Access method and access device
An access method and technology for access devices, which are applied in security devices, connection management, network topology, etc., can solve problems such as threshold setting restrictions, inconvenience for users, and inability to perform network security configuration work, and achieve the effect of secure connection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
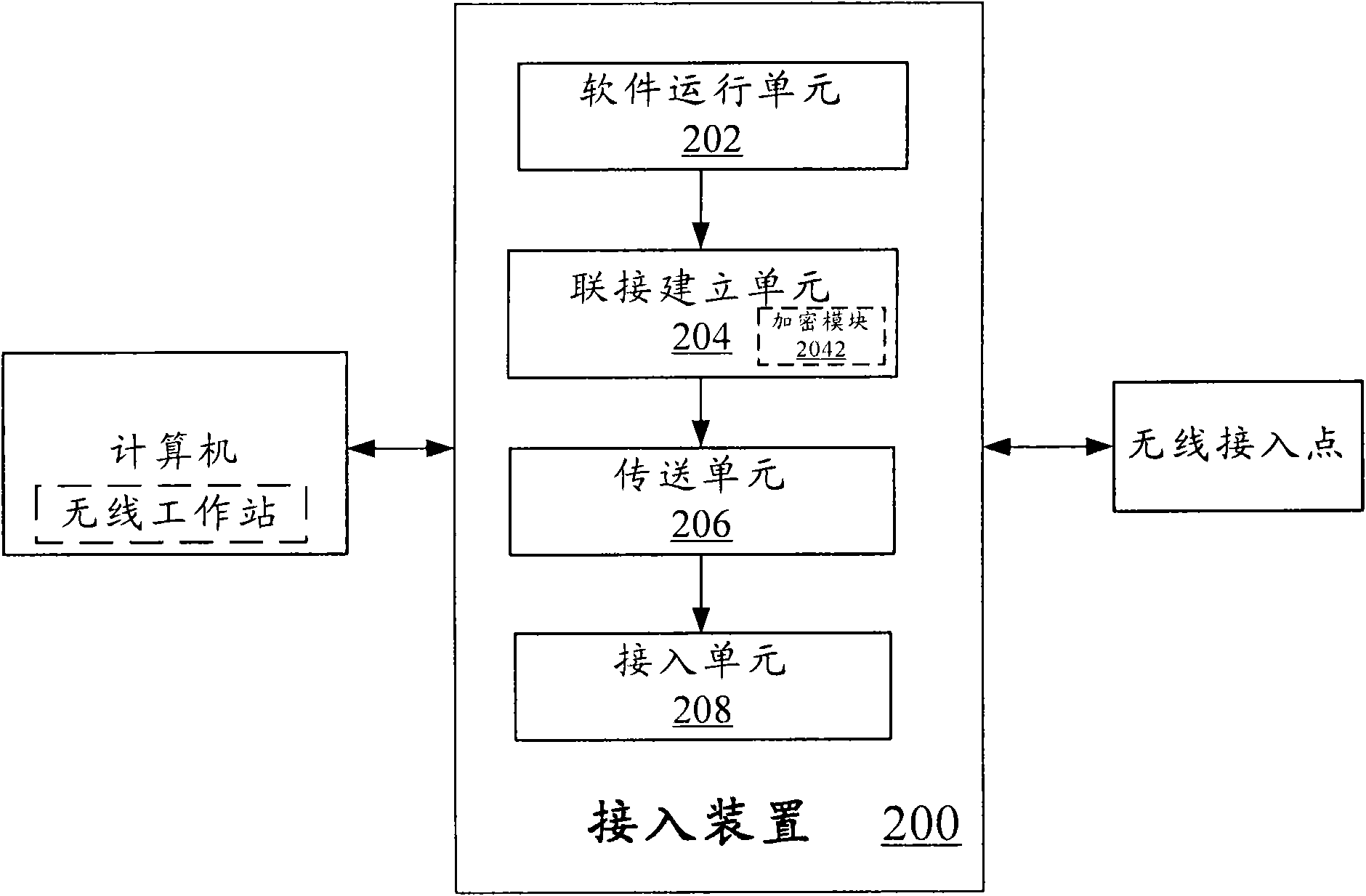
Image
Examples
no. 1 example
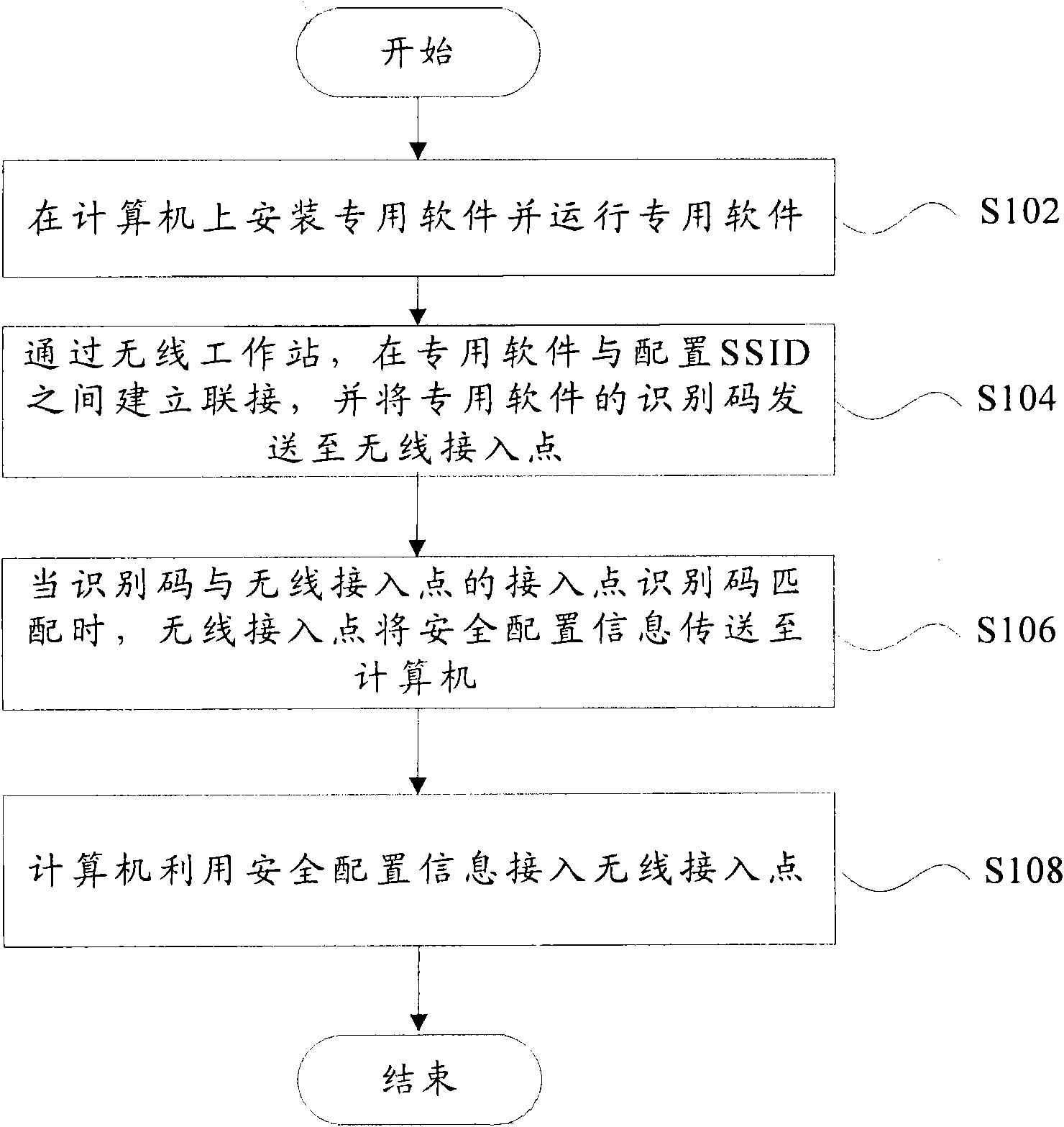
[0064] image 3 is a flowchart of processing after system startup on the access point side according to the first embodiment of the present invention. Such as image 3 As shown, in the access point test, the workflow after the system starts is:
[0065] The access point detects whether Easy_Net_Work has successfully established a connection with the configured SSID of the access point: Easy_Connecting, wherein, if successful, perform the following operations, and end this detection if unsuccessful;
[0066] After Easy_Net_Work is successfully connected to Easy_Connecting, the access point detects whether the identification code sent by Easy_Net_Work to the access point is consistent with the identification code of the access point itself. If it is consistent, perform the following operations. If not, end this detection;
[0067] After the identification code is successfully matched, the access point obtains the security configuration information of the user SSID, such as the...
no. 2 example
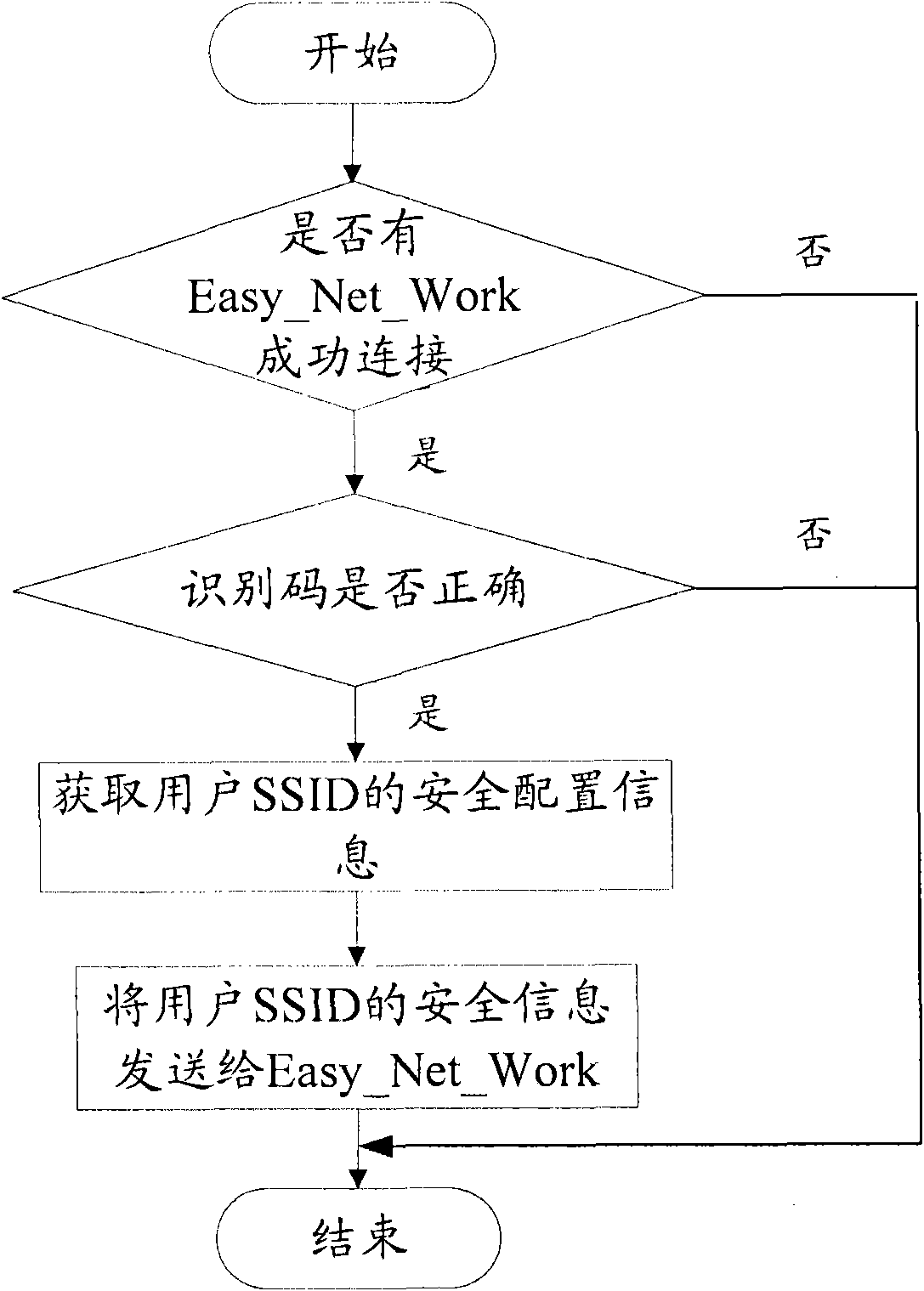
[0070] Figure 4 is a flowchart of processing after computer-side system startup according to the second embodiment of the present invention. Such as Figure 4 As shown, the workflow on the computer side is:
[0071] The user runs the software Easy_Net_Work;
[0072] Easy_Net_Work connects the configuration SSID of the access point through the wireless workstation: Easy_Connecting, wherein, if the connection is successful, perform the following operations, and if not, end the connection operation;
[0073] After the connection is successful, Easy_Net_Work sends the identification code to the access point;
[0074] If the identification code is correct, obtain the security configuration information of the user SSID from the access point, and perform the following operations, if the identification code is incorrect, end this operation;
[0075] Use the obtained security configuration information to configure the wireless workstation. After the configuration, the wireless wor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com