Method for protecting data of memorizer
A data protection and storage technology, applied in the field of storage data protection, can solve problems such as incomplete storage data protection, and achieve the effect of protection security and wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
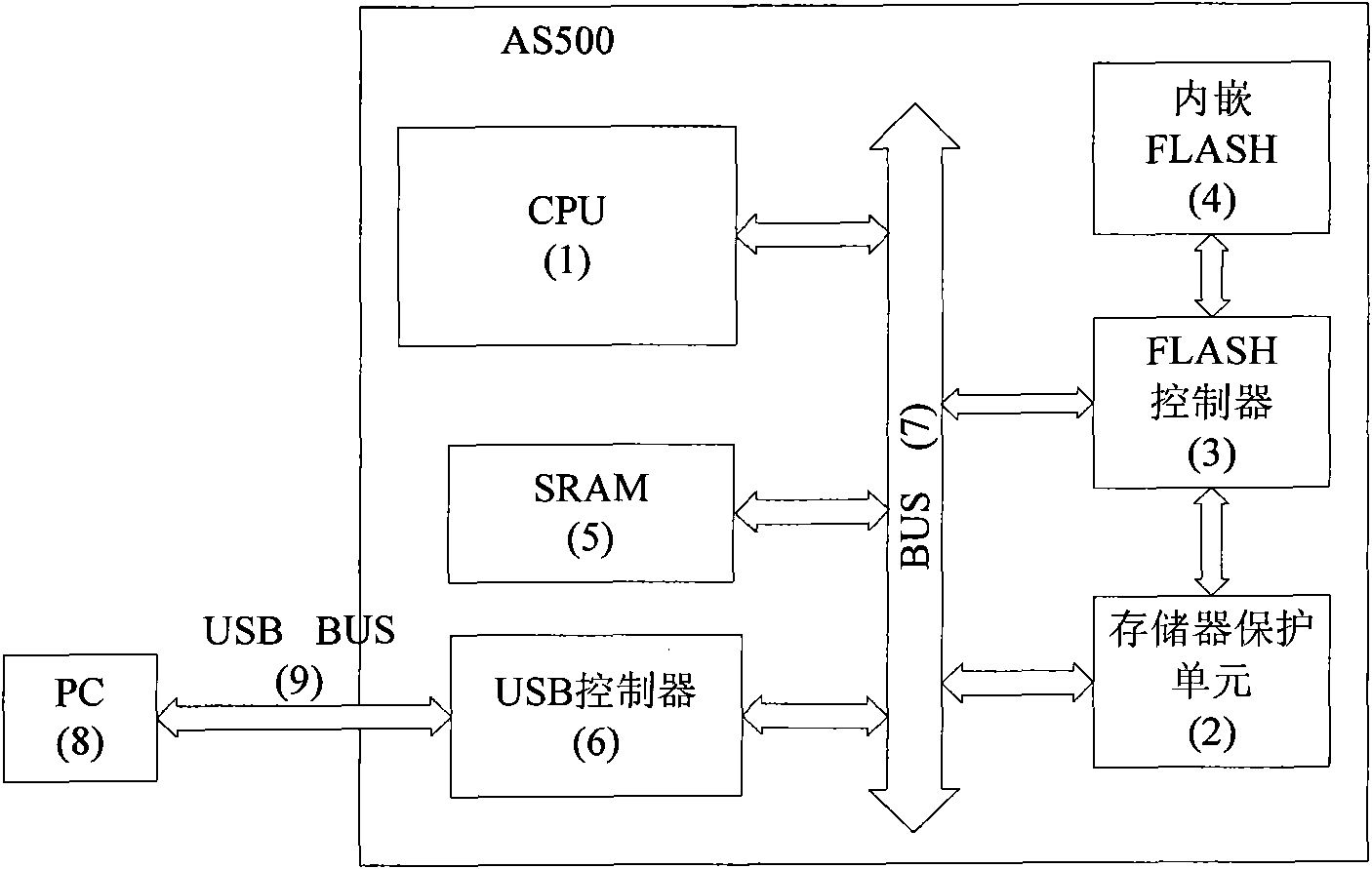
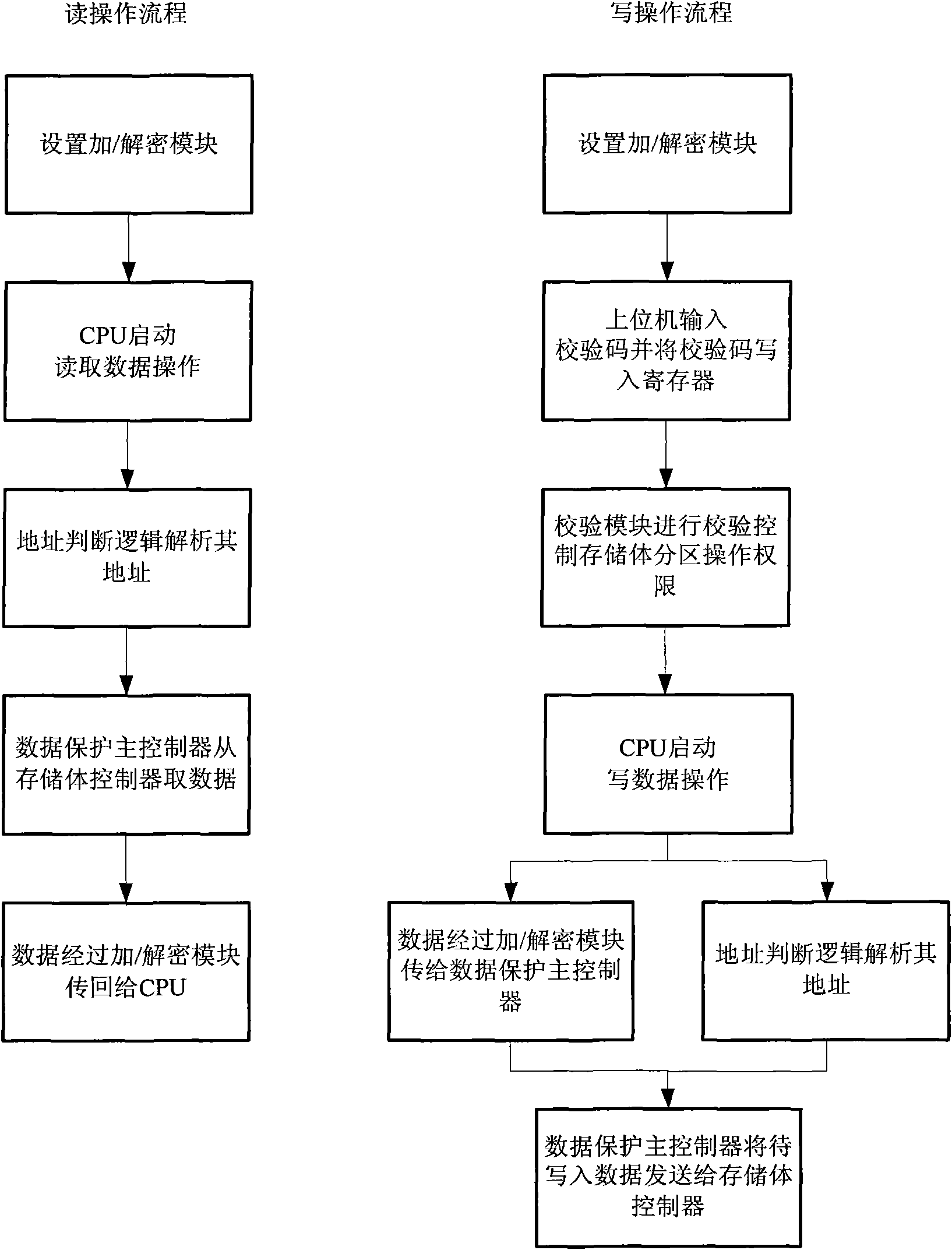
[0030] This embodiment takes the AS500 security chip as an example to illustrate the implementation and application of this patented technology. AS500 is an encryption application SOC chip with built-in FLASH (that is, memory). The upper computer PC inputs the authority check code through the USB port to control the memory protection unit to achieve data protection for the embedded FLASH. The internal ROM program of AS500 is responsible for the software part of the entire data protection mechanism. Through the USB port, the ROM program will transfer the user's authority check code in the PC to the register of the storage protection unit, and open the corresponding area operation authority through the check.
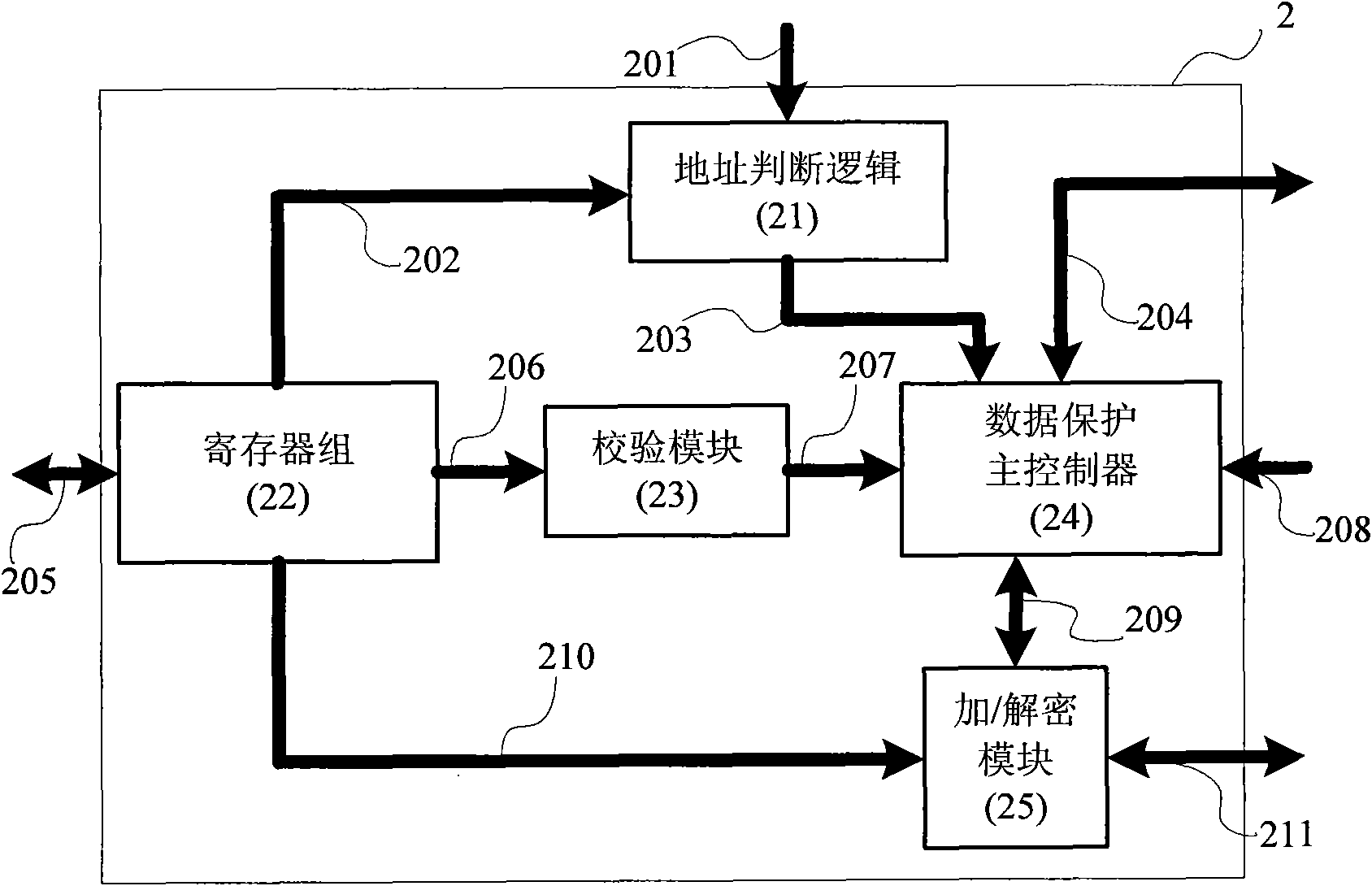
[0031] like figure 1 As shown, in the chip AS500, CPU1 communicates with the memory protection unit 2, FLASH controller 3, embedded FALSH4, SRAM5, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com