Software system module independent authorization control method and device
A technology of software system and authorization control, which is applied in the direction of computer security devices, instruments, program/content distribution protection, etc. It can solve the problems that value-added services cannot be independently authorized, and the date of use license cannot be controlled, so as to increase income and ensure version security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
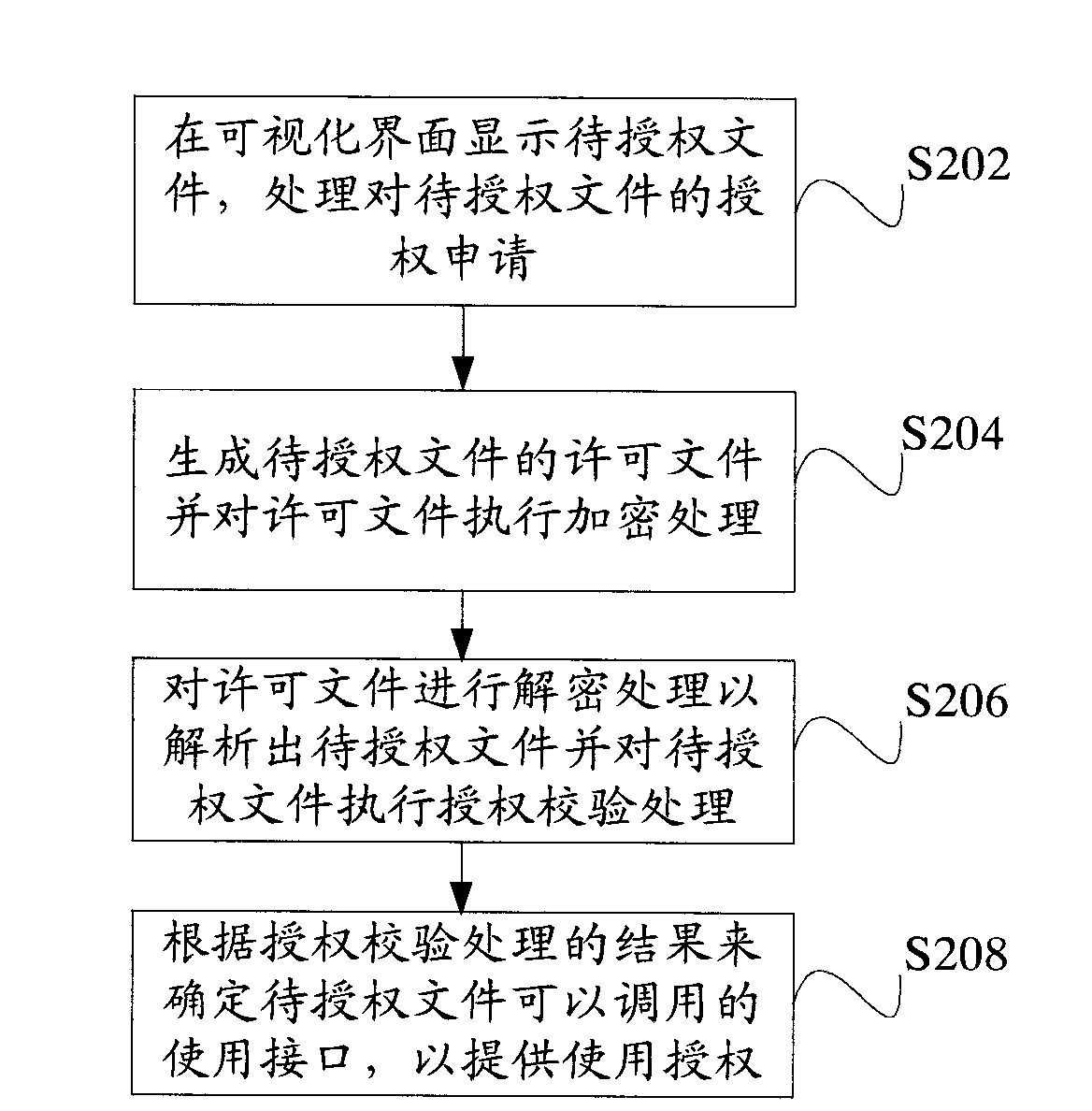
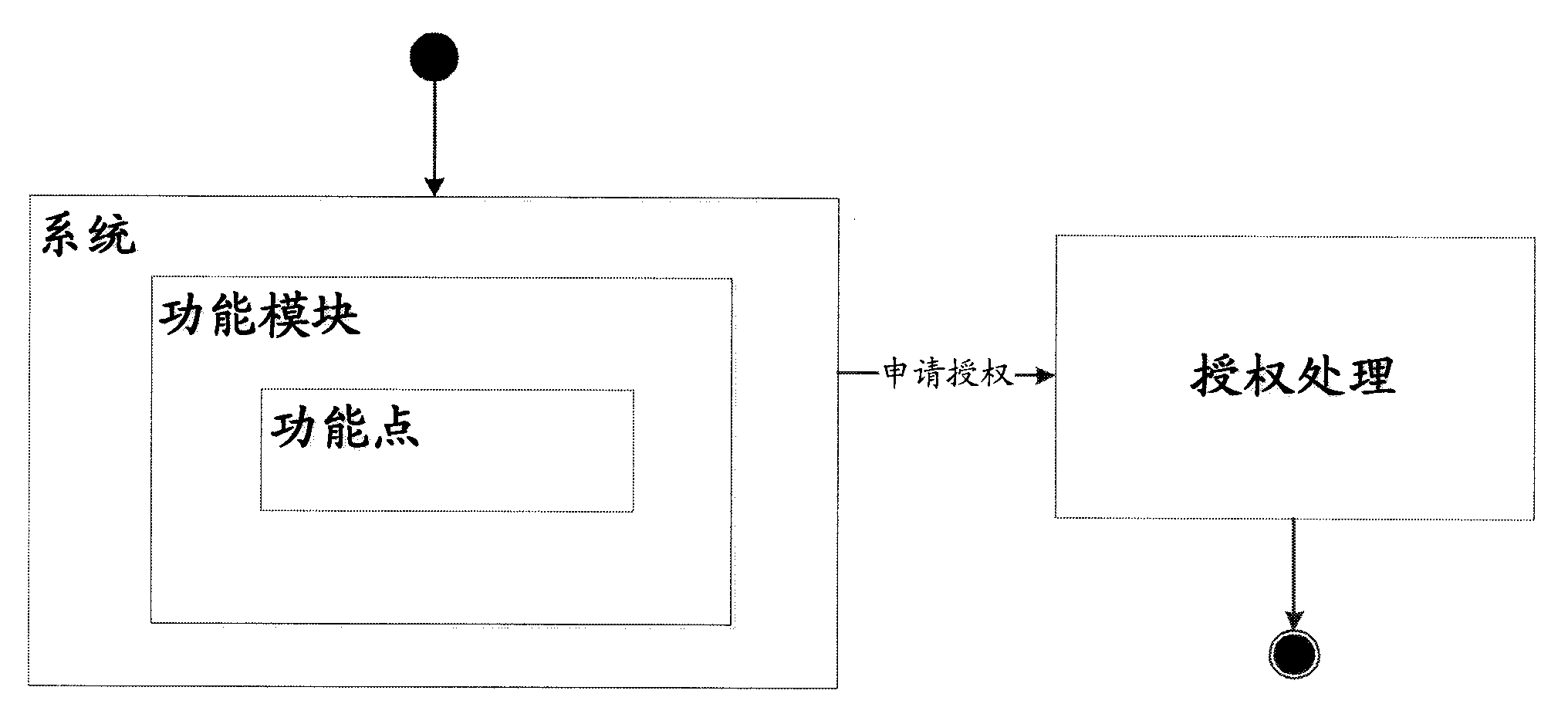
[0032] It should be understood that the present invention can be applied to the authorization of the entire software system, a certain function module of the software, and a certain function point, and provides a flexible, safe and reliable authorization control mechanism.
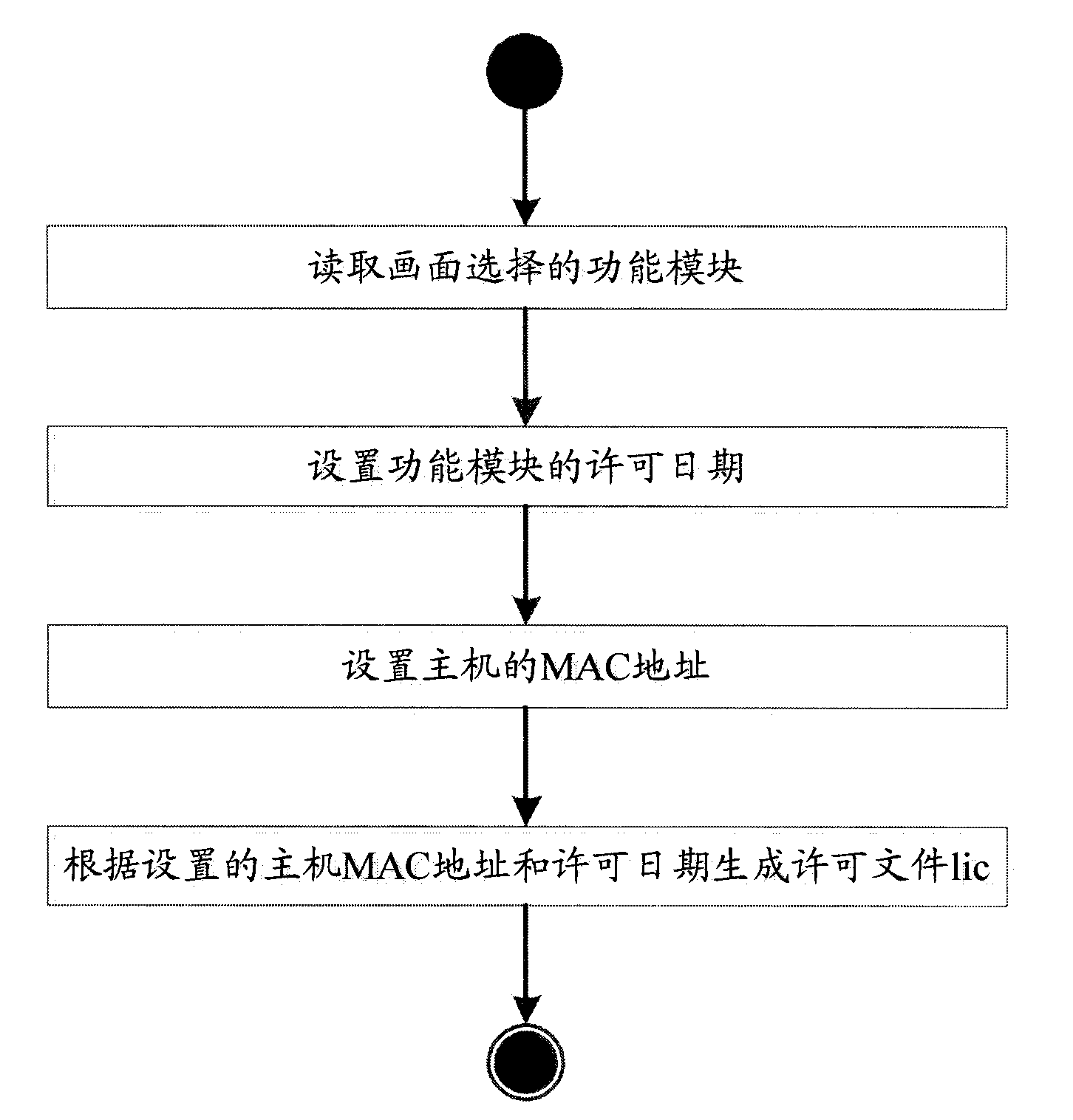
[0033] Table 1 is a schematic diagram of the individual authorization form of the functional modules of the present invention. As shown in Table 1, it is possible to separately control the usage rights of the XXX module and YYY module of the user application, and provide different license usage time for the XXX module and YYY module. figure 1 It is only for illustration and not for limiting the present invention, and corresponding changes can be made in both form and details in specific applications.
[0034] module name
Use start time
Use deadline
XXX module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com