Security alarm system and security alarm method
A security alarm and security technology, applied in the direction of alarms, closed-circuit television systems, instruments, etc., can solve the problems of inability to centrally manage equipment, security gateways cannot control the action of network cameras, etc., to improve the level of intelligent management, increase security, The effect of unified management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
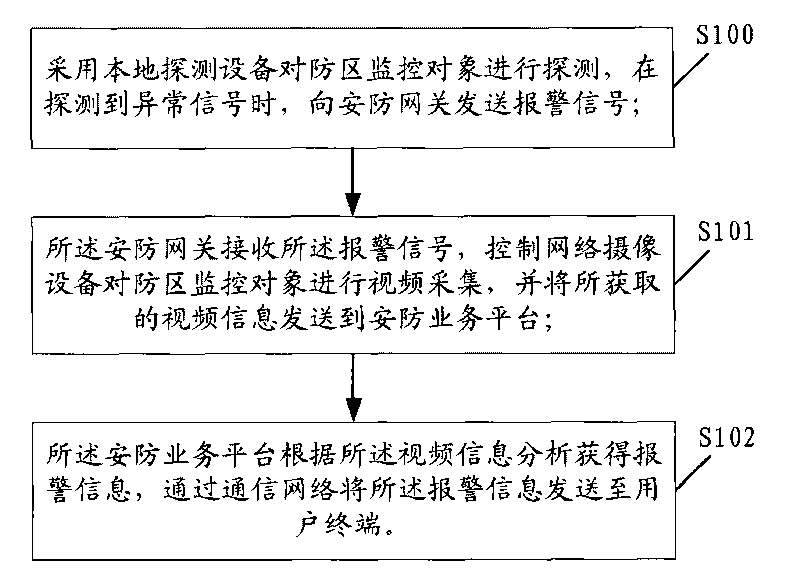
[0028] The first example of the alarm process of the security alarm system is as follows:
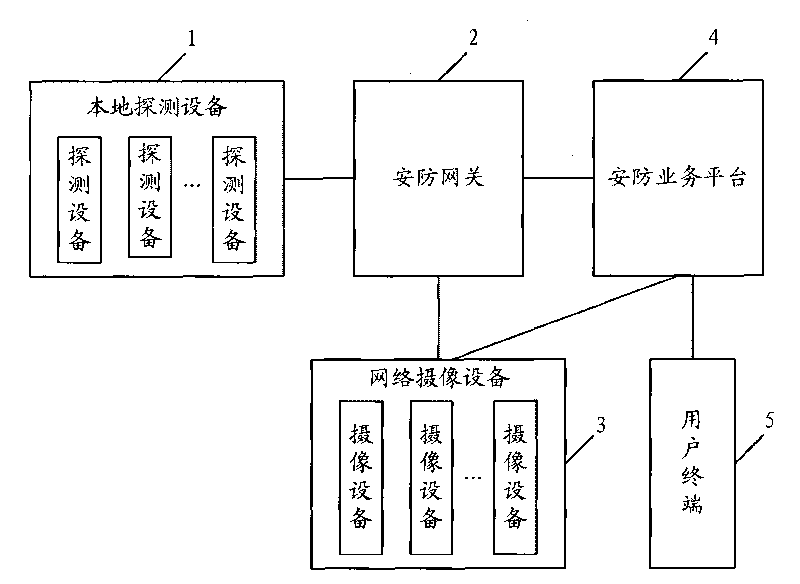
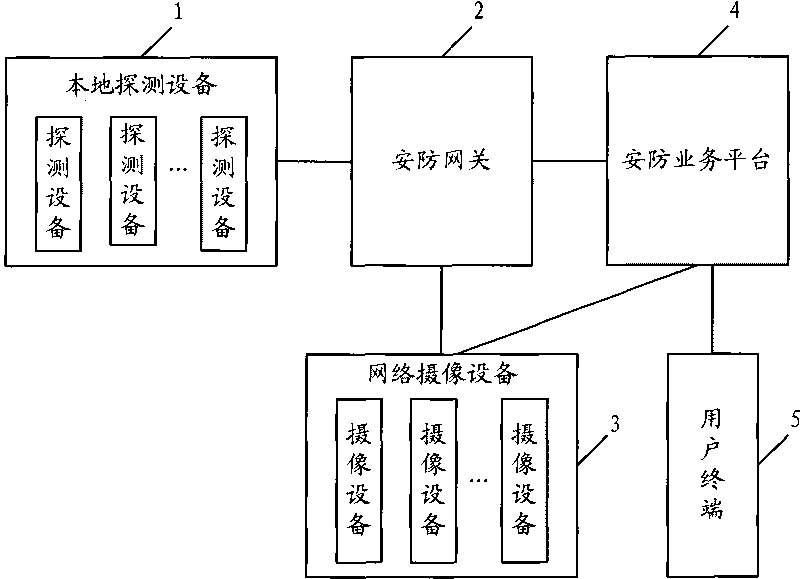
[0029] The local monitoring device 1 detects the monitoring objects in the defense zone, and when an abnormal signal is detected, it sends an alarm signal to the security gateway 2;
[0030] The security gateway 2 receives the alarm signal sent by the local monitoring device 1, and determines the location of the alarm according to the ID number of the detection device that sent the alarm signal, and determines the location of the alarm according to the linkage logic of the detection device and the camera device configured by the user. The alarm signal detects the camera equipment corresponding to the equipment, and sends control information to the camera equipment, triggering the camera equipment to perform video capture of the surveillance object in the defense area. Among them, the designated transmission mode in the control information is JPEG image format BMP image format and other commo...
no. 2 example
[0034] The second implementation example of the alarm process of the security alarm system is as follows:
[0035] The second embodiment is similar to the flow of the above-mentioned first embodiment. The main difference is that after receiving the alarm signal of the local monitoring device 1, the security gateway 2 selects the correlation according to the linkage relationship between the detection device and the camera device configured by the user. The camera equipment is controlled to collect video of the monitored objects in the defense area, and the collected video information is returned to the security gateway 2. The security gateway 2 saves the video information returned by the camera device, and sends the device information and video information of the local monitoring device 1 to the security service platform 4; the security service platform 4 receives the device information and video information sent by the security gateway 2 and analyzes the monitoring objects in the ...
no. 3 example
[0036] The third implementation example of the alarm process of the security alarm system is as follows:
[0037] The process for remote users to query and access the security alarm system is as follows: the user queries the local monitoring equipment 1 through the WEB, WAP (Wireless Application Protocol) and client software of the user terminal 5, and the security service platform 4 receives the user terminal 5 After passing the security confirmation, the instruction is issued to the security gateway 2. The security gateway 2 verifies the legality of the information and executes the control action on the local monitoring device 1. After the execution is completed, the security gateway 2 transmits the execution result to the security gateway The service platform 4, the security service platform 4 then transmits the execution result to the service terminal 5.
[0038] The process for remote users to control the security alarm system for video capture is as follows: the user controls...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com