Realization system and method for safely visiting and storing intranet data by mobile equipment
A mobile device and secure access technology, applied in the field of network security, can solve problems such as attacks, complex encryption algorithms for non-confidential data, leakage of internal network secret data, etc., to resist counterfeit attacks and denial attacks, improve encryption and decryption efficiency, The effect of high authentication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
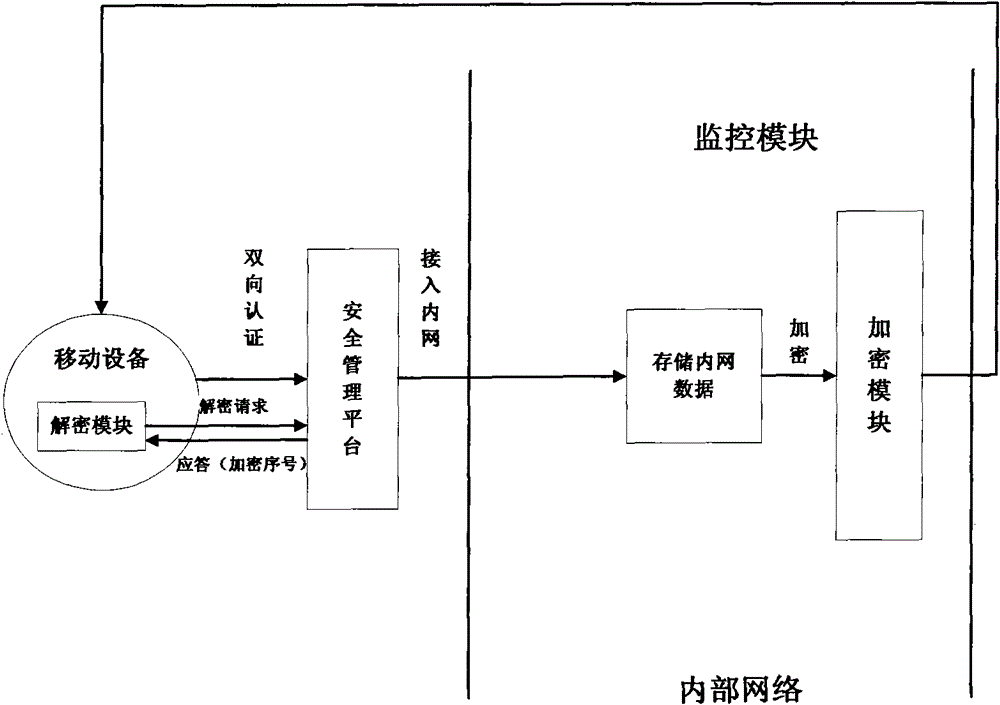
[0047] like figure 1 As shown, a system for implementing secure access and storage of intranet data by mobile devices, including:
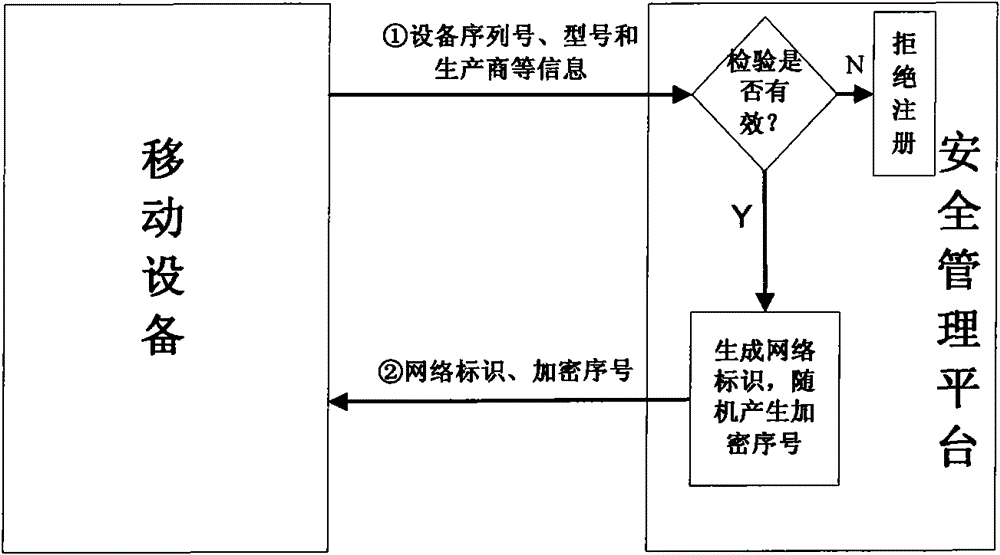
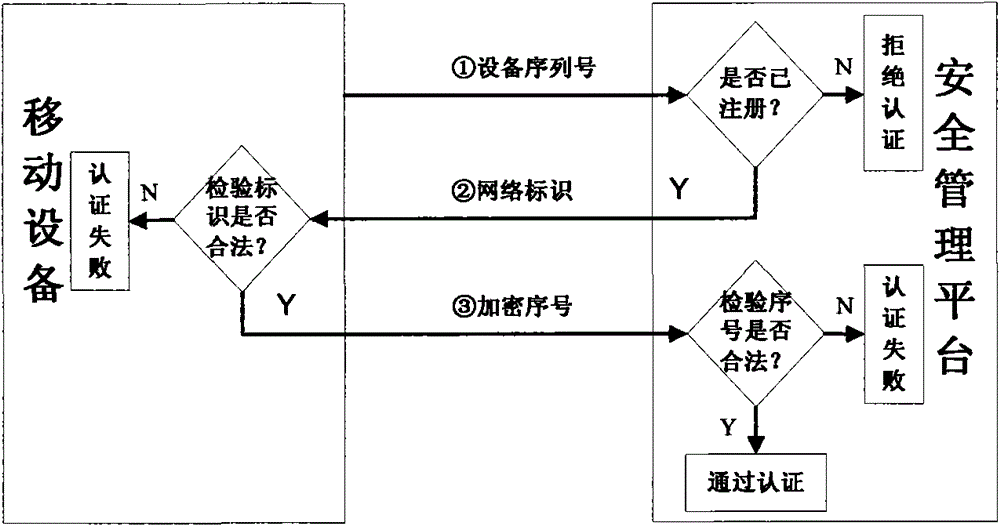
[0048] The security management platform for accessing the intranet is used for registration and two-way authentication of mobile devices to access the intranet, registration of mobile devices allowed to access the intranet, and two-way authentication of registered mobile devices, allowing two-way After the successful authentication, the mobile device is connected to the intranet and monitored by the monitoring module, and the mobile device that has not registered and failed the two-way authentication is rejected to access the intranet, so that if the mobile device has not been authenticated by the platform, it will not be able to communicate with the intranet and computer equipment. exchange of information;
[0049] The monitoring module, which runs on the intranet, is used to monitor mobile devices accessing the intranet, save the monitoring rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com