Method and system of double identity authentication based on mobile communication independent channel
A technology of identity authentication and independent channel, which is applied in wireless communication, transmission system, electrical components, etc., can solve the problems of identity authentication method influence and user's inability to monitor, etc., and achieve real-time monitoring of account changes, guarantee of uniqueness, and convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
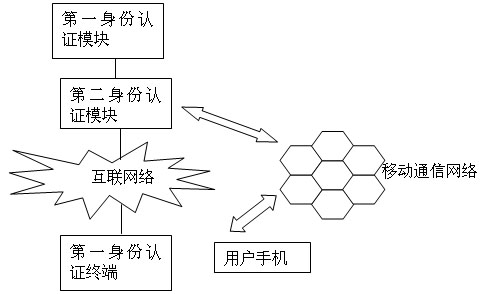
[0050] Such as figure 1 As shown, the system includes a service provider server, a first identity authentication module, a first identity authentication terminal, a second identity authentication module, and a user mobile phone. The first identity authentication terminal is a user transaction terminal; the first identity authentication module is an Internet-based The identity authentication module; the first identity authentication module is connected to the service provider server, the first identity authentication module is connected to the Internet through the second identity authentication module, the first identity authentication terminal is connected to the Internet, and the first identity authentication module is connected to the Internet through the The second identity authentication module performs the first identity authentication with the first identity authentication terminal; the first identity authentication module can be built in the application server in the ser...
Embodiment 2
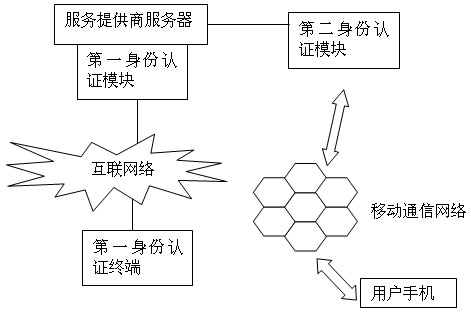
[0060] Such as figure 1 As shown, the system is basically the same as Embodiment 1, including a service provider server, a first identity authentication module, a first identity authentication terminal, a second identity authentication module, and a user mobile phone. The first identity authentication terminal is a user transaction terminal; The identity authentication module is an identity authentication module based on the Internet; the first identity authentication module is connected to the server of the service provider, the first identity authentication module is connected to the Internet, the first identity authentication terminal is connected to the Internet, and the first identity authentication module passes The Internet and the first identity authentication terminal perform identity authentication for the first time; the second identity authentication module is connected with the service provider server, and the second identity authentication module can be connected ...
Embodiment 3
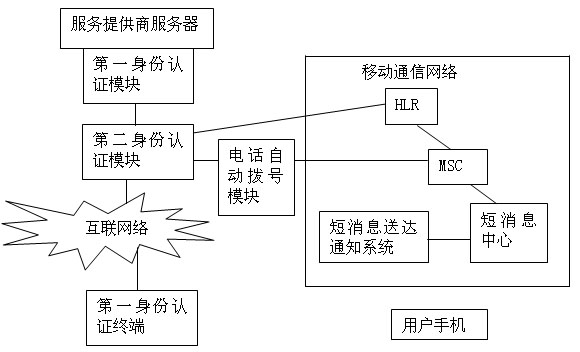
[0069] In addition to IP network fraud similar to number-changing services, there are currently mobile phone automatic reply short message viruses. For example, there are currently viruses that automatically reply to short messages on mobile phones, that is, when a third party (illegal intruder) enters the bank card number and password and requests the server to operate, the second authentication module sends a short message to the user's mobile phone to request a second identity certified. At this time, the third party can make the mobile phone of the card user automatically reply "YES" to the second authentication module, but the user does not know it at all. Especially when the user is driving or did not hear the arrival of the short message, it is even more dangerous. In order to prevent the mobile phone from automatically replying to viruses from disturbing the identity authentication process and improve the security level in the identity authentication process, the seco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com