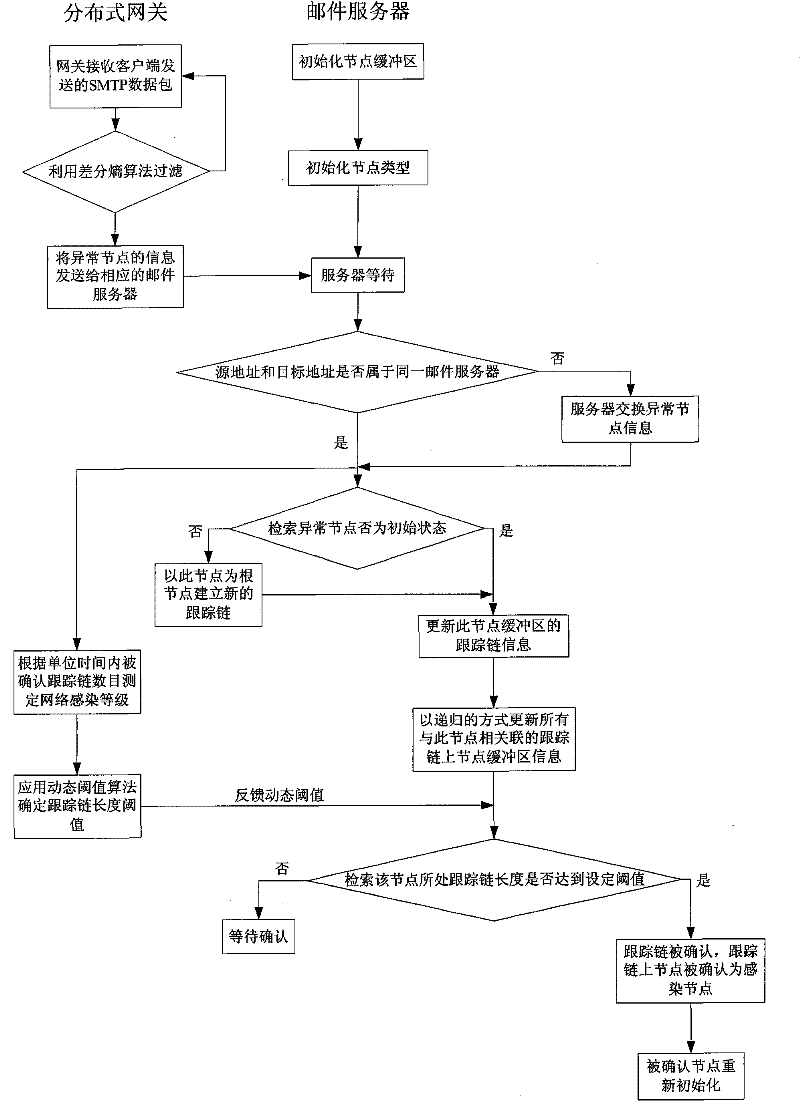
Method for detecting Email worm
A detection method and technology for worms, which are applied in the fields of instruments, computing, and electrical and digital data processing, can solve problems such as difficulty in finding, and the effect is not obvious, and achieve the effects of improving efficiency, reducing load, and improving compatibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
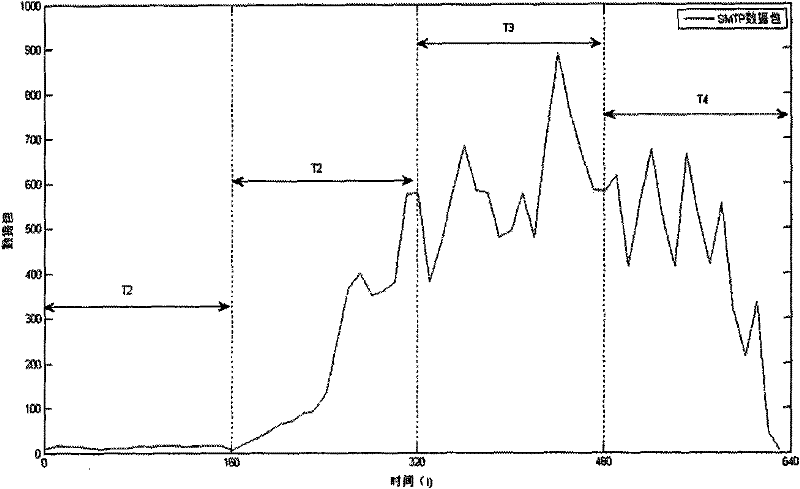
[0097] 1. Single point detection:
[0098] Using single-point detection method to detect the infection characteristics of a network node. In this embodiment, the entire detection cycle is divided into four time periods: T1, T2, T3, and T4. The duration of each time period is set to 160 seconds. For the infection characteristic curves of the detected nodes in each time period, see image 3 ;Take the thresholds M=100, 200 and 300 respectively, and use the differential entropy to calculate the data of the 4 time periods. For the calculation results, see Figure 4 .
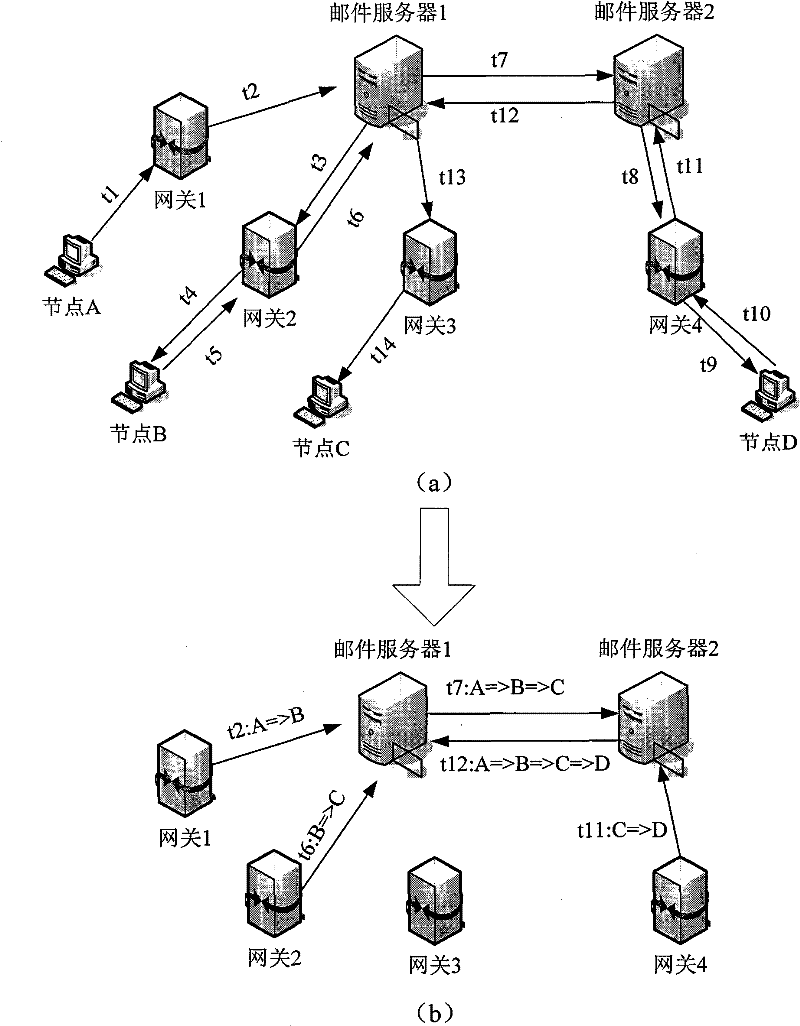
[0099] 2. Multi-point tracking detection:
[0100] For the tracking chain establishment process, see Figure 5 : Set M=2, t1i represents the level of node i. There are two tracking chains in the graph, nodes 1, 2, and 3 form chain 1, and nodes 5 and 4 form chain 2. At time t1, node 1 and node 5 have infection characteristics, and are connected to node 2 and node 4 respectively, and node 1 and node 5 are respecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com