Uni-directional function tree multicast key management method based on cipher sharing
A secret sharing, one-way function technology, applied in key distribution, to achieve the effect of enhancing attack resistance, small update overhead, and reducing the possibility of interception and cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] The present invention is applicable to any application scenario requiring multicast key management.
[0077] In the elaboration of the specific implementation, the symbol s→{m}: x means that the sender s sends the message x to the member m, and the symbol {x} K Indicates that the message x is encrypted with the key K.
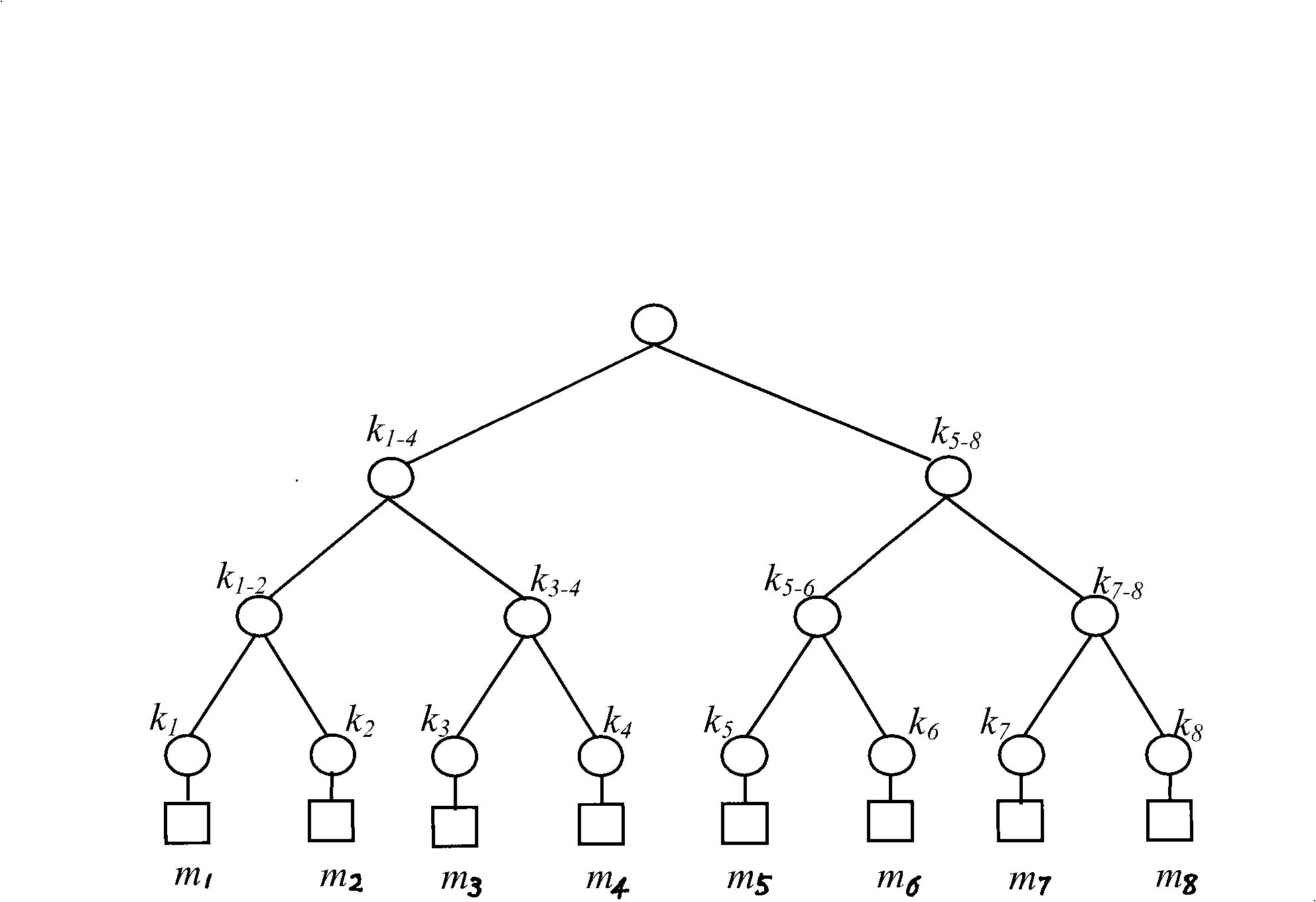
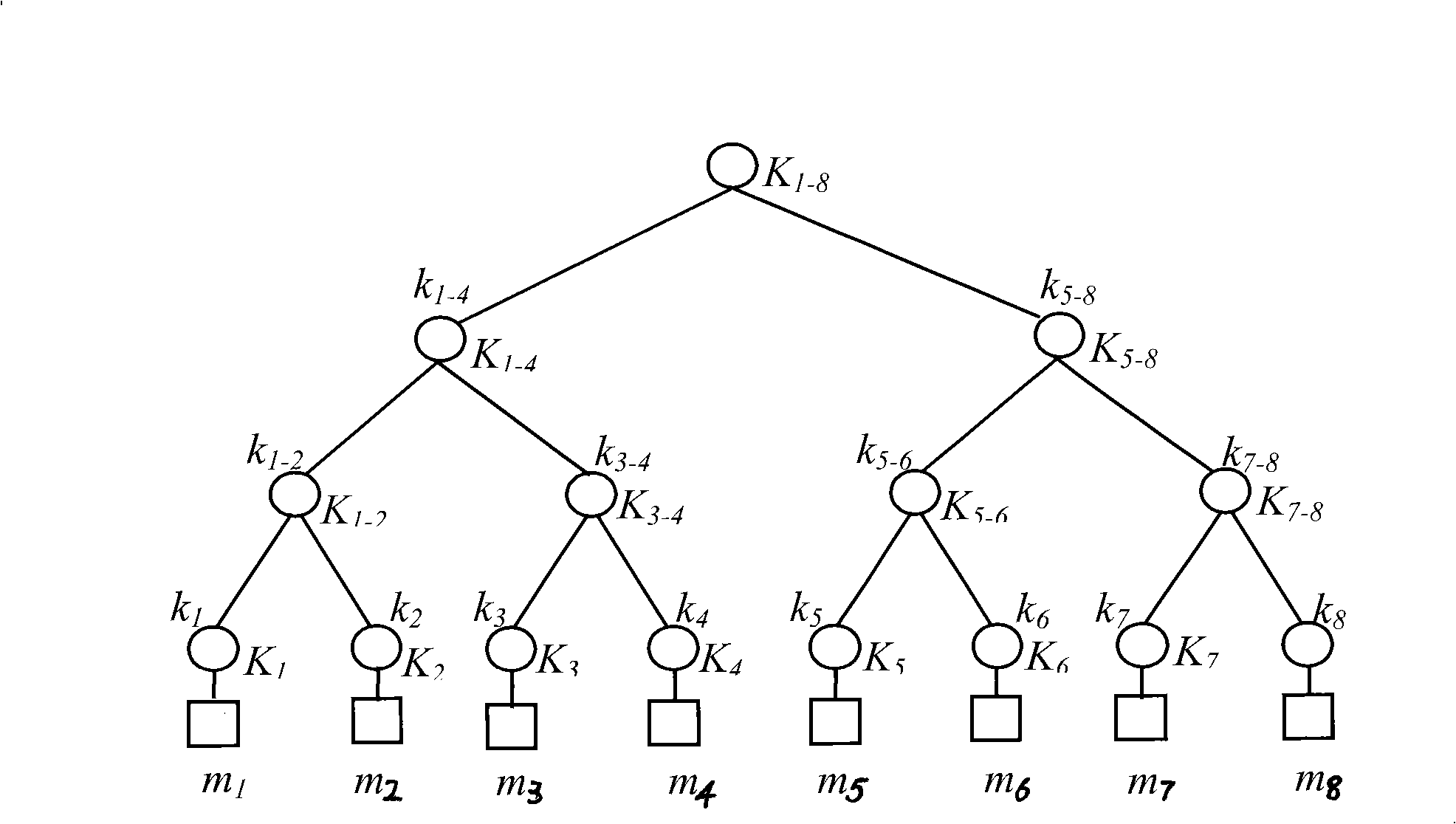
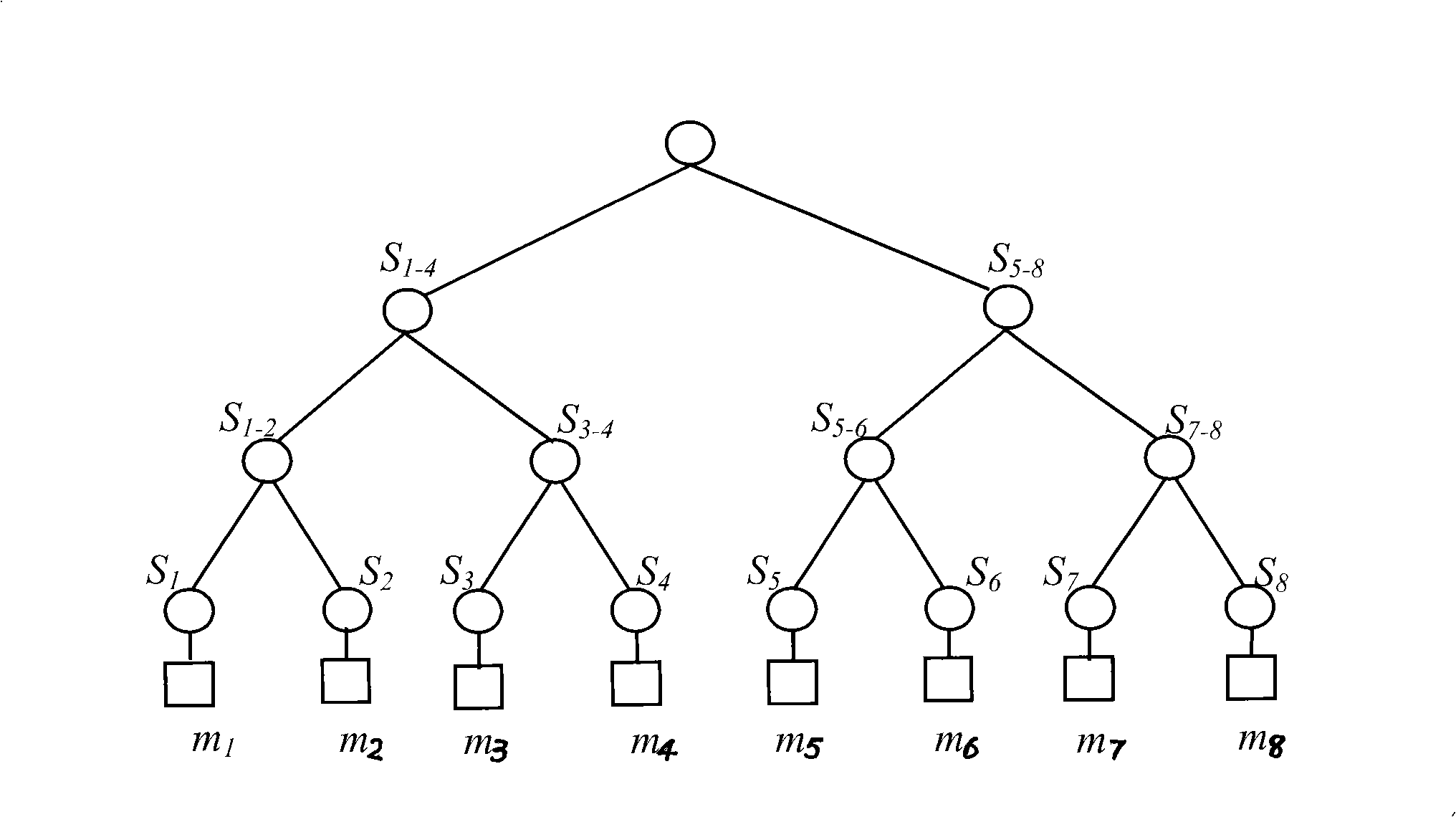
[0078] 1. Generation of key hierarchy tree
[0079] figure 2 and image 3 Respectively represent the key hierarchy tree and the blind key hierarchy tree created by the group controller with 8 group members using the method provided in the present invention. leaf node k 1 , k 2 ..., k 8 Corresponding to the private key K shared by group members and group controllers 1 , K 2 ,...,K 8 ;K i (i=1,2,...,8) is in member m i When joining a group, the private key of the member is generated through a key exchange protocol (such as the Diffie-Hellman key exchange protocol) with the group controller. middle node k 1-2 , k 3-4 , k 5-6 , k 7-8 , k 1-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com