Permission expansion control system and method thereof
A technology for extending control and authority, applied in instruments, digital data authentication, electrical digital data processing, etc. It can solve the problems of cumbersome loss, and achieve the effect of easy expansion and infinite expansion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
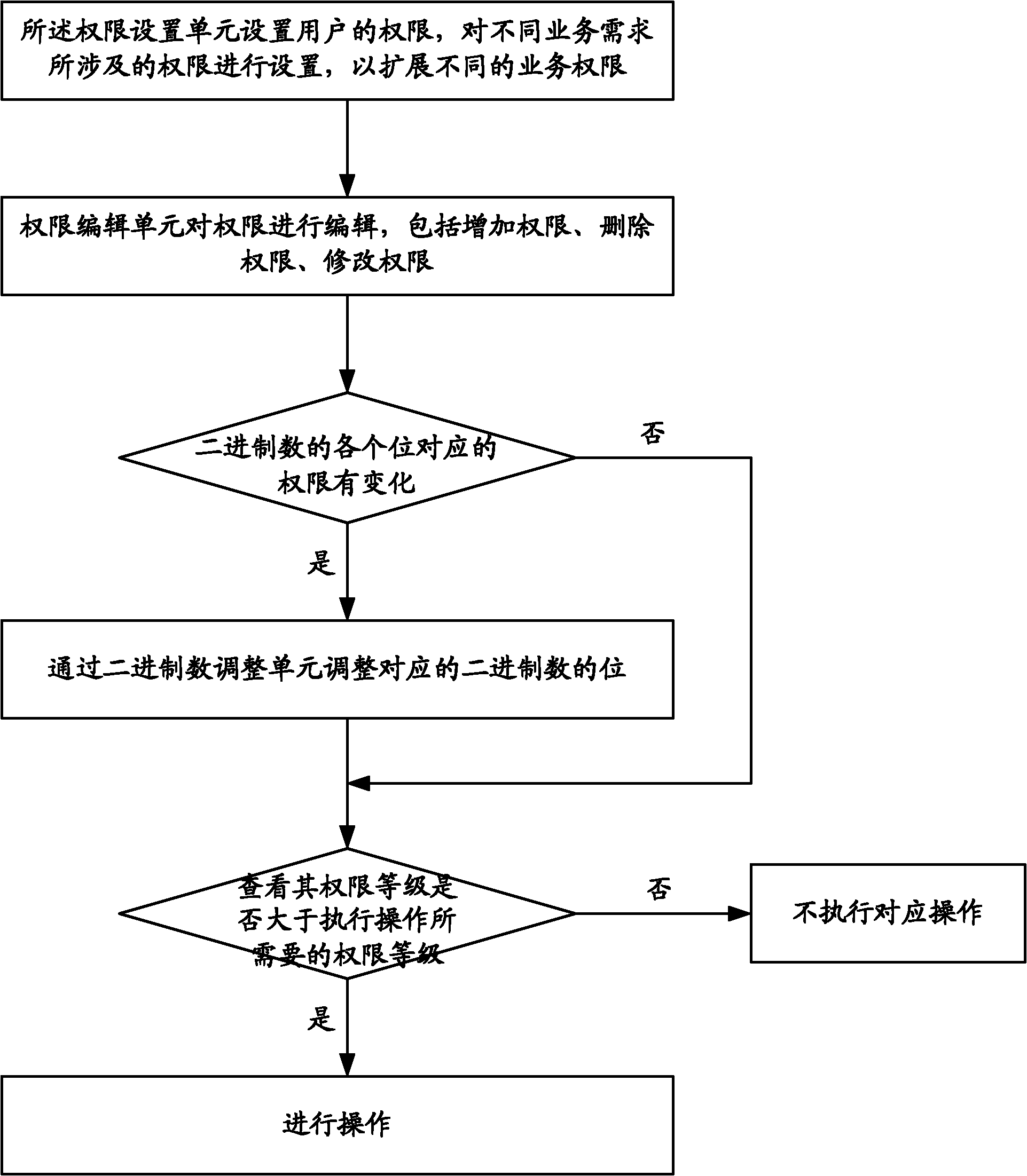
[0076] The present invention can effectively control the permissions involved in different business requirements, can infinitely expand different business permissions, can meet the customization needs of different users to the greatest extent, quickly and flexibly design permissions, and add them to the application system in a timely manner middle. Users can also edit, delete, and index the current design permissions.
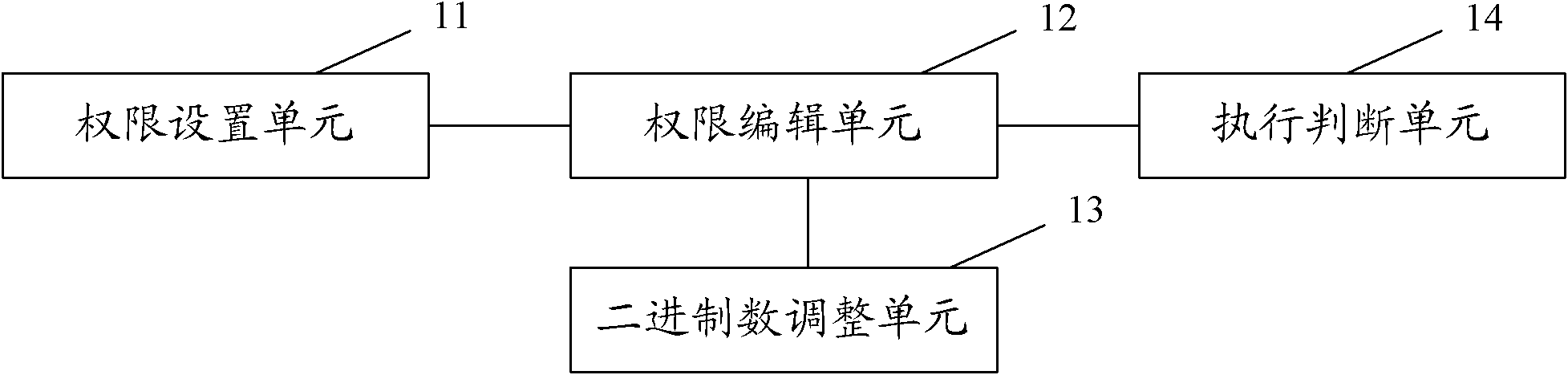
[0077] see figure 1 , the present invention discloses a permission extension control system, the system includes a permission setting unit 11 , a permission editing unit 12 , a binary number adjustment unit 13 , and an execution judging unit 14 .
[0078] The authority setting unit 11 is used to set the user's authority, and set the authority involved in different business requirements, so as to expand different business authority. Each authority of the user is set by a binary number of several digits. Whether each authority is selected is set by the value o...
Embodiment 2
[0094] In this embodiment, the extensible authority control of the system of the present invention is based on the binary carry principle, a design idea of dynamically expanding the number of authority bits to achieve unlimited expansion of authority levels. This technology is to solidify this design idea with php code and apply it to realize it.
[0095] The design idea of extensible access control is the mapping of the idea of binary digits. The binary number is a combination of 0 and 1. Therefore, it can also be designed to define unchecked (unauthorized) as 0 and checked (authorized) as 1.
[0096] In the system of the present invention, the specific operations of specific applications are separated one by one, and these independent operations will be defined as a constant in the code. The binary digit corresponding to this constant is called the permission bit, as shown in the table 1. In Table 1, permission bits for certain application operations are defined.
[...
Embodiment 3
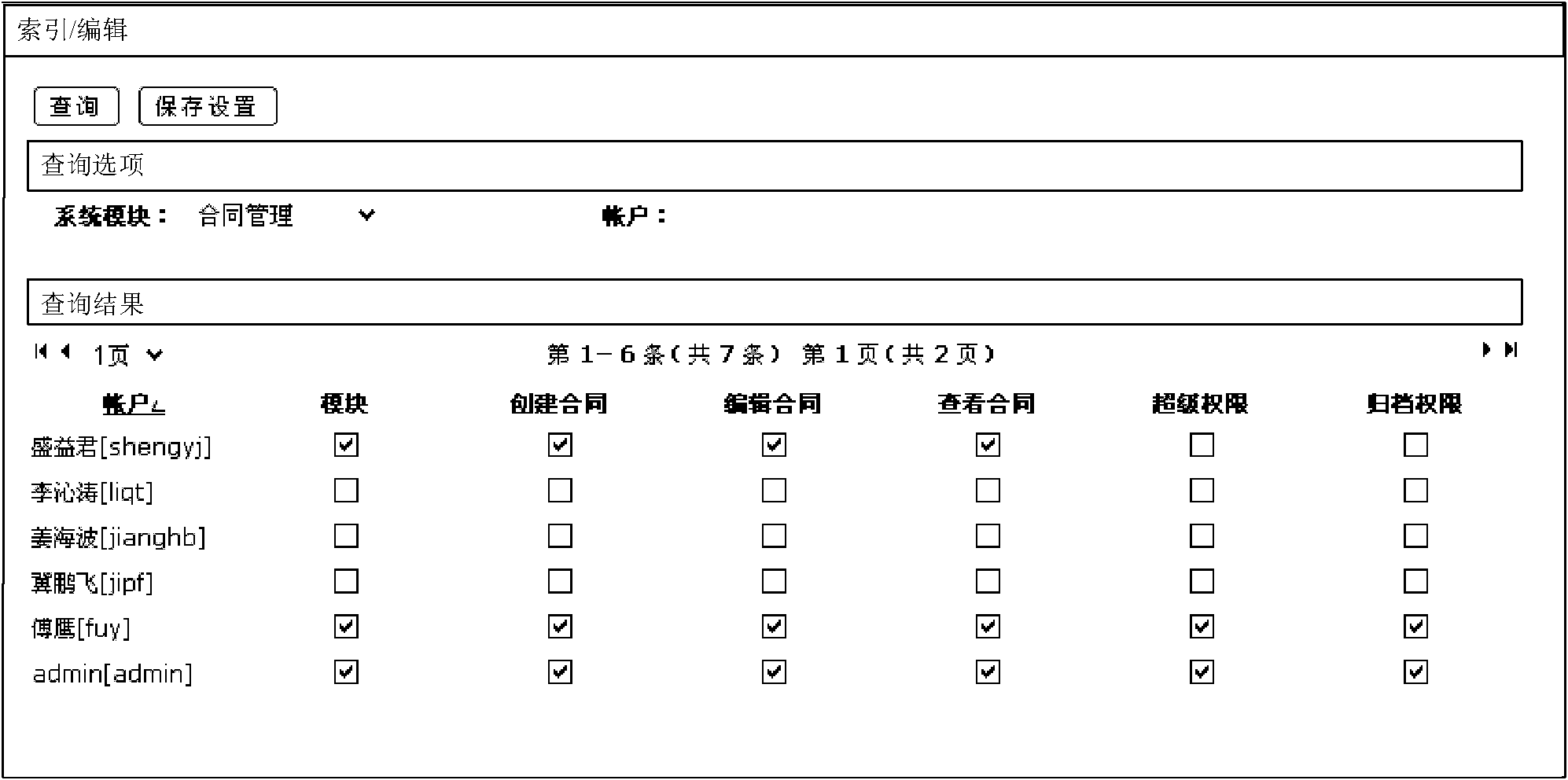
[0102] In this embodiment, different business permissions are set according to different applications, and the system administrator (or system management authorized user) authorizes the business operation of the user by checking. After the authorization operation is completed, the authorized user will have the business operation authority, such as image 3 shown.
[0103] This embodiment takes the contract management application as an example:
[0104] For example, put image 3 If it is checked, it means that the corresponding user has (authorized) the permission. If it is not checked, it means that the corresponding user does not have (not authorized) the permission. The permissions that admin has under this application are:
[0105] -Module: means that admin has been authorized and has the permission to enter the application (contract management);
[0106] -Create a contract: means that admin has been authorized and has the authority to create a contract;
[0107] -Edit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com