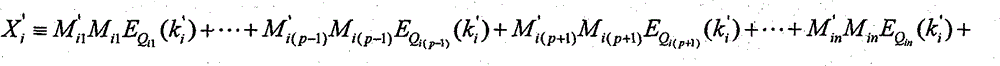Group key managing method based on Chinese remainder theorem
A Chinese remainder theorem and group key technology, applied in the field of communication network security, can solve the problems of low security, insufficient security of secret channels, and high delay in key update, so as to improve security and shorten update time. Delay time, effect of security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
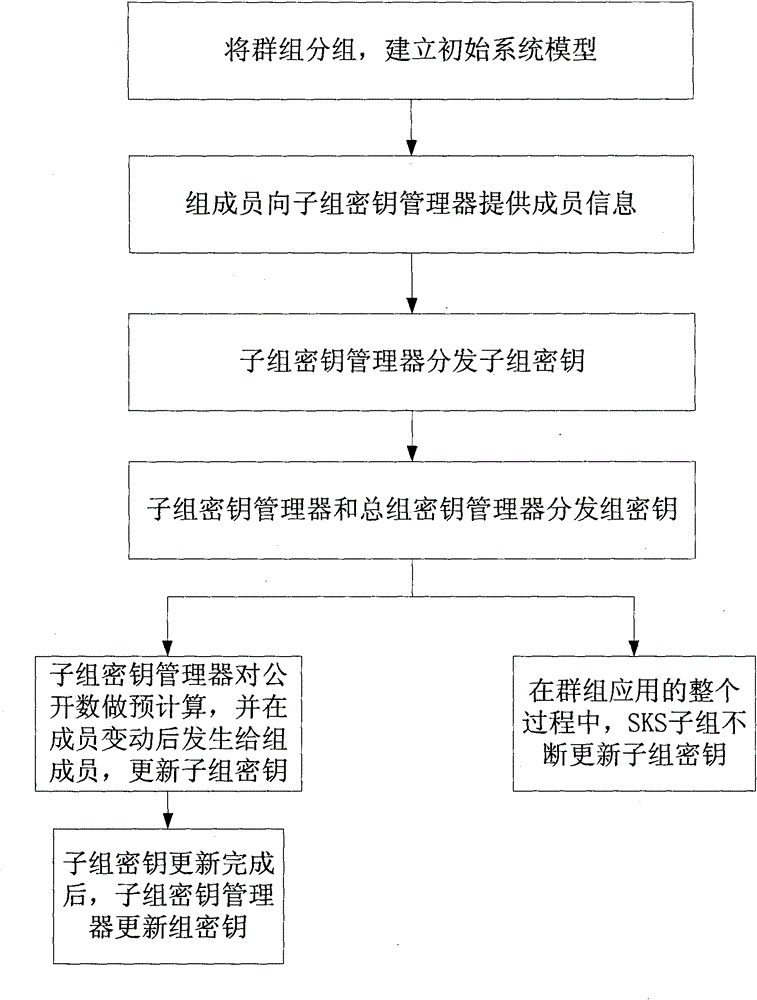
[0028] One, the symbol and mathematical theory explanation that the present invention applies
[0029] 1. Explanation of relevant symbols
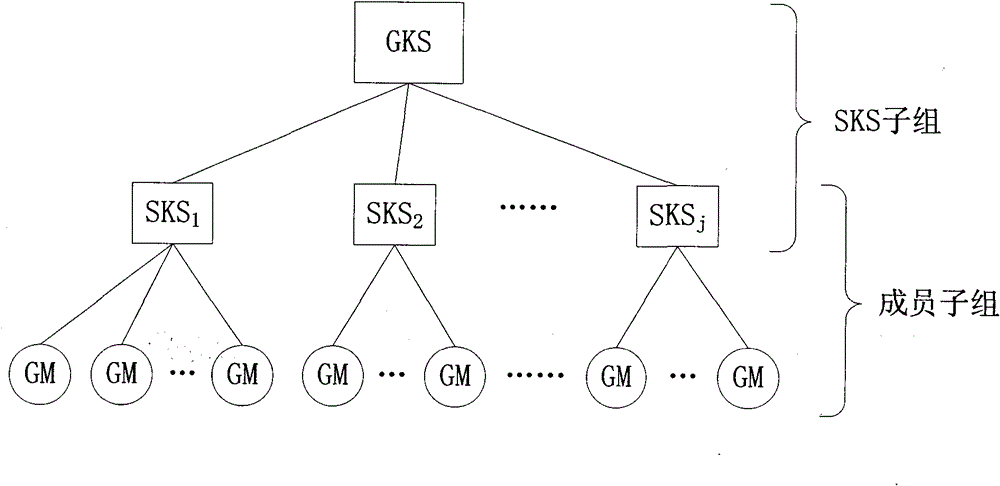
[0030] General group key manager GKS: responsible for the generation, distribution and update of subgroup keys of SKS subgroups, and the generation, distribution and update of group keys of the entire group;
[0031] Subgroup key manager SKS for group i i : responsible for the generation, distribution and update of subgroup keys of group i, as well as the distribution and update of group keys;
[0032] GM: group member;
[0033] K: group key shared by group members;
[0034] k i : The subgroup key of the i-th group, only the members of the i-th group hold it;
[0035] N: the number of group members;
[0036] n: the number of subgroup members;
[0037] m xy : the number of secrets held by the yth member of the xth group;
[0038] {P}:m xy The generative library of , that is, a library containing an infinite number of non-repeating...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com