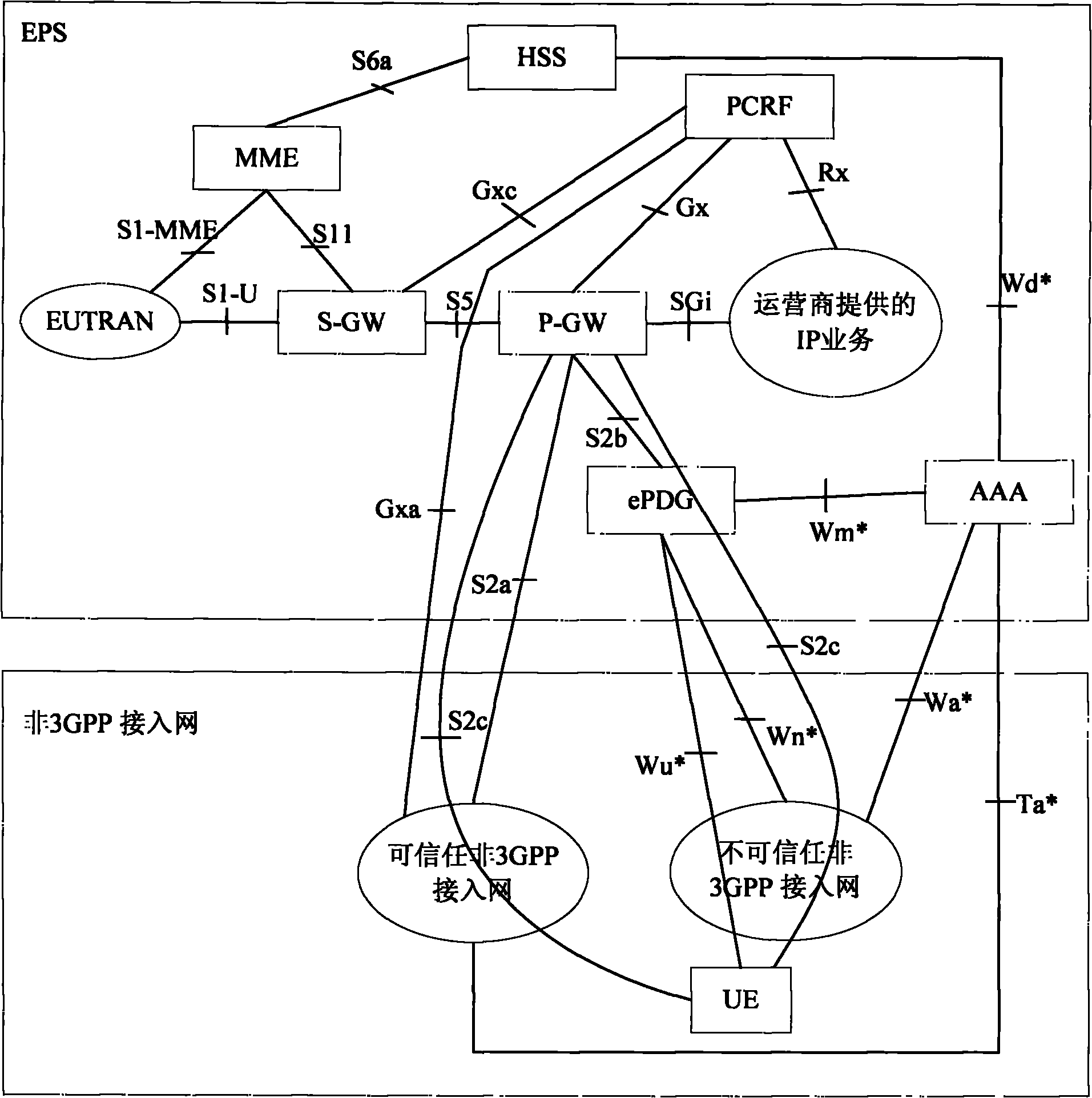
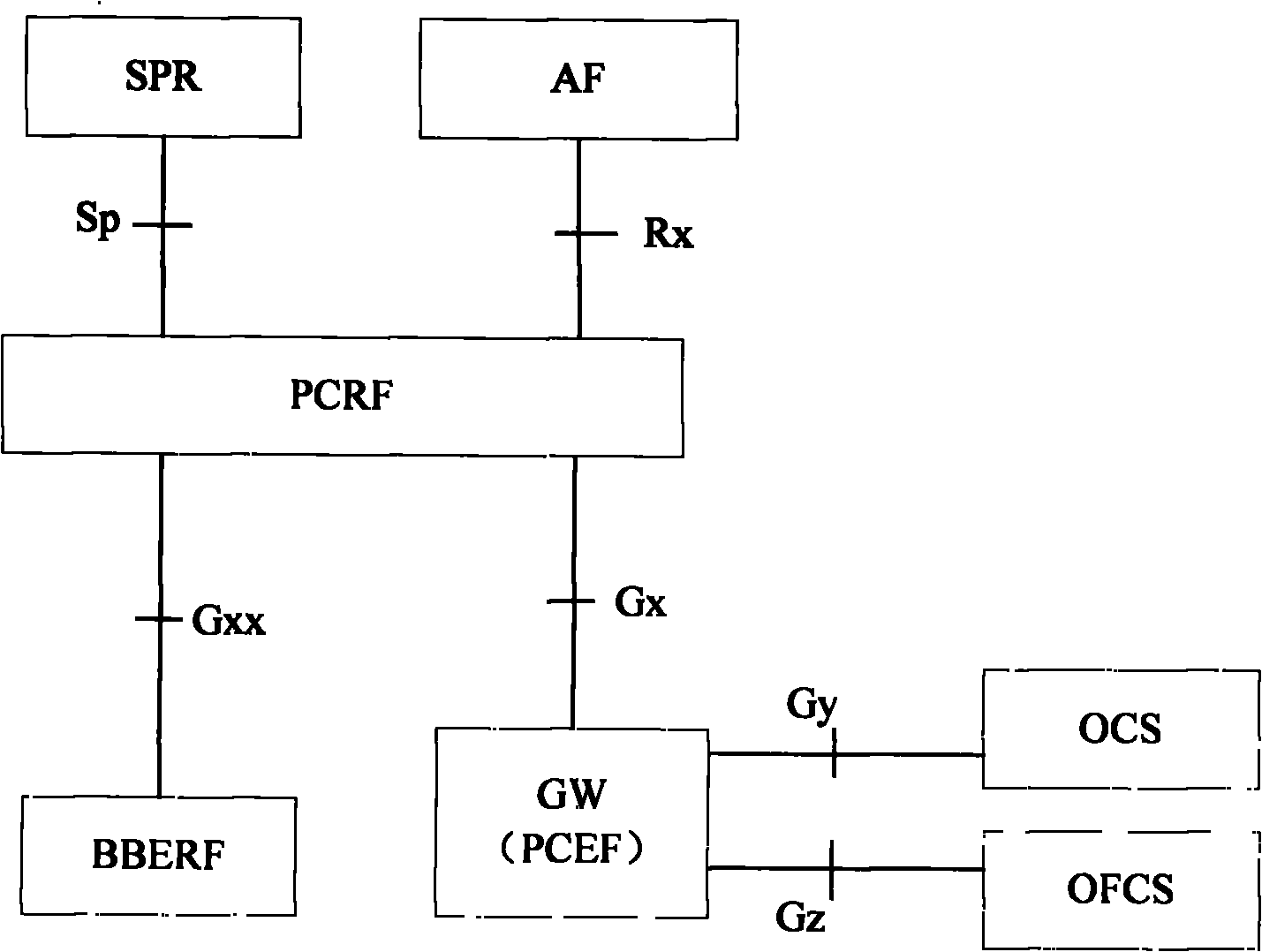
Method and system for realizing limited policy charging control
Use PCRF to determine whether the visited network supports PCC, and send the limited policy charging control deployment identifier to AF, which solves the complexity problem of AF in determining whether the visited network supports policy charging control, and achieves more accurate policy charging control and resources. save.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
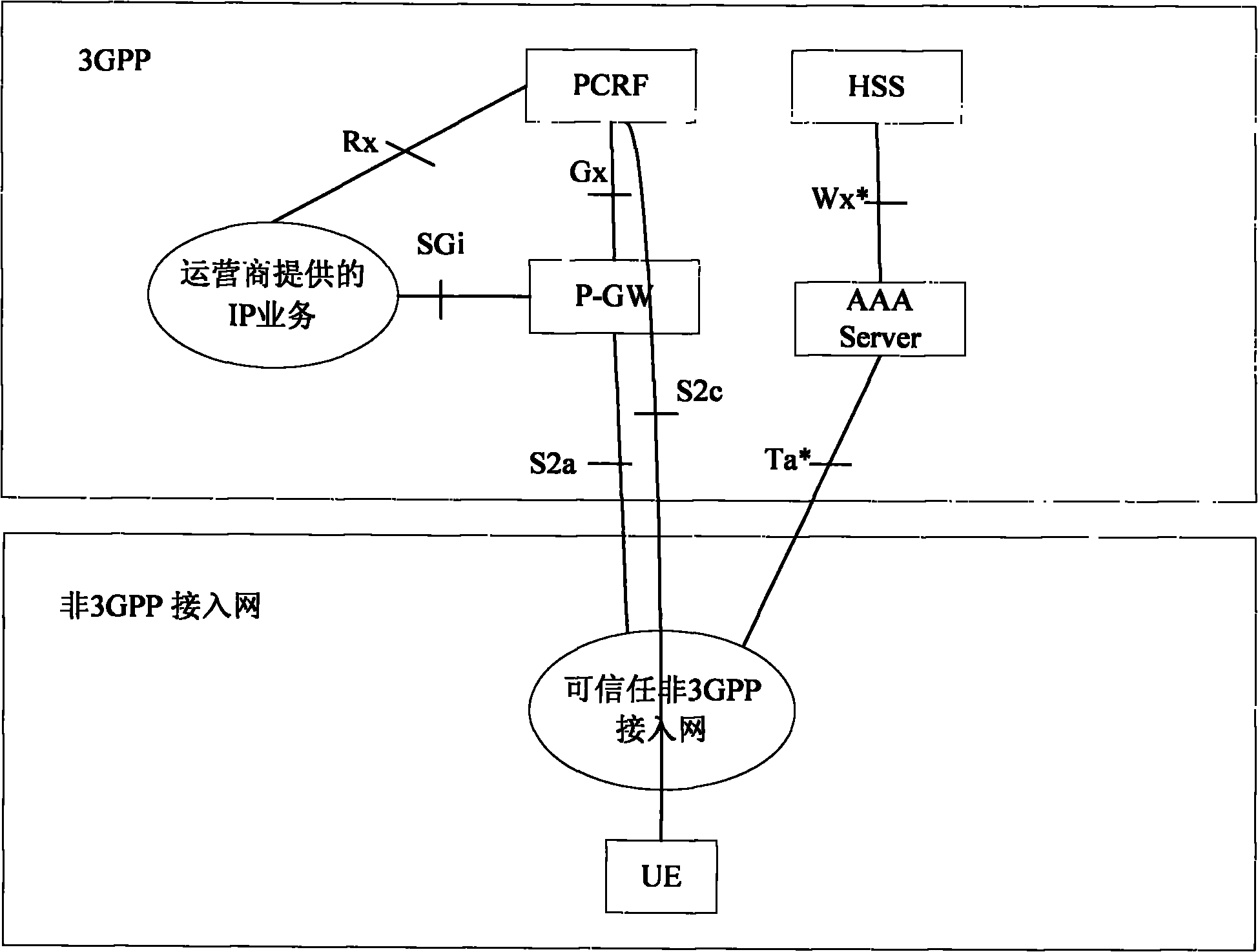
[0048] image 3 Shown is a schematic diagram of the application scenario of the first embodiment of the present invention; in this application scenario, the UE accesses the EPS through the trusted non-3GPP access network and adopts the PMIPv6 protocol; the 3GPP network supports dynamic PCC, and the trusted non-3GPP access network The network does not support dynamic PCC, and it can be trusted that the non-3GPP network and the 3GPP network belong to different operators.
[0049] The method flow chart of the first embodiment of the present invention is as follows Figure 4 As shown, the specific steps are as follows:
[0050] 401: The UE accesses a trusted non-3GPP access network.
[0051] 402: After the UE accesses the trusted non-3GPP access network, it requests the HSS / AAA for EPS access authentication; after receiving the EPS access authentication request, the HSS / AAA authenticates the requesting UE; HSS / AAA completes After the UE is authenticated, the P-GW selection info...
no. 2 example
[0068] In this embodiment, the UE is image 3 In the application scenario shown, through the trusted non-3GPP access network and the DSMIPv6 protocol to access EPS, the 3GPP network supports dynamic PCC, but the trusted non-3GPP access network does not support dynamic PCC (the trusted non-3GPP access network and 3GPP networks belong to different operators). The method flowchart of the second embodiment of the present invention is as follows Figure 5 As shown, the specific steps are as follows:
[0069] 501: The UE accesses a trusted non-3GPP access network, the HSS / AAA and the UE perform mutual authentication, and the HSS / AAA authorizes the UE.
[0070] 502: After the authentication is successful, the UE negotiates with the trusted non-3GPP access gateway and decides to use the DSMIPv6 protocol for access, the UE performs a layer 3 attachment process, and the trusted non-3GPP access gateway allocates a CoA (care-of address) for the UE.
[0071] 503: The UE performs DNS (Do...
no. 3 example
[0084] Figure 6 Shown is a schematic diagram of the application scenario of the third embodiment of the present invention; when the UE is in the roaming scenario of the home route, it accesses the EPS through the E-UTRAN of the visited location, and the PMIPv6 protocol is used between the S-GW and the P-GW, where The home network of the UE supports dynamic PCC, but the visited network does not support dynamic PCC.
[0085] The method flowchart of the third embodiment of the present invention is as follows Figure 7 As shown, the specific steps are as follows:
[0086] 701: The UE sends an attach request message to the MME; the HSS authenticates and authorizes the UE. After the authentication is successful, the MME initiates a location update process, and the HSS sends the subscription data of the UE to the MME. During the authentication process, the HSS sends the P-GW selection information subscribed by the UE to the MME, and the MME selects the P-GW according to the P-GW s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com