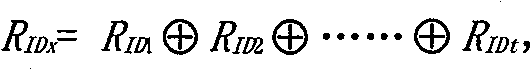Node legitimacy multiple-authentication method in layer cluster type wireless self-organization network
A wireless self-organizing, layer-clustering technology, applied in wireless communication, network traffic/resource management, electrical components, etc., can solve the problems of single authentication form and insufficient security strength.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
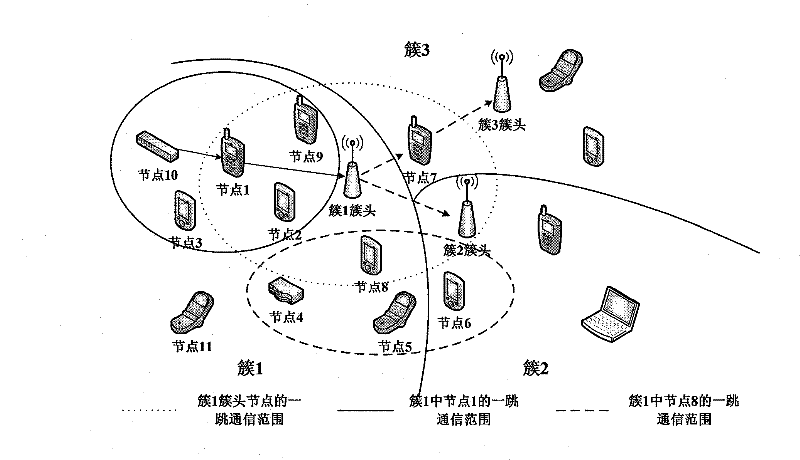
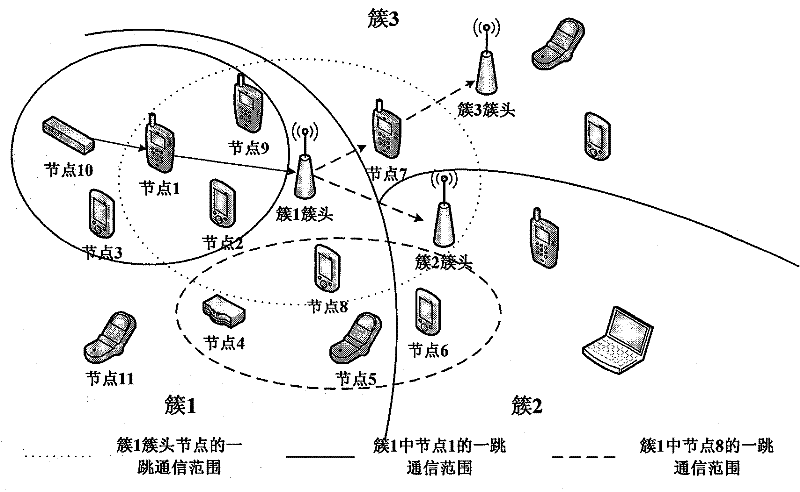
[0062] The following will be figure 1 As an example, a specific example is used to further illustrate the technical solution and method flow of the present invention in detail.
[0063] First complete the initialization of network security information and network deployment, that is, the formation of a layered cluster topology. To figure 1 As an example, it is divided into 3 clusters, which are marked as cluster 1, cluster 2 and cluster 3. C 1 , C 2 And C 3 Respectively as its cluster identifier. At this time, each node has an identity generation function f(x) and a set of prime numbers X, a same pre-configured key K and a different session key K IDi . Take node 1 as an example, it will randomly select an element in the prime number set X, and assume that it is x without loss of generality. 1 , Calculate the identity ID of node 1 1 =f(x 1 ), and x 1 = F 1 (ID 1 ) Is established, the session key corresponding to node 1 is K ID1 , The session key corresponding to the cluster head...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com