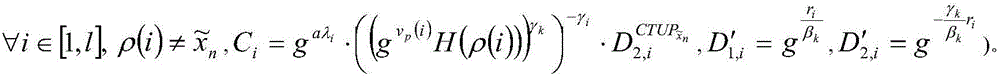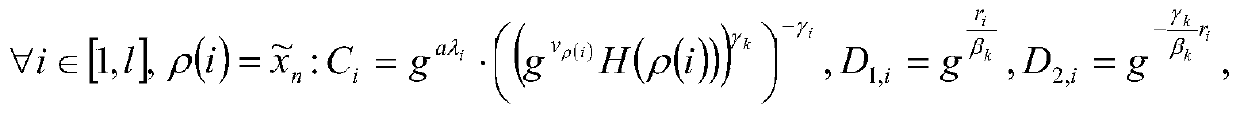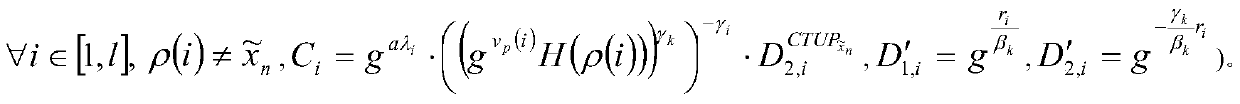Patents
Literature
33results about How to "Reduce update overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
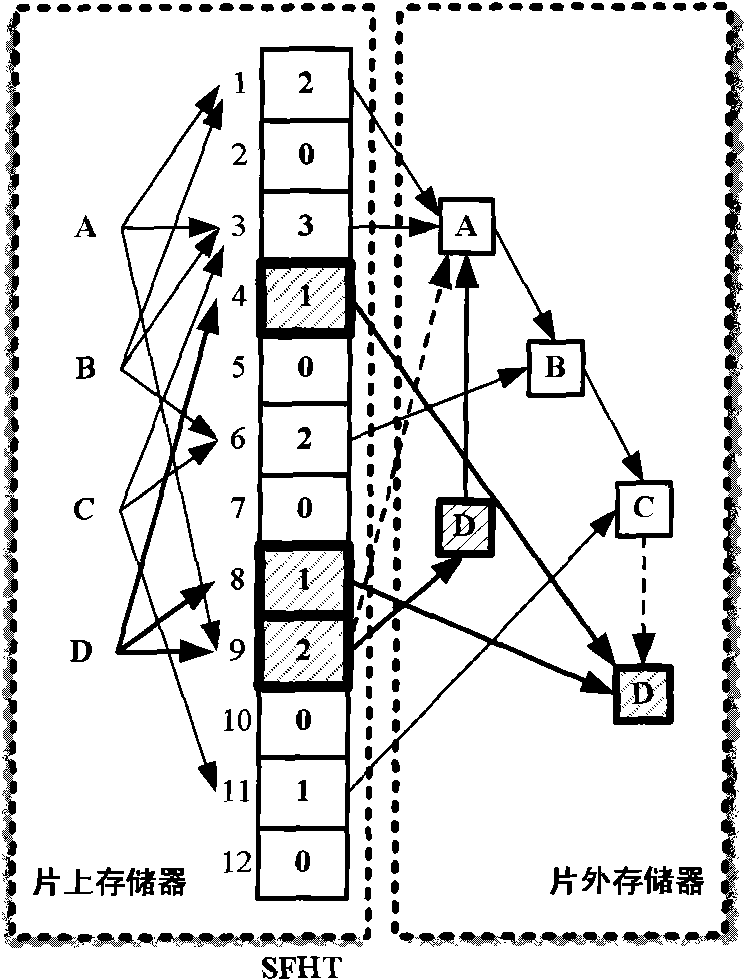
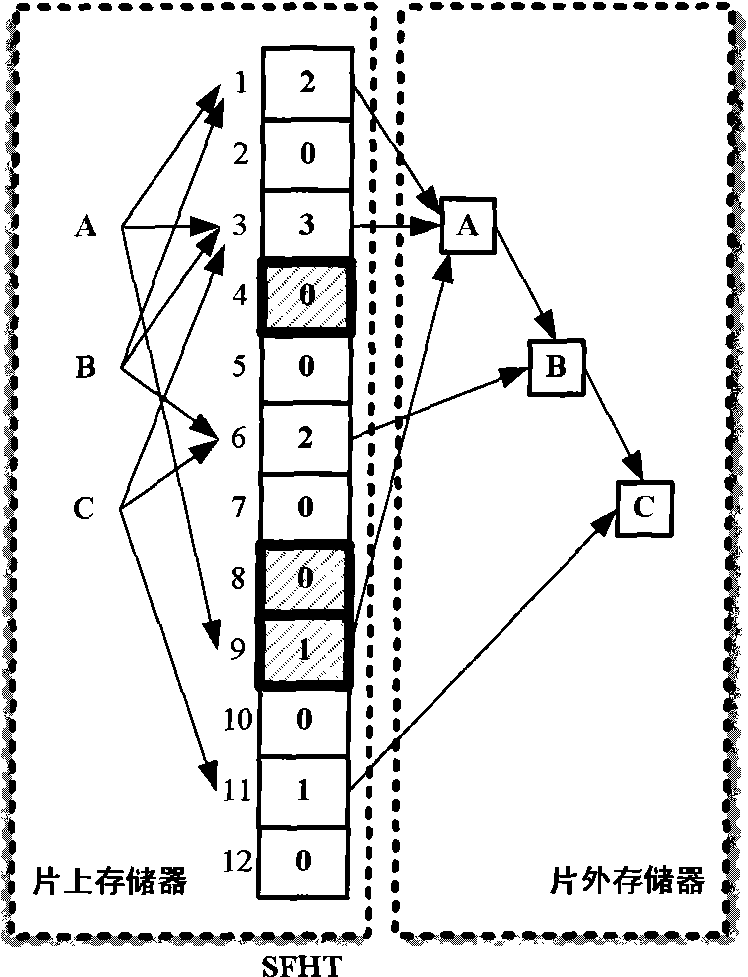
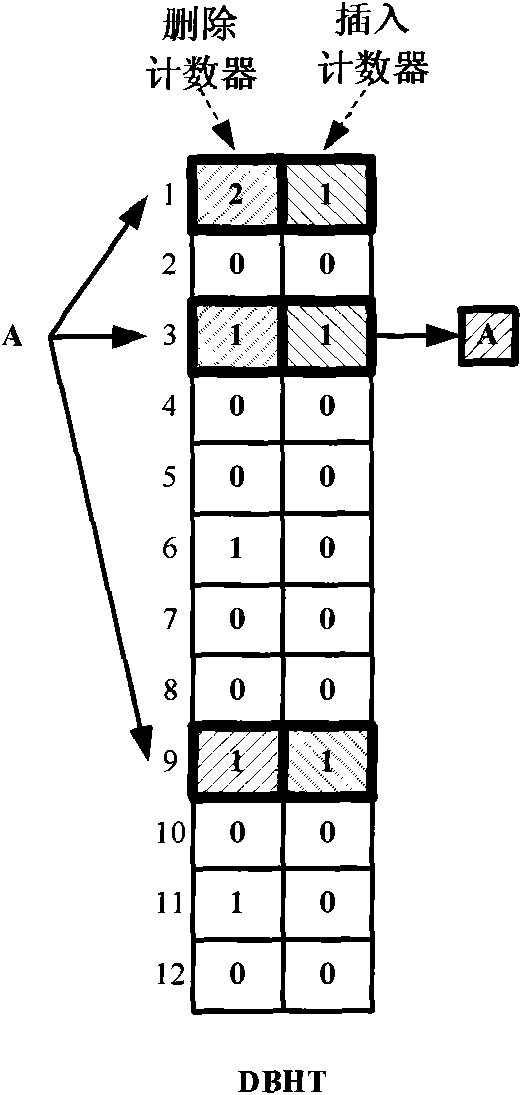
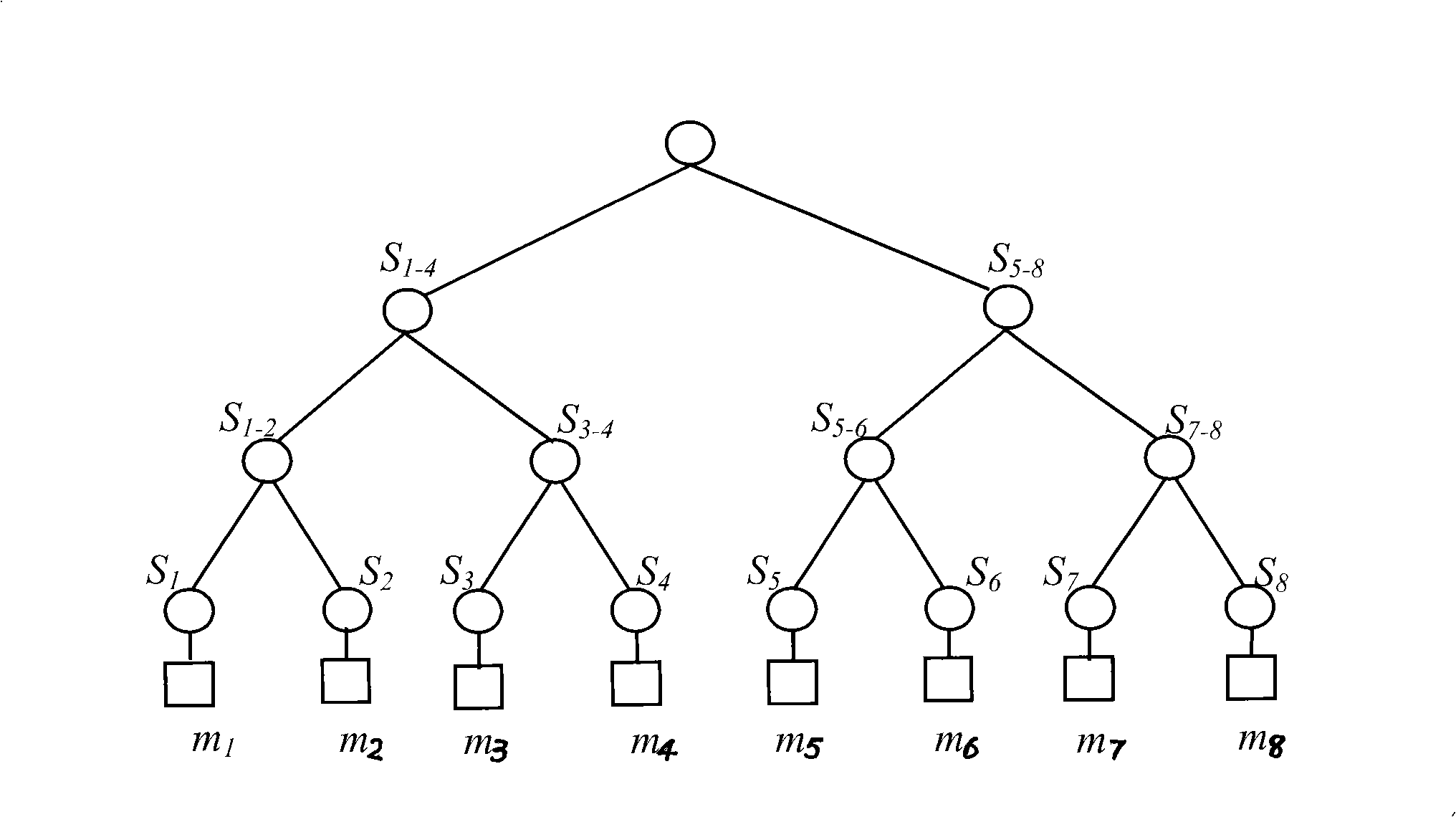
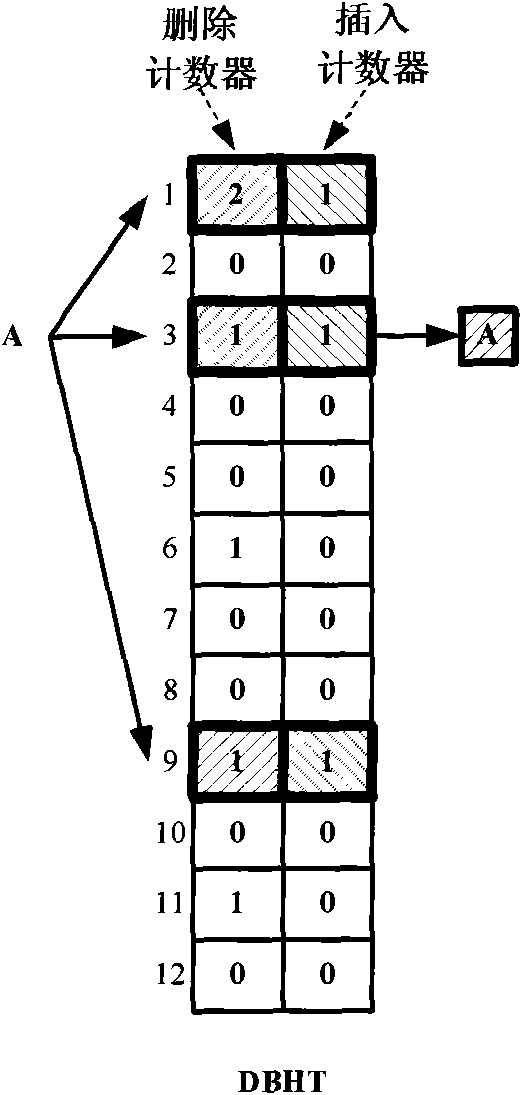
Hashing method based on double-counting bloom filter and hashing device
ActiveCN101655861AReduce update overheadReduce demandMemory adressing/allocation/relocationSpecial data processing applicationsBloom filterSelection principle
The invention provides a hashing method for realizing hashing insert operation on a hash table; the hash table comprises a plurality of buckets, the bucket comprises an insert counter and a delete counter, the insert counter is used for recording the number of insert elements in the bucket, and the delete counter is used for recording the number of the delete elements in the bucket; the method comprises the following steps: the element to be operated is mapped to at least one bucket of the hash table according to hash function, and the bucket is called as a candidate bucket; a target bucket isfound from the candidate buckets according to selection principle of the target bucket; the elements to be inserted are inserted in the target bucket; weather the inserted elements have effect on thestorage position of the stored elements in the candidate bucket is judged, if the storage positions of the stored elements can not meet the selection principle of the target bucket, the storage positions of the stored elements are re-adjusted; the hashing method also comprises the step of accumulating the value of the insert counter of the bucket.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
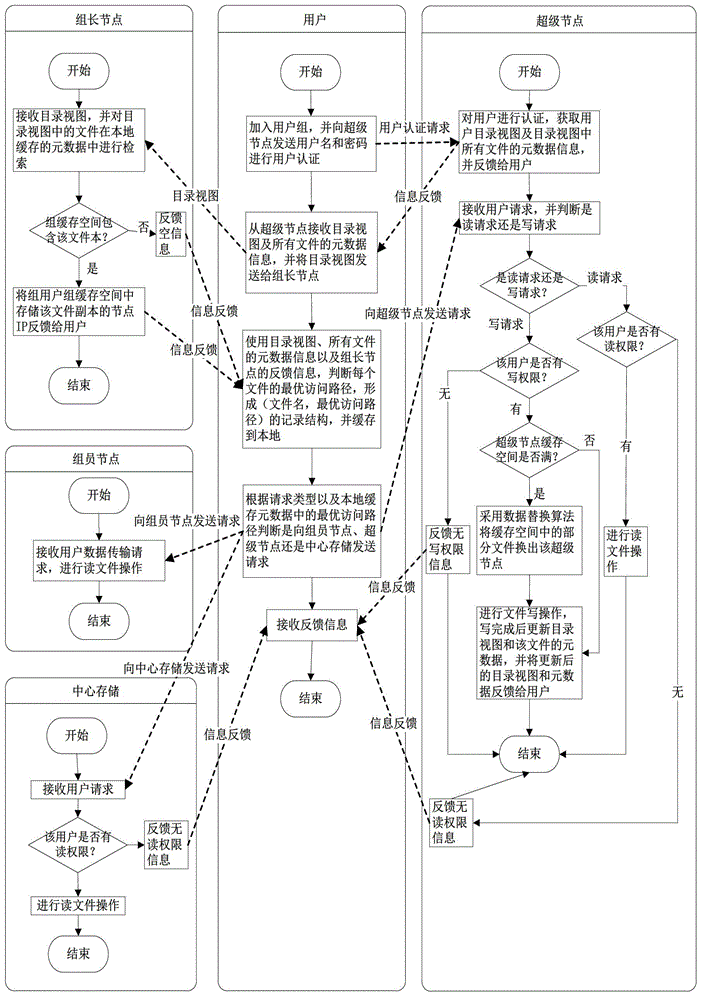
Hybrid cloud storage system and method based on multi-level cache
ActiveCN103338242AReduce network latencyImprove access bandwidthTransmissionSpecial data processing applicationsUser authenticationIp address
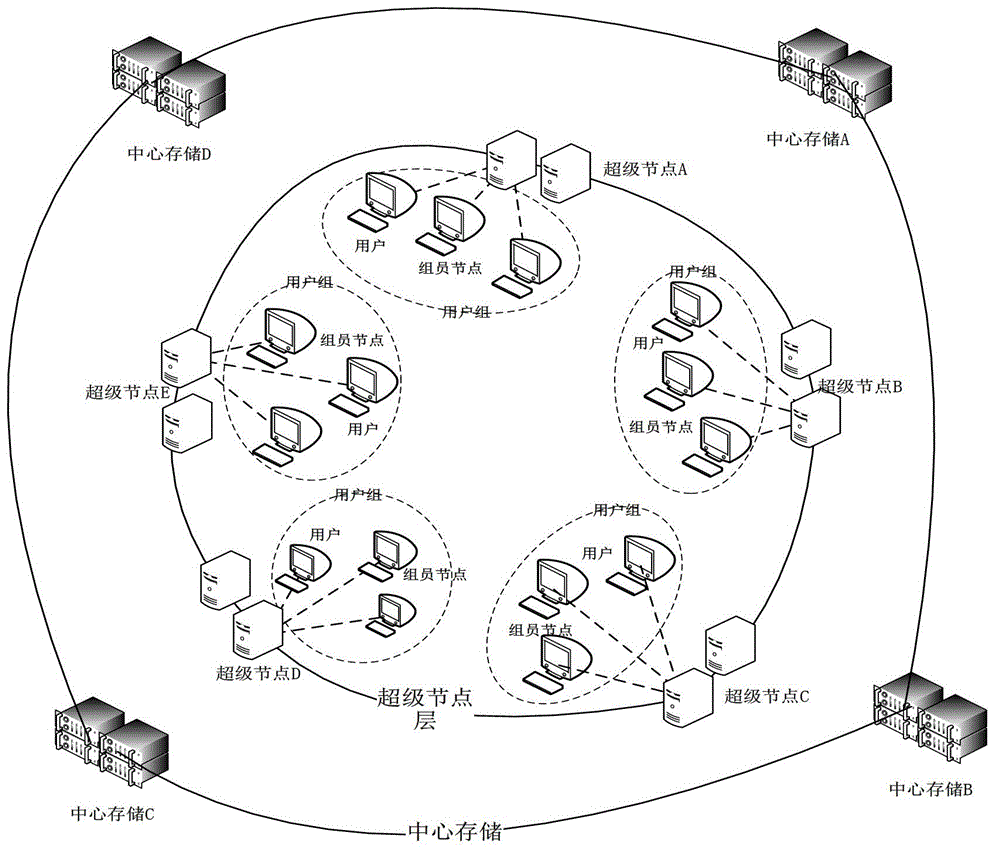
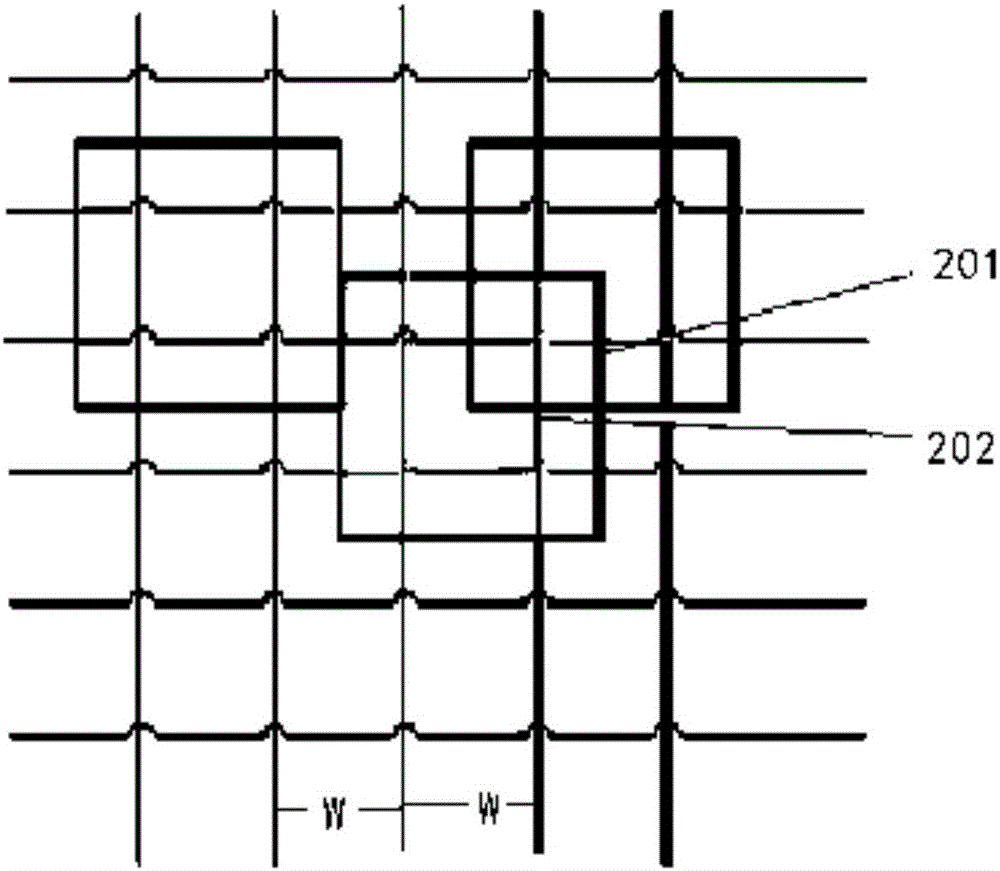
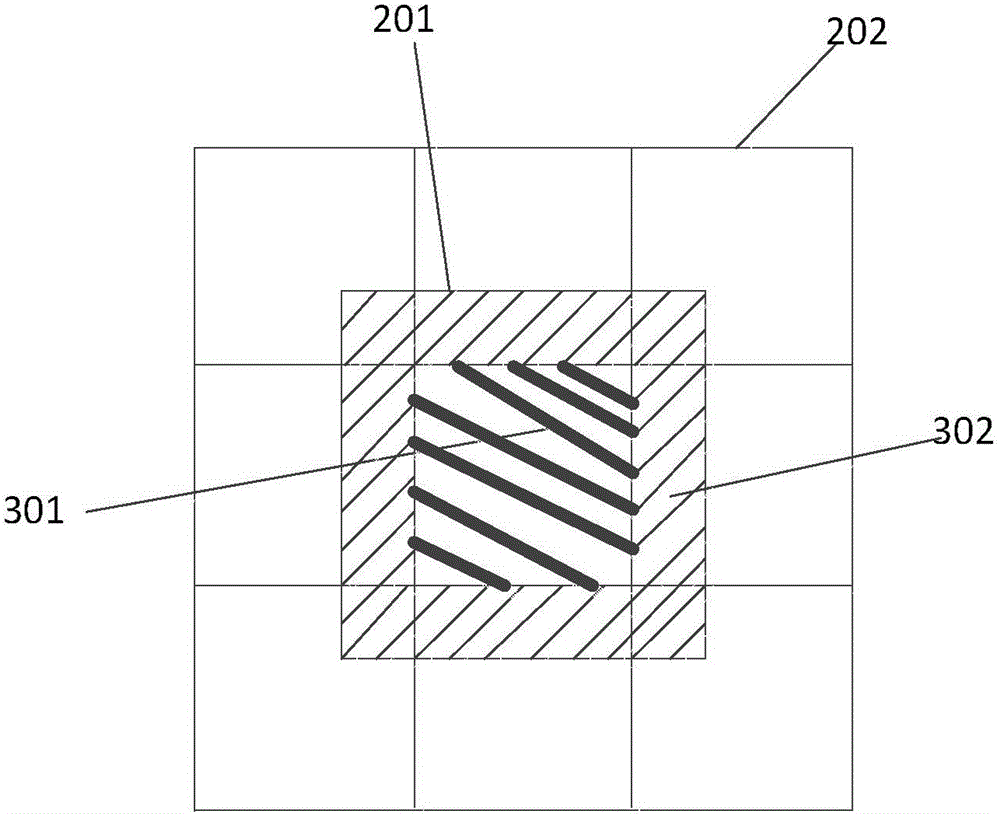
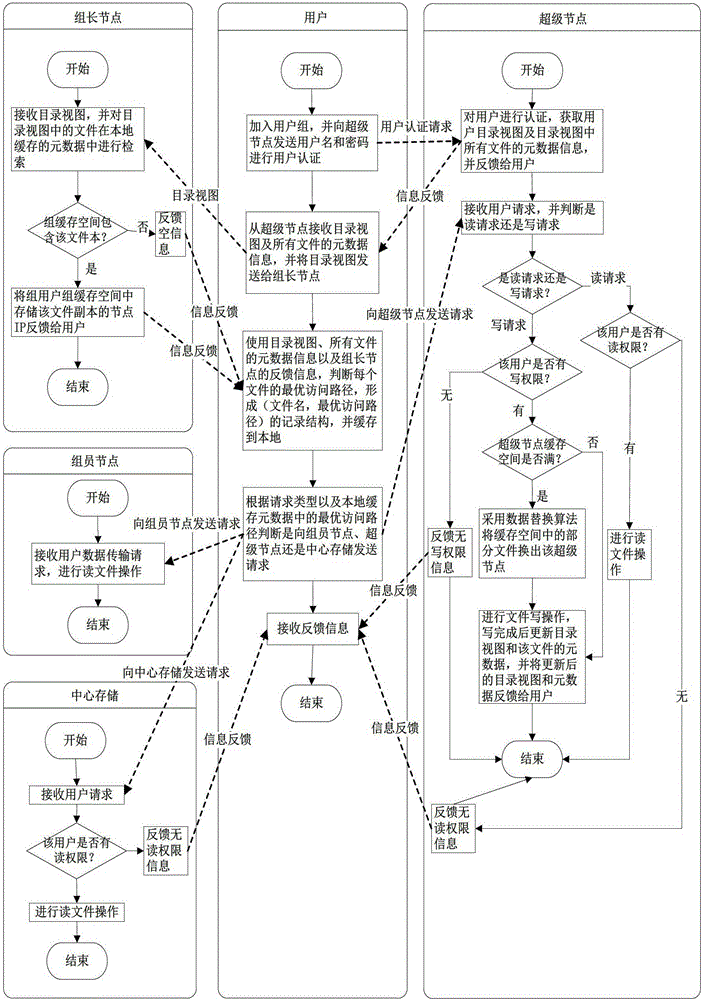
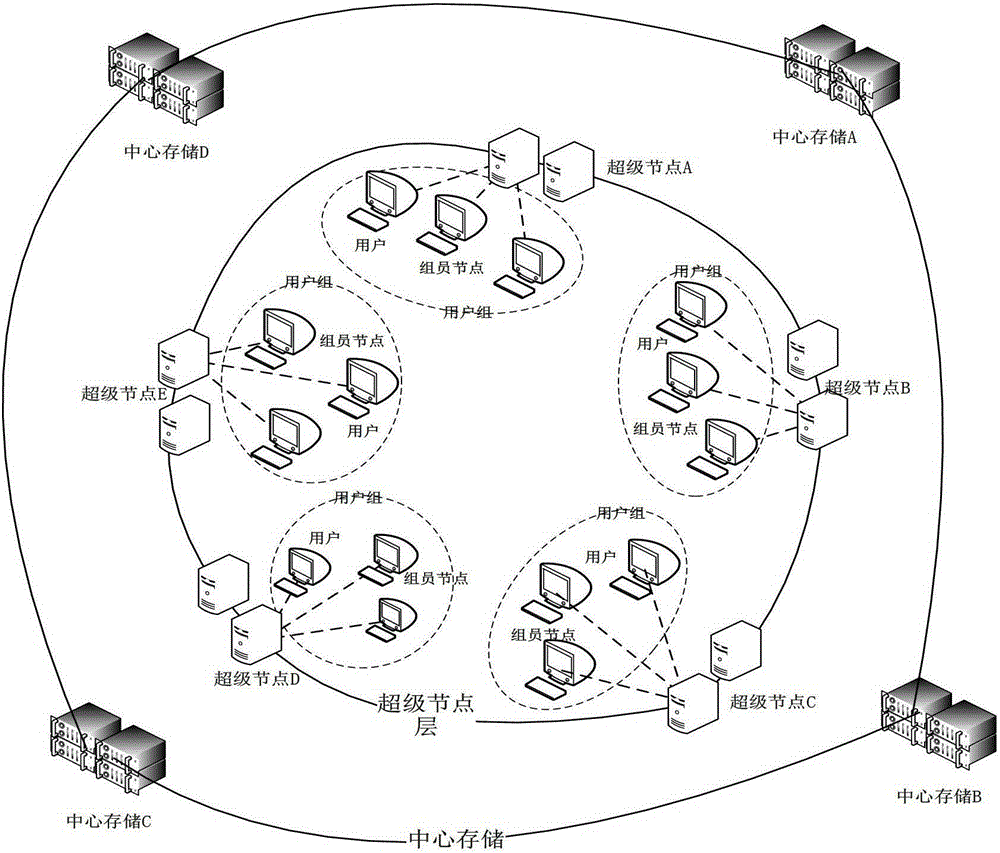
The invention discloses a hybrid cloud storage method based on multi-level cache. The method comprises the following steps: a user joins a user group for login according to the local area network where the user is, and sends a user name and a password for user authentication to a super node of the region where the user group is, the super node achieves authentication of the user according to the received user name and password, the user receives a catalog view returned from the super node and metadata information of all files and sends the catalog view to a group leader node of the user group, the group leader node judges whether the buffer memory space of the group contains files in the catalog view according to the received catalog view, and if yes, feeds the IP address of the node in which the files are saved in the buffer memory space of the group to the user, and the user determines the optimal access path of each file in the catalog view according to the received feedback information. The hybrid cloud storage method allows the user to access data from the user group cache and the super node layer cache which have lower network delay, thereby lowering the network delay of the user data access.
Owner:HUAZHONG UNIV OF SCI & TECH
Uni-directional function tree multicast key management method based on cipher sharing
InactiveCN101309137AReduce update overheadReduce computational overheadSpecial service provision for substationKey distribution for secure communicationSecret shareFunction tree
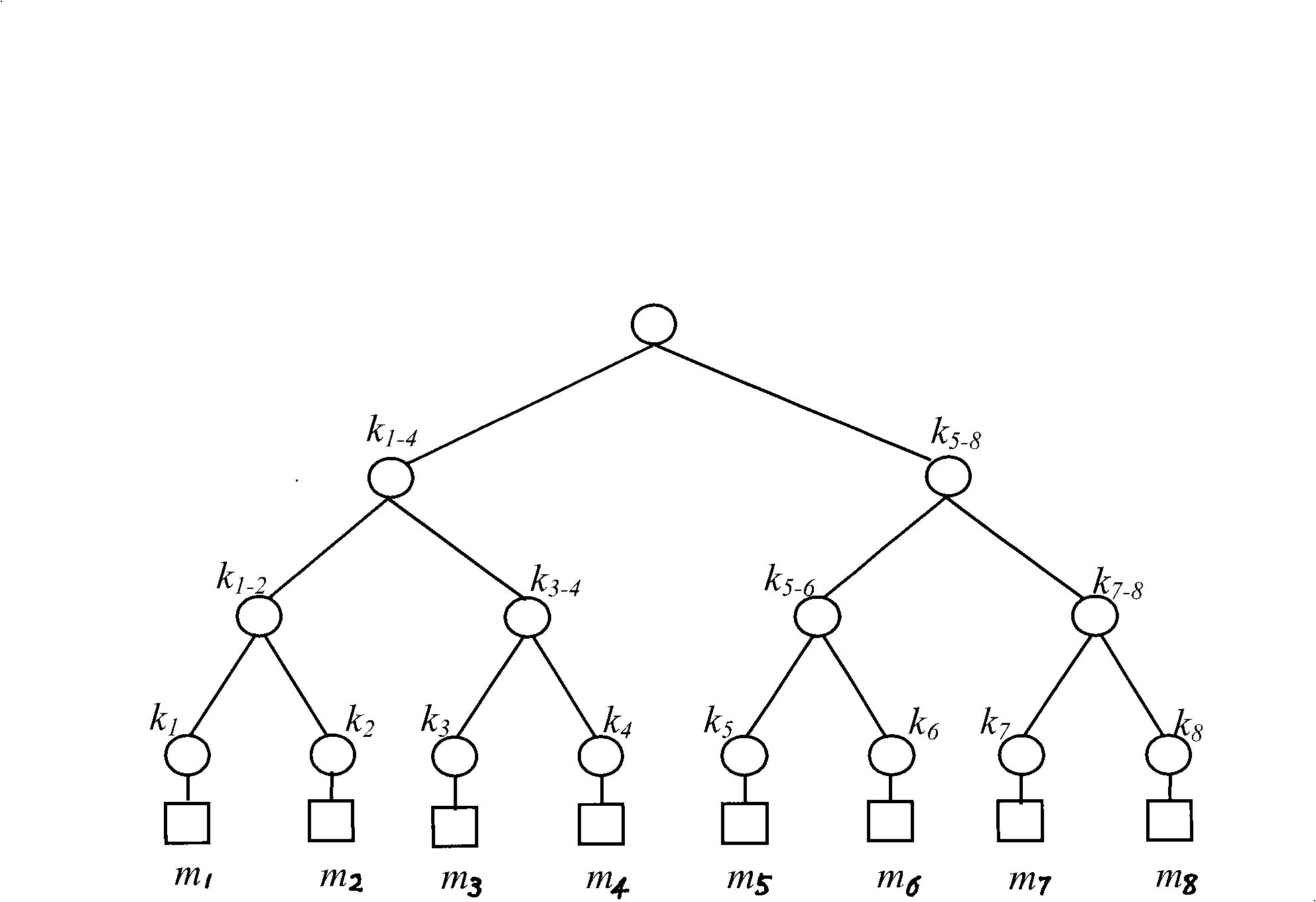
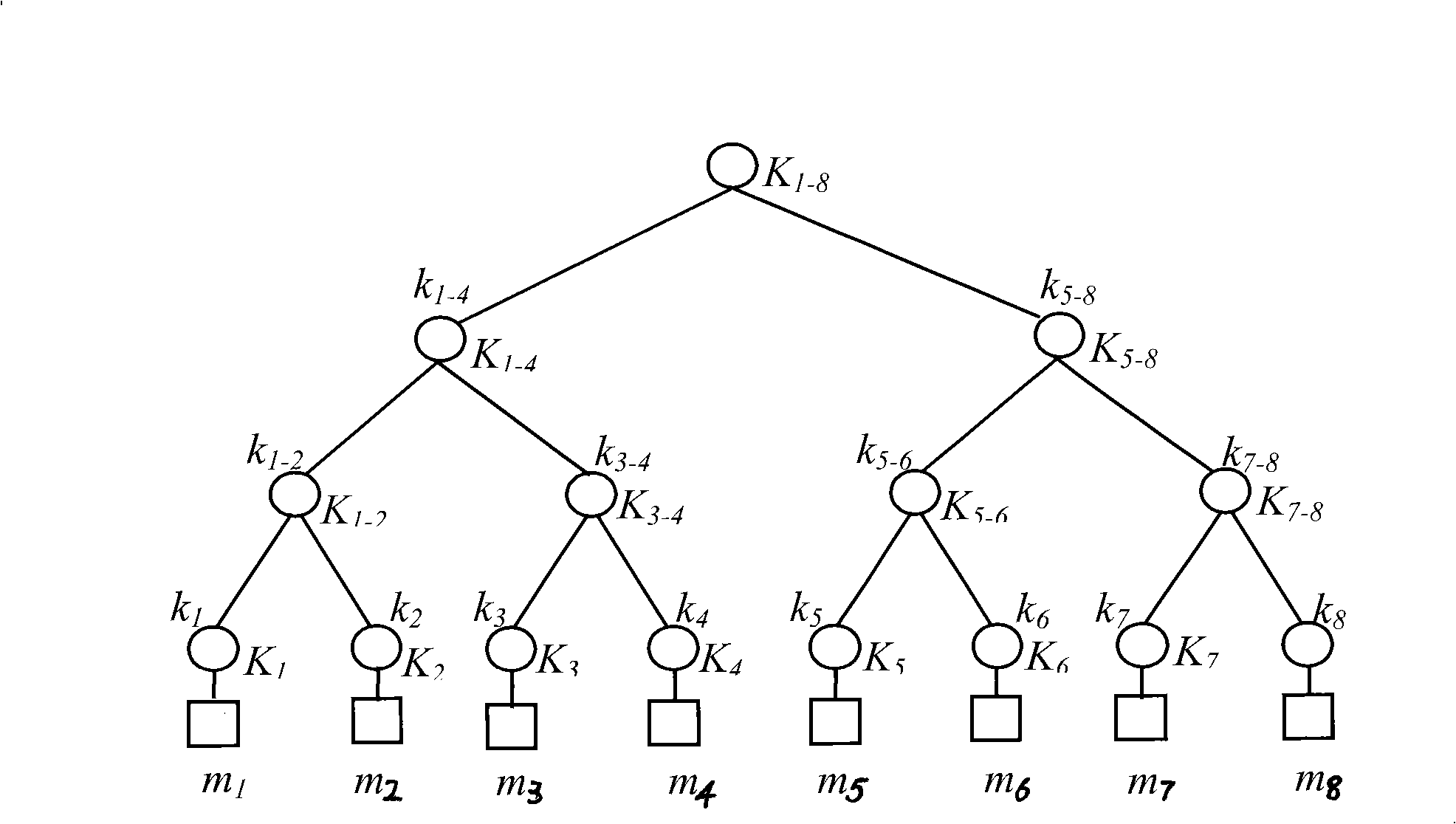
The invention relates to a one-way function tree multicast key management method base on secret sharing. The present multicast protocol lacks safety mechanism to suffice the safety requirement of the multicast application. During the key updating transmission, the invention uses the key to encrypt a blind key to realize the transmission; the process includes generating a key hierarchy tree and a blind key hierarchy tree, generating, distributing and recovering a group key, a group member joining in, a group member laving and a periodical key updating. The detail method of generating blind key hierarchy tree is that: each node of the blind key hierarchy tree uses the corresponding key K to obtain a blind key S through a function S=g(K); wherein, the function g is a one-way function. The one-way function tree multicast key management method of the invention can perform key updating by only transmitting the blind key S and sharing the secret share through the method of secret sharing, thereby avoids transmitting the true key to perform key updating, reduces the possibility of key being captured or cracked, and increases the anti-attack ability with higher safety.
Owner:ZHEJIANG UNIV
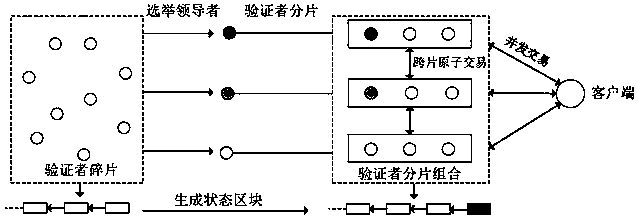
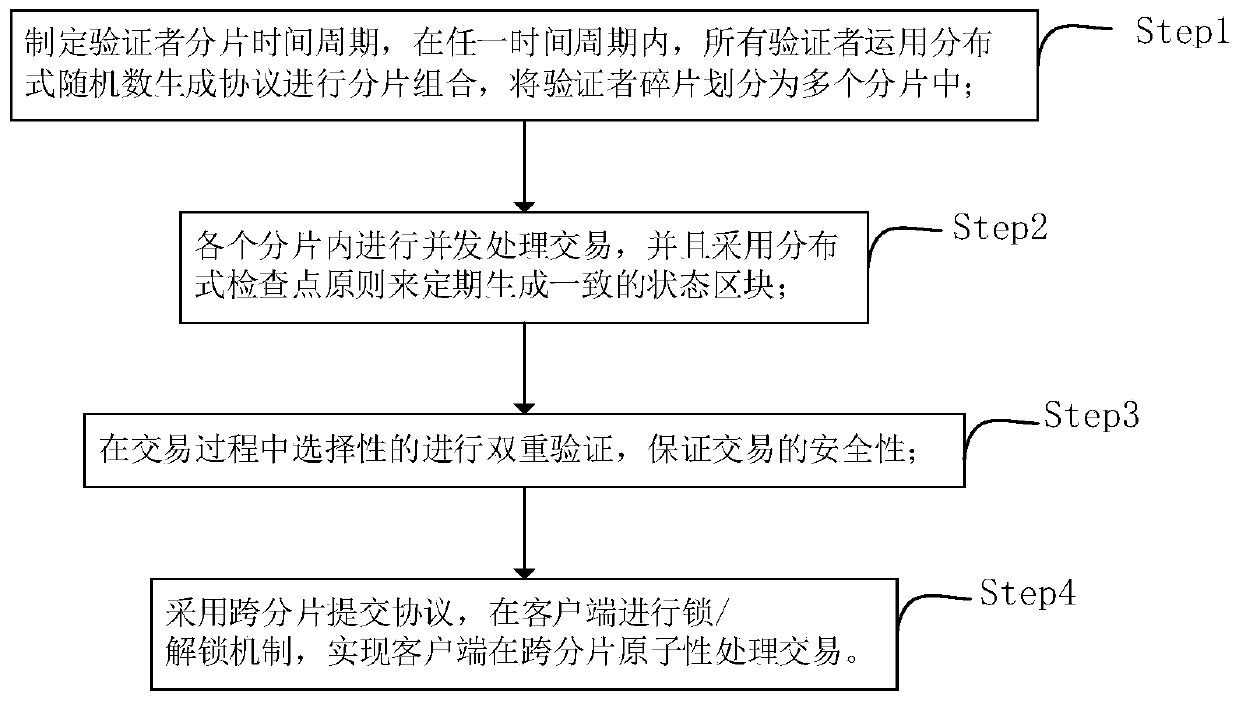
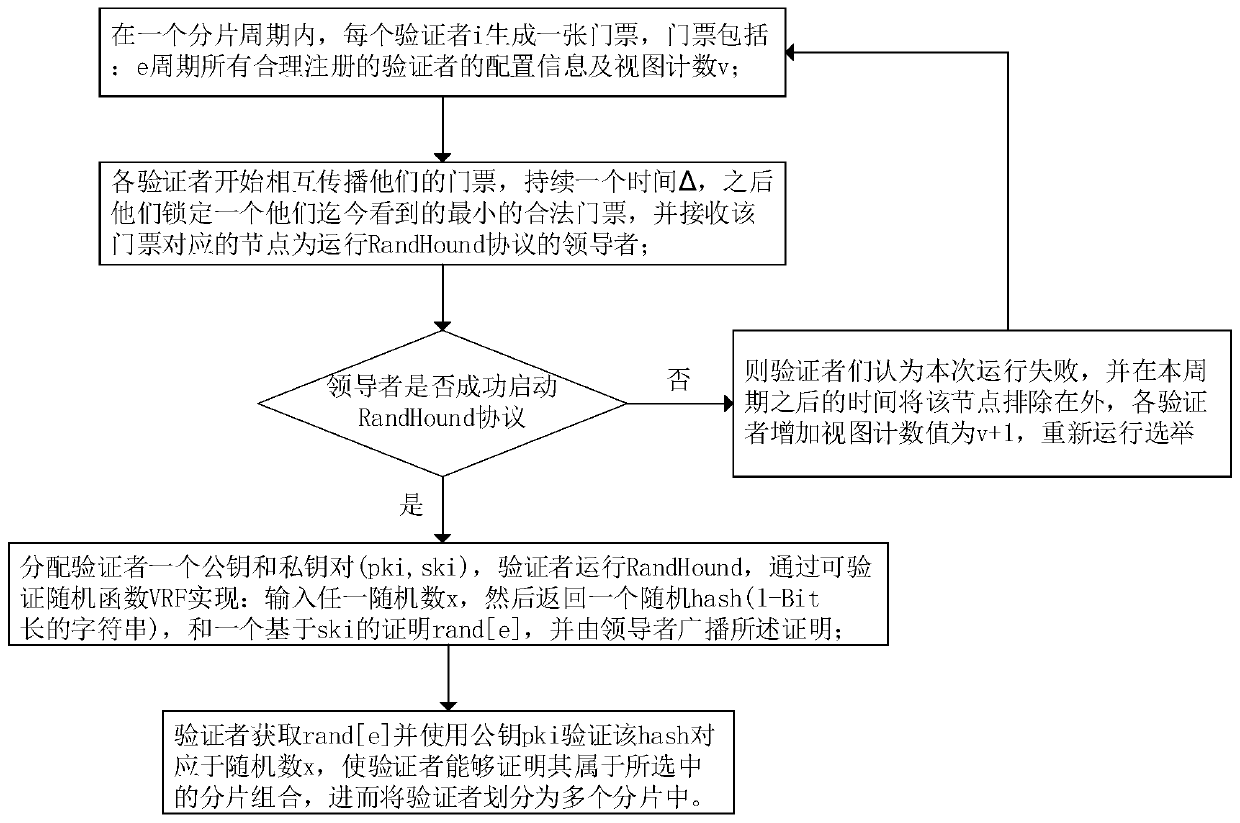
Method for realizing transverse expansion of distributed account book based on fragmentation mechanism
InactiveCN110310115AImplement the atomic commit transaction functionReduce storage spaceDatabase distribution/replicationPayment circuitsTheoretical computer scienceRandom number generation
The invention discloses a method for realizing transverse expansion of a distributed account book based on a fragmentation mechanism. The method comprises the following steps: (1) formulating a verifier fragmentation time period, within any time period, carrying out fragmentation combination on all verifiers by using a distributed random number generation protocol, and dividing the verifier fragmentation into a plurality of fragmentations; (2) carrying out concurrent processing transaction in each fragment, and regularly generating consistent state blocks; (3) selectively carrying out double verification in the transaction process to guarantee the security of the transaction; and (4) adopting a cross-fragment submission protocol, carrying out a locking / unlocking mechanism on the client, sothat the cross-fragment atomic processing transaction of the client is realized. Based on the above steps, in order to provide a horizontally extended method which does not damage long-term security,the method deploys a state block in each fragment to reduce storage space and update overhead, adopts a trusted but verified two-layer model to reduce small transaction delay, and adopts an atomic submission protocol among multiple fragments to realize a cross-fragment atomic submission transaction function.
Owner:HANGZHOU YUNXIANG NETWORK TECH
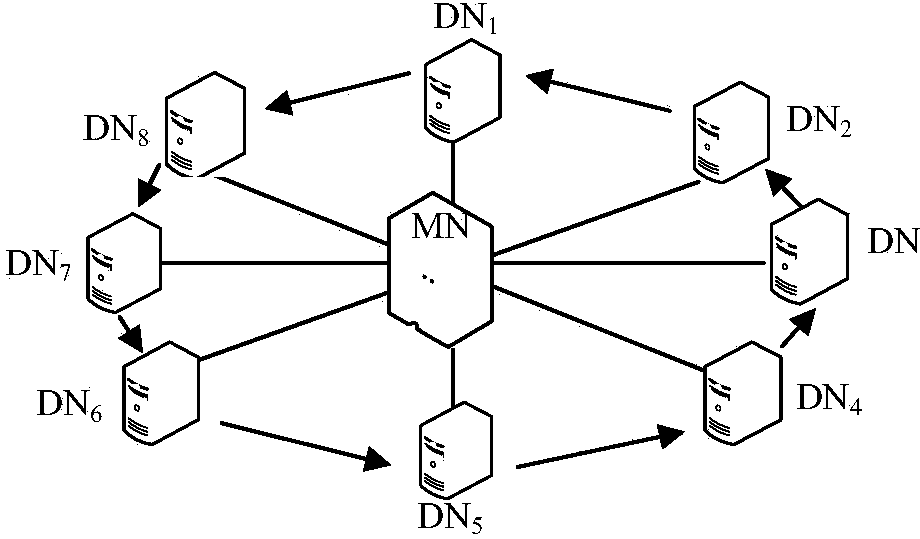
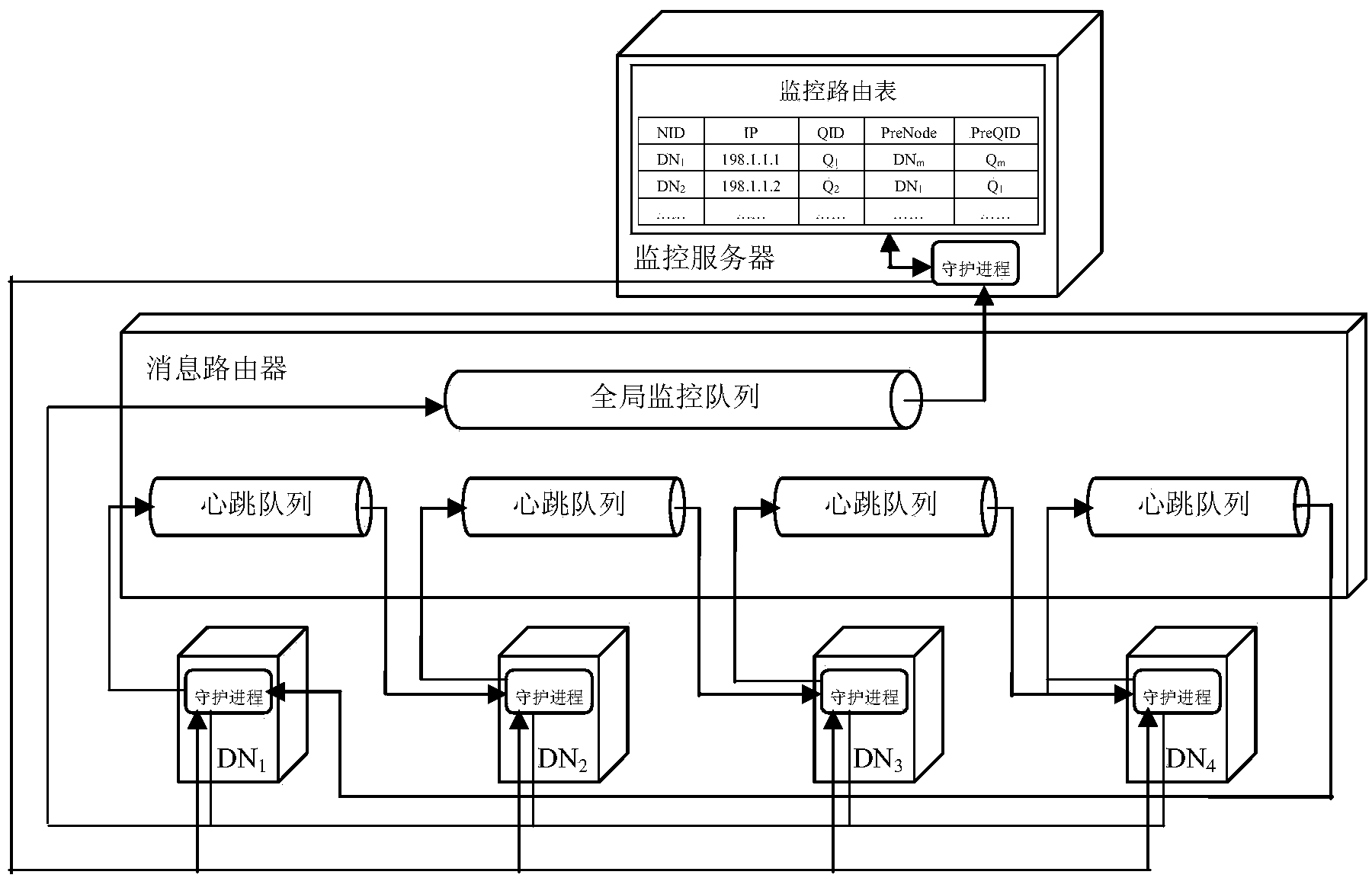
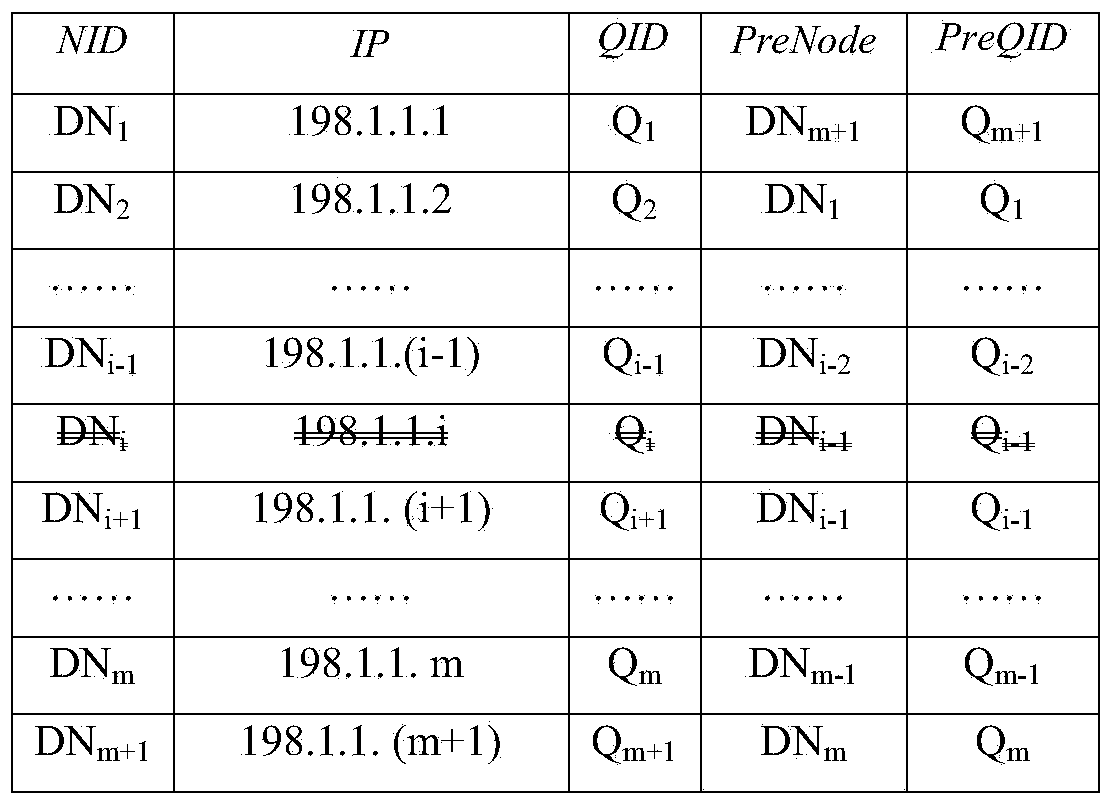
Large-scale-cloud-data-center-oriented server cooperative monitoring method
ActiveCN103944784AShort response timeLoad balancingData switching networksCloud data centerFailure risk
The invention discloses a large-scale-cloud-data-center-oriented server cooperative monitoring method. The mode that servers sense and monitor each other replaces a monitoring mode of a centralized structure, the self-managing capacity of the servers is improved, the monitoring burden of the monitoring servers is effectively lowered, and performance bottlenecks and singe point failure risks are removed. A cooperative monitoring mechanism and a functional component are provided, and the working steps of the cooperative monitoring mechanism are given when data servers are added into a system and a single data server and a group of data servers lose efficacy. The method is used in a large-scale cloud data center, system response time is obviously shorter than the response time of a centralized monitoring mechanism, load balance is effectively achieved, low updating expenditure is achieved, and under the situations that the data servers lose efficacy in a discrete mode and in a group mode, all the data servers which lose efficacy can be detected effectively.
Owner:威海蓝海银行股份有限公司
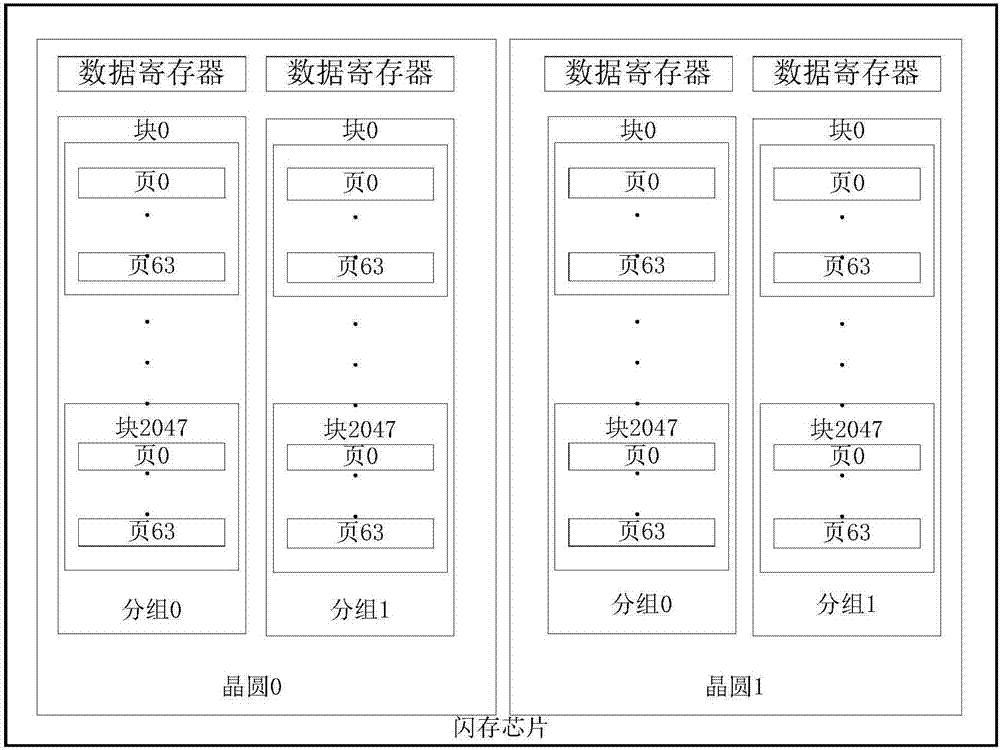
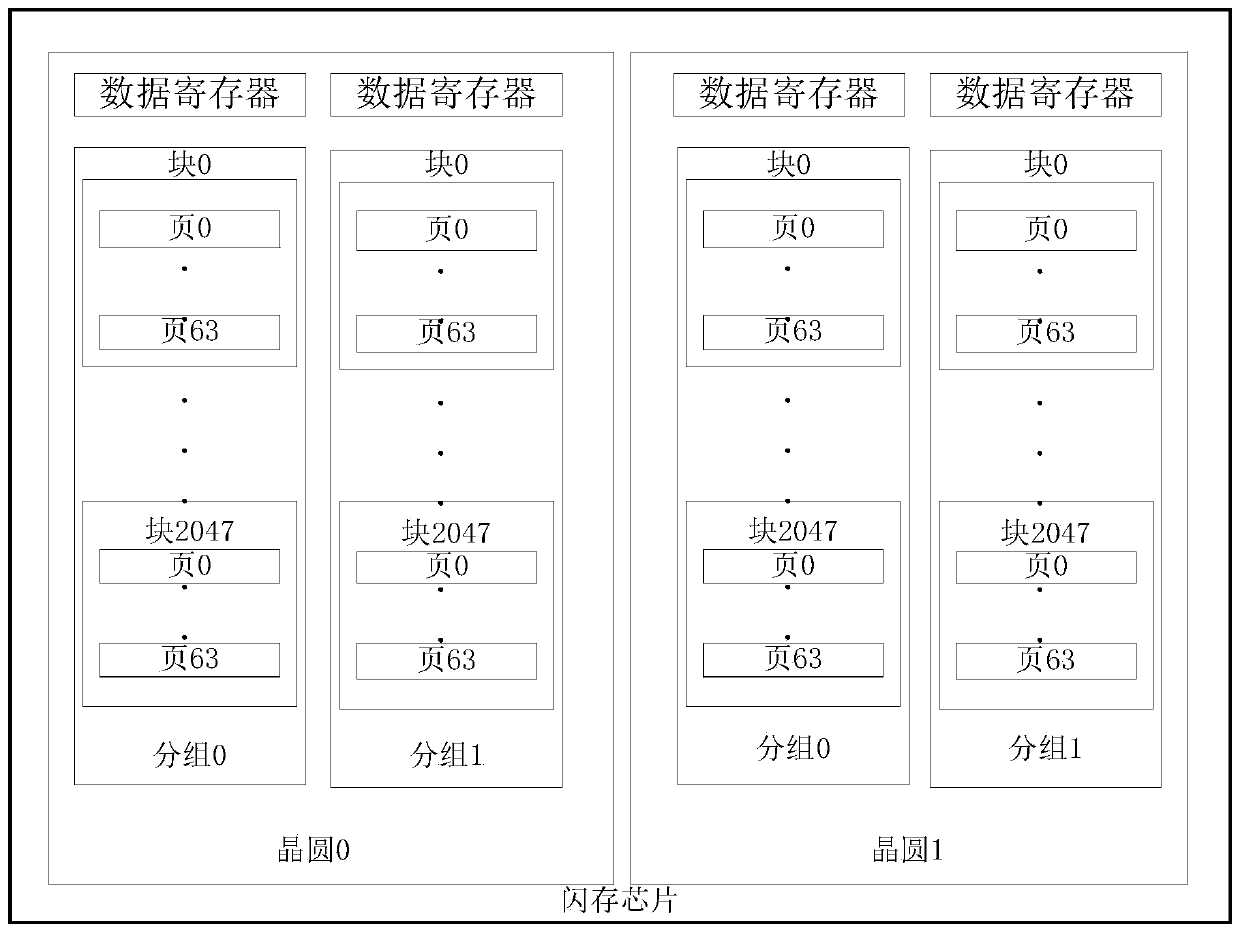
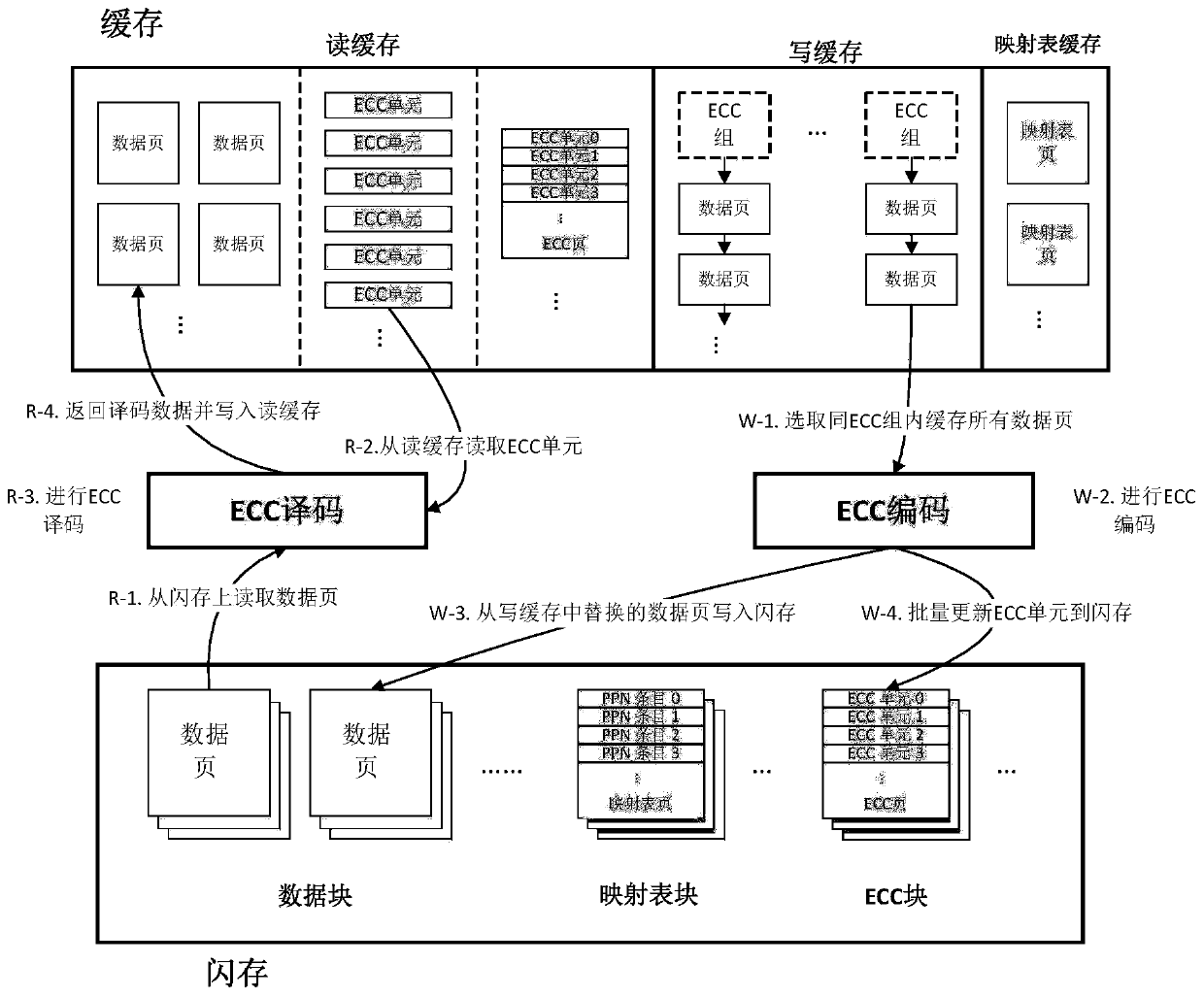
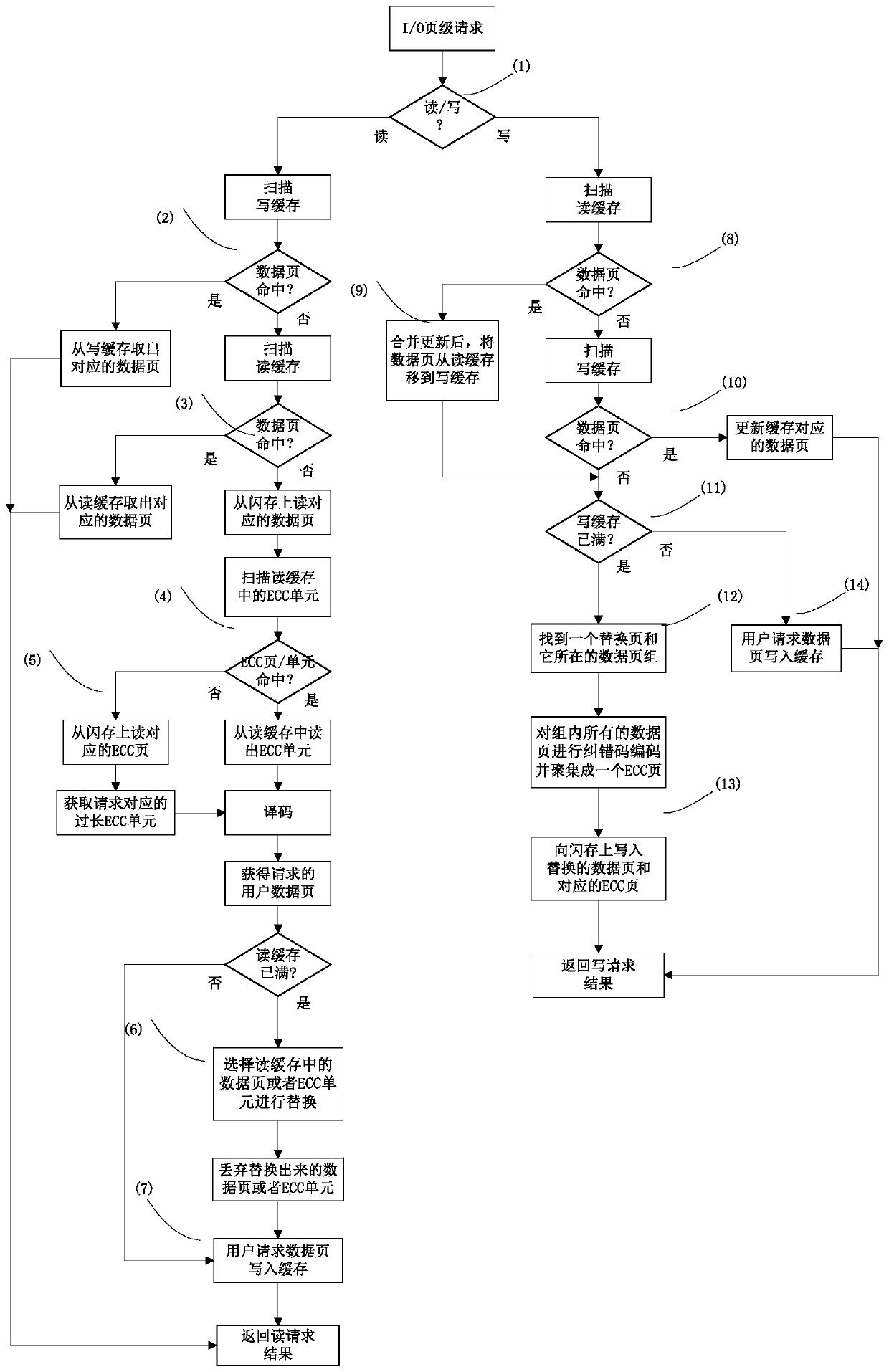
Optimization processing method for error correcting code in solid state disk system and application of optimization processing method
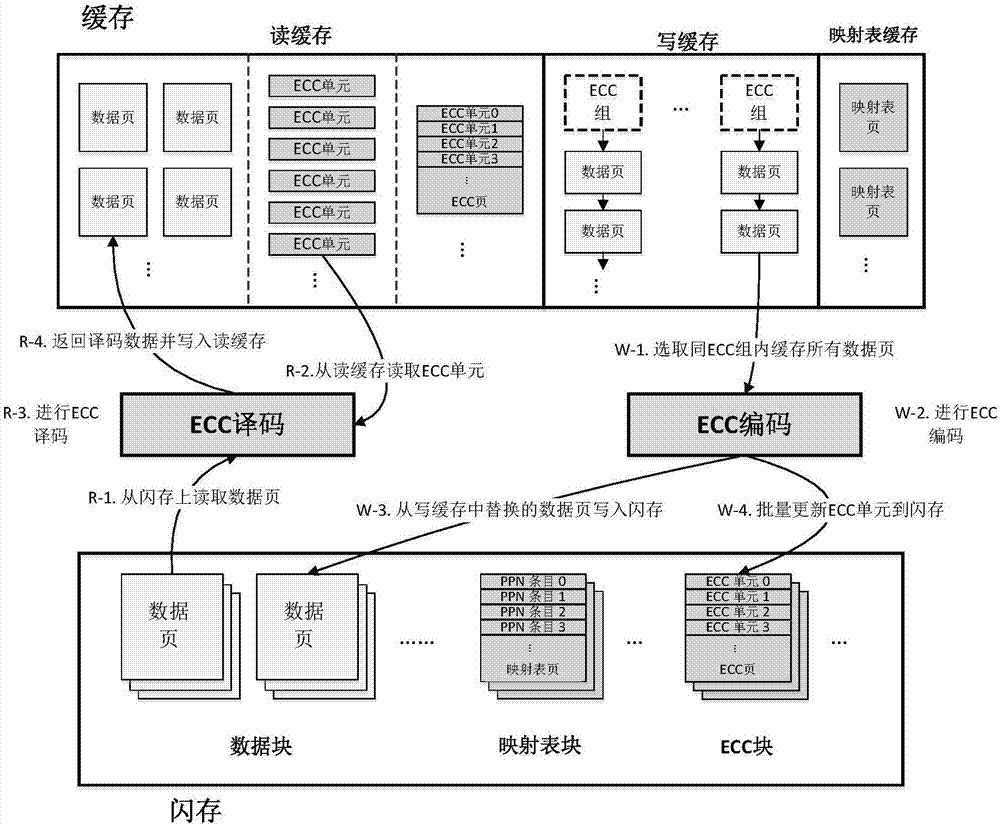
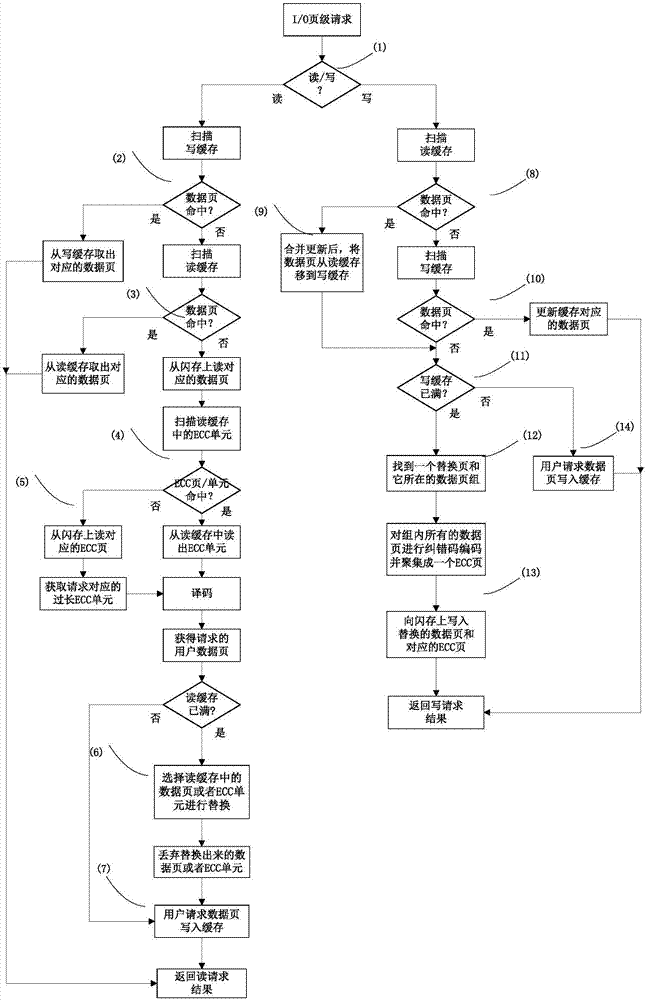
ActiveCN107221351AImprove performanceSave time for read and write accessRead-only memoriesRedundant data error correctionCache hit rateData page
The invention discloses an optimization processing method for an error correcting code in a solid state disk system. The optimization processing method is characterized by comprising the steps of combining a plurality of continuous logic data pages into a data page group, storing data pages and overlong error correcting codes in a flash memory according to a page view, and intensively storing the overlong error correcting codes of a data page group in the flash memory into a special flash memory page. According to the method, the read-write visiting time is saved, the problems of read amplification and high visit expense caused when the data pages in the other flash memory page are read are avoided, and the integral performance of a solid state disk is optimized. The invention further discloses application of the optimization processing method. By virtue of the method, the read and write caching algorithms are optimized; by caching the overlong error correcting codes, the cache hit ratio is increased; and by virtue of batch write-back of the overlong error correcting codes of multiple data pages, the updating expense is reduced, furthermore, the integral performance of the system is improved, and the service life of the solid state disk is prolonged.
Owner:HUAZHONG UNIV OF SCI & TECH
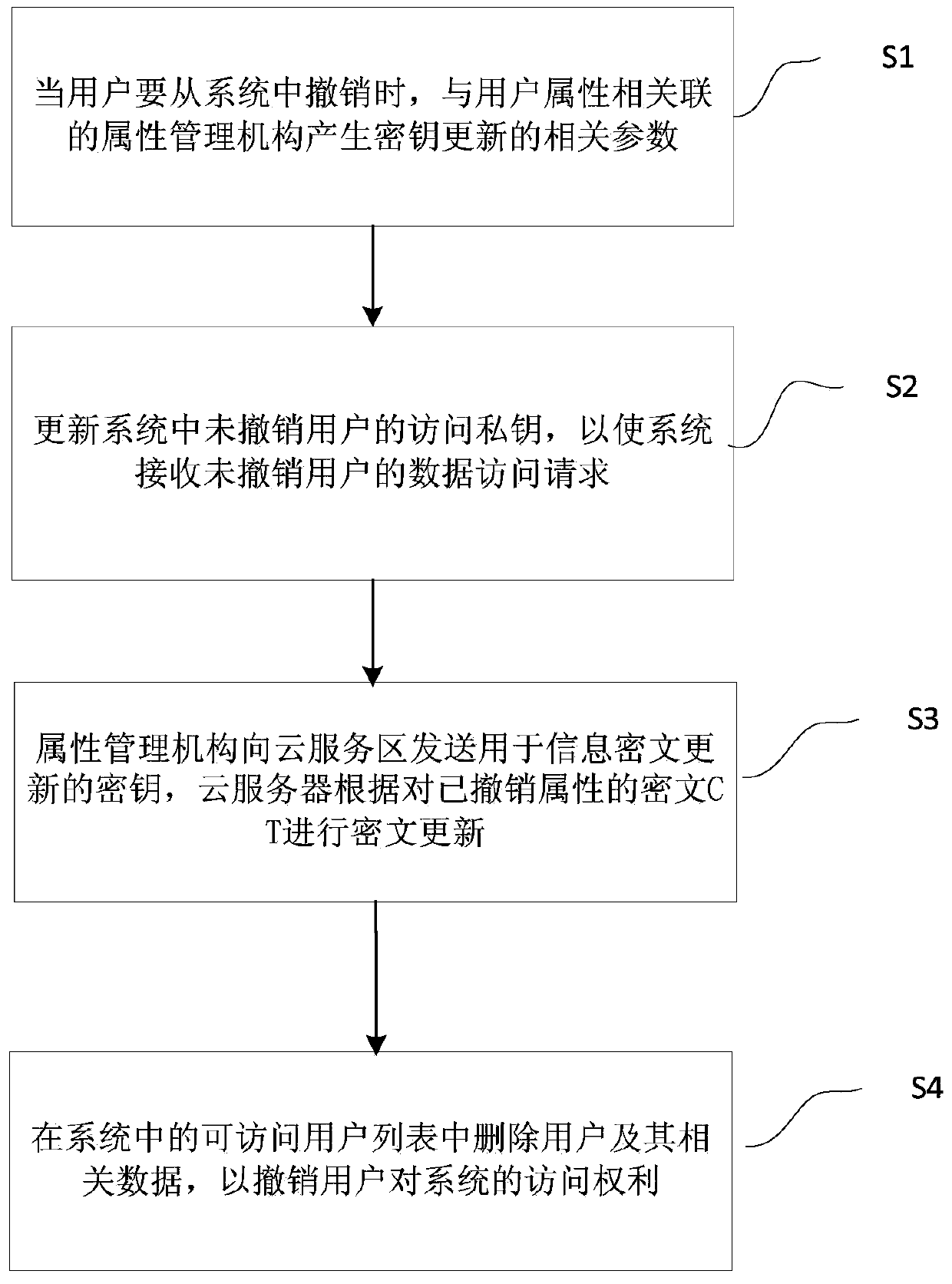
User access cancelling control method based on agent re-encryption
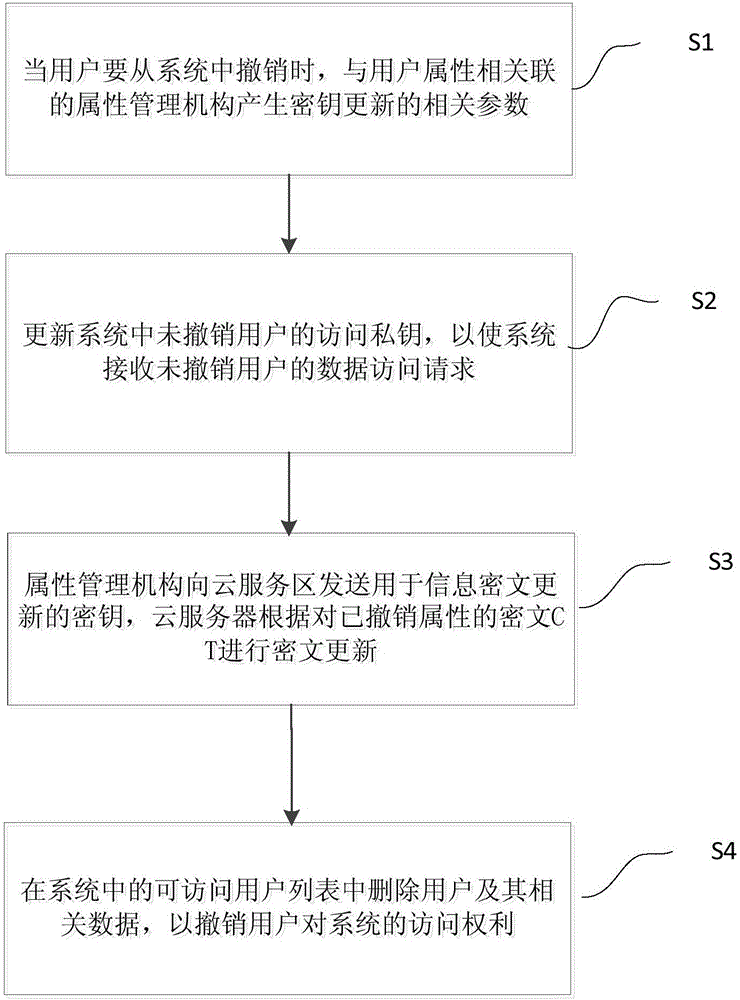
ActiveCN105871551AReduce computational overheadReduce communication overheadKey distribution for secure communicationUser needsCiphertext
The invention provides a user access cancelling control method based on agent re-encryption. The user access cancelling control method comprises the following steps: when a user needs to be canceled from a system, generating relevant parameters of key updating by an attribute management mechanism related with user attributes; updating an accessing private key of a non-cancelled user in the system, so as to receive a data access request of the non-cancelled user by the system; sending a secret key for updating an information ciphertext to a cloud service region by the attribute management mechanism and carrying out ciphertext updating on a ciphertext without attributes by a cloud server; and deleting the user and the relevant data from an accessible user list in the system so as to cancel an access authority of the user to the system. According to the user access cancelling control method, only the ciphertext related to the attributes to the cancelled user is updated, without the need of updating all the ciphertexts, so that the communication expenditure of the whole system is reduced, the operation efficiency of the whole system is improved and the safety of the system is also guaranteed.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
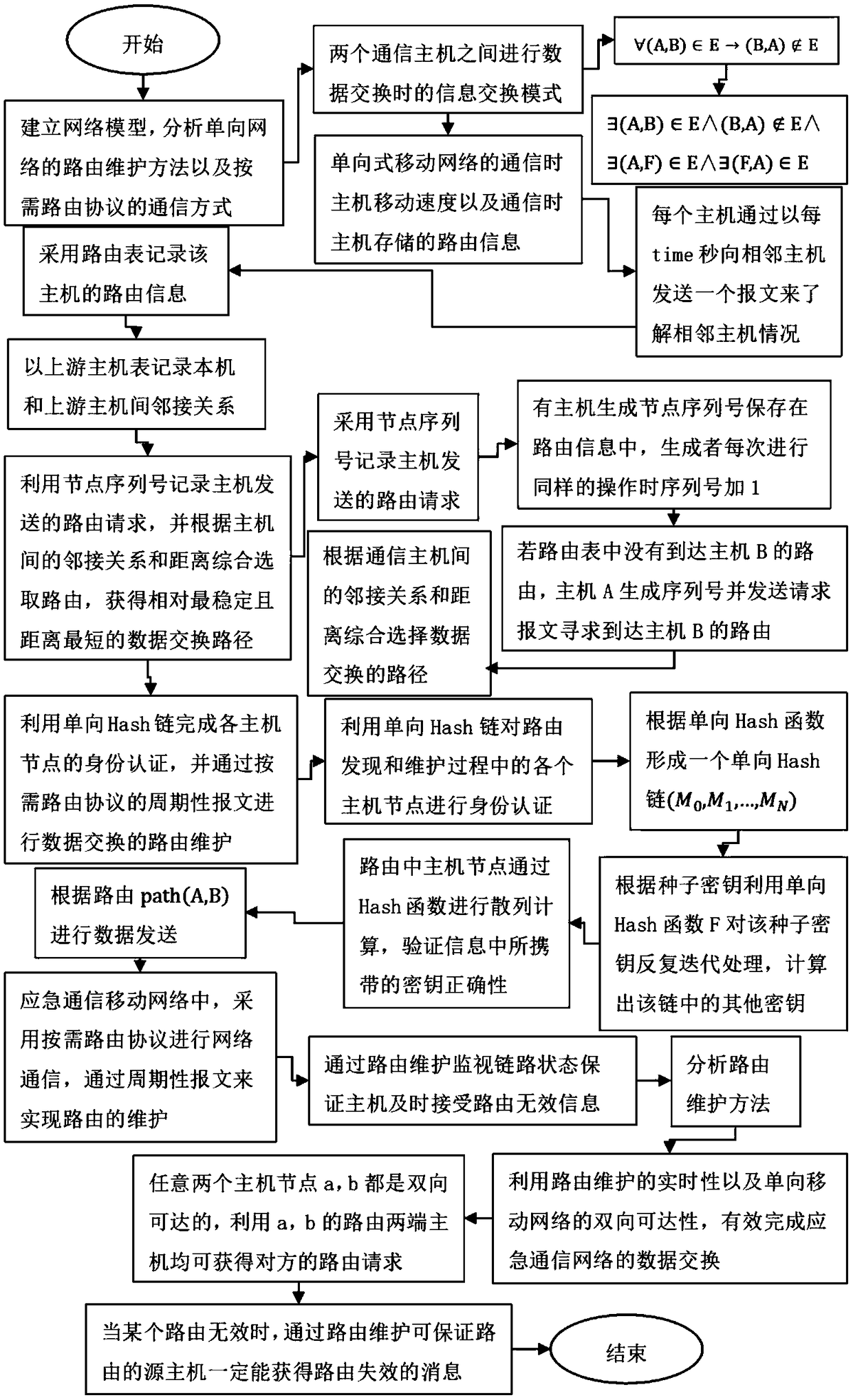
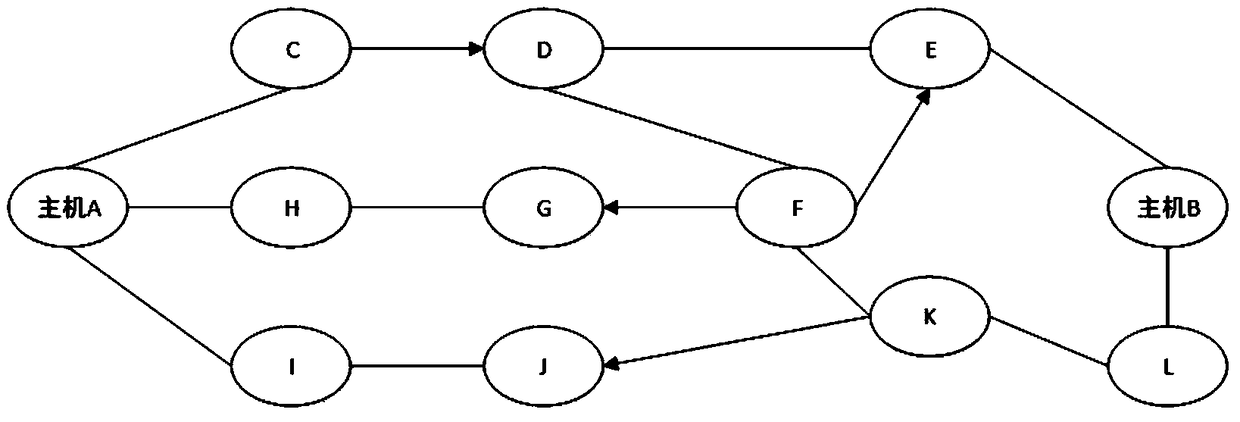
Route maintenance method for unidirectional emergency communication wireless network
InactiveCN109413654AFlexible maintenanceStable maintenanceData switching networksSecurity arrangementShortest distanceStructure of Management Information
The invention relates to a route maintenance method for a unidirectional emergency communication wireless network, solving the technical problem that a route cannot be flexibly found and an unknown network topological structure cannot be quickly adapted. A unidirectional emergency communication wireless network model is built, and all data exchange routes of a unidirectional network in the unidirectional emergency communication mobile wireless network model are computed, so that a routing protocol is determined on demand; a node serial number is used for recording a route request sent by a host, the route is selected according to an adjacency relation and a distance between the hosts, and the most stable data exchange path with the shortest distance is acquired; identity authentication ofeach host node is completed by using a unidirectional Hash chain, data exchange route maintenance is perform via a periodical message of the routing protocol on demand. According to the method, the technical scheme of maintaining the effective route of the current network in real time by using the bidirectional accessibility of the unidirectional mobile network, so that the problem is well solved,and the method can be applied to emergency communication.
Owner:赵丽妍
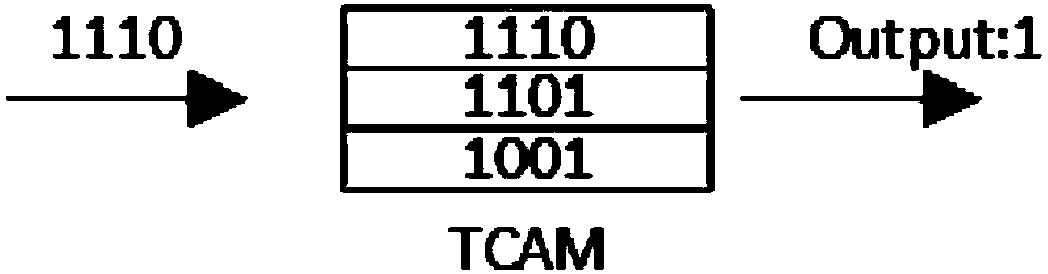
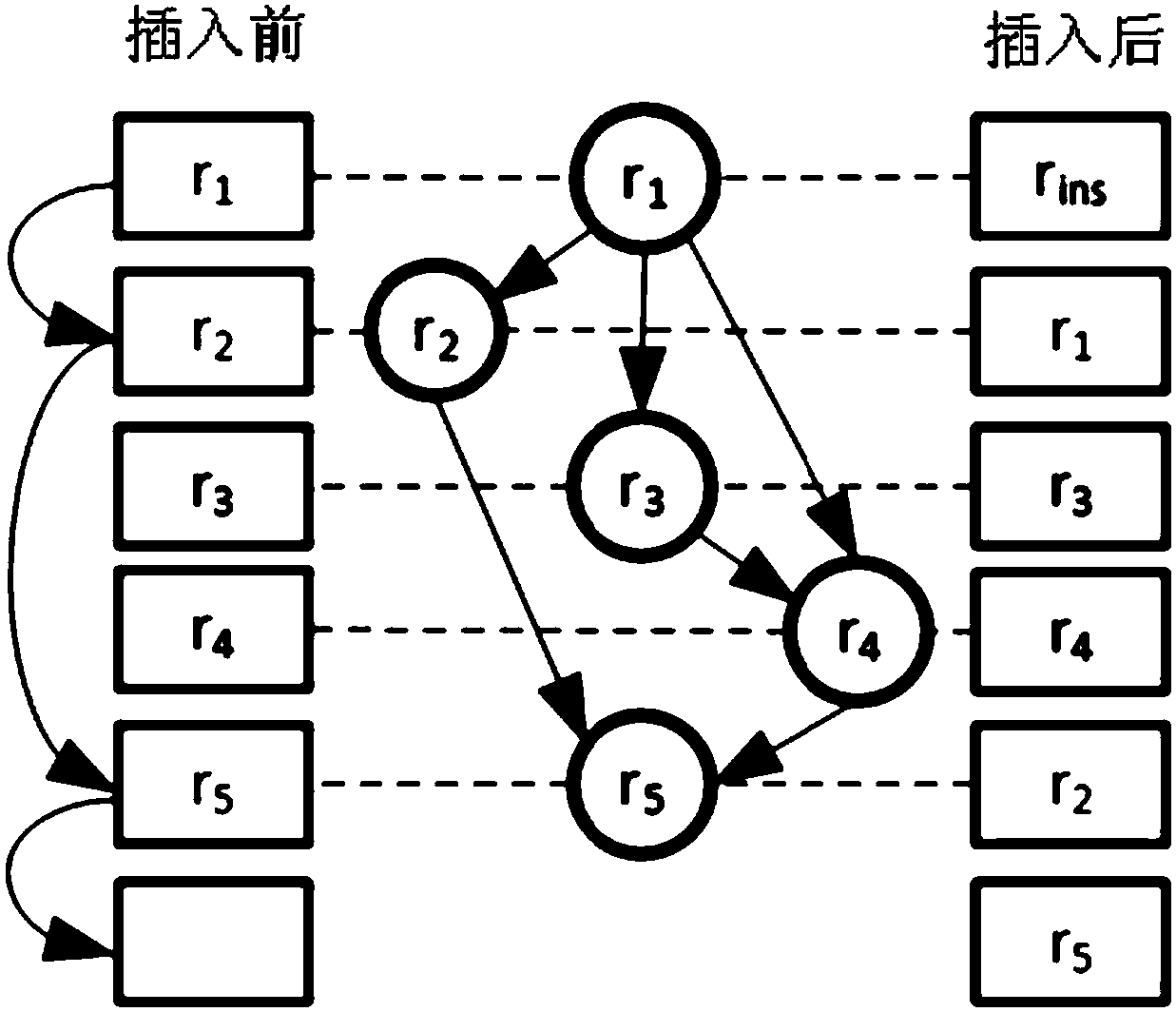
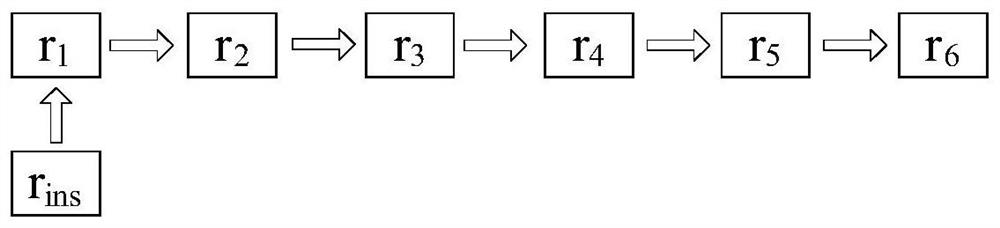
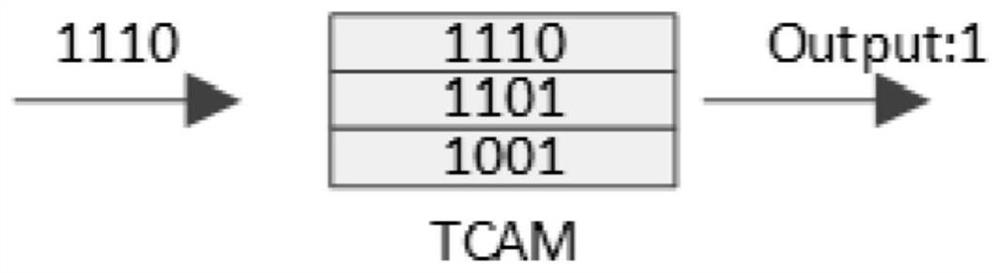
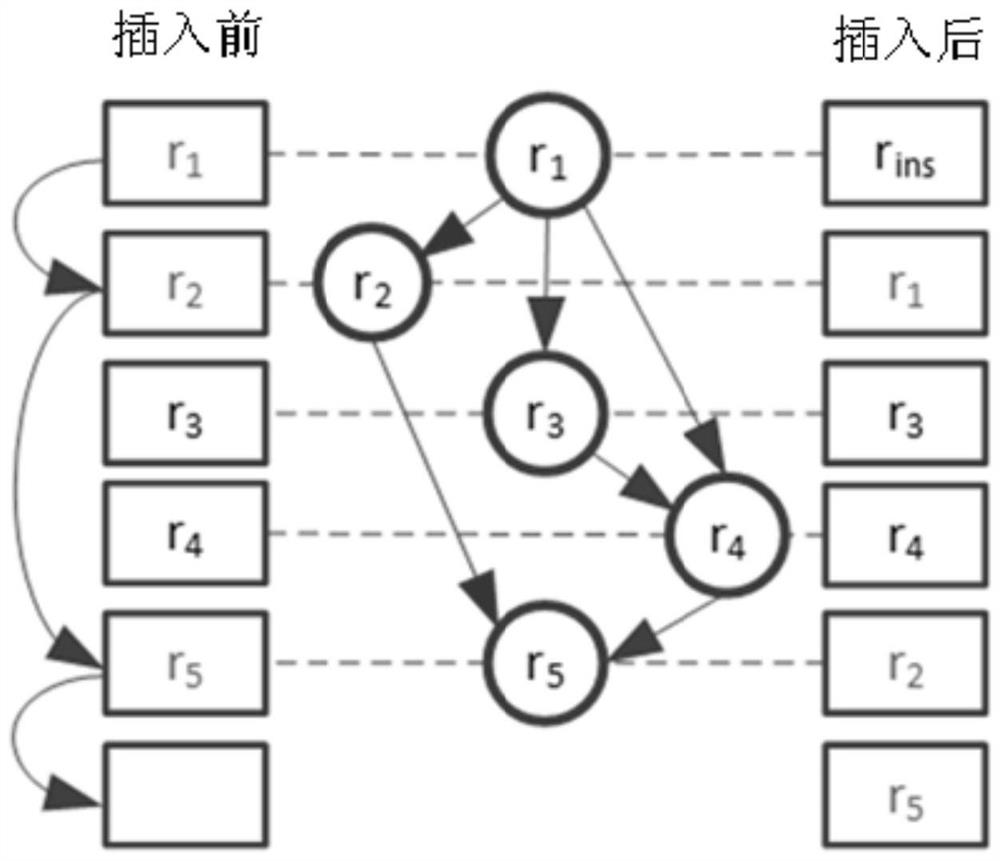
Rule set updating method and device and rule matching method and device
ActiveCN108572921AReduce update overheadReduce the number of movesMemory adressing/allocation/relocationProgramming languageRule matching
The embodiment of the invention provides a rule set updating method and device and a rule matching method and device and relates to the technical field of computers. The rule set updating method and device and the rule matching method and device are applied to a tristate content addressing memory. The rule set updating method comprises the steps that in first rule groups obtained by dividing target rule sets of the tristate content addressing memory, target rule groups which target rules belong to are determined; then, the target rules are inserted into the target rule groups to complete updating of the target rule sets, wherein for any rule having overlapping relation in the target rule sets, the quantity of rules, overlapped with the rule, in the first rule groups is not greater than thetotal quantity of the rules, overlapped with the rule, in the target rule sets. By applying the rule set updating method and device, updating expenditure for rule sets can be reduced during rule setupdating.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
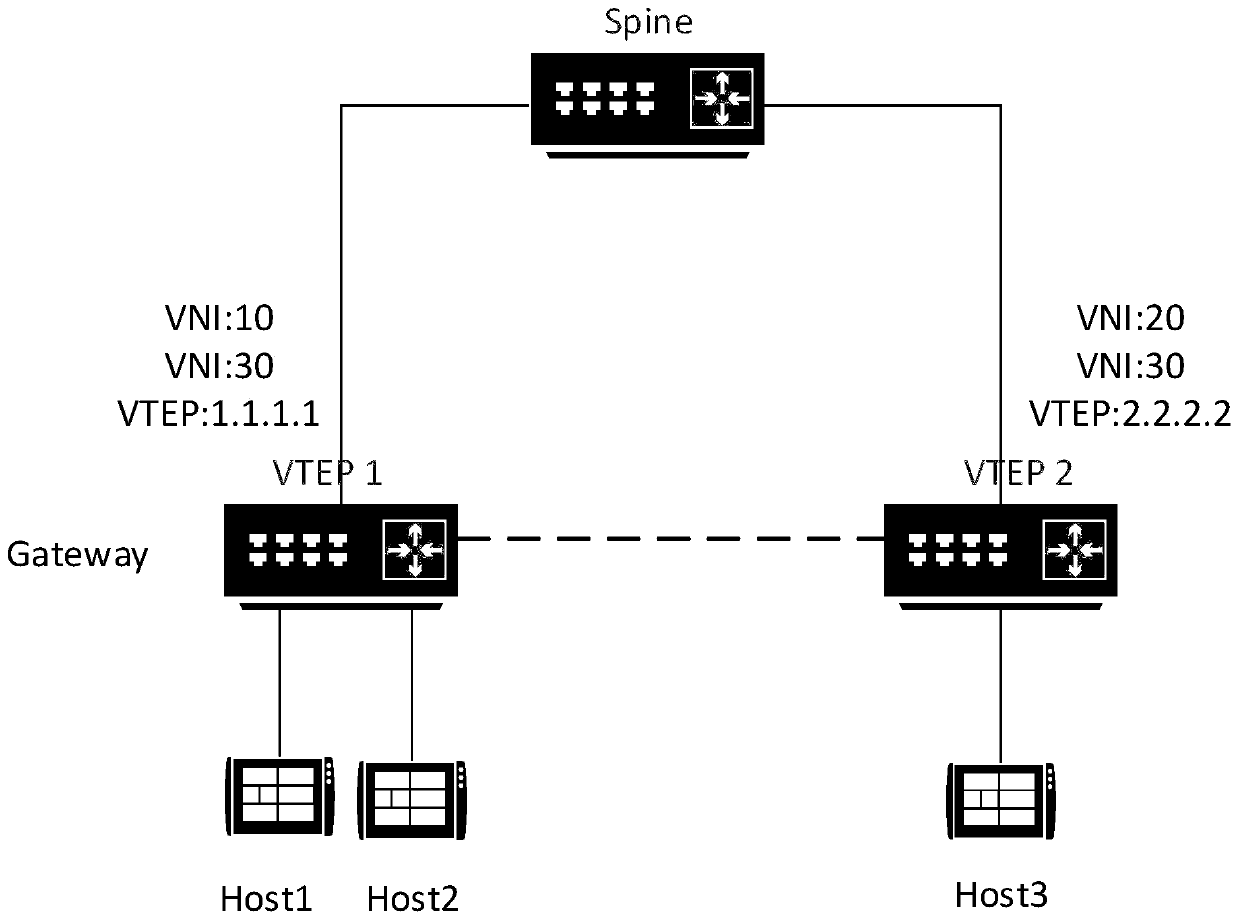
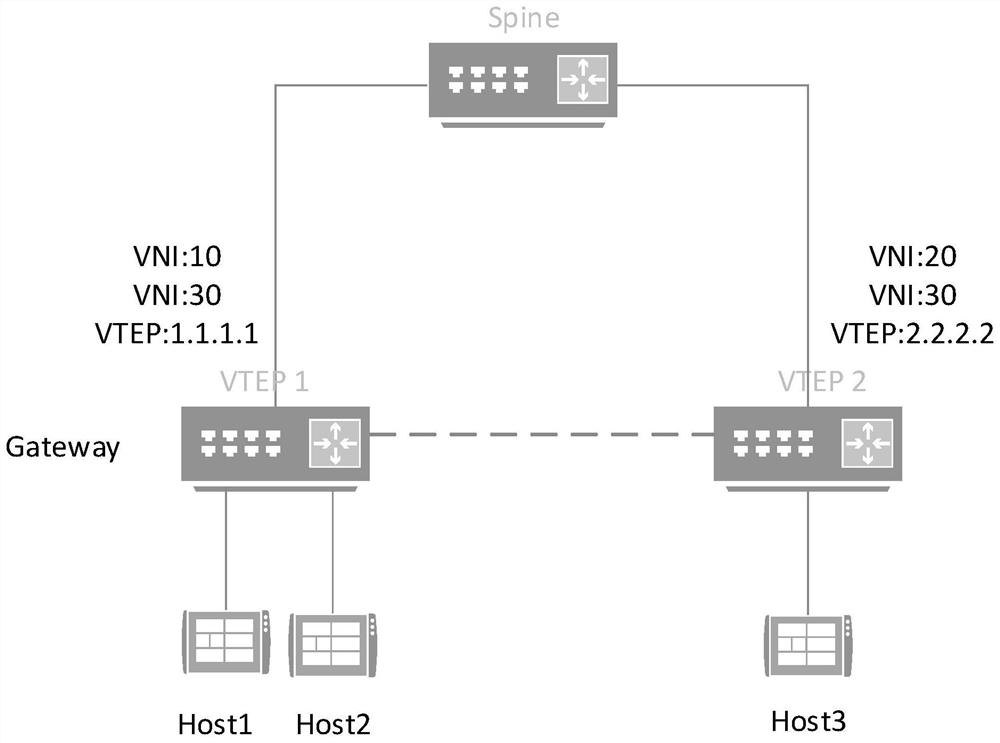
Route processing method and device under EVPN, and medium
ActiveCN111131030ARealize switchingReduce update overheadNetworks interconnectionEngineeringComputer network
The invention discloses a routing processing method and device under an EVPN, and a medium. The method is applied to a first VTEP and comprises the steps that in response to a switching instruction ofswitching from a two-layer VNI to a three-layer VNI, related routing information of the two-layer VNI is deleted, and the switching instruction is issued by binding the two-layer VNI to a corresponding VRF; and after the switched three-layer VNI takes effect, full-amount routing update is carried out through interaction with a second VTEP, and the second VTEP is a BGP neighbor of the first VTEP.According to the invention, switching between the two-layer VNI and the three-layer VNI can be realized, configuration is simple, and the cost is low.
Owner:浪潮思科网络科技有限公司
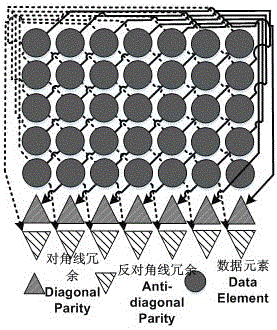
X-coding extension method capable of quickly recovering and realizing load balance
InactiveCN105824725AReduce the total number of shardsBreak the load bottleneckRedundant hardware error correctionRecovery procedureFast recovery
The invention relates to an X-coding extension method capable of quickly recovering and realizing load balance. The method comprises the following steps: performing coding extension based on X-coding used in various storage array systems, additionally arranging redundancy equipment, further reducing the total quantity of blocks required for single disk recovery on the premise of ensuring that double-disk error is allowed and reducing the IO bottleneck of the single disk recovery, thereby improving the system single disk recovery efficiency, shortening the reconstruction time, realizing the system load balance and finally realizing the improvement of system service quality. With respective to any single data disk error in an original system, the total quantity of fragment required for system single disk recovery can be reduced; with respective to any single disc error in the original system, the possible load bottleneck of the original system in the single disk recovery process can be eliminated, so that the load balance of the equipment is realized; by using binary AND-XOR, the update overhead of an additionally-arranged redundant disk is reduced, so that the service life of the redundant disk is prolonged.
Owner:NAT UNIV OF DEFENSE TECH
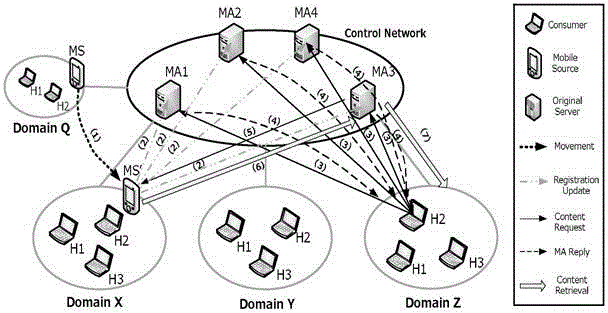
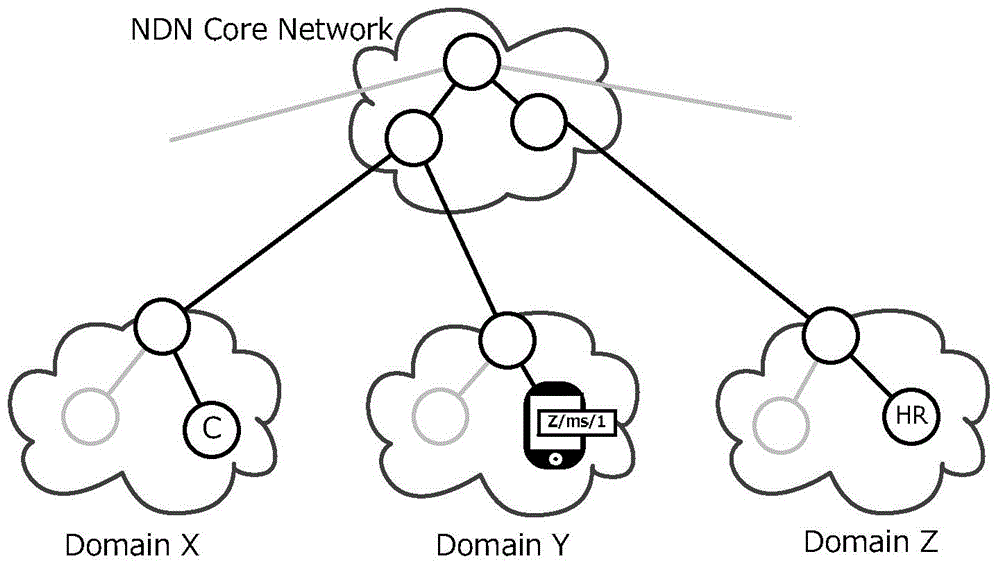
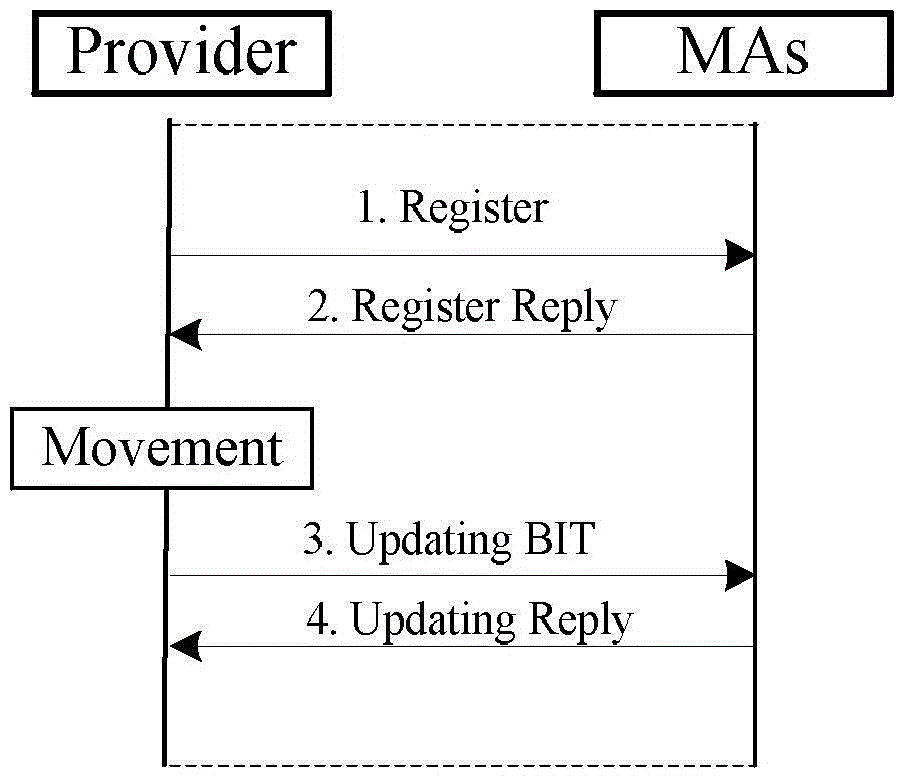
Multi-agent dynamic data source management method
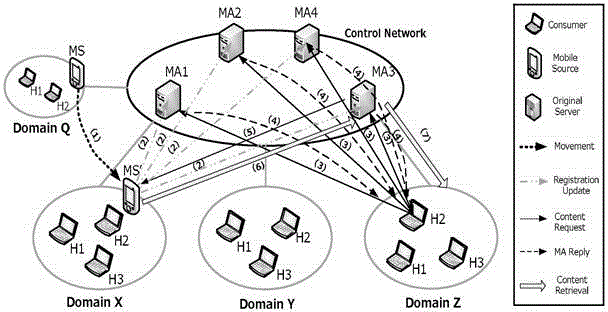
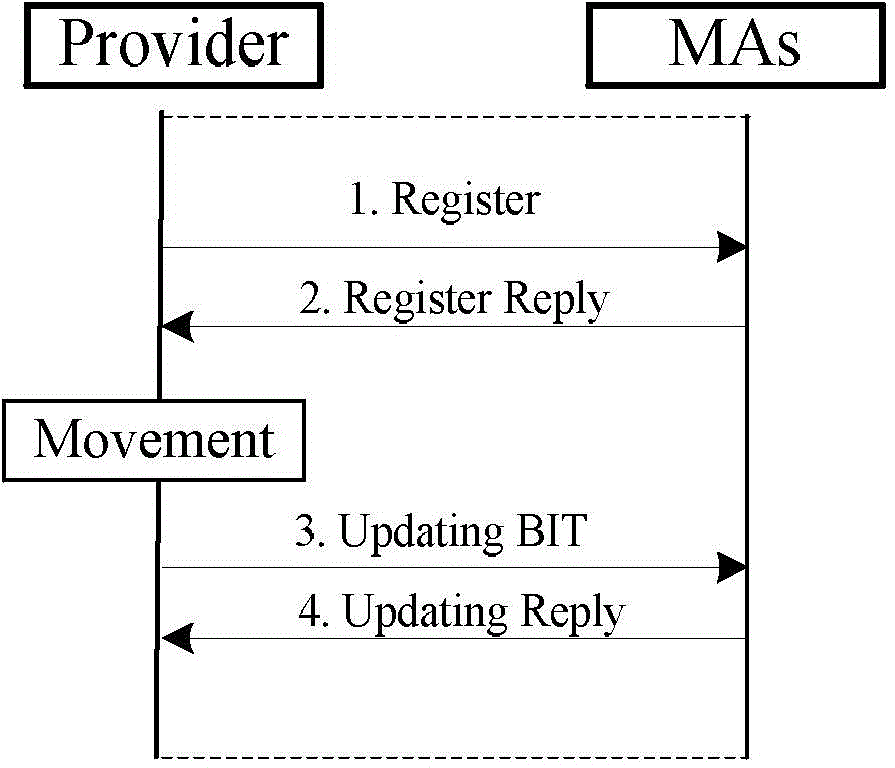
The invention relates to a multi-agent dynamic data source management method. When data content is generated in a network, the Provider sends a Register report containing both content names and signature information to all mobile proxy servers MAs in the network; after the MAs receive the Register report, the Provider calculates the data source request mobility PRMR value of the self-carried content; according to the PRMR value, either the binding updating mode or the caching processing mode is adopted. According to the invention, movement updating of the data source is carried out among a plurality of agents, corresponding management strategies are adopted according to different communication modes, content caching is performed reasonably, switching time delay caused by movement of the data source is reduced by making the best of the network property, the data network properties are optimally denominated, the network updating expenditure is reduced, and the mobility of the data source is supported.
Owner:THE PLA INFORMATION ENG UNIV
Disk array construction method based on block coding
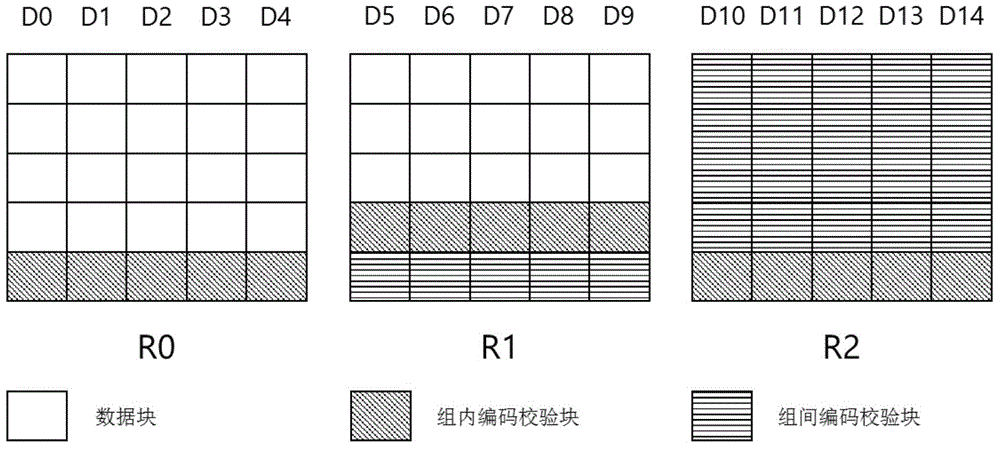
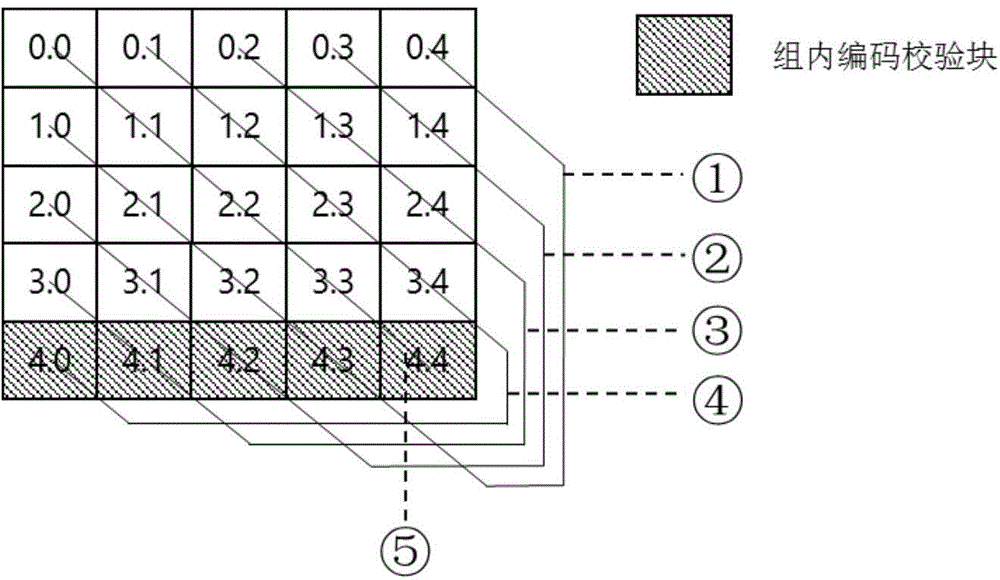
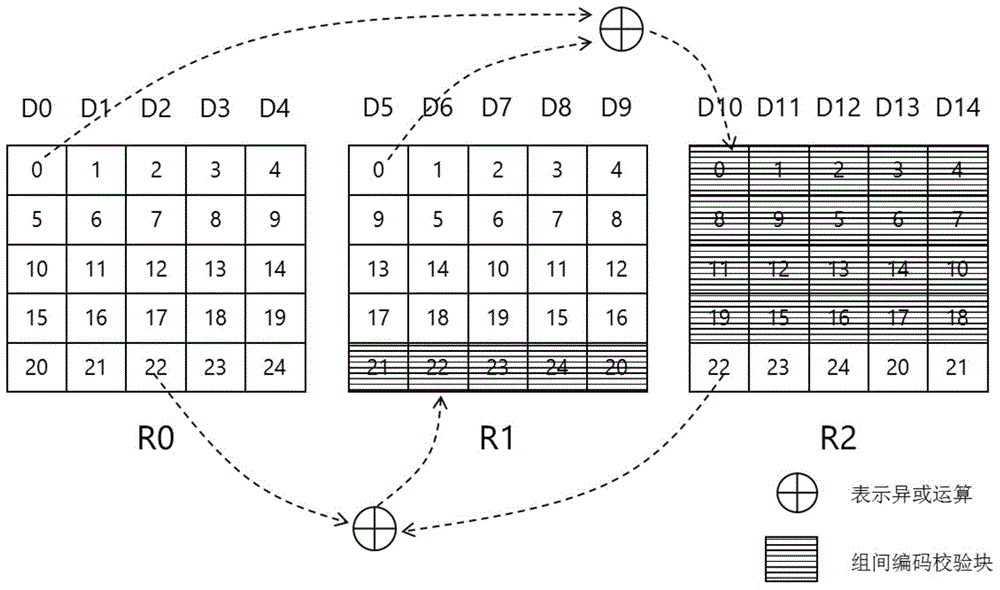
ActiveCN104615380AReduce update overheadFast encodingInput/output to record carriersBlock codeDisk array
The invention discloses a disk array construction method based on block coding. The disk array construction method based on the block coding is characterized by comprising disk partition steps, intra-block coding steps, interblock coding steps and fault-tolerant strategy formulation steps; four random disk errors can be contained in the disk array by adopting the construction method, when a single disk error occurs, the interblock coding is used for repairing; when multiple disk errors occur, the mixed repairing of the intra-block coding and the interblock coding are adopted. Compared with traditional disk array construction methods, The disk array construction method based on the block coding, on the premise of same fault-tolerant capability and redundancy rate, the total data amount read and the data reading amount of each disk are obviously decreased in the repairing of the single disk error, the network bandwidth is saved, the repairing speed is speeded up, and the system reliability is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD +1
User revocation access control method based on proxy re-encryption
ActiveCN105871551BReduce computational overheadReduce communication overheadKey distribution for secure communicationData accessProxy re-encryption
The present invention proposes a user revocation access control method based on proxy re-encryption, including: when the user is about to withdraw from the system, the attribute management organization associated with the user attribute generates relevant parameters for key update; The access private key of the user has not been revoked, so that the system receives the data access request of the user who has not been revoked; the attribute management agency sends the key for information ciphertext update to the cloud service area, and the cloud server The ciphertext whose attributes have been revoked is updated; the user and its related data are deleted from the accessible user list in the system, so as to revoke the user's access right to the system. The present invention only updates the ciphertext related to the revoked user attributes, instead of updating all ciphertexts, thereby reducing the communication overhead of the entire system, improving the operating efficiency of the entire system, and ensuring the security of the system .
Owner:JIANGSU DIGITAL DNA TECH CO LTD
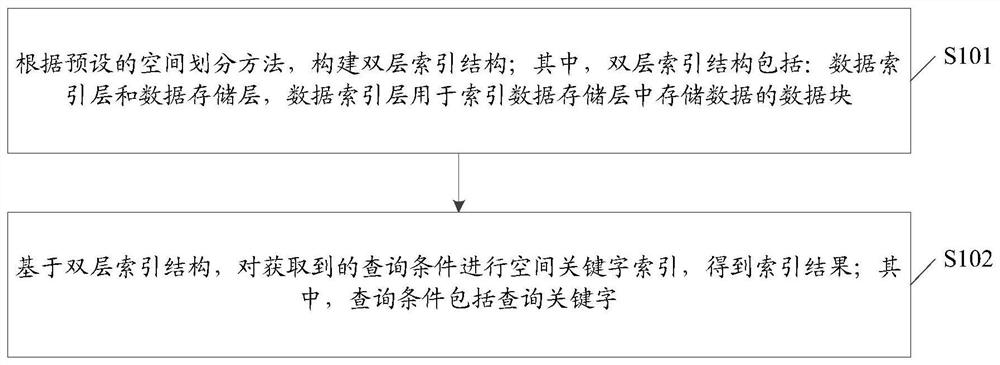
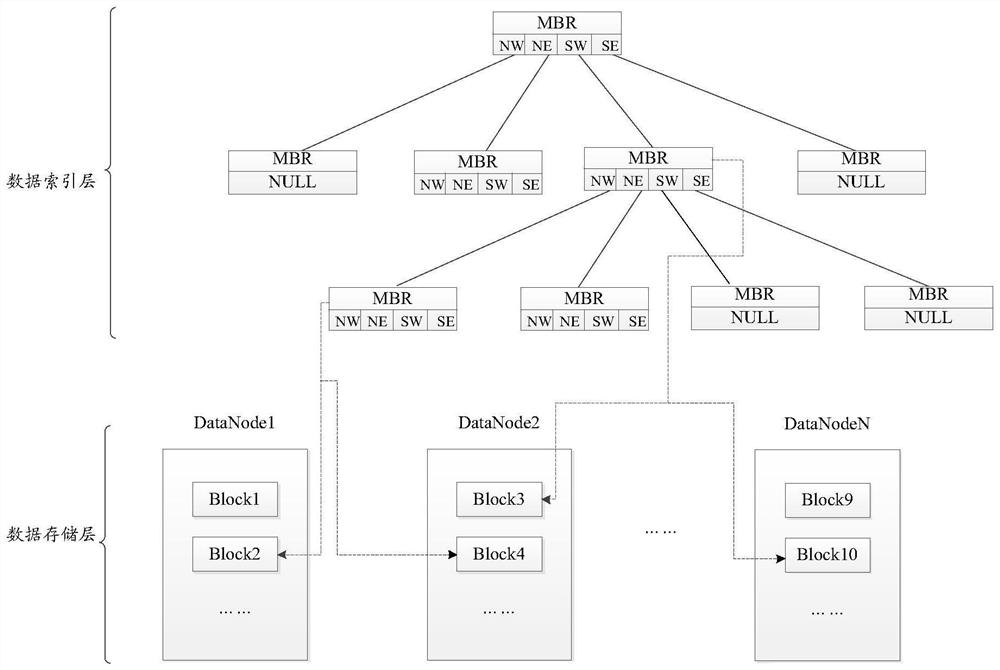
A spatial keyword indexing method, platform, and storage medium
ActiveCN108628969BReduce update overheadImprove query efficiencySpecial data processing applicationsDatabase indexingSpatial partitionData mining
Owner:MIGU CO LTD +1
Hashing method based on double-counting bloom filter and hashing device
ActiveCN101655861BReduce update overheadReduce demandMemory adressing/allocation/relocationSpecial data processing applicationsBloom filterSelection principle
The invention provides a hashing method for realizing hashing insert operation on a hash table; the hash table comprises a plurality of buckets, the bucket comprises an insert counter and a delete counter, the insert counter is used for recording the number of insert elements in the bucket, and the delete counter is used for recording the number of the delete elements in the bucket; the method comprises the following steps: the element to be operated is mapped to at least one bucket of the hash table according to hash function, and the bucket is called as a candidate bucket; a target bucket is found from the candidate buckets according to selection principle of the target bucket; the elements to be inserted are inserted in the target bucket; weather the inserted elements have effect on the storage position of the stored elements in the candidate bucket is judged, if the storage positions of the stored elements can not meet the selection principle of the target bucket, the storage positions of the stored elements are re-adjusted; the hashing method also comprises the step of accumulating the value of the insert counter of the bucket.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
A Multi-Agent-Based Dynamic Data Source Management Method
The invention relates to a multi-agent dynamic data source management method. When data content is generated in a network, the Provider sends a Register report containing both content names and signature information to all mobile proxy servers MAs in the network; after the MAs receive the Register report, the Provider calculates the data source request mobility PRMR value of the self-carried content; according to the PRMR value, either the binding updating mode or the caching processing mode is adopted. According to the invention, movement updating of the data source is carried out among a plurality of agents, corresponding management strategies are adopted according to different communication modes, content caching is performed reasonably, switching time delay caused by movement of the data source is reduced by making the best of the network property, the data network properties are optimally denominated, the network updating expenditure is reduced, and the mobility of the data source is supported.
Owner:THE PLA INFORMATION ENG UNIV
Rule set update method, device, rule matching method and device
ActiveCN108572921BReduce update overheadReduce the number of movesMemory adressing/allocation/relocationAlgorithmTheoretical computer science
Embodiments of the present invention provide a rule set updating method, device, and rule matching method and device, which relate to the field of computer technology, and are applied to a three-state content addressable memory, wherein the rule set updating method includes: dividing the three-state content addressable memory In each of the first rule groups obtained from the target rule set, determine the target rule group to which the target rule belongs; then insert the target rule into the target rule group to complete the update of the target rule set. Wherein, for any rule that has an intersecting relationship in the target rule set, the number of rules intersecting it in the first rule group is not greater than the total number of rules intersecting it in the target rule set. When the solution provided by the embodiment of the present invention is applied to update the rule set, the update overhead of the rule set can be reduced.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
A routing processing method, equipment, and medium under EVPN
ActiveCN111131030BRealize switchingReduce update overheadNetworks interconnectionEngineeringProcessing
The present application discloses a route processing method, equipment and media under EVPN. The method is applied to the first VTEP, including: in response to a switching instruction from a Layer 2 VNI to a Layer 3 VNI, deleting the relevant routing information of the Layer 2 VNI, the switching instruction is issued by binding the Layer 2 VNI to the corresponding VRF ; After the switched Layer 3 VNI takes effect, the full route update is performed by interacting with the second VTEP, which is the BGP neighbor of the first VTEP. The present application can realize switching between a layer-2 VNI and a layer-3 VNI, and the configuration is simple and the cost is low.
Owner:浪潮思科网络科技有限公司
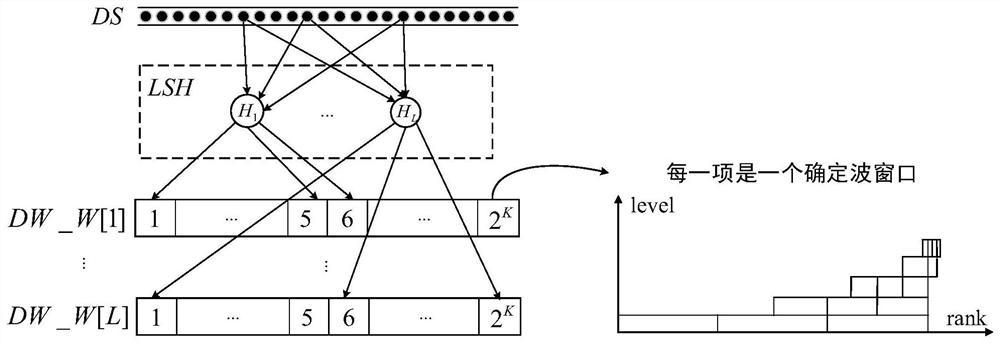
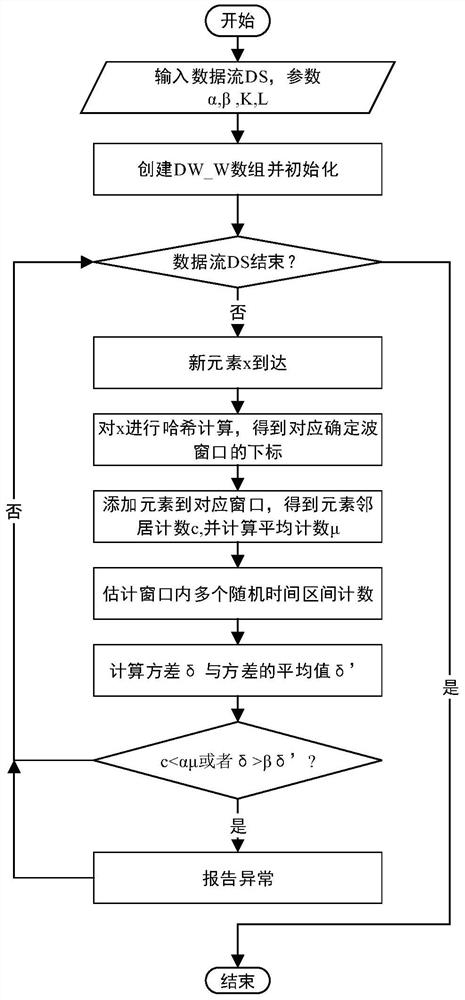
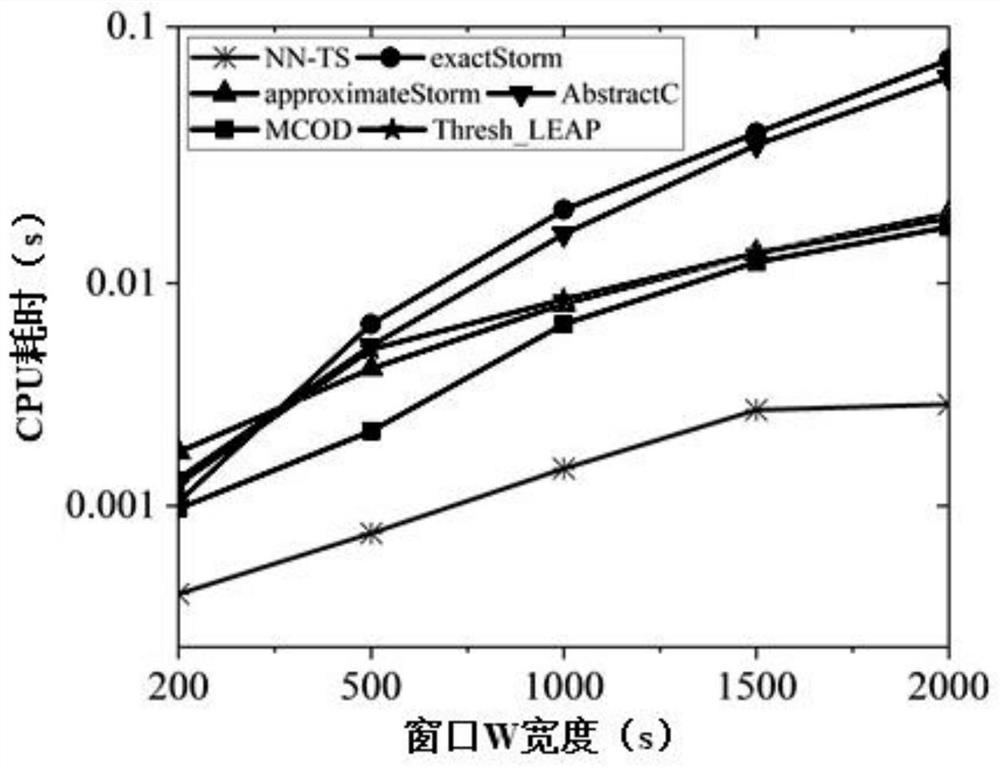
A Nearest Neighbor Based Time Sensitive Anomaly Detection Method in Big Data Streams
ActiveCN109871870BImprove time and efficiencyAvoid distance calculationsCharacter and pattern recognitionTime rangeData stream
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
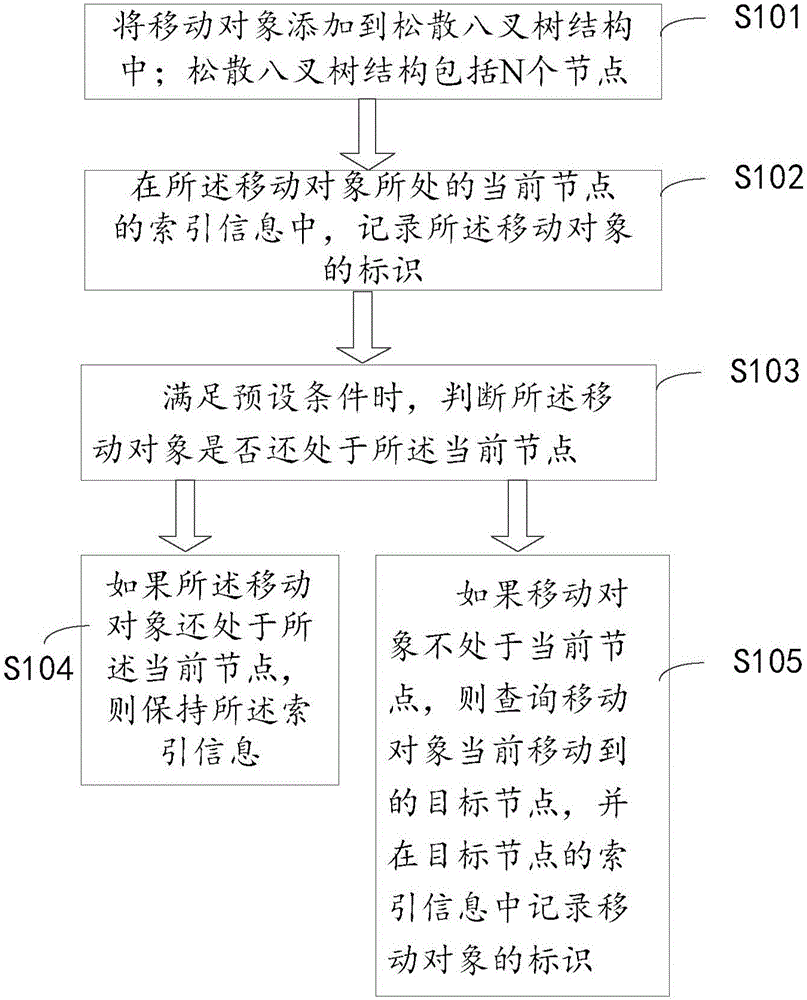
Three-dimensional moving object indexing method and apparatus
InactiveCN105930394AReduce update overheadGuaranteed accuracySpecial data processing applicationsTime processingIndex method
The invention discloses a three-dimensional moving object indexing method and apparatus. The method comprises the steps of adding a moving object into a loose octree structure; in index information of a current node at which the moving object is located, recording an identifier of the moving object; when a preset condition is met, judging whether the moving object is still located at the current node or not; if the moving object is still located at the current node, keeping the index information; and if the moving object is not located at the current node, querying a target node to which the moving object moves, and recording the identifier of the moving object in index information of the target node. The method and apparatus provided by the invention are used for solving the technical problems of huge update quantity and difficulty in meeting real-time processing demands due to adoption of the moving object with relatively large octree structure index scale in the prior art; and the technical effects of reducing the index update overhead and improving the indexing efficiency on the basis of keeping the indexing accuracy are achieved.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
A hybrid cloud storage system and method based on multi-level cache
ActiveCN103338242BLower latencyHigh bandwidthTransmissionSpecial data processing applicationsIp addressPassword
The invention discloses a hybrid cloud storage method based on multi-level cache. The method comprises the following steps: a user joins a user group for login according to the local area network where the user is, and sends a user name and a password for user authentication to a super node of the region where the user group is, the super node achieves authentication of the user according to the received user name and password, the user receives a catalog view returned from the super node and metadata information of all files and sends the catalog view to a group leader node of the user group, the group leader node judges whether the buffer memory space of the group contains files in the catalog view according to the received catalog view, and if yes, feeds the IP address of the node in which the files are saved in the buffer memory space of the group to the user, and the user determines the optimal access path of each file in the catalog view according to the received feedback information. The hybrid cloud storage method allows the user to access data from the user group cache and the super node layer cache which have lower network delay, thereby lowering the network delay of the user data access.
Owner:HUAZHONG UNIV OF SCI & TECH
A method of server collaborative monitoring for large-scale cloud data centers
ActiveCN103944784BShort response timeLoad balancingData switching networksCloud data centerFailure risk
The invention discloses a large-scale-cloud-data-center-oriented server cooperative monitoring method. The mode that servers sense and monitor each other replaces a monitoring mode of a centralized structure, the self-managing capacity of the servers is improved, the monitoring burden of the monitoring servers is effectively lowered, and performance bottlenecks and singe point failure risks are removed. A cooperative monitoring mechanism and a functional component are provided, and the working steps of the cooperative monitoring mechanism are given when data servers are added into a system and a single data server and a group of data servers lose efficacy. The method is used in a large-scale cloud data center, system response time is obviously shorter than the response time of a centralized monitoring mechanism, load balance is effectively achieved, low updating expenditure is achieved, and under the situations that the data servers lose efficacy in a discrete mode and in a group mode, all the data servers which lose efficacy can be detected effectively.
Owner:威海蓝海银行股份有限公司
Method for realizing longest prifix address route search using sectioned compressed list
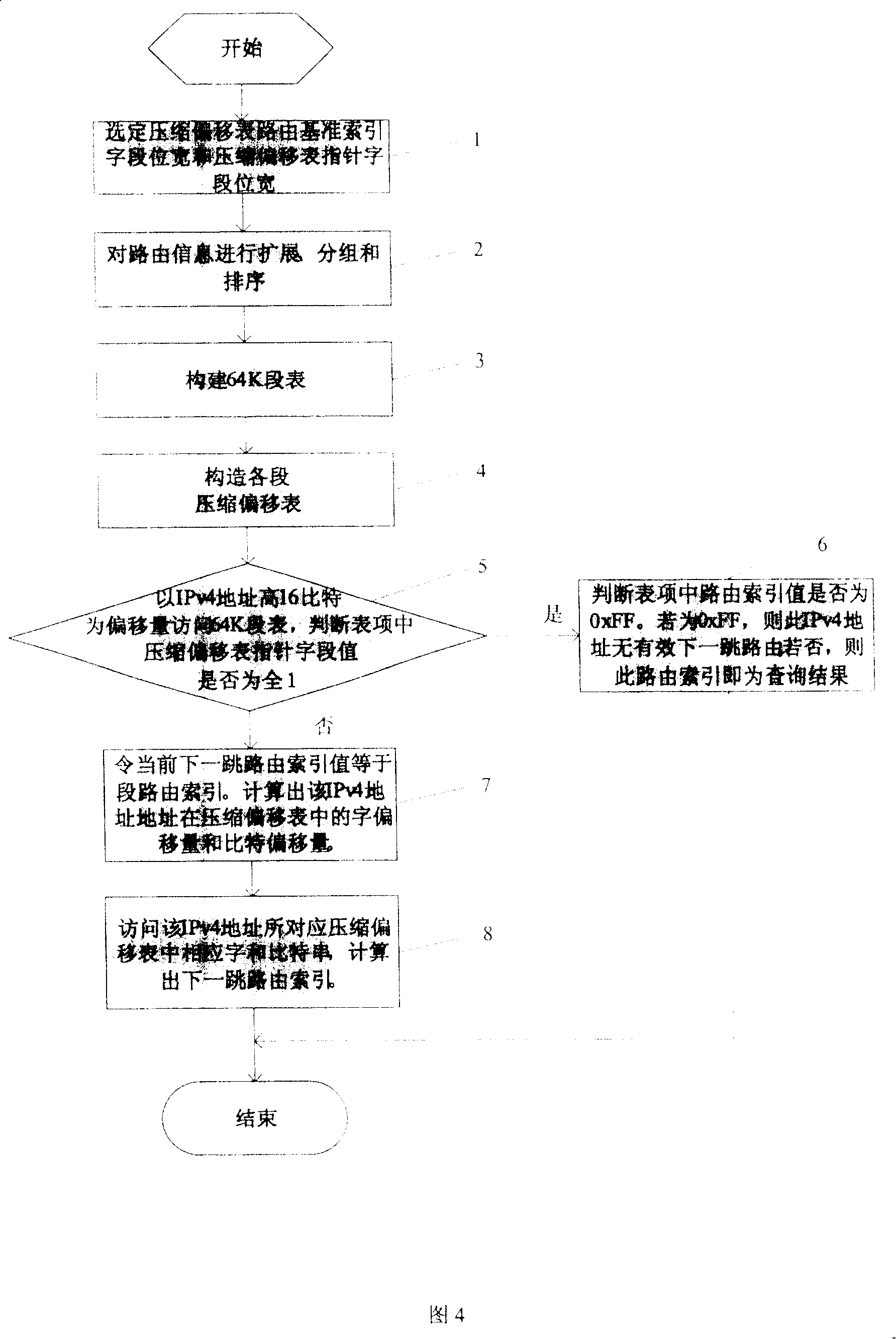
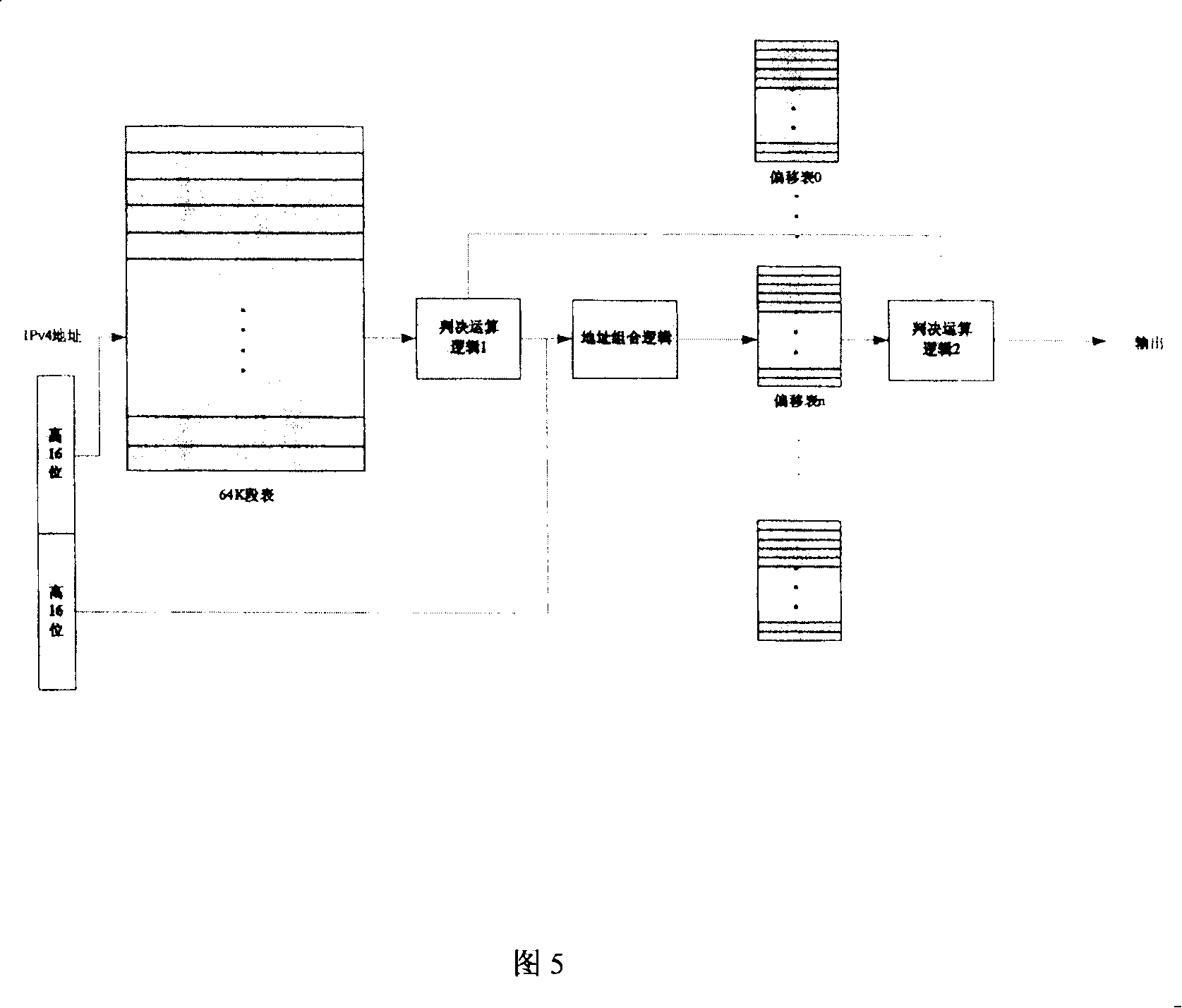
ActiveCN100375463CSave storage spaceLess lookup speedData switching by path configurationStore-and-forward switching systemsRoute searchComputer science
This invention relates to a method for realizing the longest prefix address route look up which sets up two stages of route information lists: a 64 segment list and a compressed offset list, among which, the route index value in the offset list is compressed to the difference between the said index value and the primary route index for storing route look-up information. When looking up, high 16 order of the being looked-up target IPV4 address is used as the index value to position the item in 64k segment list and judge if the compressed offset list pointer is invalid, if so, the route index is the next jump route index value corresponding to IPV 4 address, if not, the pointer value, primary value and width corresponding to compressed offset list are got to get the next jump route index value of IPV4by accessing offset list items with the low 16 order of the IPV4.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
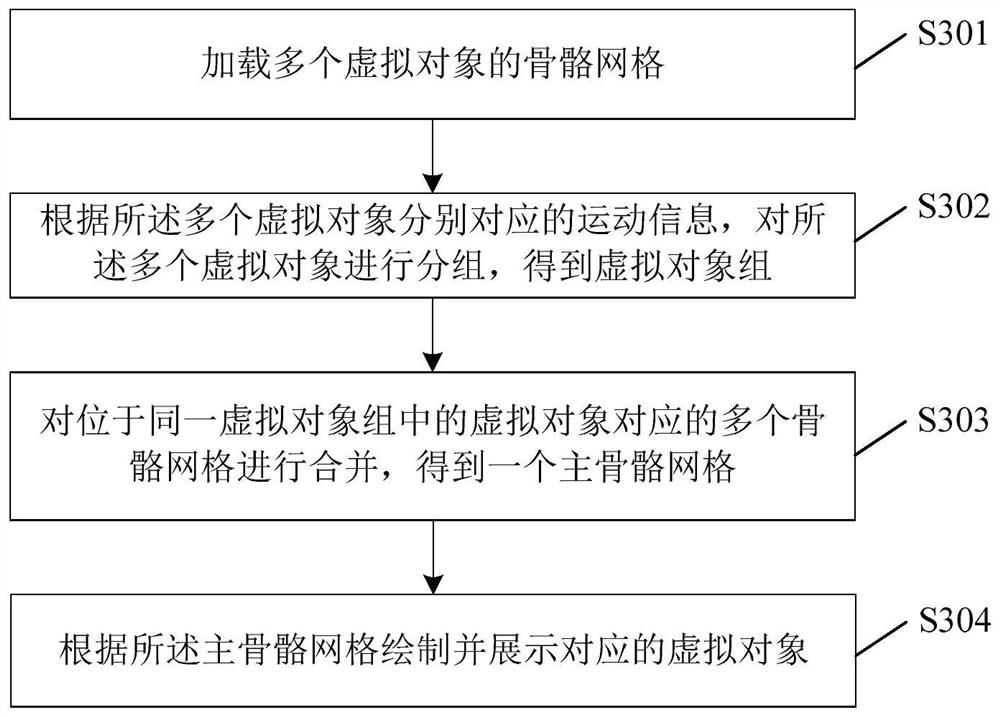
Virtual object display method and related device
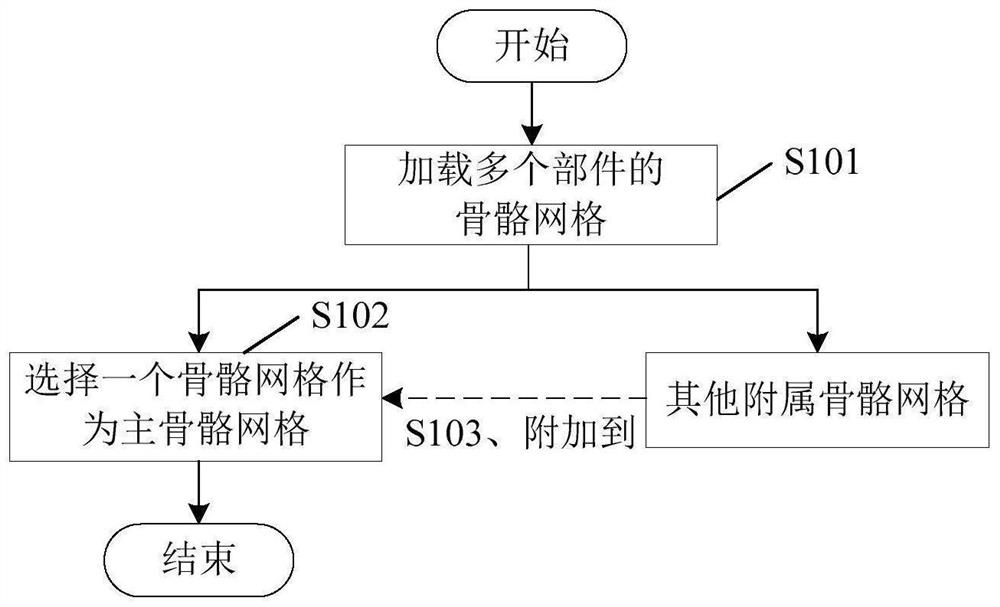
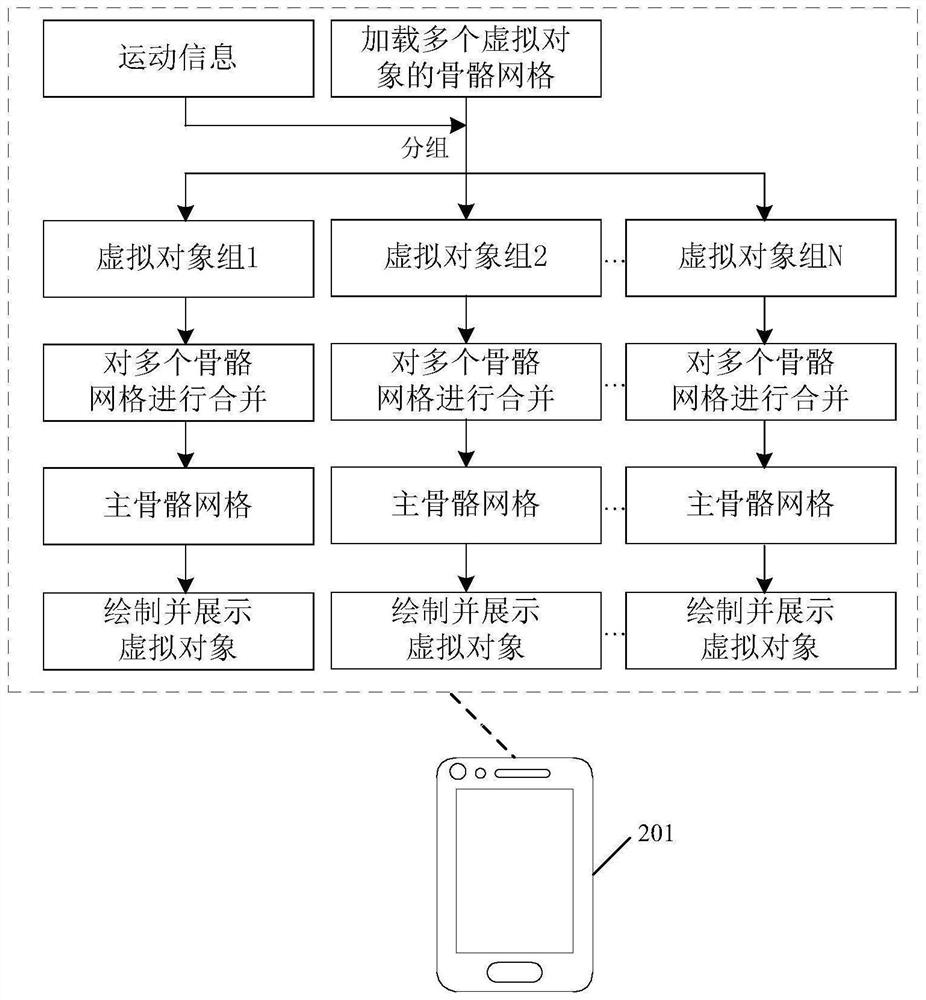
PendingCN113457162AReduce location update overheadImprove drawing speedVideo games3D modellingComputer visionMesh grid
The invention discloses a virtual object display method and a related device, when a plurality of virtual objects comprising a plurality of parts need to be displayed, each part has a corresponding skeleton grid, so skeleton grids of a plurality of virtual objects are loaded, a plurality of virtual objects are grouped according to the motion information corresponding to a plurality of virtual objects to obtain a plurality of virtual object groups; the movement of the virtual objects in the same virtual object group at the same moment is consistent; a plurality of skeleton grids corresponding to the virtual objects in the same virtual object group are combined to obtain a main skeleton grid, and the corresponding virtual object is drawn and displayed according to the main skeleton grid. According to the method, a plurality of position updating nodes are reduced into one position updating node, so the position updating expenditure of a plurality of skeleton grids is greatly reduced, the drawing speed of the display card is increased, and fluency of a picture displayed on a screen is improved; the overhead is greatly reduced, so the number of players on the same screen does not need to be reduced, and the player experience is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A kind of optimization processing method and application of error correction code in solid state disk system
ActiveCN107221351BImprove performanceSave time for read and write accessRead-only memoriesRedundant data error correctionParallel computingCache hit rate
The invention discloses an optimization processing method for an error correcting code in a solid state disk system. The optimization processing method is characterized by comprising the steps of combining a plurality of continuous logic data pages into a data page group, storing data pages and overlong error correcting codes in a flash memory according to a page view, and intensively storing the overlong error correcting codes of a data page group in the flash memory into a special flash memory page. According to the method, the read-write visiting time is saved, the problems of read amplification and high visit expense caused when the data pages in the other flash memory page are read are avoided, and the integral performance of a solid state disk is optimized. The invention further discloses application of the optimization processing method. By virtue of the method, the read and write caching algorithms are optimized; by caching the overlong error correcting codes, the cache hit ratio is increased; and by virtue of batch write-back of the overlong error correcting codes of multiple data pages, the updating expense is reduced, furthermore, the integral performance of the system is improved, and the service life of the solid state disk is prolonged.
Owner:HUAZHONG UNIV OF SCI & TECH
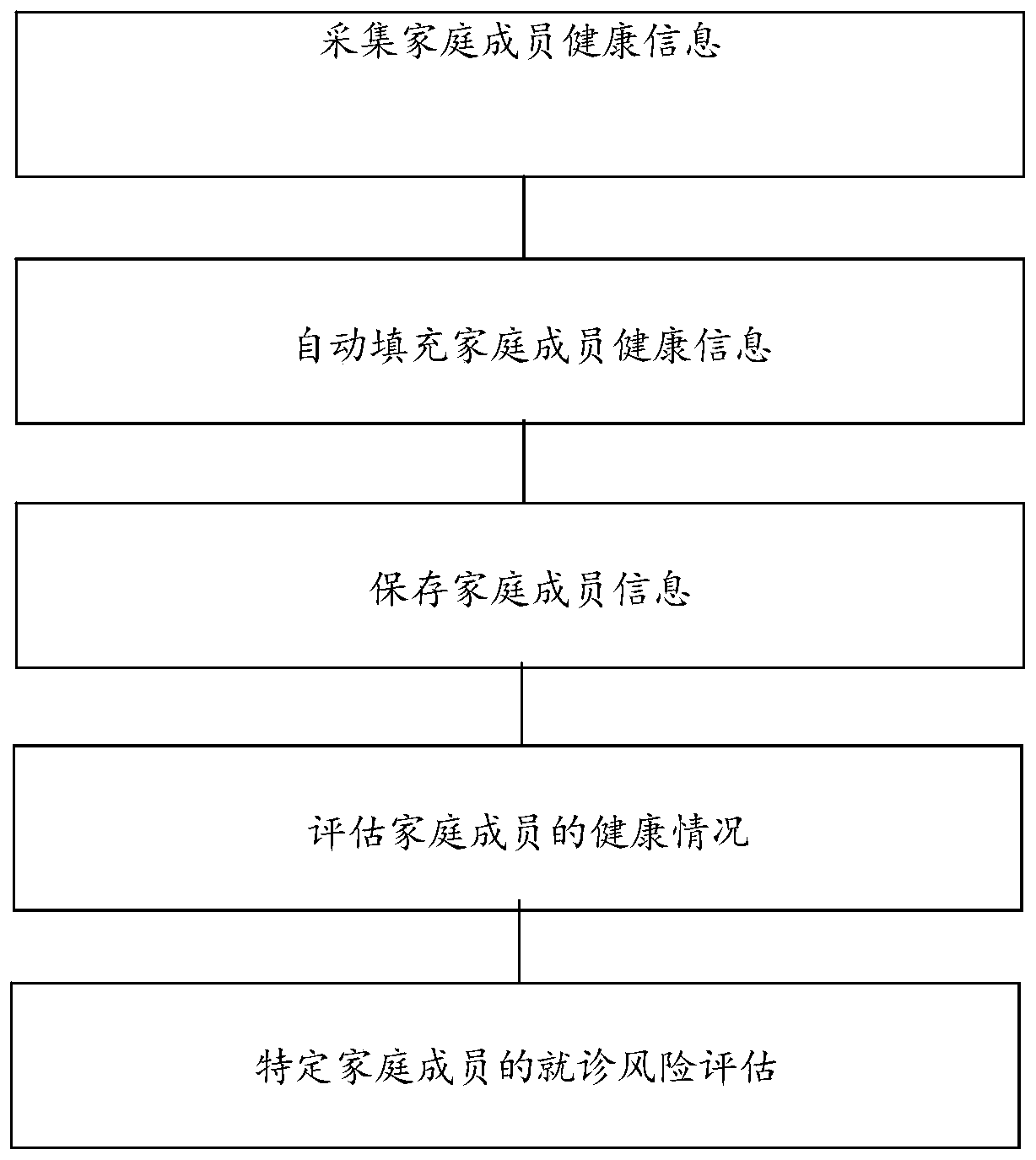
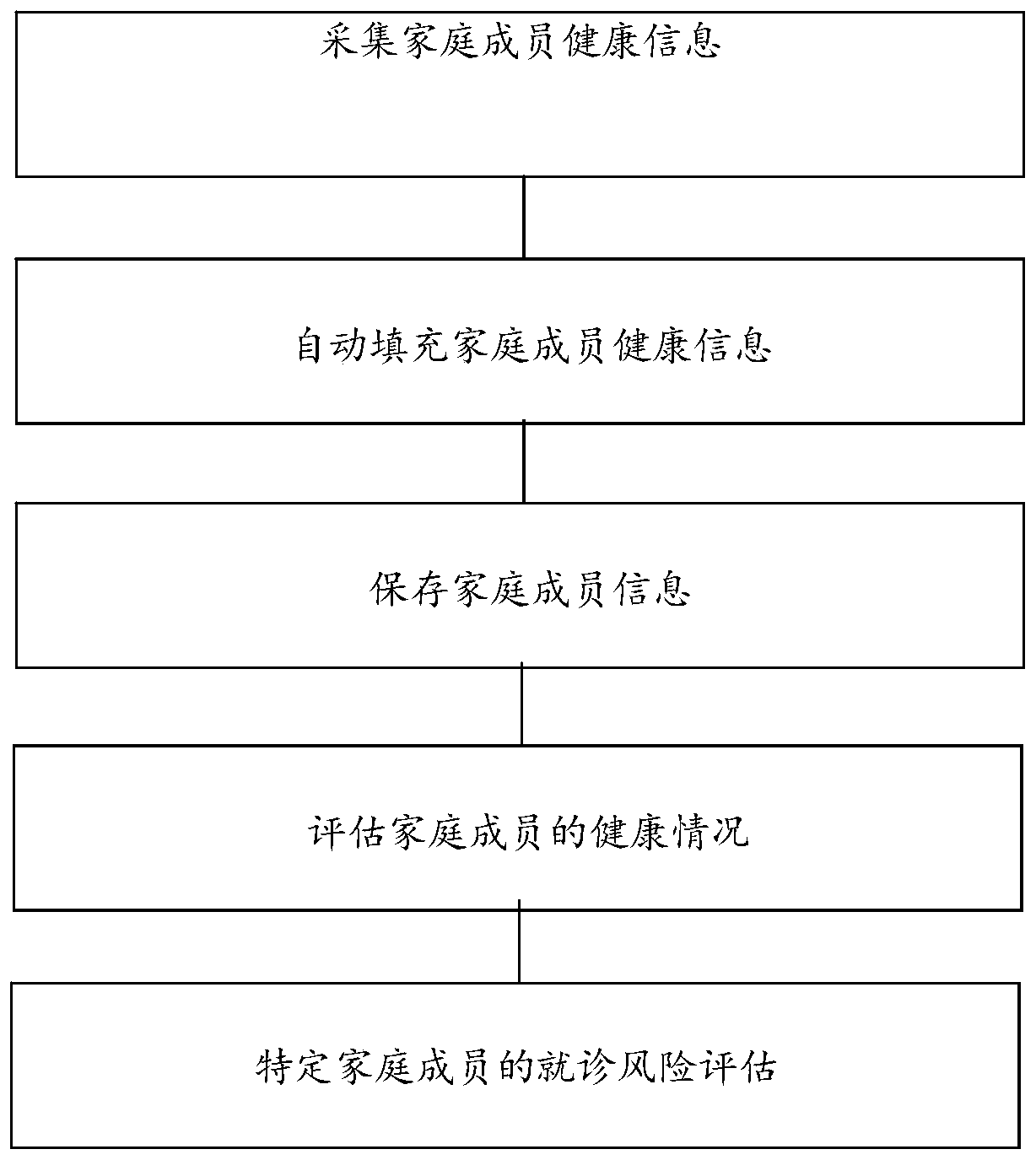
A method for managing family members' health records
ActiveCN109147950BReduce overheadReduce update overheadHealth-index calculationDigital data protectionHealth conditionRisk evaluation
Owner:北京大医未然生物科技有限公司
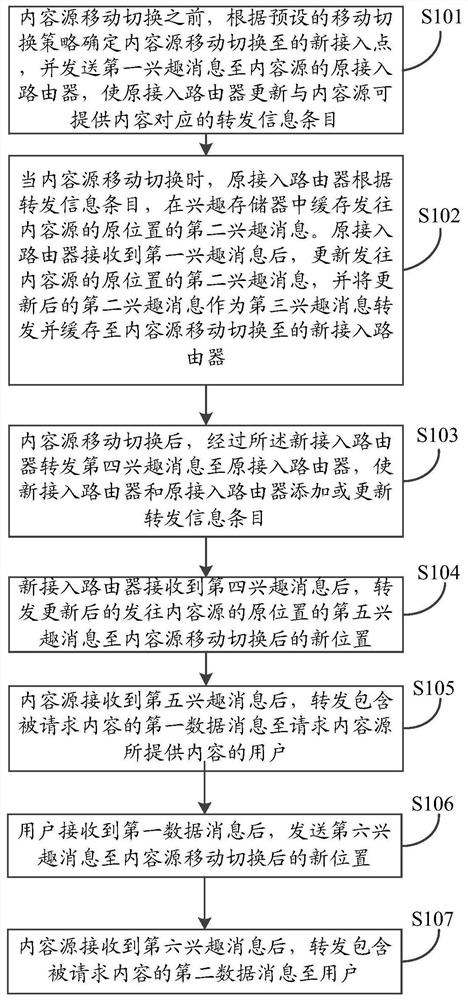
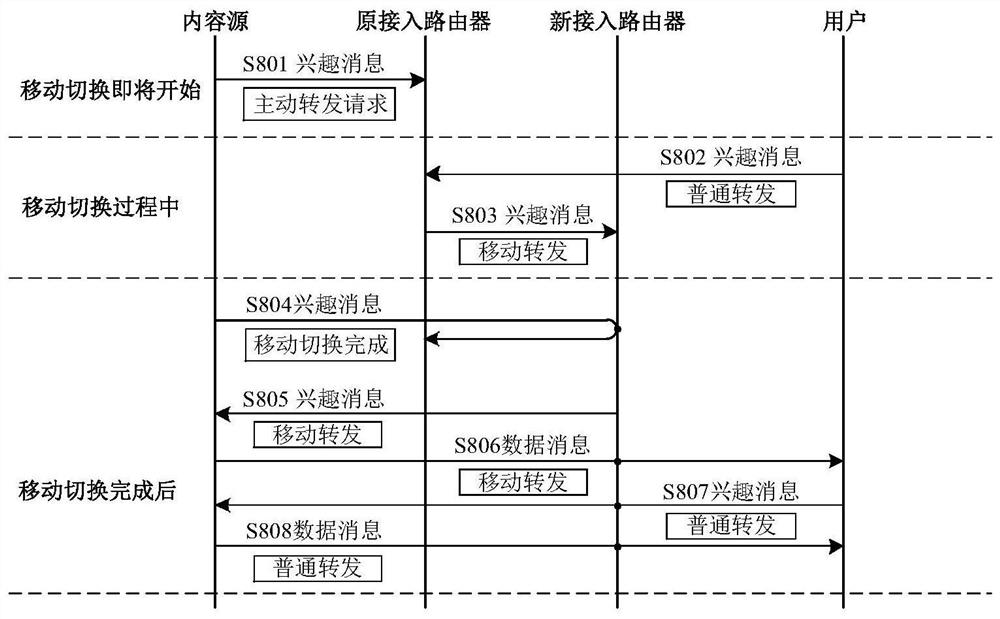
A method for supporting content source mobility based on active forwarding in CCN network
ActiveCN107733946BGuaranteed continuityOvercoming the downside of interruptionData switching networksHandoverReal-time computing
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
Group key managing method based on Chinese remainder theorem
InactiveCN101789945BReduce storageReduce the burden onPublic key for secure communicationComputer hardwareGroup communication systems
Owner:XIDIAN UNIV
Internal memory dotting-based data calling method for acquisition system
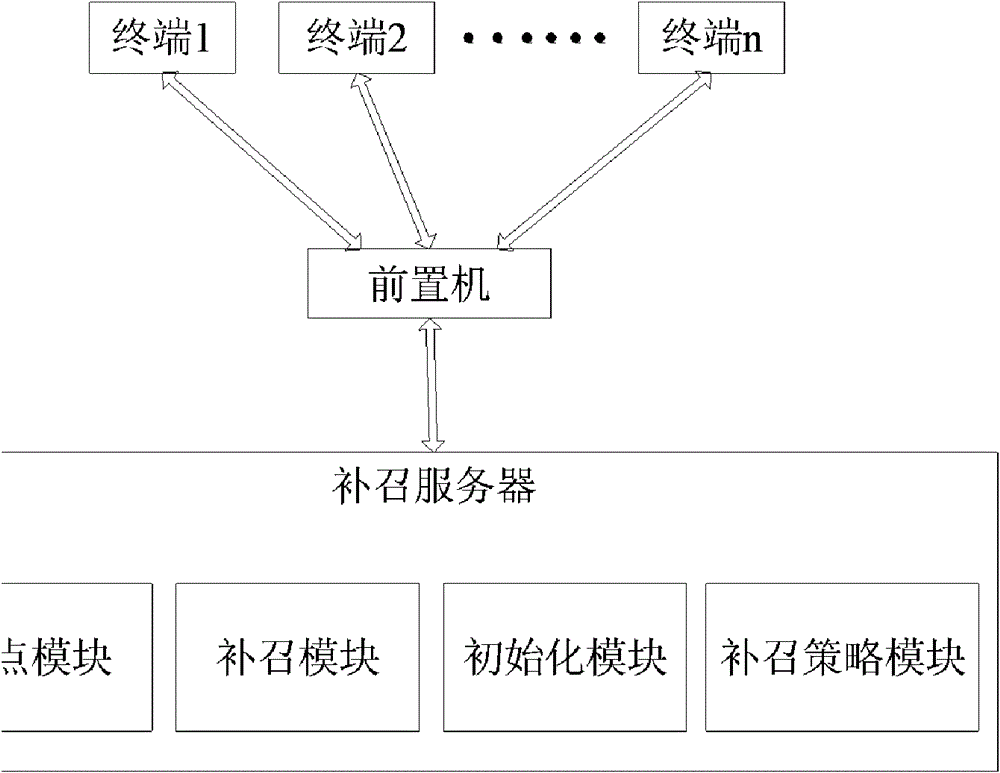
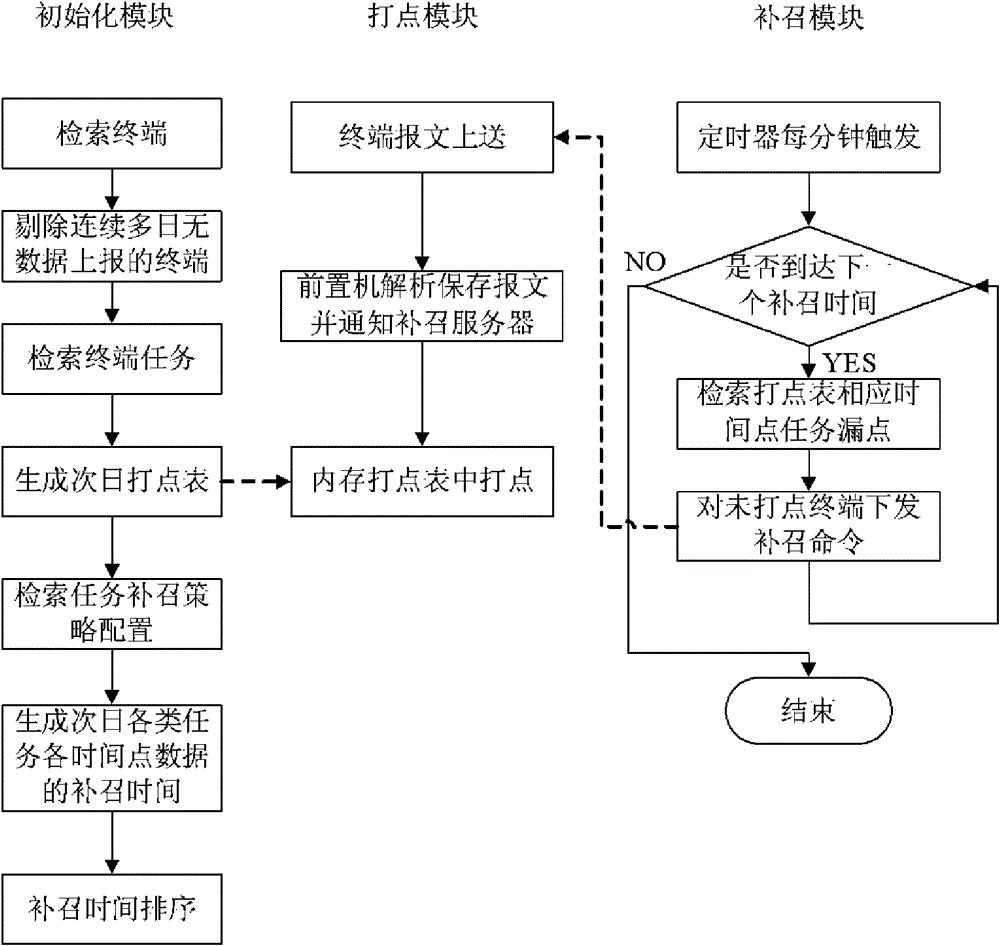
ActiveCN102043867BReduce update overheadHigh speedData acquisition and loggingInternal memoryComputer science
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com