Identification distribution and separate-storage method, identification replacing transmission method and system
A technology of separate storage and identification distribution, which is applied in the field of network security, can solve problems such as increased terminal switching delay, redundant identification functions, and affecting seamless roaming effects, and achieves the effect of improving security protection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
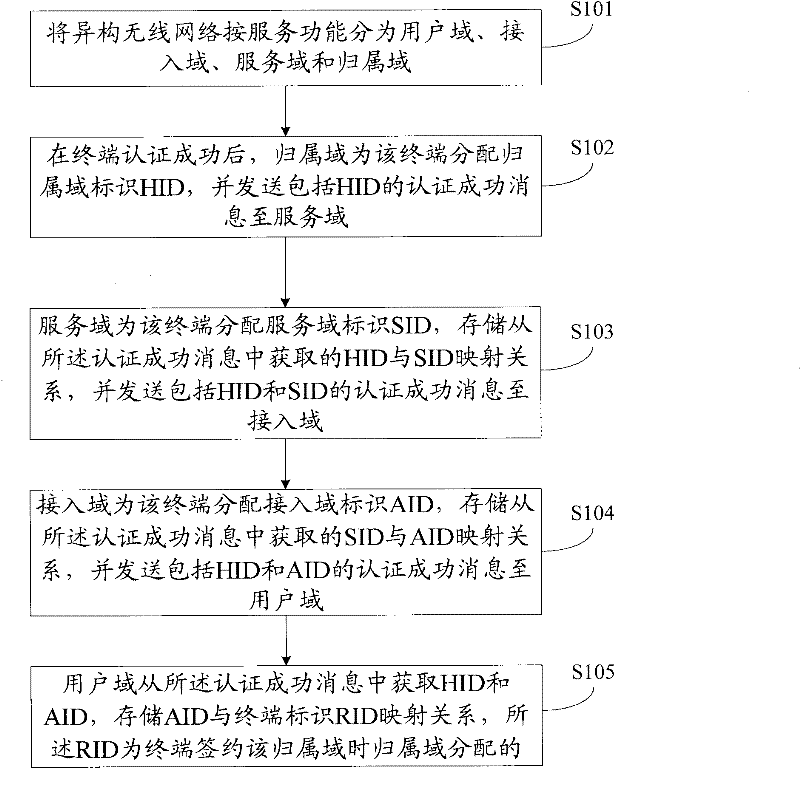
[0089] see figure 1 , the embodiment of the present invention provides a method for identification allocation and separate storage.
[0090] S101: Divide the heterogeneous wireless network into a user domain, an access domain, a service domain, and a home domain according to service functions, wherein the service domain includes at least one access domain, and the access domain includes at least one user domain, and when serving locally , the home domain and the service domain are the same network.
[0091] in:
[0092] User domain: mainly intelligent terminals (including identity mapping service modules), which can access different access networks, such as 3G, WLAN, WiMAX, etc. The terminal identifier RID of the terminal in this domain is its real identity.
[0093] Access domain: mainly base stations, wireless access points, access servers, identity mapping servers and other entities that access the network. This domain assigns an access domain identifier (AID) to each t...
Embodiment 2
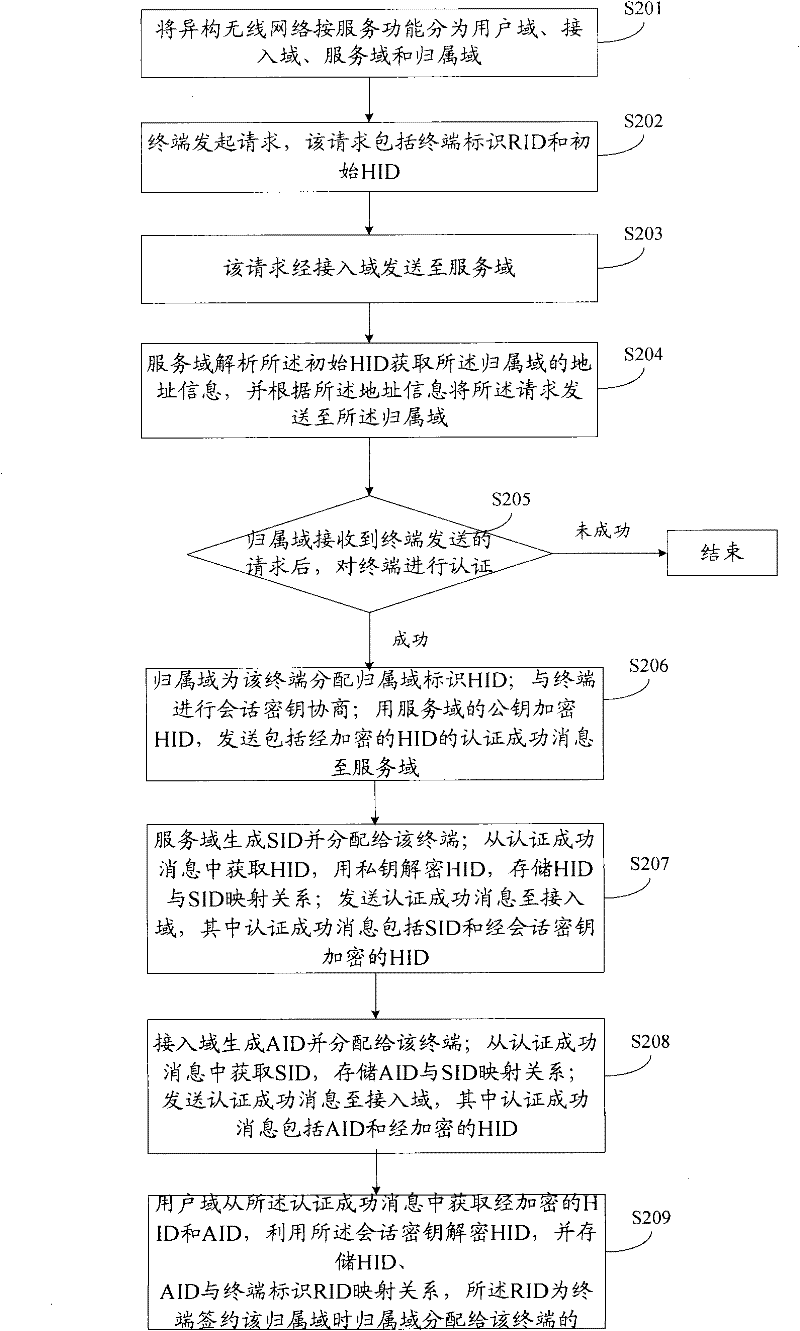
[0103] see figure 2 , the embodiment of the present invention provides a method for identification allocation and separate storage.
[0104] S201: Divide the heterogeneous wireless network into a user domain, an access domain, a service domain, and a home domain according to service functions, wherein the service domain includes at least one access domain, and the access domain includes at least one user domain, and when serving locally , the home domain and the service domain are the same network.
[0105] Usually, the heterogeneous wireless network is pre-divided, and there is no need to re-divide the heterogeneous wireless network every time identity allocation is performed.
[0106] S202: The terminal initiates an authentication request, where the authentication request includes the terminal real identity identifier RID and initial HID.
[0107] The initial HID is assigned to the terminal by the home domain when the terminal subscribes to the home domain.
[0108] Prefer...
Embodiment 3
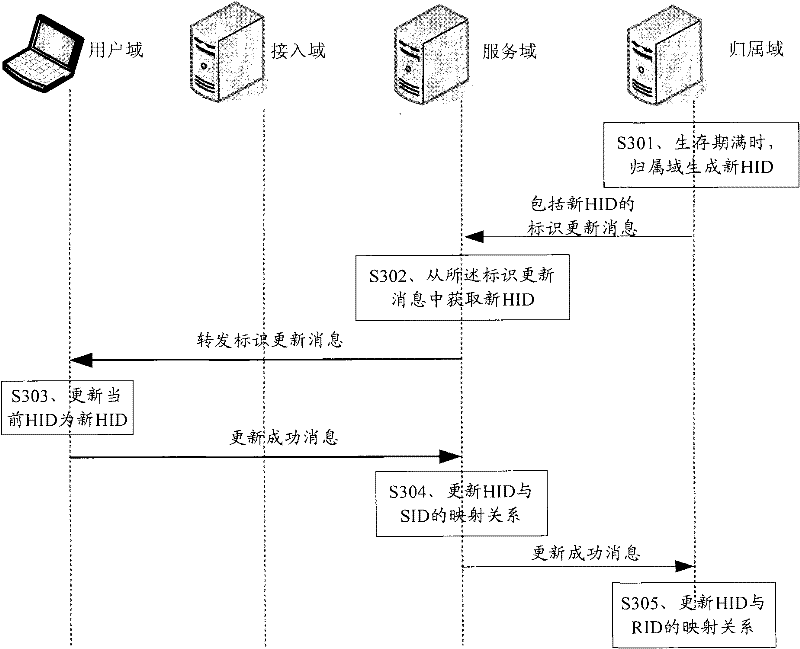
[0156] see Figure 8 , the embodiment of the present invention also provides a method for implementing identifier replacement transmission based on the above identifier allocation and separate storage method, including:
[0157] S801: When a data packet needs to be sent, send a data packet including a known domain identifier of the destination domain to the destination domain;
[0158] S802: When the data packet is received, analyze the domain identifier in the data packet to verify its authenticity; if the data packet needs to be forwarded, after the verification is successful, use the pre-stored domain identifier mapping relationship to obtain the known target domain Domain ID, replace the current domain ID in the data packet with the known domain ID of the target domain, and forward it.
[0159] In practical applications, the data packet may be sent from the terminal to the home domain, or between any two domains, which is not limited in the embodiment of the present inven...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com