Securely providing a control word from a smartcard to a conditional access module
A technology for accessing modules and control words, applied in safety communication devices, electrical components, digital transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention provides a state-based key exchange in which control words transmitted between a smart card and a CAM in a receiver are encrypted using a diversified key. CAMs are usually integrated in receivers such as set-top boxes, but may also be implemented in other types of receivers such as televisions, personal video recorders, mobile phones, smartphones or computer devices. Diversification is based on user interaction with the set-top box, which can be detected in the CAM, smart card, or both.
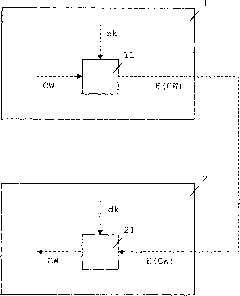
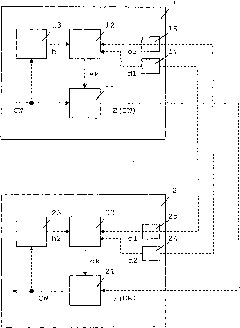
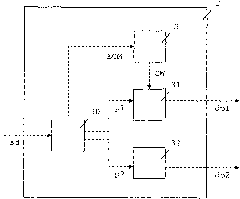
[0030] The basic concept of state-based key exchange is in figure 1 shown in , and based on the symmetric encryption of the control word CW. The smart card 1 receives one or more control words CW in a manner known per se, for example by transmission to the smart card's ECM. The smart card 1 encrypts the control word in the encryptor 11 using the encryption key ek and the encrypted control word E(CW) is transmitted to the CAM 2 . The CAM 2 decrypts the encrypted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com