Safe consultation method and device based on emergency call
An emergency call and safety technology, which is applied in security devices, emergency connection processing, emergency/dangerous communication services, etc., can solve the problems affecting the success rate of emergency call connection, etc. Simple and practical effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
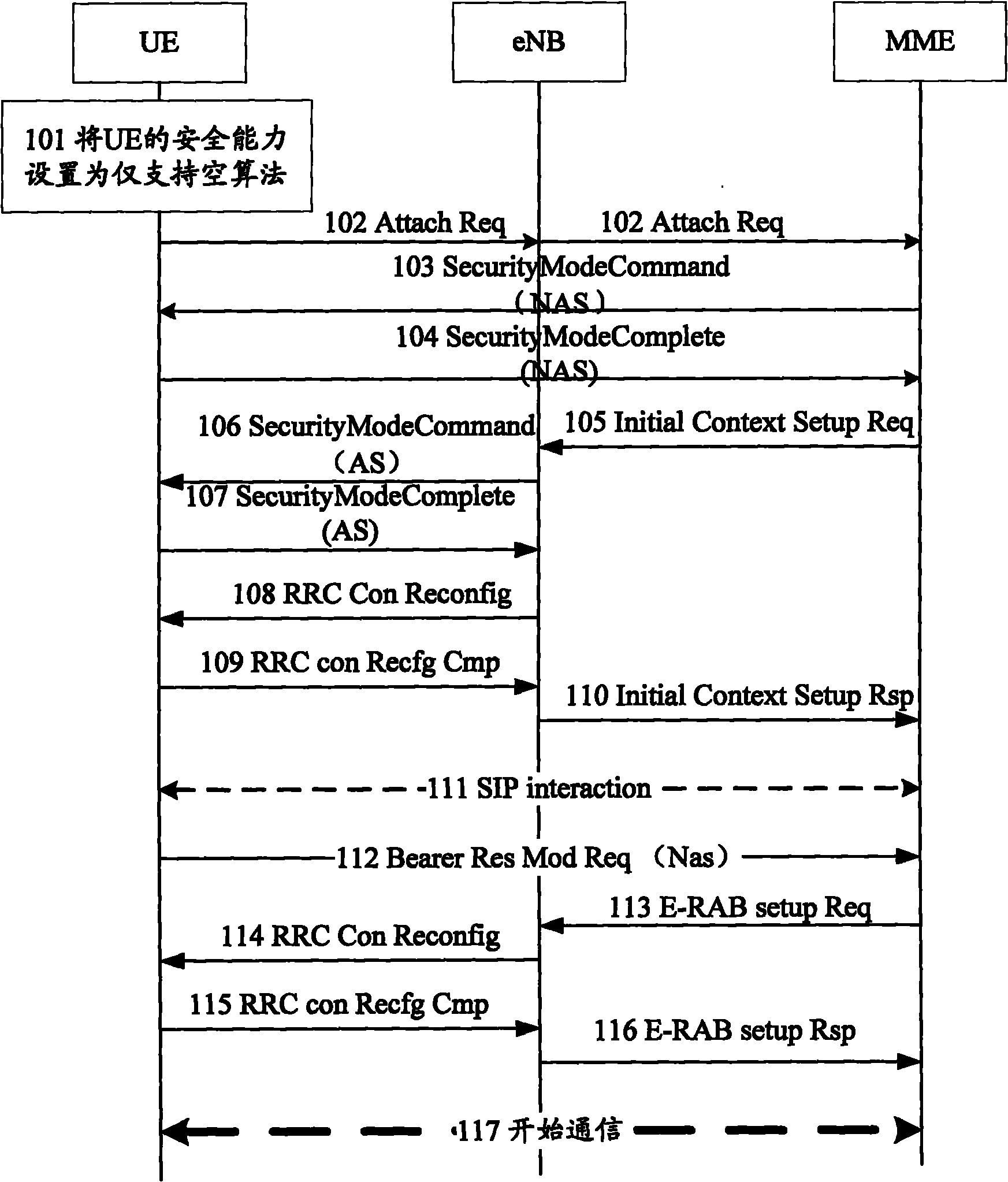
[0060] figure 1 It is a flow chart of Embodiment 1 of the emergency call-based security negotiation method of the present invention, as shown in figure 1 As shown in this example, the emergency call-based security negotiation method includes the following steps:
[0061] 101: When the UE determines that the call request initiated by the current user is an emergency call request, set the security capability of the UE to only support the null algorithm.
[0062] In step 101 of the present invention, once the UE determines that the call requested by the user is an emergency call, the security capability is set to only support the null algorithm, no matter whether the UE is in a restricted service state or not.
[0063] 102: UE sends an Attach Request (Attach Req) message to the network side, and the Evolved Packet System Attach Type (EPS Attach Type) item in the Attach Req message is set to Evolved Packet System Emergency Attach (EPS Emergency Attach), where the user terminal T...
Embodiment 2
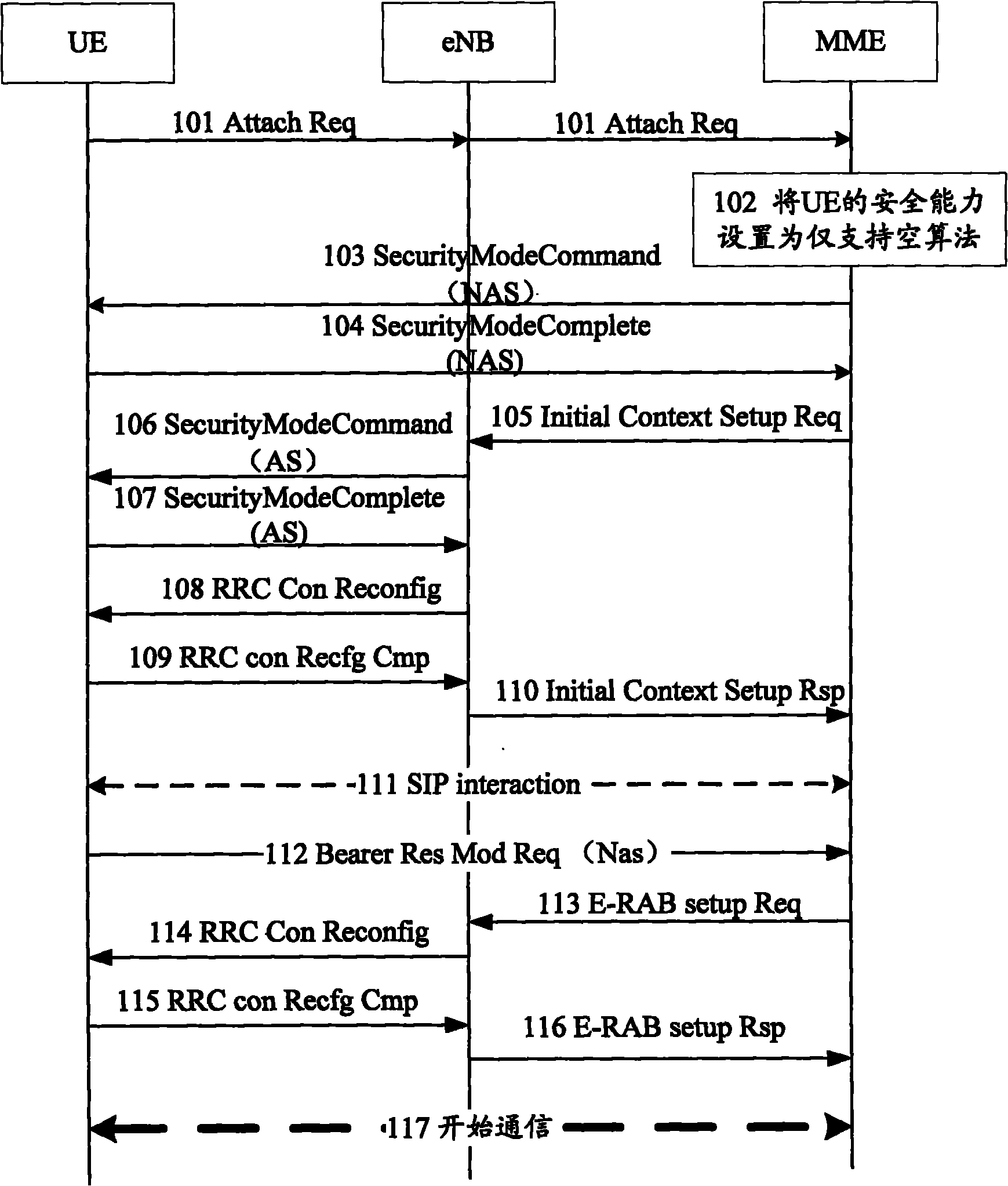
[0080] figure 2 It is a flow chart of Embodiment 2 of the emergency call-based security negotiation method of the present invention, such as figure 2 As shown in this example, the emergency call-based security negotiation method includes the following steps:
[0081] 201: The UE sends an Attach Req message to the network side. The Eps Attach Type item in the Attach Req message is set to Eps Emergency Attach, and the UE Network Capability item is filled in with the real security capability of the UE, that is, the security capability of the UE under normal conditions and the security capability of the UE under normal conditions. Security capabilities in restricted service situations.
[0082] 202: The MME ignores the security capability reported by the UE, and directly sets the UE security capability to only support the null algorithm.
[0083] 203: The MME selects an empty algorithm according to the security capability of the UE, and initiates a NAS Security Mode Command to...
Embodiment 4
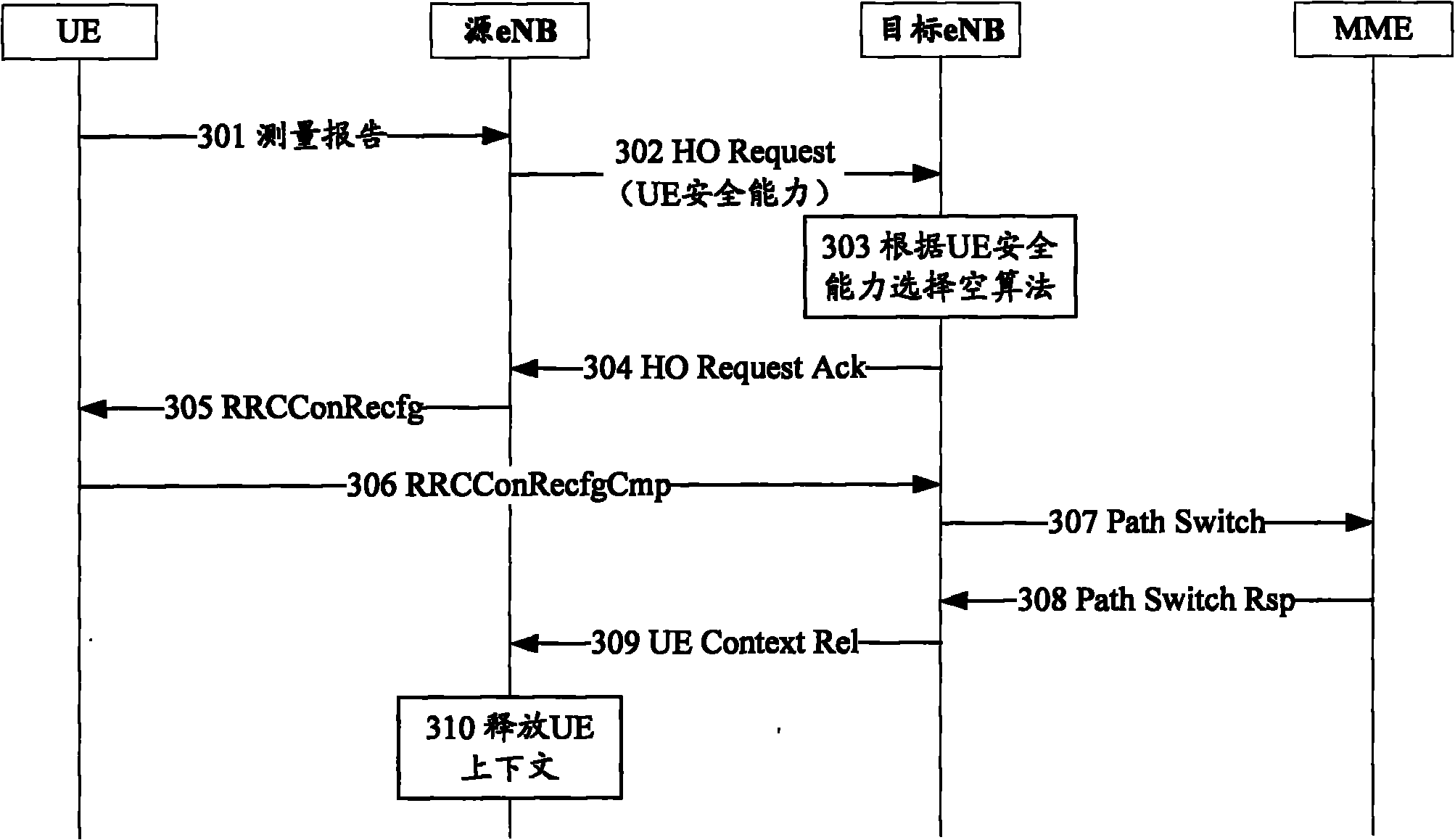
[0100] Figure 4 It is a flow chart of Embodiment 4 of the emergency call-based security negotiation method of the present invention, as shown in Figure 4 As shown in this example, the emergency call-based security negotiation method includes the following steps:
[0101] 401: The UE reports a measurement report, and the report carries a target cell ID that meets requirements.
[0102] 402: The source eNB initiates handover based on the S1 interface according to the target cell ID, and sends a HANDOVER REQUIRED to the MME.
[0103] 403: The MME stores UE Security Capabilities that only support the null algorithm, and sends a HANDOVER REQUEST request to the target eNB, carrying the UE Security Capabilities (only supports the null algorithm).
[0104] 404: The target eNB selects the null algorithm as the security algorithm of the AS according to the UE Security Capabilities sent from the MME.
[0105] 405: The target eNB generates an RRCConnectionReconfiguration message acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com