Method for identifying access point identity, workstation roaming method and related equipment
An access point and workstation technology, applied in the field of communication, can solve the problem of occupying MAC address resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
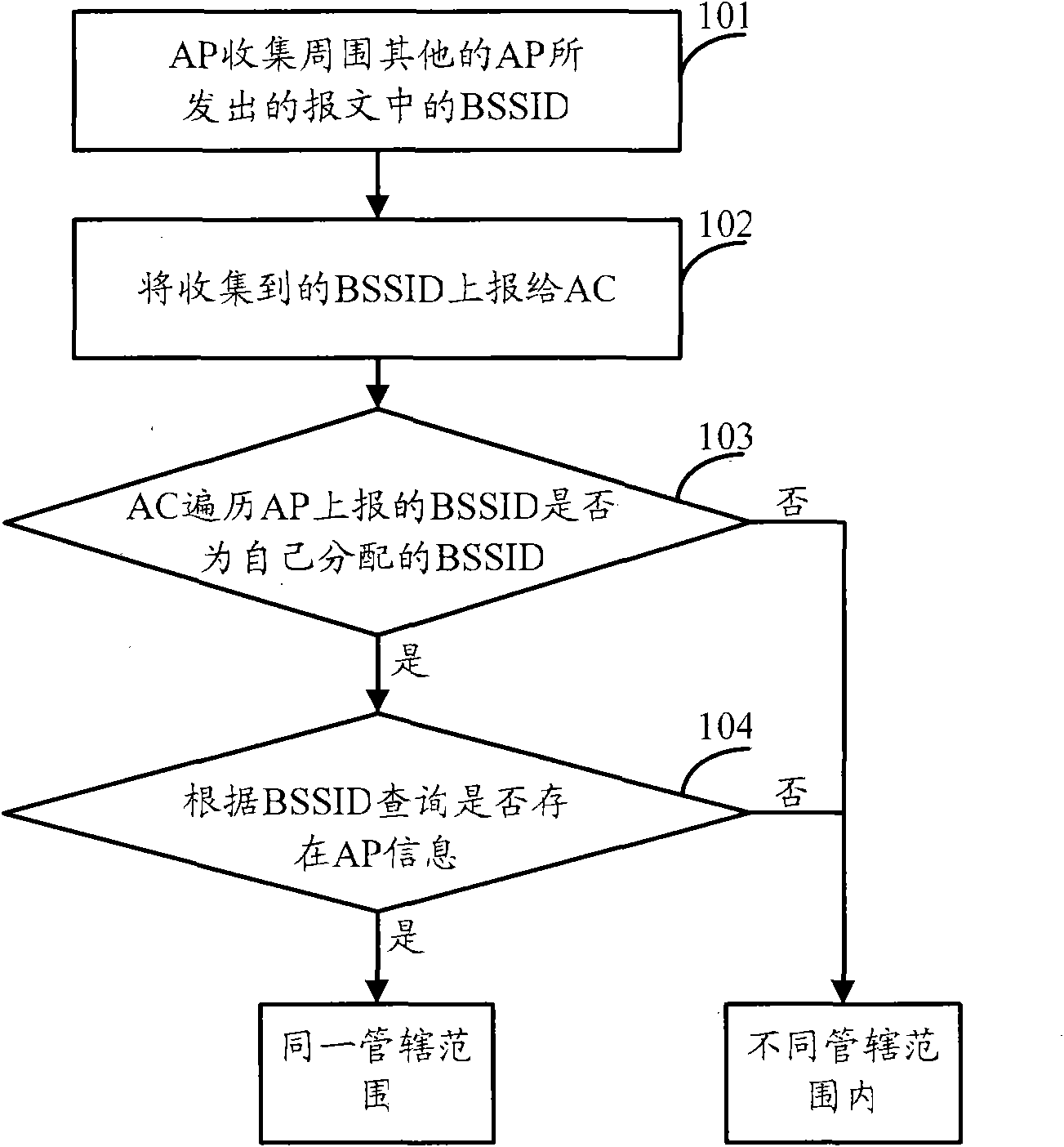
[0057] see figure 2 , figure 2 It is a flowchart of a method for identifying an access point identity provided in an embodiment of the present invention. Such as figure 2 As shown, the method may include:
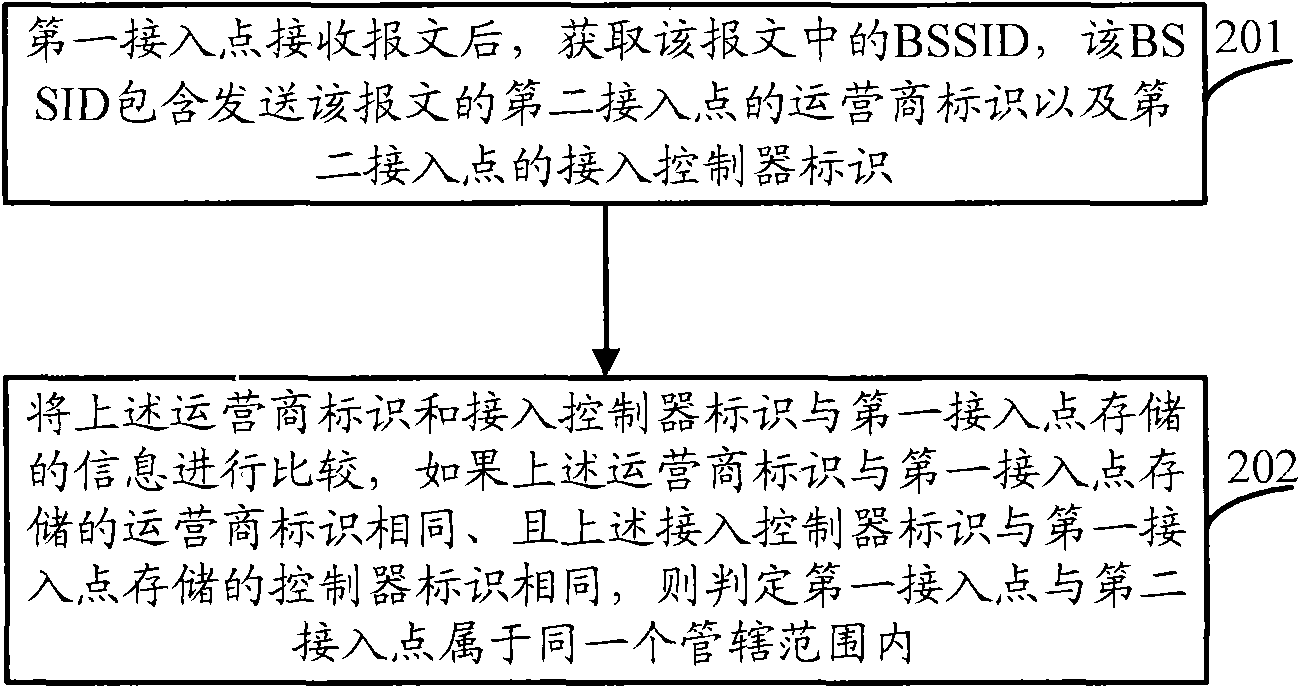
[0058] Step 201: After receiving the message, the first access point obtains the BSSID in the message, and the BSSID includes the operator identifier of the second access point that sent the message and the access controller identifier of the second access point ;
[0059] Step 202: Compare the above-mentioned operator ID and access controller ID with the information stored in the first access point, if the above-mentioned operator ID is the same as the operator ID stored in the first access point, and the above-mentioned access controller If the identifier is the same as the controller identifier stored in the first access point, it is determined that the first access point and the second access point belong to the same jurisdiction.
[0060] Preferably, the BSSID ...
Embodiment 2
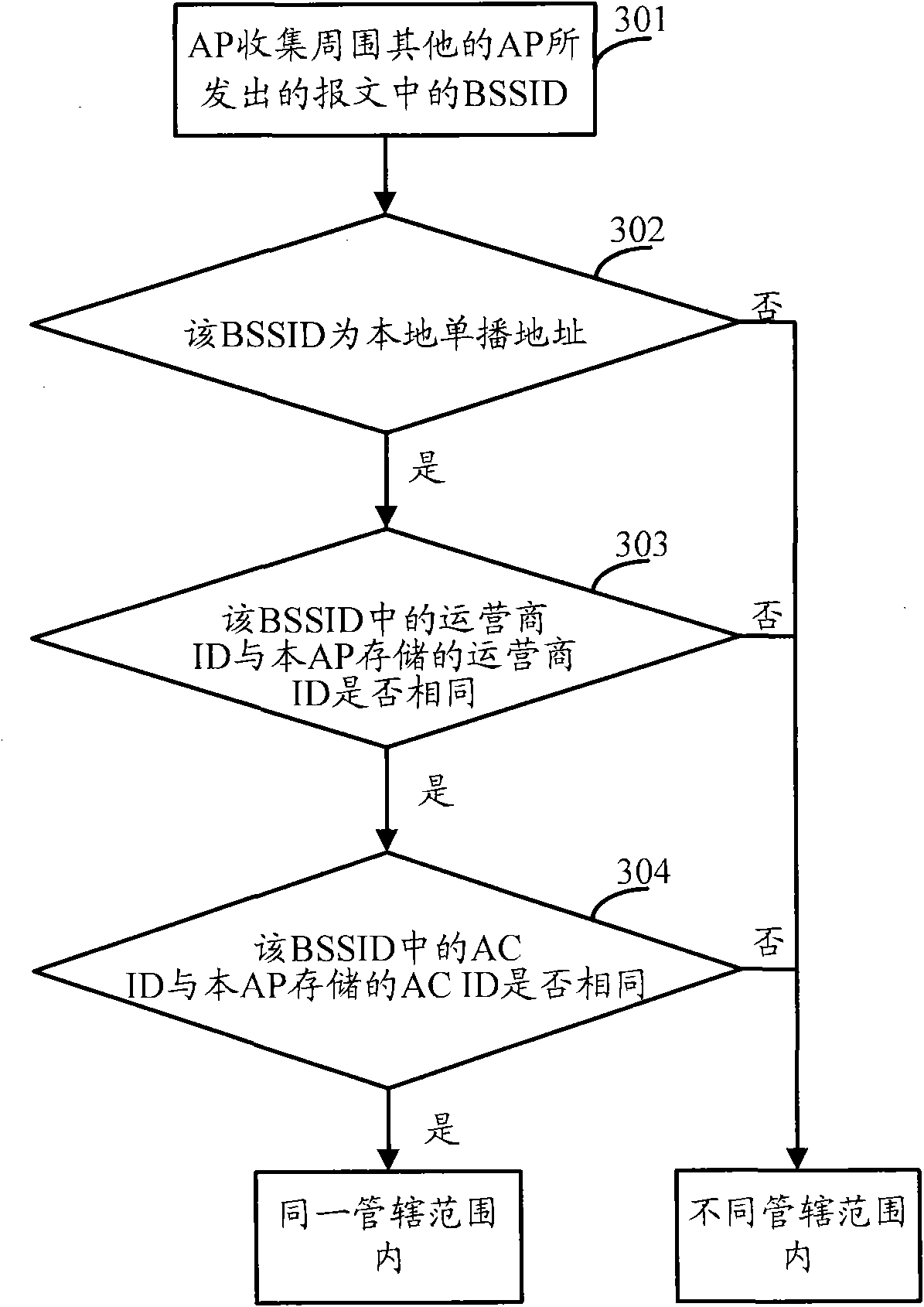
[0063] see image 3 , image 3 It is a flowchart of a method for identifying an access point identity provided in an embodiment of the present invention. This embodiment takes identifying the identity of a local access point as an example, where all local access points have a local unicast address. Such as image 3 As shown, the method may include:
[0064] Step 301, the AP collects the BSSID in the message sent by the surrounding access points, and the BSSID includes at least the operator identification and the access controller identification;
[0065] In the BSS, each AP can receive the messages sent by other APs around it, and obtain the carried BSSID from the messages, which is common knowledge of those skilled in the art. The specific process of BSSID in the message sent by the AP will not be introduced.
[0066] Among them, the operator ID is represented by the operator ID, and the value range of the operator ID is 0 to 4K-1, which occupies 12 bits; the access cont...
Embodiment 3
[0074] see Figure 4a , Figure 4a It is a flowchart of another method for identifying an access point identity provided in an embodiment of the present invention. Such as Figure 4a As shown, the method may include:
[0075] Step 401, the AP receives and stores the operator ID, AC ID, AP ID, and radio frequency identification (Radio ID) of the AP issued by the AC;
[0076] Such as Figure 4b As shown, in the BSS, one AC can manage multiple APs; generally, based on network capacity and compatibility considerations, an AP may have multiple radios; Each radio provides multiple VAP services.
[0077] Step 402, the AP receives the VAP identifier issued by the AC, if the value of the VAP identifier is 0, it is stored directly; if the value of the VAP identifier is not 0, the VAP identifier is decremented by 1 and stored;
[0078] The BSSID customized by this AP is shown in Table 2, and the customized BSSID actually identifies the wireless network structure.
[0079] Table 2 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com