Information system security risk assessment model based on combined evaluation method
An information system and security risk technology, which is applied in the field of information system security risk assessment model based on the combined assessment method, can solve the problems of inconsistency of assessment conclusions, difficulty in obtaining consistent assessment, differences, etc., to overcome one-sidedness and limitations, Reduce subjectivity and assess the effects of cost, efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] Embodiments of the present invention will be described in detail with reference to the accompanying drawings.
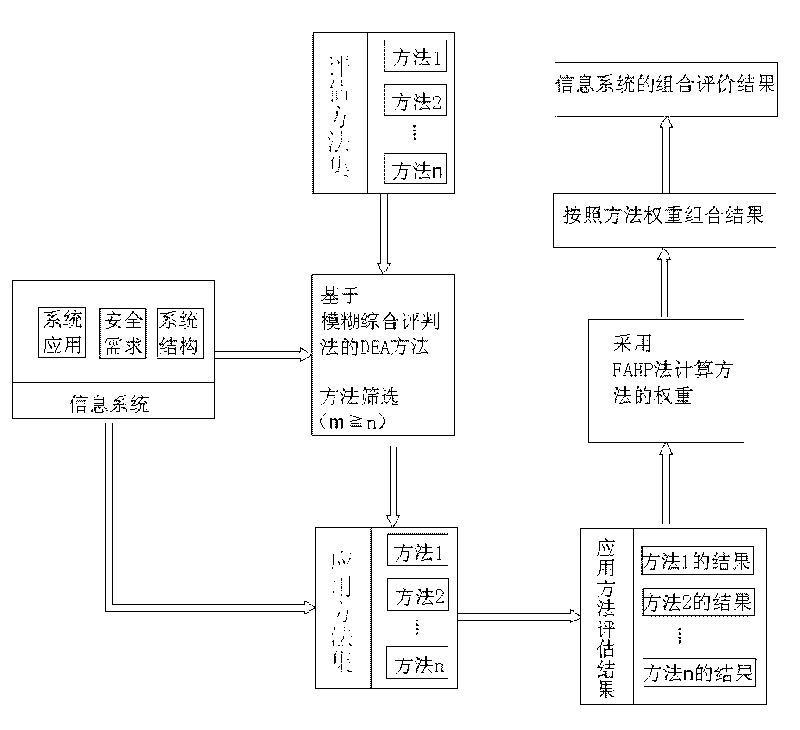
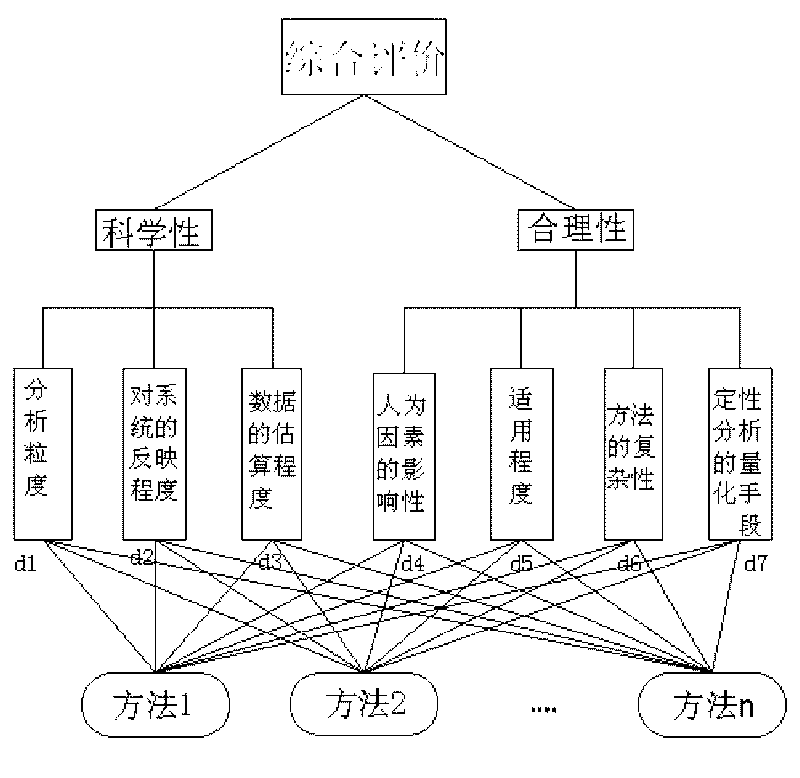
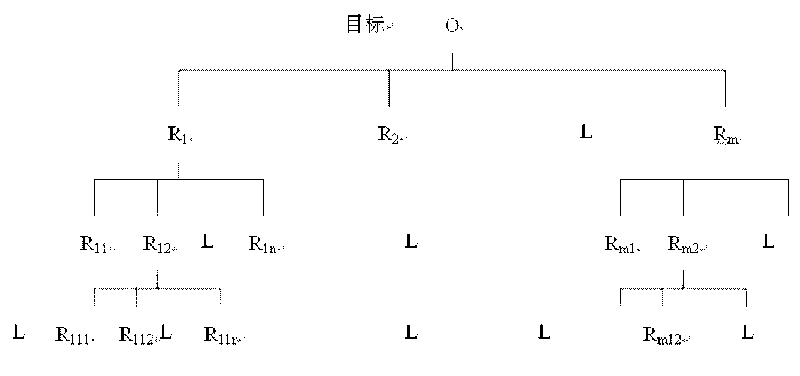
[0015] figure 1 It is the overall structure of a complete information system security risk model based on the combined assessment method. The process of combined evaluation is as follows: For m methods in the method library, according to the principle of fuzzy comprehensive evaluation method, expert evaluation is carried out from the two aspects of scientificity and rationality of the method, and then the calculation of each method is obtained by fuzzy analytic hierarchy process. Evaluation value, the first-level index of the evaluation method is used as the output index of the data envelopment analysis (DEA), and the result of the second-level evaluation of the fuzzy combination evaluation is used as the index value, and the relative effectiveness of different evaluation methods is evaluated by using the DEA method. Then select one or several evaluation meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com