Method for protecting security of mobile communication terminal data and device thereof
A mobile communication terminal and data security technology, which is applied in the field of protecting mobile communication terminal data security, can solve problems such as being too simple, easy to be cracked, and insufficiently comprehensive data protection, so as to achieve the effect of protecting security and ensuring that it will not be leaked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
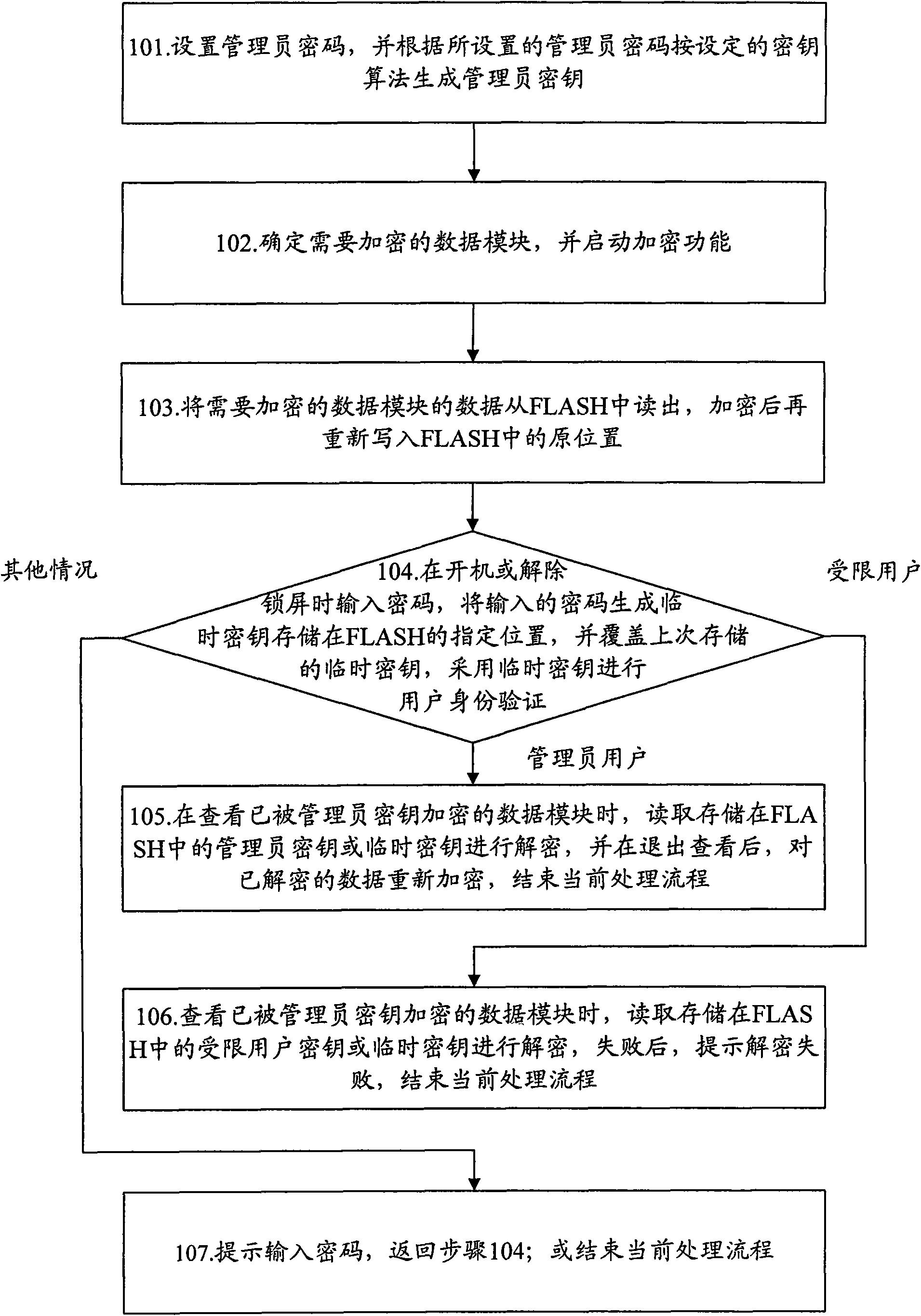
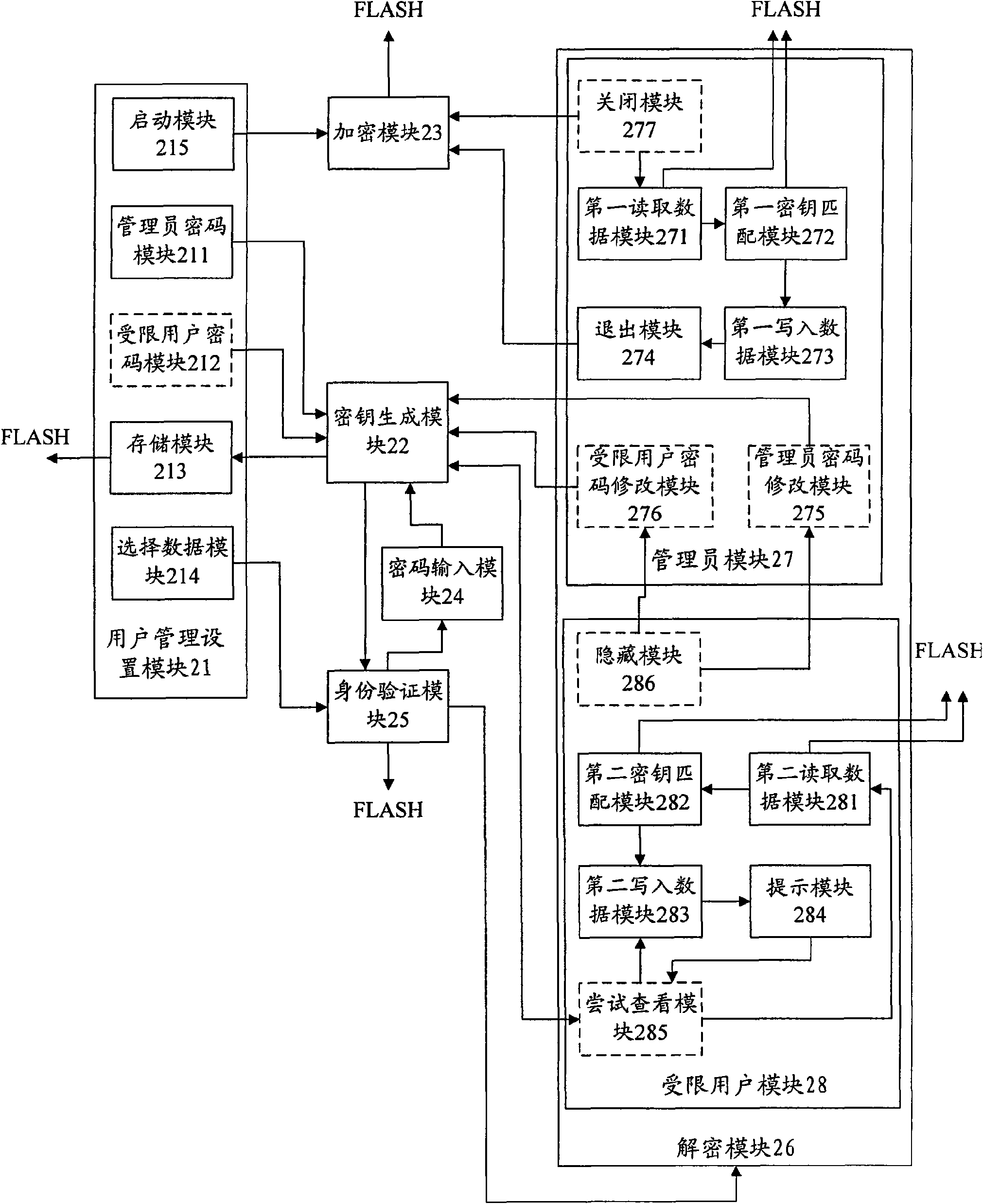
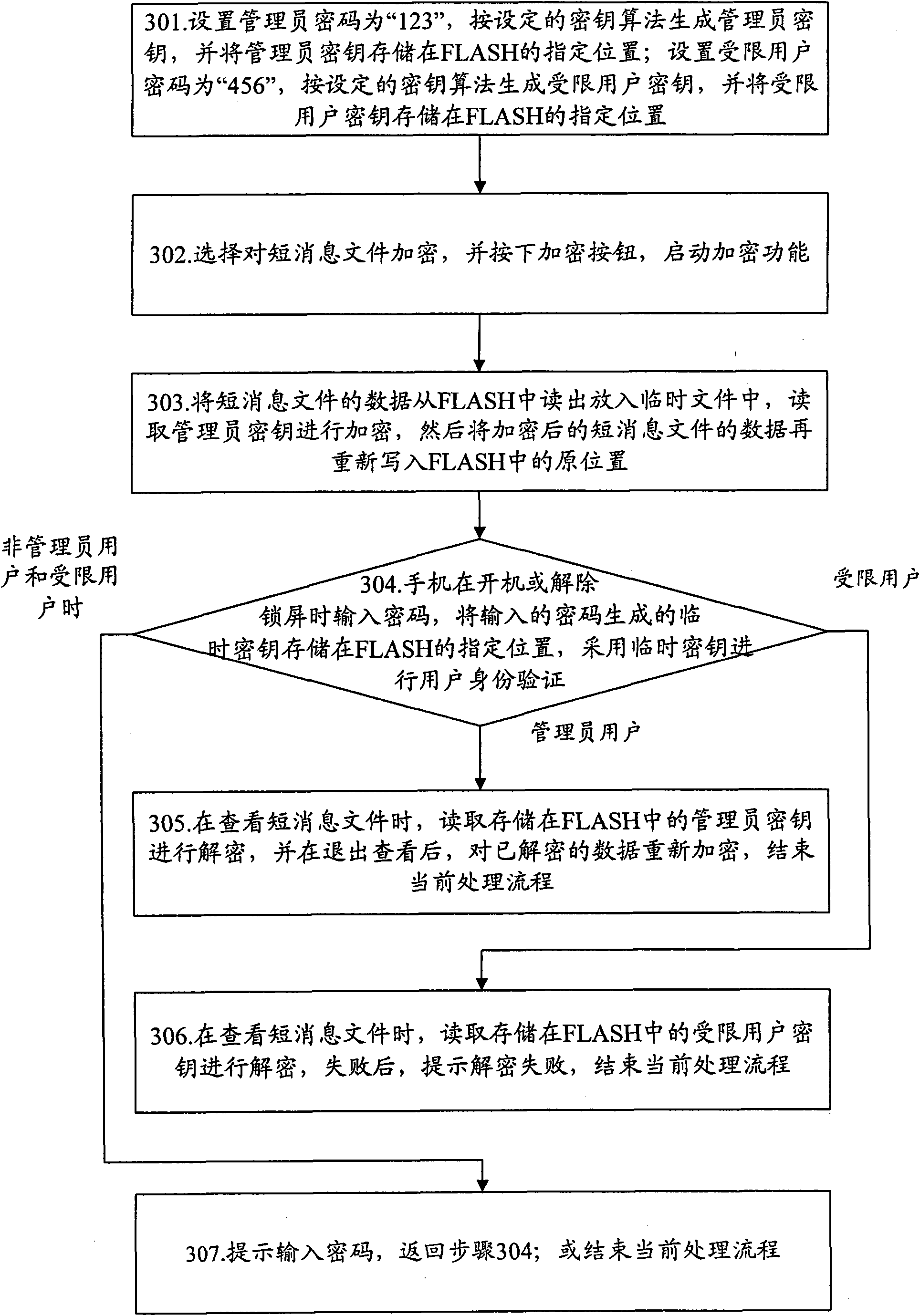
[0037] The basic thought of the present invention is: respectively set administrator's password, limited user's password, and generate administrator's key, restricted user's key respectively according to setting key algorithm; After exporting, encrypt according to the generated administrator key, and then re-write the FLASH; unlock the administrator password and decrypt the administrator key to view the data of the encrypted data module; unlock only the unencrypted data module through the restricted user password The data of the data module.
[0038] Specifically, after successfully unlocking through the administrator password, when viewing the data of the data module encrypted by the administrator key, read the administrator key stored in FLASH to decrypt; after successfully unlocking through the restricted user password , when viewing the data of the data module that has been encrypted by the administrator key, read the restricted user key for decryption, because the encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com