User identifying method and device for internet connection sharing
A user identification and legal technology, applied in the Internet field, can solve the problems of inability to accurately identify shared Internet users, poor identification accuracy and reliability, and achieve the effects of low cost, convenient network deployment, and high identification reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0076]Embodiment 1 of the present invention provides a method for identifying shared Internet users, the process of which is as follows Figure 9 As shown, the execution steps are as follows:
[0077] Step S101: the terminal sends a message to the network side device.
[0078] Generally, the terminal will send the message to the access switch directly connected to itself, and then the access switch will send the message to the aggregation switch.
[0079] Step S102: The network side device obtains the message transmitted by the terminal.
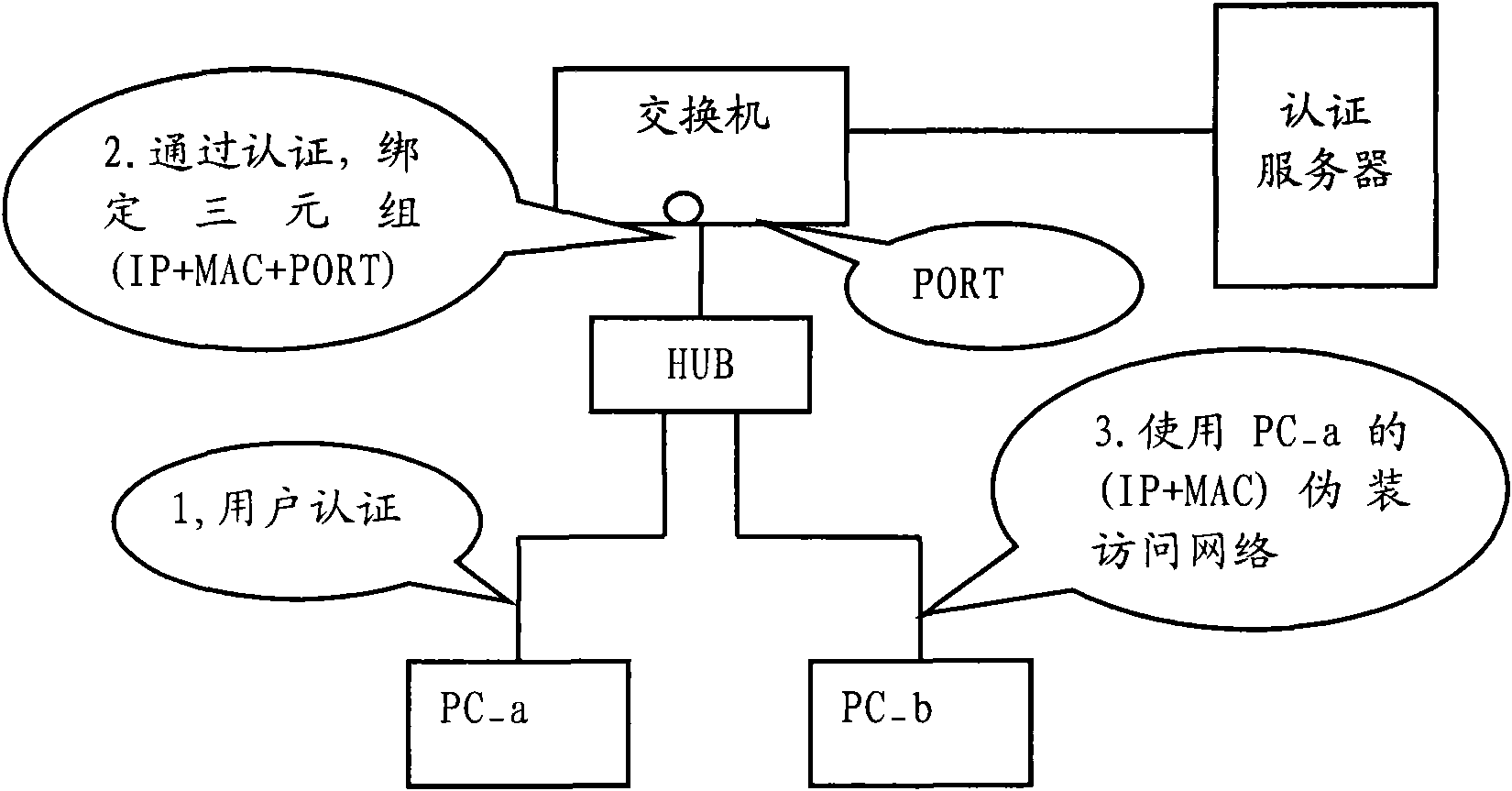
[0080] In this application, generally, the converging switch obtains the message transmitted by the terminal and analyzes it. Determine the TCP first session information corresponding to the terminal sending the message according to the address information, port information carried in the message, and the time when the message is received.
[0081] The foregoing first session information may specifically include: a source IP address, a de...
Embodiment 2
[0098] Embodiment 2 of the present invention provides a Figure 8 The system shown realizes the method for identifying shared Internet users, and its process is as follows Figure 10 As shown, the execution steps are as follows:
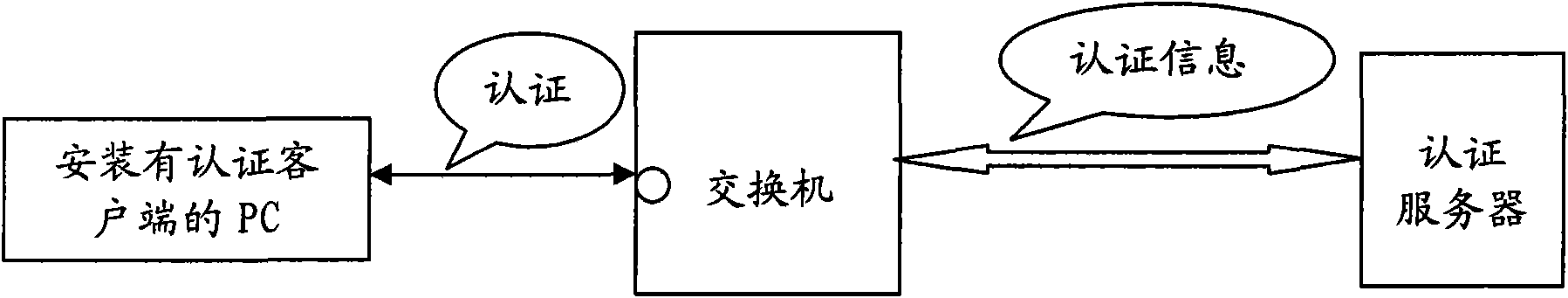
[0099] Step S201: the terminal 22 sends an authentication request to the authentication server 31.
[0100] The terminal 22 may be a personal computer (PC), or may be a mobile terminal or the like. The legitimate user sends authentication information such as an authentication request to the authentication server 31 through the authentication client installed on the terminal 22 .
[0101] Step S202: the authentication server 31 authenticates the terminal 22 sending the request.
[0102] After passing the authentication, the authentication server will notify the detection server that the terminal 22 has passed the authentication. After passing the authentication, the message sent by the terminal 22 can be smoothly transmitted in the network.
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com