Identity authentication system and method
An identity authentication and subsystem technology, which is applied in the field of identity or credential devices, can solve the problems of easy leak of mobile phone numbers and complicated operation of identity authentication methods, and achieve the effects of simple operation, easy leak, and complicated operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Preferred embodiments of the present invention will now be described in detail with reference to the accompanying drawings. Wherever possible, the same parts have been designated by the same or like reference numerals throughout the drawings.
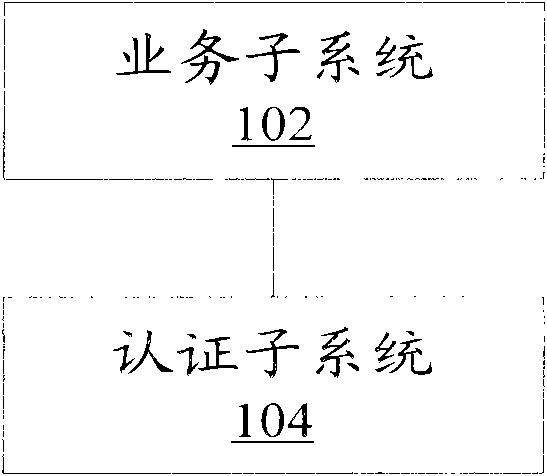
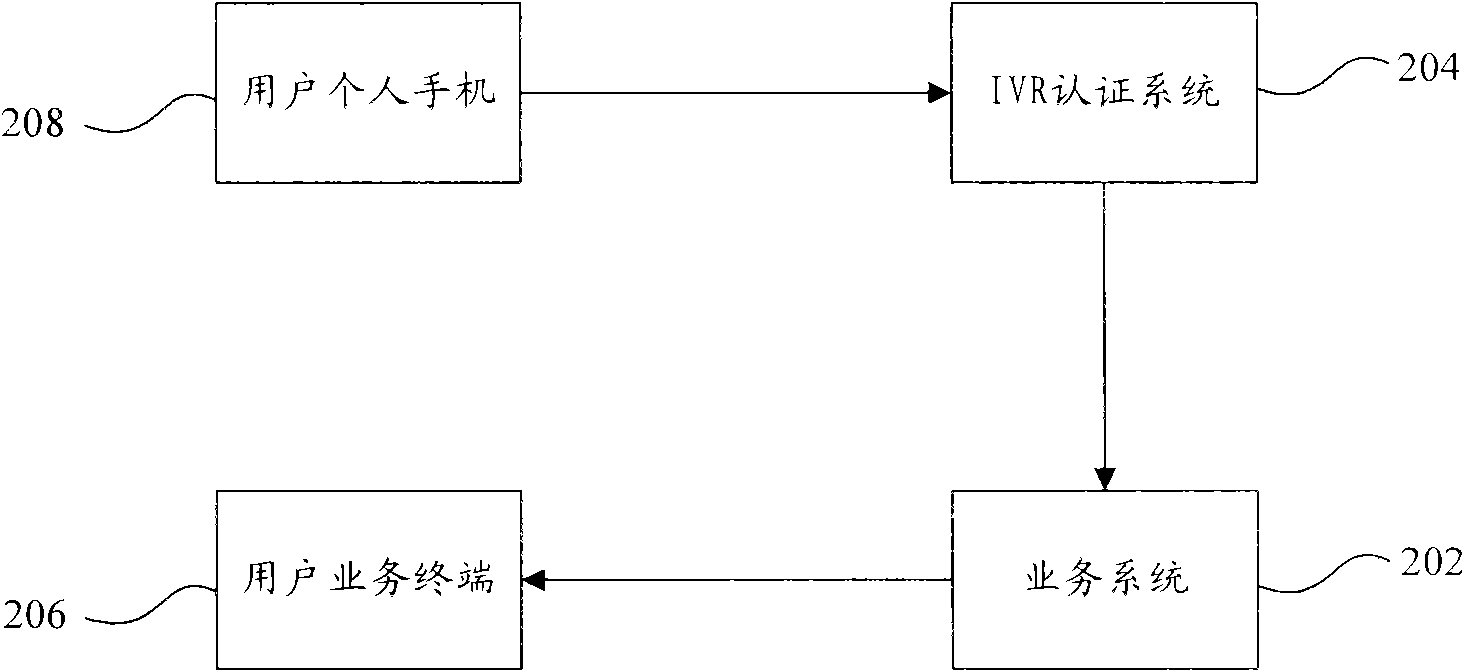
[0016] figure 1 A schematic diagram of an identity authentication system according to an embodiment of the present invention is shown. Such as figure 1 As shown, the identity authentication system includes:
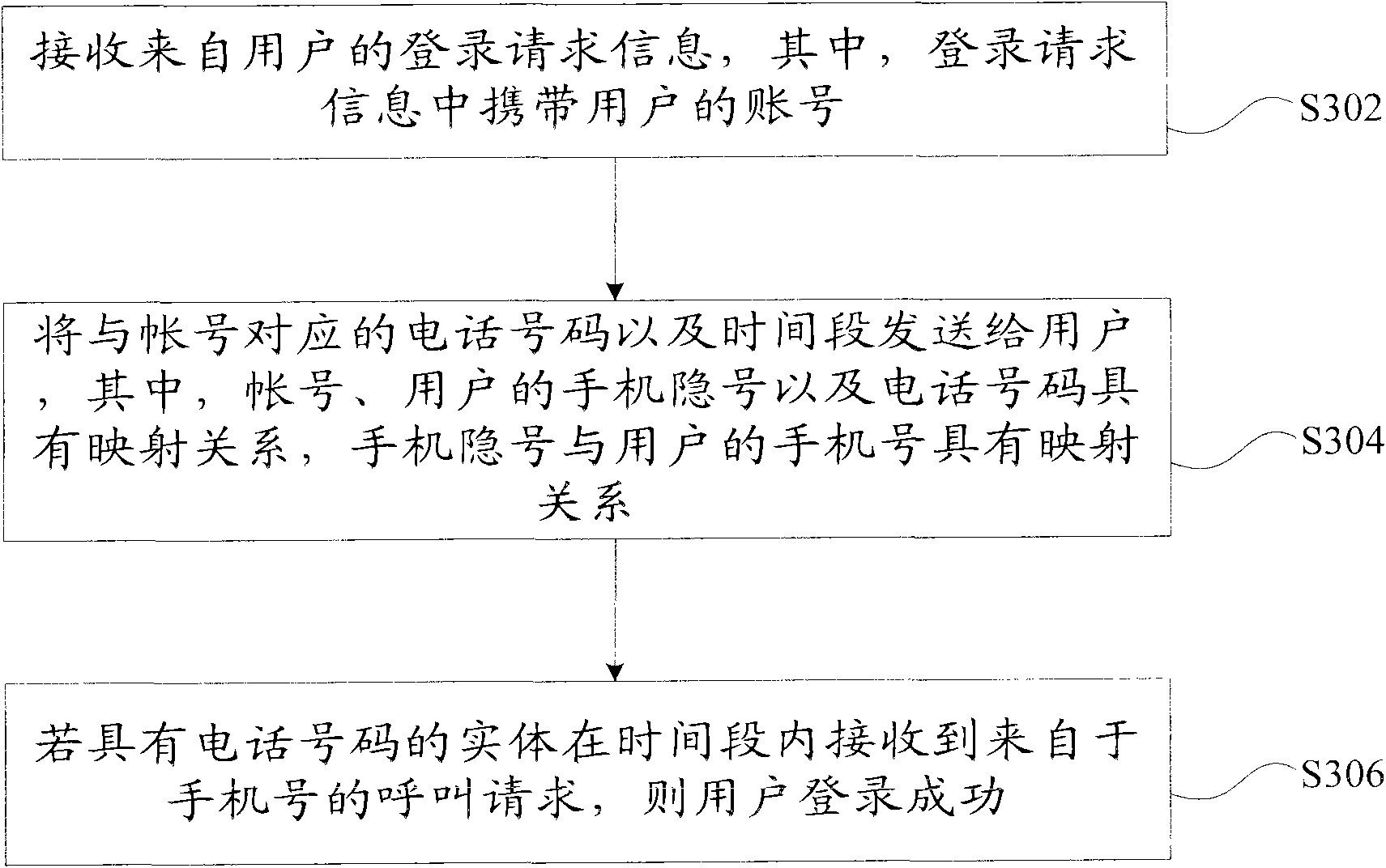
[0017] The service subsystem 102 is used to receive the login request information from the user, and send the phone number and time period corresponding to the user's account to the user, wherein the login request information carries the user's account number, account number, and the user's mobile phone number And the phone number has a mapping relationship, and the mobile phone number has a mapping relationship with the user's mobile phone number;
[0018] The authentication subsystem 104 is configured to determine that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com