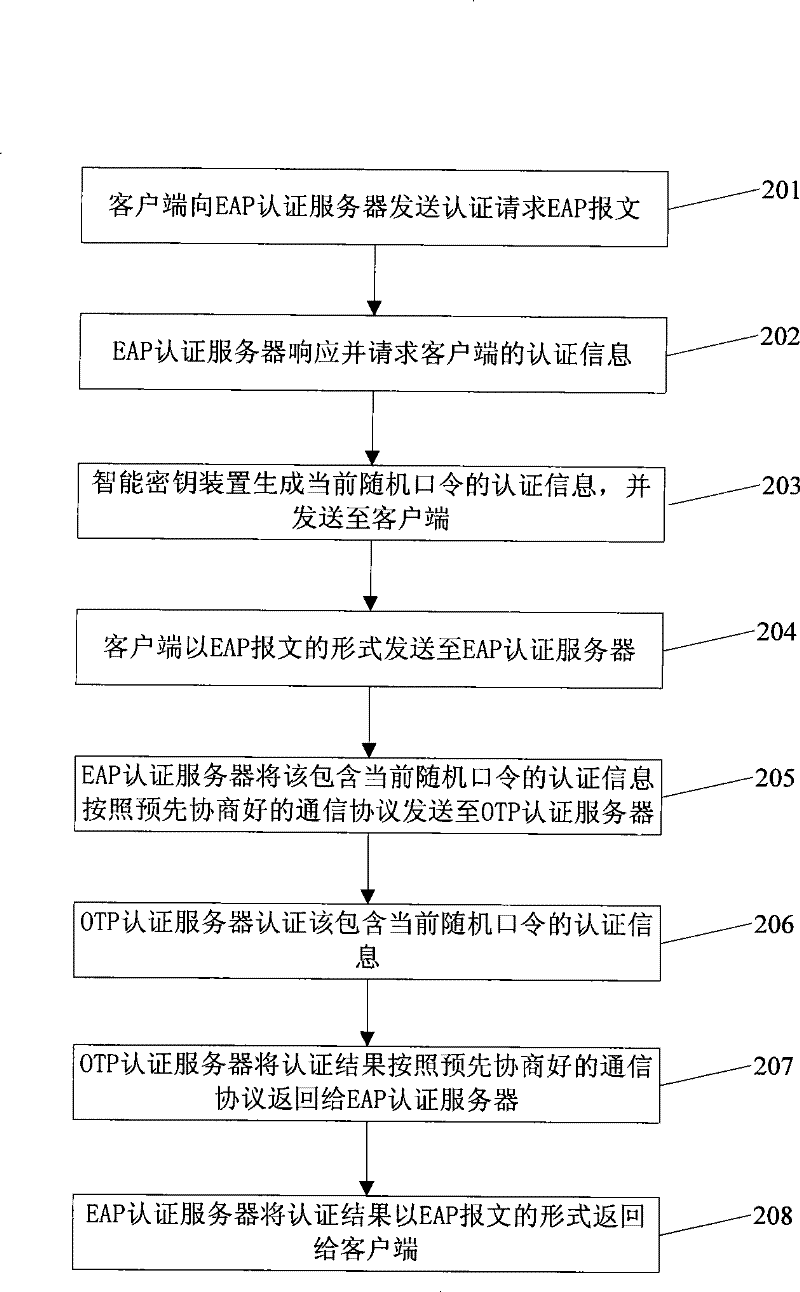
[0112] see figure 2 , the embodiment of the present invention provides a method based on EAP authentication, which specifically includes the following steps:
[0113] Step 201: the client sends an authentication request EAP packet to the EAP authentication server.
[0114] Step 202: The EAP authentication server responds and requests authentication information of the client.
[0115] The EAP authentication server may also be other forms of network access control terminals, such as routers.
[0116] Step 203: The smart key device generates the authentication information of the current random password and sends it to the client.
[0117] The step of generating the current random password by the smart key device is specifically: the smart key device calculates the built-in generating elements according to the preset random password algorithm to generate the current random password. The generation element is a time generation element, an event generation element, or the like. ...
Embodiment 3
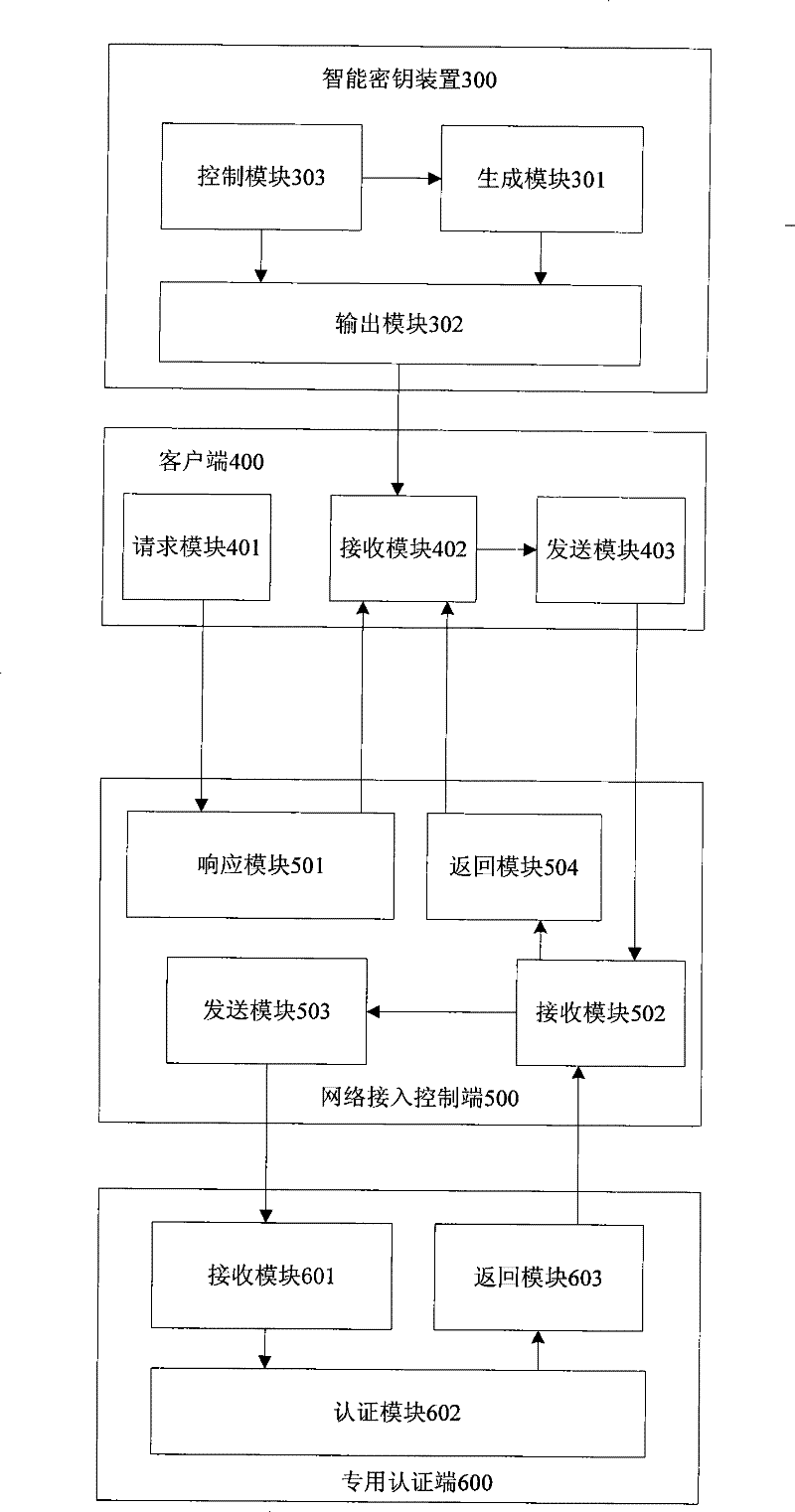
[0135] see image 3 , the embodiment of the present invention provides a system based on EAP authentication, including a smart key device 300, a client 400, a network access control terminal 500 and a dedicated authentication terminal 600,
[0136] The smart key device 300 includes a generation module 301, an output module 302 and a control module 303:
[0137] The generation module 301 is used to generate the current random password according to the preset random password algorithm under the control of the control module 303, and send the current random password to the output module 302;
[0138] The output module 302 is used to send the authentication information including the current random password to the client 400 under the control of the control module 303;
[0139] The control module 303 is used to control the generating module 301 to generate the current random password, and control the output module 302 to output the authentication information including the current ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com